Operating and planting an ATM skimmer — cleverly disguised technology that thieves attach to cash machines to intercept credit and debit card data — can be a risky venture, because the crooks have to return to the scene of the crime to retrieve their skimmers along with the purloined data. Increasingly, however, criminals are using ATM skimmers that eliminate much of that risk by relaying the information via text message.
[NOTE TO READERS: The Today Show this morning ran an interview with me for a segment they produced on ATM skimmers.]
Visit msnbc.com for breaking news, world news, and news about the economy
This latest entry in my series on skimmers includes a number of never before published pictures of a cell-phone based skimmer set that sends stolen bank card data to the attacker using encrypted text messages. The following images were obtained directly from a skimmer maker who sells them on a very well-protected online fraud forum. This particular craftsman designs the fraud devices made-to-order, even requesting photos of the customer’s targeted ATMs before embarking on a sale.
Just as virus writers target Windows in large part because it is the dominant operating system on the planet, skimmer makers tend to center their designs around one or two ATM models that are broadly deployed around the globe. Among the most popular is the NCR 5886, a legitimate, unadulterated version of which is pictured below. 
This skimmer I’m writing about today sells for between $7,000 and $8,000 USD, and includes two main components: The actual card skimmer device that fits over the card acceptance slot and records the data that is stored on the back of any ATM cards inserted into the device; and a metal plate with a fake PIN pad that is designed to sit directly on top of the real PIN pad and capture the victim’s personal identification number (PIN) while simultaneously passing it on to the real PIN pad underneath.
Not all skimmers are so pricey: Many are prefabricated, relatively simple devices that fraudsters attach to an ATM and then collect at some later point to retrieve the stolen data. The trouble with these devices is that the fraudster has to return to the compromised ATM to grab the device and the stolen data stored on it.
In contrast, wireless skimmers like the one pictured below allow the thief to receive the stolen card data from anywhere in the world, provided he or she has a working cell phone signal.
The actual card skimmer in this seller’s model is quite small, and yet includes both a magnetic strip reader and a tiny radio that sends the collected data (known as “dumps” in fraud circles) in an encrypted format to a device built into the PIN pad (more on that in a moment).
Here are a few photos of the razor thin skimmer that comes with this kit:
And here’s a view of the electronics that powers this little thief:
Now, let’s have a look at the brains behind this custom skimming combo. Below is the PIN pad overlay:
And if we turn the bogus PIN pad overlay around, we get a glimpse of what really makes this thing tick:
Although you cannot really tell from this picture, the PIN pad overlay contains its own GSM module, basically the guts of a cell phone that is capable of sending text messages to any phone of the customer’s choosing that operates under the GSM mobile communications standard. According to the maker of this kit, to whom I spoke briefly via online chat, the GSM module is responsible for collecting the skimmed card data from radio transmissions sent by the skimmer, and then bundling that data with the corresponding PIN into an encrypted text message.
The designer says it typically takes between 2 to 4 text messages to send the encrypted output from a single dump and PIN combination.
We didn’t get too chummy in our chat, but one of the pictures this guy shared with me provides a clue to his potential home country. Check out the photograph below, which includes a pencil ostensibly designed to give a point of reference for the size of the bogus PIN pad.
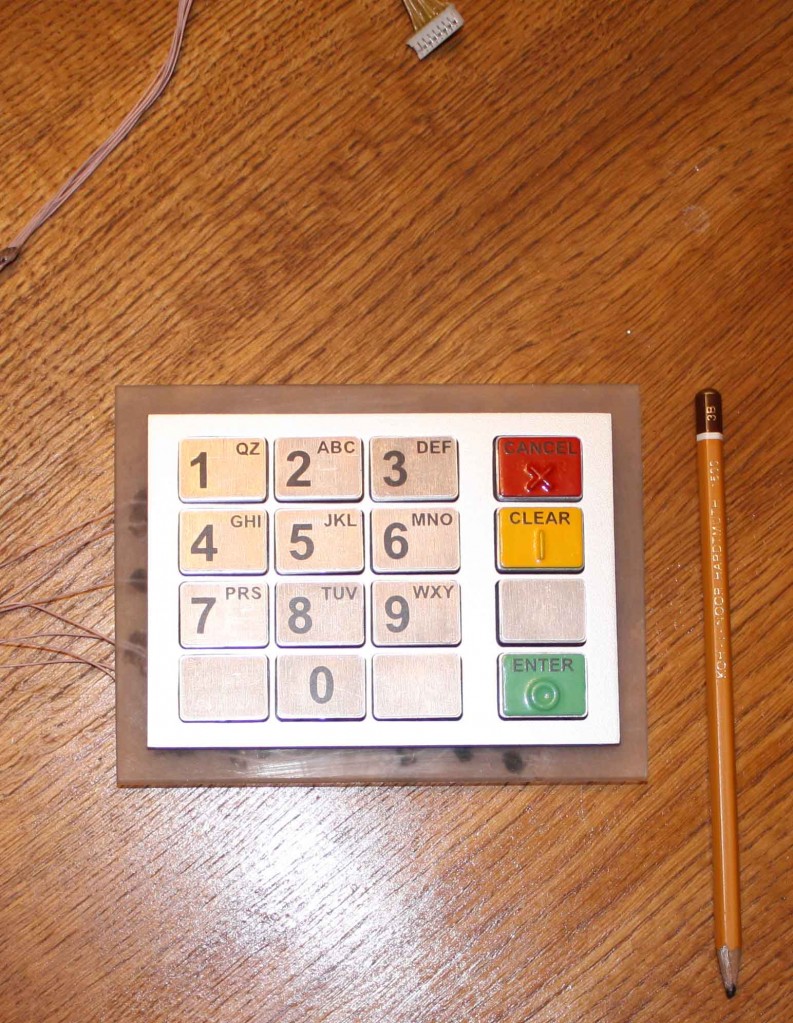 The markings on the pencil show it to be a “Koh-I-Noor” drafting pencil, a brand of writing utensil first introduced in 1890, according to leadholder.com, which bills itself as the online “pencil museum.” Leadholder.com says this writing stick established a number of trends in pencil design that we now take for granted, most notably the yellow finish, a trait that other pencil manufacturers would later imitate. More importantly, the maker of the Koh-I-Noor, a company called L&C Hardmuth, is based in the Czech Republic.
The markings on the pencil show it to be a “Koh-I-Noor” drafting pencil, a brand of writing utensil first introduced in 1890, according to leadholder.com, which bills itself as the online “pencil museum.” Leadholder.com says this writing stick established a number of trends in pencil design that we now take for granted, most notably the yellow finish, a trait that other pencil manufacturers would later imitate. More importantly, the maker of the Koh-I-Noor, a company called L&C Hardmuth, is based in the Czech Republic.
Leadholder curator Dennis Smith said the pencil in the photo is a Czech-made model 1500 that has not been distributed in the U.S. since before World War II.
“The type shown in the picture is of recent vintage, 1990s to present. There was an American made 1500 that died with the [now defunct] U.S. company in the 1990s,” Smith wrote in an e-mail to KrebsOnSecurity. “A company called Chartpak now owns the rights to the trademark in the U.S. They import and distribute products of the Czech company, but not the 1500 for some reason.”
At any rate, below is a photo of both devices attached to a working ATM (the photo has been retouched by the designer, probably to hide markings that might identify the location of the machine).
[EPSB]
Have you seen:
Skimmers Siphoning Card Data at the Pump…Thieves recently attached bank card skimmers to gas pumps at more than 30 service stations along several major highways in and around Denver, Colorado, the latest area to be hit by a scam that allows crooks to siphon credit and debit card account information from motorists filling up their tanks.
[/EPSB]









Yep! Pretty grim! The crooks just keep getting better at it! Hmmm! I think I have some of those pencils! They are in a pre-war German drafting kit, my Dad owns!
Cool article, as usual Brian! =D
re: pencil. kohinor pencils were (not sure of the current trends) quite popular all over europe and the former soviet union. as such, i would hold off on portraying it as a smoking gun 🙂
thank you for the series.
hehe 🙂 – nice pencil – same as the one on my table 😉 – u can buy these in most shops in Czech Republic 😉
Hi Brian
Love the detective work on the pencil front and you have to give it to the manufacturer of the skimmer – whilst the motive is bad; the quality looks good.
Interesting alpha layout on the keypad. Not having travelled abroad much I thought the QZ being on the #1 key a mistake until I realized I was being too US-centric. Great article.
Congrats on the Today Show interview! Wish I’d caught it, any chance of a link to that segment or a Youtube clip or something like that?
Quality of the device looks really good, wonder how difficult it is to recognize when it’s in place? Would any of us who are inclined to be skeptics still be fooled? From the photos I wouldn’t want to bet my bank balance on it!
DUH, missed that link – too big and obvious – guess I need the coffee more than I realized!
Great work. Great posting. Great interview. Thank you so much for all you are doing to alert us to this problem.
It amazes me that the banking industry doesn’t jump out in front of this problem because the real danger is that as public trust deteriorates in e-banking and e-commerce generally the biggest losers will be banks and other businesses that have come to depend on the convenience and cost savings electronic methods offer. Trust is the commodity that fuels the system. Once people fully believe that ebanking is unsafe and ATMs are untrustworthy, banks are going to start to have to hire real employees again and costs will go through the roof. Personally, I’m considering a return to mostly cash-based transactions and dependence on bank-0-mattress. (Not entirely kidding here…)
You’ll need to consult an Attorney, but I’m pretty sure that would void the mattress warranty. Be careful. 🙂
The ATM industry has been working on methods to defeat skimming for quite some time. Diebold recently announced a series of improved security measures, as I wrote about here for example:
http://www.flyingpenguin.com/?p=5595
I found it interesting that so much effort was spent analyzing the pencil, which is irrelevant to the skimmer, when the keypad is clearly for Australia (AUSTEL format). I’m in the US and I have Koh-I-Noor sitting in front of me right now.
I think what you mentioned about the AUSTEL format is very interesting, but I’m not sure why it makes the part about where the pencil was made irrelevant. This guy makes custom skimmers for ATMs, and one of the questions he’ll ask you is which country you’re planning to skim in.
Another great article Brian. Loved the investigative work on the pencil! Keep it up!
Koh-I-Noor pencils are widespread all over Europe and Russia. The are pretty much standard fare everywhere in Eastern Europe and the ex-USSR. If you had done your research, you would have reported this, instead of irrelevant details on Koh-I-Noor importation and defunct companies. 🙂
Either both those cash machines have skimmers on or neither of them.
If you look at the thickness of the keypad panel you can see that it should be visibly higher on a modded machine, yet judging by the other features of the cash machine the keypad panels on both machines are the same height.
What bothers me is that they are getting so good at these faux skimmers, that simply whacking on the ATM enclosure, may not always reveal any fake equipment, in such a simple way!
As far as region identification, I notice that the keypad in your picture has “QZ” mapped to the 1 key. Looking at my desk phone and cell phone, its different here in New York. The 7 key has “PQRS” and the 9 key has “WXYZ”. Perhaps that’s something to keep an eye out for when using ATMs?
(P.S.) I hereby self-declare myself cybersleuth!)
yeah, i caught that too. i can’t recall ever having seen the QZ keys on the 1 key, but then again i don’t think i’ve ever paid much attention to it before.
Great story Brian! As is often said when it comes to things like this, “knowing is half the battle.” Thanks.
Nice segment! But I didn’t hear them mention this blog. It would have been nice if people came by to learn about skimmers and stayed to learn about ZeuS, online banking, and money mule scams.
I’d also like some estimate of how much more banks could pay in interest on deposits if they weren’t reimbursing people for these types of losses.
Yeah, thanks for saying that, and for the first couple of times I watched the segment I didn’t see it either. But they DO mention krebsonsecurity.com on the screen, but you have to watch very carefully, because it’s only on the screen for about 1 second.
Ever since I saw your first article about this, I have been on the lookout for skimmers. I am especially vigilant when I am away from home. Like now, I am in Dubai and noticed something different about all of the ATM machines, the card slot is surrounded by a flashing green light. It would be very easy to see if there was a skimmer on an ATM as the light would be harder to fake. It would make it so the skimmer would need to be deeper and need more power for the fake light. I think this would make it easier to spot a fake.
I wonder why they do not do something like this in the US.
A light emitting from the card slot is also used in the US and elsewhere to defeat card skimming, not only to alert you but also to notify the ATM operator of the presence of a skimming device.
There are several security flaws with the light, but it is still a step in the right direction.
yeah, i caught that too. i can’t recall ever having seen the QZ keys on the 1 key, but then again i don’t think i’ve ever paid much attention to it before.
http://www.telstar-online.nl/thumbs.php?id=542&pagina=
Some picture of a skimming device in the Netherland (a year ago) they used ther camera in the mobile to look “over the schoulders”
I’m not seeing any braille markings on the fake keypad. They should be there like in this photo: http://bit.ly/a3kgLF
The absence of them could be an indication of a skimmer. It may not be a foolproof but then again…
PS most skimming equipment looks 100% like the original equipment. In the netherlands they replaced teh complete machine used to pay with debit cards in super markets.
The rail company has a new device that prevents against skimming equipment
http://webwereld.nl/nieuws/63504/ns-treft-opnieuw-maatregelen-tegen-skimmers.html
(sorry dutch article but has a nice picture)
This has brought skimming to a stop
Am I free to use the above information and video. I would like to make a presentation to the citizens / tourist in the Town of Mammoth Lakes and make them aware of skimming devises and the sort?
Thank you
Detective Douglas Hornbeck
Mammoth Lakes Police Department
Mammoth Lakes, Ca 93546
w. (760) 934-2011 etc 17
c. (760) 914-0707
Typo:
“who I with spoke briefly”
Thanks for your good work.
When you find a typo, it is more polite to send an email to the author than to post a display of your proofreading skills.
He, he,
Brian, as I was reading the beginning of your article, I noticed in the third picture a resistor (approximately wilted carrot color) with a specific shape (0.25Wattt). I also used those resistors in my youth in simple electronic toys and I know they are Russian made, hence I made my (early) assumptions over the origins of the supplier. However, those resistors were imported all over EasternEurope and after 1990 even made their way into Western Europe, therefore, your rationale, based on pencil origins is for sure more reliable than mine.
I had a call last night and thought of you.
It was a live call with an accent so outrageous that I suspected he was pretending to call from India.
His garbled message to me was that he needed to tell me I had a security problem with my internet access and that someone was about to steal my information. (I paraphrase)
As one of your fans who has been reading you for years, I couldn’t stop myself from blurting out, strongly, “Oh, you can’t be serious. You’re not actually gonna try this, are you?”
That, as you might think, gave him pause. Then he started in, gamely, with another attempt to scare me into listening to him. And I hung up.
I still have a record of the number that appeared on my caller ID. The number is from New Jersey. I’m sure it’s just one part of long network of relays designed to hide the perpetrators.
Thanks for your comment, April, but I think maybe you meant to place it on the other thread about phone phishing?
Probably Bulgarian – Bulgarian ATM skimming gangs are very active all over Europe, Russia and the US. That’s what their mafia specialized in.
That guy really knows his pencils!
Snopes.com (the urban legend investigation site) mentioned an interesting related issue:
http://www.snopes.com/crime/warnings/hotelkey.asp
Data thieves are collecting hotel key cards and encoding the magnetic stripes with their stolen credit/debit card data. The cards can then be used at ATMs and similar point-of-sale devices where no human is examining the card the customer is swiping.
Should the police stop someone carrying a pocketful of such cards, having hotel key cards does not create the same suspicion that carrying credit cards with multiple people’s names on them would. If someone is traveling, even having multiple key cards from the same hotel chain would not be unusual.
Some police departments that are seeing the technique being used locally have gotten wise and begun using card scanners to examine what is encoded on the mag stripes of any cards a suspect is carrying.
Did anyone translate the French instructions on the label in photo 3?
I would guess the RF gets some major attenuation from being behind the metal panel. I wonder if he requires the ATMs to be within a certain range of a cell site.
This skimmer is almost impossible to notice for the average user, frightening.
Ambient light sensors in a clear card reader part would make such attempts a lot more difficult; just my 5 cents.
I read your article on USA today and then on this blog . The information you provide here are very valuable. Thank you
In here, the top bank is reinforcing their ATMs by integrating two cylindrical acrylic blocks in the card insertion mechanism (cards go between the acrylic ‘sandwich’) to make it harder for skimmers to place a logging device there.
Clueless people with no ATM skimming information might not understand the importance of the simple ‘hack’ but I never draw my money from an ATM without those blocks built-in.
Here is a Simple fix for the problem:
These machines have a display screen, so the bank can simply send an image(s) (from their server, not stored in the ATM where it could be over-ridden) of what the machine is supposed to look like, overall picture and closeups of key areas. If the machine doesn’t match the images, please call the bank so they can put a hold on your card.
Very simple idea Ron! I like it! 🙂