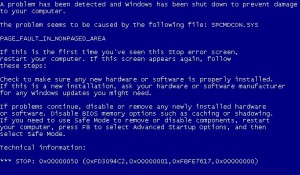
 Microsoft confirmed today that the recent spate of Windows XP crashes and blue-screens experienced by people who installed this month’s batch of security updates were found mainly on systems that were already infected with a rootkit, a tool designed to hide malware infestations on host computers.
Microsoft confirmed today that the recent spate of Windows XP crashes and blue-screens experienced by people who installed this month’s batch of security updates were found mainly on systems that were already infected with a rootkit, a tool designed to hide malware infestations on host computers.
The folks at Redmond initially suspected rootkits may have played a part in the interminable reboot loops that many Windows users suffered from following February’s Patch Tuesday, but the company also said that it couldn’t rule out the possibility that third-party hardware and software conflicts might have also been to blame. Today, Microsoft rejected the latter possibility, and said it had concluded that the reboot occurs because the system is infected with malware, specifically the Alureon Rootkit.
“We were able to reach this conclusion after the comprehensive analysis of memory dumps obtained from multiple customer machines and extensive testing against third party applications and software,” wrote Mike Reavey, director of the Microsoft Security Response Center. “The restarts are the result of modifications the Alureon rootkit makes to Windows Kernel binaries, which places these systems in an unstable state. In every investigated incident, we have not found quality issues with security update MS10-015.”
Indeed, as I noted in a post earlier this week, Alureon is among the Top 10 threats that Microsoft’s various security technologies — including its “malicious software removal tool” — regularly detect on Windows systems. According Microsoft’s own Security Intelligence Report, Microsoft’s security products removed nearly 2 million instances of Alureon from Windows systems in the first half of 2009 alone, up from a half million in the latter half of 2008. [Microsoft’s malicious software removal tool is a download offered through automatic update and Windows update that runs in the background once a month, and removes any malware it finds.]
Microsoft’s guidance for people who have been affected by this leaves a bit to be desired. The company says users should continue to deploy this month’s security updates and make sure their systems are up-to-date with the latest anti-virus software. Microsoft also says it is working on a simpler solution to detect and remove Alureon from affected systems which should be released in a few weeks, as are several other third party vendors.
Obviously, if you are having trouble getting out of the reboot loop caused by this patch+infection, you are not going to be able scan your system with a traditional anti-virus program. I have posted instructions here on how to manually remove both the problematic patch and the infected system files. But folks who have recovered their systems through these methods should strongly consider scanning their systems for additional malware with several anti-virus tools. I list a few free online scanners at this blog post, but be aware most of those require users to install ActiveX controls and to use Internet Explorer.
If you want to be doubly sure, I would suggest booting your computer into a Live CD solution that is centered around removing virus infections, such as the AVAST! Bart CD or LinuxDefender Live! I wrote a short tutorial on how to burn and boot into a live CD at this link here.




“If you want to be doubly sure, I would suggest booting your computer into a Live CD solution…”
Agreed. But don’t take the CD out.
Hah! Love it.
Don’t worry, the BSOD isnt a problem anymore..
http://www.theinquirer.net/inquirer/news/1592421/microsoft-security-patch-flaw-plugged-hackers
The rootkit authors updated their code!
So I can take the CD out now? Is this true?
Oh this is a double-win! I get to take out the CD and I get to keep my rootkit too! Wow!
Brian, thanks for the clear, direct reporting.
My PC XP-Pro/SP2 got a “clean bill of health”
from:
– Avast
– Malwarebytes Anti-Malware
– SuperAntiSpyware
– MS’ own MSRT tool
Yet…I refuse to patch my PC in February!.
Why?
Maybe the above tools will not detect this rootkit,
and I risk a fatal BSOD….
Result:
millions of PC Users (incl. myself),
will not install the February Windows Update patches…ie: KB 977165 et al.
By not patching in February, to avoid a BSOD,
we are now exposing our PCs to other threats!
When do you think MS will give the “all clear”,
and the rootkit detection tool, they promise?
txs Brian!
SFdude
SF – there are several free tools to use that can find and fix any Alureon rootkit infection. The Kaspersky tool has been mentioned, and there are others.
http://support.kaspersky.com/downloads/utils/tdsskiller.zip
Sophos has a search and kill for rootkits like Alureon too:
http://www.sophos.com/products/free-tools/sophos-anti-rootkit.html
instructions on using it:
http://www.sophos.com/support/knowledgebase/article/17026.html
I would say if you’re using XP, have scanned with these tools and found nothing you should feel good about going ahead and installing the ms010-015 update
Thank you, Brian!
An “all clear”? You’re kidding, right?
Someone’s waiting for an ‘all clear’ from Microsoft? When has there ever been an ‘all clear’ from Microsoft? When in the past ten years has Windows been safe? When?
92-97% of all spam today is generated by Windows PCs. There are hundreds of thousands of Windows malware strains in the wild. Now Amit Yoran’s NetWitness uncovered a new botnet with 74,126 compromised Windows PCs. Only a few months ago a cache of 74,000 FTP login credentials were discovered by Prevx for companies like Disney, for NASA, Bank of America, Symantec, McAfee – where’s the ‘all clear’?
Let’s take a brief look at the best of the trojans. This from FortiGuard.
http://bit.ly/1P4TPT
First to note: Zeus is not self-propagating. It must find a way of attacking. This is usually accomplished through either a drive by or a mail attachment. But once this is done and the trojan resides on the local machine, the following happens.
1. The install function searches for the ‘winlogon.exe’ process, allocates some memory within it, and decrypts itself into the process.
So it’s possible to corrupt another running process? This isn’t supposed to be possible on a secure system.
2. The bot executable is written to the hard drive as ‘C:\WINDOWS\system32\sdra64.exe’.
It writes to a system area? How is this possible? Isn’t the system supposed to protect itself?
3. The directory ‘C:\WINDOWS\system32\lowsec\’ is created.
So a rogue process can even create a directory in a system area? Where’s the security?
3b. This directory is not visible in Windows Explorer
O RLY? How is that possible? This is secure?
4. The Winlogon (‘HKLM/SOFTWARE/Microsoft/WindowsNT/CurrentVersion/Winlogon’) registry key’s value is appended with the path of the bot executable: C:/WINDOWS/system32/sdra64.exe. This will cause the bot to execute when the computer restarts.
So a rogue process can even write to supposedly protected parts of the Registry? How is this possible on a secure system?
5. The Windows XP firewall is disabled.
O RLY? Where is the security?
Those are five security violations that could never happen on a secure operating system. Given that there are tens of millions of Windows machines infected in a similar fashion, it’s painfully obvious even to the security hobbyist that this system has no security whatsoever.
But of course it only gets worse and worse. For once the trojan is up and running, it starts to do even worse things.
And let’s dwell a second on that most precious of critters, the rootkit. A rootkit by definition is supposed to attain ‘root’. Given that Windows doesn’t have a real equivalent – only the mostly defunct ‘SYSTEM’ account – one has to extrapolate to what ‘root’ means on Windows. And one thing it has to absolutely mean is: being able to do anything to the system, including hiding itself from kernel processes.
But a moment’s thought reveals what’s going on. For to get that kind of privilege – even on Windows – means that the rootkit can essentially overpower everything else, including the kernel.
And yet where is the privilege escalation? Where did it occur? How did it occur? Rootkits on Windows normally are not installed through social engineering. Being prompted for an admin password to do something sensitive doesn’t occur much in the world of Windows. No, these rootkits install themselves so easily because there is no resistance from the system. The Sony DRM rootkit didn’t need privilege escalation – and remember who first discovered it. Do you think Mark R was going to be duped as he inserted a Sony music CD into giving a password away? Of course not. And yet look what happened.
So many people read about the endless procession of Windows exploits Brian has reported on. Tale after tale of woe, most caused by Zeus and his friends. All these people – even at major banks and even at the AV vendors – getting infected with rootkits and trojans and they didn’t have a clue. They never noticed a thing.
What kind of operating system allows that?
Pavlov rings his bell and the dogs salivate because it’s time for dinner. Microsoft have their Patch Tuesday and everyone scrambles to get their updates. But does anyone think a bit about what is going on? Does anyone hear any other bell tolling?
Microsoft and Microsoft products are a royal pain. So are the people who use them. Now here’s a shocker: Brian has a MacBook Pro. Yes, he uses Windows too because he wants to report on the general security situation. But he has (and uses) an Apple computer. And you may remember he openly advocates (nags about) using a Linux live CD for critical operations. Yet how many people gravitating here every day have a MacBook Pro? Or a Linux live CD? How many have even tested another system?
Not many. And it is this self-same group modding down reminders that Brian recommends a live CD and/or an Apple box. It is this self-same group squirming in the face of those slings and arrows directed at Microsoft and coming out with gems such as ‘oh all platforms are insecure, the other platforms will be just the same tomorrow’. We’ve had ten years of this New Millennium; ten years since ILOVEYOU; and the world has yet to see any major calamity outside the world of Windows, all the while inside the world of Windows it gets only worse and worse and worse…
And someone is waiting for an ‘all clear’?
@Rick,
For the most part I agree with you and find your taking a step back to view the problem at a higher level refreshing. I spent many years working with mainframes and was reasonably familiar with the internal OS design. Thus, like you, I see the painfully poor design choices made with Windows.
Much of it goes back to the early days when hardware was very different. Mainframes never made a concession to security or reliability even when their hardware was less powerful.
That said, you are targeting the worst case here, which may not be fair. Anyone who runs as an Admin level user is all but asking for it. This turns off whatever security MS has baked into the system. Not a fair fight.
Yet, many Windows users run as Admin and don’t realize the danger this entails.
Whose fault is poor user education?
Microsoft is REALLY at fault with Win7 where they recommend running as a restricted user and where the OS does this fairly well. Yet, they default everyone to being admin users.
These are the Fred Flinstone years in personal computing. Future generations will look upon this era as brutally crude, the same way we might regard a 1910 era automobile.
Respectfully, for starters, you’re using a logical fallacy of Appeal to Emotion.
Second, you’re being disingenuous as your entire argument is based on a user being logged in as a full administrator which goes against best practices. Like other modern OS’s, Windows does have a security architecture that allows you to lock down/secure the system. The problem is that running as administrator, you’ve basically disabled all those security features built into the OS and given the keys to the castle to anything that runs on that system. Without administrator access, rootkits, as well as, most malware would NEVER be able to get their hooks into the system. The most they could do is affect the current user profile, NOT the entire system.
The issue of running as administrator stems from an old paradigm where a great majority of software developers, including Microsoft designed software that required admin access. Something malware authors have taken full advantage of these days. It was a different ecosystem back then. We didn’t have the Internet connecting all these computer systems together. You didn’t have the threat landscape that exists today. Obviously, much as changed and it’s been a long drawn out struggle to change that old paradigm, which requires software to be rewritten and ecosystems to be changed. It’s not a simple process considering the ubiquitous nature of Windows. Much has been accomplished over recent years, although there is still much to be done, primarily now, I believe, in user education.
Ultimately, it’s a compromise between usability and security. The most secure system is one powered off, but it’s not one that is very useful. Microsoft could default more toward security, but that would break a plethora of software applications that still require admin access and tilt the apple cart away from usability upsetting many users (ex. outcry with Vista’s UAC). Regardless, considering the nature of threats these days, it is imperative to implement one of the biggest defenses against malware, the use of a non-admin account. Overall, it’s part of a defense in depth strategy that should be common practice. The problem is people don’t want to be bothered. They just want their computers to work out of the box without much effort. To most security is an afterthought. That is until they become a victim of malware. It must be understood that security is a process, not a onetime thing like installing antivirus/security software and thinking you’re safe. Until that mentality changes, we will continue to have these issues.
To raise such an argument involving ‘best practices’ isn’t right either. Microsoft knows the majority of the end users will get their new box from their local shop and they use it as the OEM has left it along with all the links, tool bars and other customizations to the system that mostly run with elevated privileges before you even buy it off the shelf. These people bring their boxes home, power it up and once they configure their network they go on their way.
Making it mandatory for the OS to help the user maintain ‘best practices’ should be the mandate, especially for a company involved in OS development for 30+ years now. Expecting a bit more of a company like Microsoft is not a bad thing they make billions of dollars a year making the OS, hire the most talented developers and have the most pull in the industry, we should be in digital nirvana by now. Alas we deal with constant “security theater” due to OS ‘best practices’ not being followed. Wouldn’t it be nice if we could pay for someone to do that?
SFDude, is there a reason you are SP2? SP3 has been out sometime and is a worthwhile upgrade…
Hi Sam,
My understanding (I may be wrong),
is that
XP SP3 = XP SP2 + all win updates.
I have (up to now), installed all the monthly patches.
Anyhow, I’ll have to install XP SP3 later,
‘coz M$ will suspend all update patches to XP SP2
in June 2010.
Brian, Kaspersky has a preventative maintenance tool that can be used before someone installs MS10-015. It is specifically for cleaning the Alureon/TDSS rootkit, and can be download from here:
http://support.kaspersky.com/downloads/utils/tdsskiller.zip
You can trust it because you are downloading directly from the vendor, and the executable inside the zip file is digitally signed by them.
The only trouble is that if you have an existing antivirus solution from Trend Micro, Symantec, or CAT that has not already detected and cleaned Alureon/TDS from your disk driver, it may interfere. According to VirusTotal, these three vendors all detect the Kaspersky tool as potential malware:
http://www.virustotal.com/analisis/e385b9d7912dbde0cdf4f48aff7e73d0dbffb9f6b7b6090b27016bfbbf690b2c-1266508047
A head-scratcher for me is:
The machines affected by this interaction of the Alureon rootkit and MS10-015. And MSRT has had good success against Alureon.
So were the affected machines previously running the MSRT to remove Alureon?
If so, was this a variant that the MSRT didn’t clean, or did MSRT remove the Alureon yet left the corrupted storage driver in place?
And if that last part were true, why didn’t Windows File Protection kick in and restore the good version of atapi.sys (or whichever storage driver was affected on the particular machine)?
I still see value in waiting to install MS10-015 until after the next MSRT update that will better target Alureon. Hopefully that will also target the new flavour that the malware authors have already released!
All excellent points, Andrew.
Following your own (correct) logic:
by the time the next versions of MSRT and Microsoft Security Essentials are released (in March), Alureon will have changed once again…and will not be detectable.
I guess the same holds true for Avast, MBAM, etc.
The “stealth race” is on…
I worked on an XP machine today that had been rendered unbootable by the MS010-015 patch. Backing out the patch (using a Linux Live CD rather than the Recovery Console but basically doing the same thing) did not work. All it did was force a checkdisk and change the STOP error code.
Replacing atapi.sys did get the system up and running.
Then I ran the Kaspersky TDS Killer software (which is portable by the way) and it found another file also infected by TDS.
Info on Linux Live CD for patch backout
http://blogs.computerworld.com/15595/using_linux_to_back_out_a_windows_xp_patch
I wonder just how long this has been going on.
So many of the upgrades my the environment have gone wrong going “strangely” I suspect that BSODS are a way of diagnosing the possible presence of all sorts of malware – even going back quite a ways now.
I remember when boot sector viruses often reared their ugly heads when a machine was finally restarted after a long time (say a month) after an update forced a reboot. When did the virus get in? There was to be no analysis as like today. It took a while for AV products to find and remove them on a active system. It took a lot longer to protect the boot sectors themselves.
The biggest crime is that generations are being taught patching – post discovery of exploits – is normal and to be expected. Analogs to this situation into meatspace would call for investigations and resignations after an “Moushiwake arimasen” for poor quality products negatively impacting the lives & livelihoods of consumers.
‘The biggest crime is that generations are being taught patching – post discovery of exploits – is normal and to be expected.’
Bingo. Pavlovian. A lot of people make a lot of money off making fools out of everybody else.
Amit Yoran and Alex Cox @ NetWitness say expressly that AV cannot protect against attacks like these and an analysis by Trusteer ascertains the effectivity of AV to stop Zeus at a pathetic 23%.
You can never compensate for a system that architecturally has no security.
I think part of the problem is that home users have been conditioned to expect convenience over security. I know that when Vista first came out, people kept talking about what a pain UAC was, and how to turn it off so they didn’t have to keep entering passwords.
Come to think of it, I got a new Windows-7 laptop at work yesterday, and I installed a bunch of stuff. I don’t recall seeing any UAC dialogs…
what? didn’t microsoft’s free antivirus software not pick this up and clean it beforehand? i’m shocked! what of microsoft’s malware scanner and/or cleaner why doesn’t microsoft guard with the os itself against malware hooking programs?
I’ve had a weird, albeit minor, problem with the latest MS patches. I installed all EXCEPT the KB977165 on 2 WinXP-SP2 machines and rebooted yesterday without problems.
Upon starting both machines this morning, I discovered that Automatic Updates had been “automatically” turned ON & both machines were busily downloading updates.
Rebooted, and AU stayed OFF, but I’m getting the annoying “Your computer may be vulnerable” notification at startup.
Has anyone experienced this? I’ve had automatic updates turned off on all my machines for more than 2 years.