Keystroke-logging computer viruses let crooks steal your passwords, and sometimes even read your e-mails and online chats. Recently, however, anonymous criminals have added insult to injury, releasing a keylogger strain that publishes stolen information for all the world to see at online notepad sharing sites such as pastebin.com.
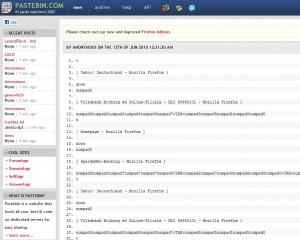 Last week, security experts at BitDefender discovered a continuing stream of new entries at pastebin.com and pastebin.ca that included text files laid out in the format typically used by keystroke-logging malware. For example, each keypress in the log posted to pastebin.com is preceded by a listing of the program currently in focus on the victim’s screen, and each function key pressed is spelled out, so that when the victim hits the backspace or down arrow key, for instance, the keystroke log will show a “[back]” or “[down]” entry in place of each corresponding keypress (see the screenshot to the right).
Last week, security experts at BitDefender discovered a continuing stream of new entries at pastebin.com and pastebin.ca that included text files laid out in the format typically used by keystroke-logging malware. For example, each keypress in the log posted to pastebin.com is preceded by a listing of the program currently in focus on the victim’s screen, and each function key pressed is spelled out, so that when the victim hits the backspace or down arrow key, for instance, the keystroke log will show a “[back]” or “[down]” entry in place of each corresponding keypress (see the screenshot to the right).
Typically, keystroke logging malware will submit stolen data to a Web server specified in the malware that the attacker controls. BitDefender theorizes that those responsible for creating this keylogger variant may have chosen pastebin.com because it is unlikely to be blocked by Web filters or malware blacklists.
I kept the pastebin.com home page open most of the weekend and refreshed it periodically, and confirmed that a relatively large number of keylogger records were being uploaded in real time to the free service. To the right is one of many screenshots I took of the files I found on Pastebin.com.
Pastebin owner Jeroen said Pastebin is aware of the problem and is working on a new version of the site that should block these automated keyloggers from posting their content there.
“This will take another week or two though,” Jeroen wrote in an e-mail to KrebsOnSecurity. “We also remove all reported pastes within 24 hours. But at this point in time people do need to warn us about them manually via the report pages.”
A great deal of what gets posted into pastebin.com appears to be programming code snippets and online gaming logs, but if you poke through the incoming posts long enough, you’re bound to find random gems by turns strange, funny, lurid and voyeuristic. Oh, and if you stumble upon any entries that look like keylogger reports, consider clicking the “report” button in the upper right of of the pastebin, per Jeroen’s suggestion.
I suspect that this particular keylogger variant is the work of amateurs or beginners trying out a new method, as many of the files keylogger reports I found included chat logs and snippets of e-mails. Most criminals are after financial information — such as credit and debit card account numbers and online banking credentials — and couldn’t care less about your everyday online conversations. Indeed, all of that extra data tends to quickly cause massive data storage problems for thieves, who often are dealing with monster amounts of data streaming from thousands of infected systems. Hence, criminals who have been doing this for a while tend to rely on keyloggers that are really more akin to what are known as form grabbers; the malware concentrates on recording the credentials that the victim passes when he or she logs in to an encrypted or unencrypted Web site.




It hasn’t been updated in a while, but take a quick look through: http://www.pastebinfail.com/ for similar fail items.
Checking out that site. Checked one logger in particular. It’s shattering how many of those ops wouldn’t work on a secure operating system. It’s a duck shoot.
hmmm Pastebin would make interesting fodder for a screensaver.
And see this pastebin post too! Apparently the guy stealing passwords doesn’t like people reporting his keylogger posts
http://www.pastebinfail.com/2009/07/stop-stalking-pastebin.html
it’s quite easy to find them; search on “numpad0” and chances are likely you’ll get a list of them.
Now combine with your favorite mailtool and you should get logins/passwords (sadly it seems like many people automatically login to facebook)
@ jeff:
It’s quite possible.