I spent the past few days in Mexico City participating in the annual meeting of the Honeynet Project, an international group dedicated to developing and deploying technologies that collect intelligence on the methods malicious hackers use in their attacks. The event brought in experts from around the globe, and our hosts — the National Autonomous University of Mexico (in Spanish, UNAM) were gracious and helpful.
As it happens, honeynets and other “deception technologies” are among the approaches discussed in the following document, written by the National Security Agency‘s Information Assurance Directorate. A source of mine passed it along a while back, but I only rediscovered it recently. I could not find a public version of this document that was published online previously, so it has been uploaded here.
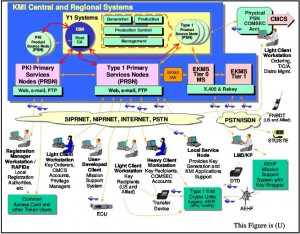 The 605-page PDF document reads like a listing of the pros and cons for a huge array of defensive and counterintelligence approaches and technologies that an entity might adopt in defending its networks. Of particular interest to me was the section on deception technologies, which discusses the use of honeynet technology to learn more about attackers’ methods, as well as the potential legal and privacy aspects of using honeynets. Another section delves into the challenges of attributing the true origin(s) of a computer network attack.
The 605-page PDF document reads like a listing of the pros and cons for a huge array of defensive and counterintelligence approaches and technologies that an entity might adopt in defending its networks. Of particular interest to me was the section on deception technologies, which discusses the use of honeynet technology to learn more about attackers’ methods, as well as the potential legal and privacy aspects of using honeynets. Another section delves into the challenges of attributing the true origin(s) of a computer network attack.
The document is a final draft from back in 2004, although I’m told the final version of the document varies little from this copy. In any event, it may be surprising to some to see how many of the techniques, technologies and challenges detailed in this document remain relevant and timely six years later. It is embedded in this blog as a Scribd file, viewable after the jump (the document is > 5mb, so please be patient). I removed the Scribd embedded PDF, because it was causing problems for too many readers. The full PDF is available at this link here.




Thank you for sharing this. NSA puts out some good stuff and it is great that they share it with the public. I am an IT Security engineer and I really enjoy your blog. Keep up the good work!
@KB, “I could not find a public version of this document that was published online previously, so it has been uploaded here.”
With the “For Official Use Only” labeling that is not surprising. Hope there are no negative repercussions from your posting it now, even though it is six years old some folks are sticklers about such things.
Best of luck!
Yes, but we’ll visit Brian in prison.
Thanks for posting this document, Brian. IMO, it reflects well on the work being done at the Fort.
@Jeffrey, I agree, and I think it is important to get this kind of information shared into the private sector. Hopefully that will be an area that Mr. Schmidt will be working to address, so we won’t have to wait six years to see the blueprint that some of our best and brightest cooked up.
You said: The full PDF is available “at this link here.”
Brian, are you sure it isn’t also available
“at that there link.” 🙂
Maybe just available “at this link” or even available
“here” would be a better way to put it.
Redundant redundancy lives!
BK,
Do you intend to post the PDF as a permalink ?
It would be a very handy reference.
The Federation of American Scientists posted this little NSA gem : http://www.fas.org/sgp/othergov/dod/nsa-redact.pdf way back when – “Redacting With Confidence”. It is of a little later vintage, but still very consistent with the non-adoption of the RAdAC Model which is evidently the approach of Industry. That was of course their choice, but the reason it is important now is that Google, FaceBook and others really do not have any clear guidance as to what sort of personal information they may or may not subject to mass disclosure. This was never really an issue for the NSA and the Government in general.
I appreciate the concern which is been rose. The things need to be sorted out because it is about the individual but it can be with everyone. I like this particular article It gives me an additional input on the information around the world Thanks a lot and keep going with posting such information.
=========================================
New Technology
I have been a computer / IT technician for a long time now. I have dealt with PCs amd MACs but still prefer PCs for personal reasons. I have worked for many local corporations and like to read about new products, software, hardware, systems, and other developments in the industry. I find it is very usefull in the job-world to always keep up-to-date on infromation. Obviously I can’t read tons of blogs all day, but ocasionally I do stumble upon a good one like yours. I really apreciate the infromation you provided in the blog. It always amazes me how I can still learn something new every day.