 Microsoft Windows users seeking more certainty about the security and integrity of downloaded files should take a look at a free new offering from Internet security research firm Team Cymru (pronounced kum-ree) that provides a solid backup to anti-virus scans.
Microsoft Windows users seeking more certainty about the security and integrity of downloaded files should take a look at a free new offering from Internet security research firm Team Cymru (pronounced kum-ree) that provides a solid backup to anti-virus scans.
The tool, called “WinMHR,” is an extension of the “Malware Hash Registry” (MHR), an anti-malware service that Team Cymru has offered for several years. The MHR is a large repository of the unique fingerprints or “hashes” that correspond to millions of files that have been identified as malicious by dozens of anti-virus firms and other security experts over the years.
The MHR has been a valuable tool for malware analysts, but until now its Web-based and command-line interface has placed it just outside the reach of most average computers users. WinMHR, on the other hand, is essentially a more user-friendly, point-and-click interface for the traditional MHR service, which Team Cyrmu described this way:
“While your AV posture helps you perform detection based on signatures, heuristics and polymorphism, the MHR provides you additional layer of detection, for known badness. Based on our research, AV packages have trouble detecting every possible piece of malware when it first appears. The MHR leverages multiple AV packages and our own malware analysis sandbox to help aid your detection rate. Coupled with AV, the MHR helps identify known problems so you can take action.”
WinMHR queries the MHR in real time when the user tells it to scan downloaded files (to cut down on resource consumption, the program does not automatically scan downloaded files). If it finds any malicious files, it includes precise information about where the malware is hiding on the PC. The tool also includes a component that runs at Windows startup and scans Windows processes for malware (this feature can be disabled at installation or in the program’s “Preferences” panel).
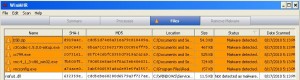
 It is important to understand the limitations of this tool. First, it is designed to supplement — not replace — anti-virus software. Second, the tool doesn’t include the capability to remove bad files that it finds (as readers can see in the screen shot above, the WinMHR detected several malicious files when run on a test machine that I abuse quite a bit).
It is important to understand the limitations of this tool. First, it is designed to supplement — not replace — anti-virus software. Second, the tool doesn’t include the capability to remove bad files that it finds (as readers can see in the screen shot above, the WinMHR detected several malicious files when run on a test machine that I abuse quite a bit).
Finally, while the tool displays the unique cryptographic hashes of any malware threats found on the user’s system, it does not try to classify or name them. If a scan with WinMHR manages to flag a file that fails to generate an alert when the user scans the same file with his or her anti-virus program, the user can find more information about the nature of the file by exporting that hash to a text file and submitting it to a scanning site like VirusTotal.com, which allows visitors to search for malware based on MD5 or SHA1 hashes. Few but the most geeky users are likely to bother with that step, which is why an application like this could be more useful with a simple right-click option to submit a hash lookup at Virustotal. Team Cymru’s Steve Santorelli told me his firm likes that idea for a future version, and that it plans to soon release a Firefox add-on version of the tool.
Despite its limitations, WinMHR can be a useful addition to the security toolbox for Windows users, experts and novices alike.




I’ve searched the Team Cymru website but could not find “WinMHR” to download. Do you have a link to it?
Thanks;
Stan
WinMHR is not yet available to the public. It is coming out in late August.
You can now check out http://winmhr.com!
http://hash.cymru.com/
Sorry, that’s only the Web frontend.
VirusTotal have just released an addon called VTzilla for Firefox http://www.virustotal.com/advanced.html#browser-addons. been using it for a day it is very good. I will try WinMHR thanks Brian, you can not have to much security.
Love being a little geeky– You can download a tool from VirusTotal so you can submit files or hashes to be scanned by them, right from your desktop. It’s great for when users forward me suspicious emails with attachments (a lot of that as of late).
I don’t think it’s all that geeky to scan my downloaded files using VirusTotal’s uploader tool. I’ve been doing it for about a year now.
I fail to see how WinMHR is any better than VT’s uploader…
One difference between WinMHR and VT’s uploader is that Team Cymru will never receive anything other than hashes of files. When you submit a file to VT, you’re sending them the entire file, which they are free to keep and do what they want with; VT’s terms are here: http://www.virustotal.com/terms.html
I hope they get faster at sending uploaded malware to all of the anti-malware companies. A few weeks ago I got a redirect to a site that wanted me to download a video codec, probably because it could not force a drive-by. So I downloaded the file, and then uploaded it to VirusTotal. Two of the anti-malware companies detected malware, the others (including Norton and McAfee) found no problem.
I was running Microsoft Security Essentials, which detected nothing during the download, and subsequent scans found no problem. I uploaded the file to MSE, and it was three days (including the weekend) before I finally got an update that detected the malware in the file.
I should have included the VirusTotal link to the scan results in the submission to MSE, that might have helped them expedite their analysis.
Doesn’t seem to be very useful, it has a very high rate of false positives for those of us managing systems. For example, it “detects” malware in most of the nirsoft.net password-recovery tools and it considers VNC to be malware. Should not be used blindly by someone who doesn’t know what she’s doing.
We are working hard on getting the false positive rate down. The false positive will be weeded-out quickly with the adoption of WinMHR’s ‘Report a False Positive’ feature.
Wouldn’t it make more sense for Microsoft to simply come out with authenticated hashes for legitimate system files and applications instead? Anything else found should be considered suspect until proven otherwise?
Speaking of which, check out Shadowserver,org’s Binary Whitelisting Service:
http://bin-test.shadowserver.org/
SANS has similar in beta:
http://isc.sans.edu/tools/hashsearch.html
Well, with the SANS product, it appears that you get two for the money.
Per your above link:
“In addition to the NIST database, we also run a test against the Team Cymru Hash Registry. It covers malware. If a match is found we will post a link to the respective page at Threatexpert.com (only for MD5 hashes right now).”
Brian, I do hope you will let us know when this program is available.
Which is worse? … To be geeky or stupid?
If you place your hand on a hot stove and get burned, will you continue to place your hand there?
Why then do so many people continue using such obviously flawed and inferior operating systems from Microsoft?
Ubiquity is not an indicator of quality or popularity in this case but rather a lack of choice and education.
Great strides have been made over the years to make the “geeky” alternatives user friendly for all and if free software wasn’t enough reason to at least try it, I don’t know what would convince you.
Nor do I know why so many continue to pound their heads against the Microsoft wall.
Let’s break it down; Jack buys a machine with Windows, continuously gets infected, has to buy various anti-this and anti-that to get a false feeling of security which in reality he will never be secure because this is a cat and mouse game over the security of inferior products where the mice always have the advantage.
No matter how many products and methods are released to “Protect” Jack, the mice reverse engineer said products and have all the answers to what and how the cats are searching for.
Naturally, the mice will stop using the same techniques and always have something new and temporarily untraceable to infect Jack with.
The success rate that security products boast is directly related to the amount of OLD malware, viruses and Hashes still traveling around the net infecting people.
Over the years of Microsoft’s rein Jack has spent more money on security products, repairs, licenses, and forced hardware upgrades than he can account for.
In the words of Homer Simpson… Dohhh!
Futility Fu”til`i*ty, n. [L. futilitas: cf. F. futilit[‘e].]
The quality of producing no valuable effect, or of coming to nothing; uselessness.
…
Every person I have turned on to LINUX has never had one problem and are very grateful.
Including those who are completely computer illiterate.
Here is your homework:
Security Report: Windows vs Linux
http://www.theregister.co.uk/2004/10/22/security_report_windows_vs_linux/
Linux vs. Windows Viruses:
http://www.theregister.co.uk/2003/10/06/linux_vs_windows_viruses/
Related Searches:
http://search.theregister.co.uk/?q=windows+linux+viruses
http://search.theregister.co.uk/?q=windows+vs+linux+viruses&site=&psite=0
And, last but not least, a Source of M$ relief:
http://www.ubuntu.com/
Windows vs. Linux… windows is like an automatic transmission car, easier to use just turn it on and go.
Where as Linux is like a standard transmission car, you use a command line a.k.a clutch. To each their own and what they prefer to use.
Will WinMHR has command line version or command line support?
It already does using ‘whois’, ‘dig’, etc.
http://www.team-cymru.org/Services/MHR/
The Cymru website says WinMHR is coming soon. Where did you download it from ?
hello, I have a question about winmhr.
when I scan a big file, for exemple a 5.49GB win7.vdi file ( virtualbox disk ) it returns the md5 hash (
43ae6879c359169620da3a937f00a12f
) and it says “not detected as malware” but how is that possible ? this file is unique and has never been published on the internet. Does this mean that when a md5 hash is not in the database it’s just classified in “not detected as malware” ? This is no very serious. And what if there really was a virus inside ?
Please explain things to me.
answer from winmhr team:
Hello,
Thanks for using WinMHR!
It seems like you are scanning a disk image that contains your operating
system. WinMHR works by calculating the digest (MD5/SHA-1) of each
file, then checking that digest against or database of known malware.
It is treating that .vdi image as one file.
In your case, please mount the .vdi file so you can get at the Windows
file structure; then scan those files using WinMHR. Alternatively, use
VirtualBox to run that .vdi file, then install and run WinMHR from
inside that instance.
If you have any more feedback, comments, or questions, please send them
to feedback@winmhr.com.
Thanks,
Chad Bibler
my second answer:
wow fast 🙂
ok thanks for the clarification. I think you should add a new feature in winmhr, whenever a file is scanned and the md5 hash that is returned is not in the malware database you should offer an option to upload it to your server to scan it, and not return “not detected as malware”. because the fact that the md5 is not in your database doesn’t mean that it’s not a virus.
but I imagine it’s not possible because of server costs.
Anyway I think winmhr is a very interesting tool and I hope that its development will continue for years.
winmhr tem second answer:
Hello again,
Thanks for the feature request, and we are working on implementing the
ability for users to send files to us for additional inspection. We
don’t have a schedule yet for that feature, but keep tuned!
Thanks,
Chad Bibler