Supermarket giant Kroger Co. is the latest major business to disclose that its customer email list has fallen into into the hands of spammers and scam artists.
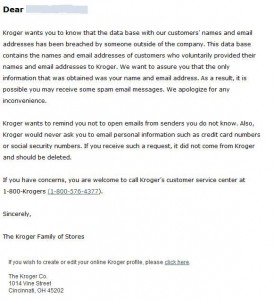 In a communication sent to customers today, Kroger said its database of customer names and email addresses had been breached by someone outside the company. A call to the 1-800 number included in the missive connects to a lengthy recorded message warning customers about an increase in phishing attacks and spam targeting Kroger customers. Kroger’s media relations folks have not yet returned calls seeking comment.
In a communication sent to customers today, Kroger said its database of customer names and email addresses had been breached by someone outside the company. A call to the 1-800 number included in the missive connects to a lengthy recorded message warning customers about an increase in phishing attacks and spam targeting Kroger customers. Kroger’s media relations folks have not yet returned calls seeking comment.
The disclosure comes close on the heels of similar acknowledgments from McDonalds, Walgreens, Honda, deviantART, and most recently TripAdvisor and play.com. They appear to be the lingering fallout from a series of sophisticated, targeted attacks against dozens of email service providers (ESPs) that manage communications between some of the world’s top brands and customers that have opted-in to receive messages from these companies.
In most cases, the spam sent to customers of these companies pushed recipients to buy dodgy services and software. It’s not clear which email service provider may have leaked the Kroger customer information, but it seems that few — if any — ESPs have escaped injury.
 According to the CEO of play.com, that breach involved an attack against marketing firm SilverPop Systems. SilverPop did not respond to requests for comment.
According to the CEO of play.com, that breach involved an attack against marketing firm SilverPop Systems. SilverPop did not respond to requests for comment.
I called SilverPop today because a source forwarded a junk email message to me that appears to have been sent directly from SilverPop’s internal email systems (the text and headers from that email are here). The missive is an offer to download Adobe Reader, and recipients who click the included link are brought to a page that tries to charge them for the free software. This approach is almost identical to the scam emails sent out directly after the successful attacks against email services providers in November of last year.
My initial reporting on this attack against the email service provider industry indicates that most of the providers in the industry had client customer data stolen. I’m left wondering how long we have to keep watching this stream of disclosures trickle out, and how long it might take for email service providers like SilverPop to get their houses in order?
Update, 6:55 p.m. ET: A story in the Cincinnati Business Courier says the breach occurred at Epsilon, an email service provider headquartered in Dallas.
Update, 9:45 p.m. ET: Several readers have reported receiving similar disclosures today from gift store Brookstone.
Update, Apr. 2, 9:35 a.m. ET: Another reader wrote in to say he’d received a notification (PDF) from U.S. bank, which said the financial institution’s customer email list was stolen due to a breach at Epsilon.
Update, Apr. 2, 5:41 p.m. ET: The Epsilon breach extends to JP Morgan Chase, McKinsey Quarterly, and apparel chain New York & Co, according to new disclosures from those companies.
Update, Apr. 2, 8:45 p.m. ET: And the list of disclosures continues: The Home Shopping Network just issued a release (PDF) saying its customer list was compromised via the Epsilon breach.
Update, Apr. 2, 9:00 p.m. ET: Looks like we can add TiVo to the list, although the company’s disclosure doesn’t say which email service provider was responsible.
Update, Apr. 3, 9:11 a.m. ET: According to SecurityWeek.com, the brands impacted by the Epsilon breach include Capital One, City Market, Dillons, Jay C, Food 4 Less, Fred Meyer, Fry’s, King Soopers, Marriott Rewards, QFC, Ralphs, Ritz Carlton, and Smith Brands and Walgreens.




Thoughts on phishing;
Many will stress the caveat on navigating to the site independent of email link.
However; I should think LastPass would not work on a phished URL, unless the certificate were stolen.
I invite your criticism.
That sounds right to me, JCitizen. I use LastPass, and unless the domain matches exactly, it disclaims any knowledge of my login credentials.
However, this doesn’t protect you from other nastiness that might be lurking on that bad URL.
I’d suggest defense in depth. . . stay vigilant, and if that fails, your NoScript/AV/LastPass/etc. should protect you.
Good advice barefootwriter;
They say WinPatrol can detect the injection of any Zeus variant into the start-up folder. I doubt it could stop it, but all it would have to do is give me the alarm. Then I could use CCleaner to blow the start-up folder away.
I use a lot of different technology to arrive somewhere close. Nothing is perfect. Things are developing so rapidly, my defense, tomorrow, may not look at all like it does presently!
What keeps being missed in these notices to affected customers is that they need to be very careful in the future about emails coming the company.
This letter, and an almost identical one I recently received from TripAdvisor.com, tell people that only their name and email address were compromised, and at the most they may experience an increase in the amount of SPAM mail they receive. Sounds harmless and I don’t need to worry.
So Joe/Jane consumer think nothing of it when a fews days or weeks later they receive what appears to be an email from the same company with a PDF file attached, or a link to a customer-satisfaction survey. Only the PDF is carrying an exploit, or the link takes them to SQL-injection compromised site. Game over, you’re p0wned.
These companies are going to have to start taking on some of the responsibility in keeping this from happening. A simple (read free) apology email doesn’t cut it.
“So Joe/Jane consumer think nothing of it when a fews days or weeks later they receive what appears to be an email from the same company with a PDF file attached, or a link to a customer-satisfaction survey. Only the PDF is carrying an exploit, or the link takes them to SQL-injection compromised site. Game over, you’re p0wned.”
I think you’re right. Spoofing email headers was one of the first games the spammers learned. Have you ever dumped your spam folder into a spreadsheet and tried to analyze the sender and subject data to make your own spam filters? I did that for a couple of years before I gave up in disgust. You can tell that it’s the same people sending hundreds of the same messages from dozens of different domains, and some of those domains are legitimate businesses and organizations who would never send that kind of email to anyone. Or all the spam sent to you from your own email addresses. I don’t know how to do it, but they do. Probably it’s a custom made email client that allows them to specify what’s in the headers.
Thanks for the heads-up. I got the Kroger email just seconds after the notice that this article had posted. Good for a chuckle, but I’ll be watching for anything “they” send me now.
I received a very similar email breach notification from Brookstone today. I’m thinking they were likely to be utilizing the same provider as Kroger (Epsilon). Below is the full copy of the notification:
Dear Valued Brookstone Customer,
On March 31, we were informed by our e-mail service provider that your e-mail address may have been exposed by unauthorized entry into their system. Our e-mail service provider deploys e-mails on our behalf to customers in our e-mail database.
We want to assure you that the only information that may have been obtained was your first name and e-mail address. Your account and any other personally identifiable information are not stored in this system and were not at risk.
Please note, it is possible you may receive spam e-mail messages as a result. We want to urge you to be cautious when opening links or attachments from unknown third parties.
In keeping with best industry security practices, Brookstone will never ask you to provide or confirm any information, including credit card numbers, unless you are on our secure e-commerce site, Brookstone.com.
Our service provider has reported this incident to the appropriate authorities.
We regret this has taken place and for any inconvenience this may have caused you. We take your privacy very seriously, and we will continue to work diligently to protect your personal information.
Sincerely,
Brookstone Customer Care
It was Epsilon.
Notice, you can login to their DREAM system from the internet. I wonder if admins can login from that page?
My imagined scenario: Epsilon employee gets spear-phished, and his account creds are compromised.
Attacker then uses these creds to login to the public internet site, which Epsilon hasn’t restricted from use by admins.
This admin has access to multiple company accounts. Attacker proceeds to download the email lists from all these vendors.
This seems the most likely attack scenario. It begs the question: does Epsilon care about their customer data, if the admins can login from the internet? Their customers have to trust SOMEBODY within Epsilon. They seem to have not respected that trust.
This reminds me of the compromise to my State’s hospitals and emergency services. In October of 2010 I received a notice of personal information compromise that was discovered in October of 2009. Personnel information for thousands of State emergency medical service related personnel were stolen. A whole year before the compromise was discovered?
The flaw? The servers handling the sensitive information was allowed Internet access for those authorized to input/output our information into the system. Smart huh?
This is the same agency whose staff members were caught using servers for personal use by visiting porn and gaming sites in 2008…..Hello!
This is what you get when you a trust a third party to handle your email marketing.
If you want to do it well, do it yourself.
p.s Reply to my email Brian. I got something interesting for you.
I got a Brookstone notification. The only problem is I have never used Brookstone on line or have ever given them my email address. The email address used is a msn one. I have gotten a lot of spam from the msn account. I just assumed they got the email there.
I received a similar disclosure from US Bank at 7:38 AM ET today (April 1). The vendor was Epsilon Interactive.
More on the US Bank notification from Boise Weekly:
http://www.boiseweekly.com/CityDesk/archives/2011/04/02/chase-us-bank-customers-warned-of-e-mail-security-breach
It’s ironic that you refer to “opt-in” and “Email Service Provider” (ESP). The first term is a practice that is required but often ignored. The second term is a whitewash of insulting spin from a dirty industry.
From the point of view of an email administrator or one who runs honeypots with spam trap addresses, operations like SilverPop, Epsilon Interactive, and Broadwick Corp. AKA iContact (compromised in January 2010) are more properly known as “spammers for hire”. They send unsolicited and substantively identical email in bulk quantities. There is no actual opt-in involved.
SilverPop and Epsilon Interactive (Bigfoot Interactive) are some of the more interesting offenders. They’ve been very aggressive at both their spamming volume, and their smears against critics of their spamming. It’s quite a dirty business they’re in.
That they’ve been owned is not surprising. Still, the essential nature of what’s done to the addresses they hit in the course of their normal business hasn’t changed all that much after the owning.
Its important to remember, many companies use these vendors for managing promotional campaigns that consumers have opted in for. The promotional mail opt-in may be checked ‘bt default’, but they’re coming after consumers have registered an account with the vendor.
It’s also important to remember that in many (even most) cases, the victim didn’t give permission, and didn’t opt-in.
Permission cannot be assumed. Nor can it be unilaterally declared in fine print that no-one ever reads. It must instead be deliberately and knowingly given by the address owner.
These companies can’t be bothered to do it right, so they end up spamming. Understandably, this gets them blacklisted. Rather than fix their practices, however, they dodge the problem by finding a cutout to take the heat. They outsource the spamming to a different IP range under the control of a firm that’s good at PR.
And thus they end up shopping information given them in confidence (names linked to email addresses) over to sleazy and careless spammers for hire, thereby getting their customers compromised. Excellent customer service all around!
@Christopher & Richard
Makes you wonder whether this “breach” was from an “outside attacker” at all. If it was staged to look like one by an insider, they’ve just harvested all those valid email addresses to do whatever they want with. I wonder how many of those email addresses can be linked to shopping, preferences and service subscription profiles in the businesses’ databases? Even though the businesses maintain these profile databases in their own domains separate from the email service, how secure do you think the businesses’ databases are? Particularly the ones that don’t keep credit card data in them.
If their true business is spamming, they wouldn’t have a drop of respect for either the employers or their customers.
The fact that these companies use a third-party service to handle their customer data to begin with means that they don’t give a hoot about the privacy and security of the information they have on their customers. Instead, they would rather have the blame directed elsewhere if something were to happen.
It would be foolish to provide any kind of personal information about yourself to any of these companies.
AlphaMack,
“The fact that these companies use a third-party service to handle their customer data to begin with means that they don’t give a hoot about the privacy and security of the information they have on their customers.”
That *might* be a little unfair to the companies. I say *might* because on the one hand, they’re all probably just following industry standards in how they conduct their business, and hiring 3rd party companies seems to be the prevailing wisdom for non-technical companies to handle their IT functions. It’s very likely that they haven’t thought through the implications for their relationships with their customers. Or they trust that the 3rd parties they hire will do it for them.
On the other hand, we do live in a technological age, and perhaps it’s time for these companies to hire their own technical staff who can think through these problems and find their own unique solutions for them. A similar thing happened when the automobile was invented. Before there were cars and trucks, all businesses handled their transportation needs with horses, carts and carriages. Granted, the transportation of people and material objects is a considerably simpler set of operations than the technological transformation we’re going through today, but in the end what needs to happen is for companies to embrace the new technologies, just as in yesteryear companies switched from horses to gasoline.
It’s possible that companies may be a little confused by this. In the case of transportation, most of them hired it out, and whether the transpo was horse-drawn or gas-powered made little difference to them. Now perhaps we’re finding that with internet-based operations, it does matter whether it’s hired-out or handled in-house. Or at the very least, that something more than was previously expected needs to be known about the 3rd parties a company hires.
You’re making an apples and oranges comparison here. Transportation does not involve personal and private information which could have serious personal and financial consequences for the *customers* of these companies. What recourse does the consumer have except to not do business with them? If you have a Capital One CC, you can’t just opt out of their promos. Sure, you could close your account, but then your FICO will take a hit. The bottom line is that you can’t stuff the genie back into the bottle and hope that you won’t be exploited by the black hats behind this breach. Moreover, you can’t just say “Don’t be idiot and sign up for those club cards.” You and I may know not to give out personal information to these companies, but there are many, many more blissfully ignorant consumers out there who have no idea that their meatspace privacy is being compromised in cyberspace.
Since I can’t edit my previous post I want to add that I wasn’t trying to be harsh with my apples/oranges comment, and I know that you did emphasize that the transportation example was a simpler comparison, but we do not know if it is a matter of these companies needing to adapt or their indifference, especially when it comes to protecting sensitive information. Also while Epsilon stressed that only the names and e-mail addresses were breached, we still need to keep a critical eye on this incident. Was it really just that information and they’re being mum about the rest? We won’t know and this should remind the rest of us to be on guard with all of our personal information floating out there, not just our names and e-mail addresses.
Yes, I think times are more complex for all of us – companies and consumers – we all need to understand that life just isn’t as simple as it used to be. And more than that, we need to know and understand the specific ways that it’s become more complex.
I guess I’m a little inclined to cut everyone some slack, at least until we’ve all gotten up to speed with exactly what kind of world we now live in. So I’d come down on the side of thinking that the companies just didn’t know this could happen as the reason why they didn’t think it through.
But now, they should at least have a clue. We’ll see what they do with it.
OK, looks like the Tivo email system just joined the crowd:
Dear TiVo Customer,
Today we were informed by our email service provider that your email address was exposed due to unauthorized access of their system. Our email service provider deploys emails on our behalf to customers who have opted into email-based communications from us.
We were advised by our email service provider that the information that was obtained was limited to first name and/or email addresses only. Your service and any other personally identifiable information were not at risk and remain secure.
Please note, it is possible you may receive spam email messages as a result. We want to urge you to be cautious when opening links or attachments from unknown third parties.
We regret this has taken place and apologize for any inconvenience this may have caused you. We take your privacy very seriously, and we will continue to work diligently to protect your personal information.
A company that specializes in email communication should be expected to specialize in keeping mailing list data secure. They should have practices that are as good or better than the companies hiring them. Most companies don’t have enough awareness of proper bulk mailing practices to not muck things up for themselves and end up with a reputation for spamming.
That’s not to say there aren’t a lot of scummy spammers offering their services to companies that want to communicate with their customers, but that isn’t what we should expect or accept to be the case. If you can’t trust a company to choose a reliable customer contact contractor, you can’t trust them with your email address period. You can’t criticize them for looking for a third party company with the competence to help them do the job right.
I will withhold judgment in this case until I learn more about how the breach occurred. I will be the first to admit that a determined attacker could pwn me or anyone else if they chose to.
This is turning out to be much bigger than just Kroger and the other companies mentioned in the comments here. SecurityWeek has updated the list of companies compromised:
http://www.securityweek.com/massive-breach-epsilon-compromises-customer-lists-major-brands
Slashdot just picked up the article as well.
http://yro.slashdot.org/story/11/04/03/016215/Epsilon-Data-Breach-Bigger-Than-Just-Kroger-Customers-Data
i find it SO interesting that Epsilons “Browse Work” section in their case studies isn’t working: http://www.epsilon.com/Our-Work/p43-l1
might have not worked before but i highly doubt it.
Also was just forwarded a message that Disney Destinations sent out a breach notification letter.
Barclay Bank of Delaware’s email this morning.
————————————-
Dear Customer,
Re: Important information regarding a breach to the privacy of your email address.
Barclays Bank of Delaware is the bank behind your credit card referenced above. We have been informed by Epsilon, a marketing vendor we use to send emails to customers, that someone outside their company gained unauthorized access to files in their systems that included your email address. This has affected many of our credit cards under our various co-brands, including the brand on your card.
Epsilon has assured us that the only information that was obtained was your name and email address. Please be assured your account and any other confidential or personally identifiable information were not at risk.
It is possible you may receive spam email messages as a result which could potentially ask you for additional information about your account. Please note, Barclays will never ask you in an email to verify sensitive information such as your full account number, Username, Password or Social Security Number. Therefore, any email which does so should be treated suspiciously, even if it looks like it comes from Barclays. As a reminder, we urge you to be cautious when opening links or attachments from unknown third parties.
Barclays is one of many companies affected and so you may receive similar notifications from other companies.
Please visit the “Privacy and Security” section at our website http://www.BarclaycardUS.com for more information on protecting your personal information.
We sincerely regret this has taken place and for any inconvenience this may have caused you. Barclays is committed to protecting customers against the misuse of their personal information and we take security issues very seriously. We vigorously monitor the security of our systems and require all third party vendors to adhere to strict security and privacy policies and procedures.
Please know that a full investigation of this matter is under way by Epsilon and we will continue to work diligently to protect your personal information.
If you have any questions or need further assistance, please call our customer care center at the phone number on the back of your credit card.
Sincerely,
Chief Privacy Officer
Barclays Bank of Delaware
Information Security Officer
Barclays Bank of Delaware
Here is the Disney Destinations email, sent out 4/3 around 7:00 am CDT
Dear Guest,
We have been informed by one of our email service providers, Epsilon,
that your email address was exposed by an unauthorized entry into that
provider’s computer system. We use our email service providers to
help us manage the large number of email communications with our
guests. Our email service providers send emails on our behalf to
guests who have chosen to receive email communications from us.
We regret that this incident has occurred and any inconvenience this
incident may cause you. We take your privacy very seriously, and we
will continue to work diligently to protect your personal information.
We want to assure you that your email address was the only personal
information we have regarding you that was compromised in this
incident.
As a result of this incident, it is possible that you may receive spam
email messages, emails that contain links containing computer viruses
or other types of computer malware, or emails that seek to deceive you
into providing personal or credit card information. As a result, you
should be extremely cautious before opening links or attachments from
unknown third parties or providing a credit card number or other
sensitive information in response to any email.
If you have any questions regarding this incident, please contact us
at (407) 560-2547 during the hours of 9:00 am to 7:00 pm (Eastern Time)
Monday through Friday, and 9:00 am through 5:00 pm (Eastern Time)
Saturday and Sunday.
Sincerely,
Disney Destinations
“Epsilon sends over 40 billion emails annually and counts over 2,500 clients, including 7 of the Fortune 10 to build and host their customer databases.”
Hmmmmmmmm! How much is spam to customers that were opt-in by default? I’m beginning to dislike Epsilon. Bordering on a legal Rustock.
The euphemism “opt-in by default” is great. Normally I just call that noisome practice “slam and spam”.
I’ll have to use “opt-in by default” alongside “email deployment” and similar beauties.
2500 clients? And how many have admitted to it so far?
Add AbeBooks to the list. Received 7 minutes ago:
Epsilon Informs AbeBooks of E-mail Database Breach
We have been informed by Epsilon, a third-party vendor we use to send e-mails, that an unauthorized person outside their company accessed files that included e-mail addresses of some AbeBooks customers. Epsilon has advised us that the files that were accessed did not include any customer information other than email addresses.
As a reminder, AbeBooks will never ask customers for personal or account information in an e-mail. Please exercise caution if you get any emails that ask for personal information or direct you to a site where you are asked to provide personal information.
barefootwriter quoted AbeBooks as saying:
“Epsilon has advised us that the files that were accessed did not include any customer information other than email addresses.”
Yeah, sure. What else should the spammer say to the ones he/they just robbed? After all, valid email addresses of known consumers who spend money on the internet are no big deal.
Add Ameriprise Financial to the list…
We were recently notified by Epsilon, an industry-leading provider of email marketing services, that an unauthorized individual accessed files that included some of our client and consumer information. Epsilon sends marketing and service emails on our behalf but does not have access to sensitive client data such as social security numbers. They have assured us that only names and email addresses were obtained. We take your privacy very seriously and want you to be aware of this.
You are receiving this because you have in the past received a communication from Ameriprise. If you receive an email that appears to be from Ameriprise asking for personal or financial information, do not respond. Instead, please immediately forward the email to us at: anti.fraud@ampf.com.
Consider these tips to help protect your personal information online:
Don’t email personal or financial information. Regular email is not a secure method of transmitting personal information. Some companies, including Ameriprise Financial, offer a secure email service that you can use when you need to exchange sensitive information.
Don’t reply to or click on links in email or pop-up messages that ask for personal information. Legitimate companies will not attempt to collect personal information outside of a secure website. If you are concerned about your account, contact the organization mentioned in the email or pop-up.
Use anti-virus and anti-spyware software and a firewall. Some phishing emails contain software, such as spyware, that harm your computer or track your activities on the Internet. Anti-virus software and a firewall can protect you from inadvertently accepting such unwanted files.
Use caution when opening attachments or downloading files from email. These files can contain viruses or other software that can weaken your computer’s security.
If you previously unsubscribed from promotional emails from Ameriprise, that will continue. The security of your information is very important to us. If you have questions or concerns, visit our Privacy and Security Center on ameriprise.com.
Sincerely,
Ameriprise Financial
Add Home Depot (Citibank) to the list. Just received the following email:
An Important Message Regarding Your The Home Depot® Consumer Credit Card, Issued By Citibank (South Dakota), N.A
Recently, Citi was notified of a system breach at Epsilon, a third-party vendor that provides marketing services to a number of companies, including Citi. The information obtained was limited to the customer name and email address of some credit card customers. No account information or other information was compromised and therefore there is no reason to re-issue a new card.
etc.
Oh look.. an email from a Marketbay affiliate again. How many times have we seen that lately?
I got the same notice from Robert Half as well – seems a lot of different companies put their trust (and money) to Epsilon just to find out it wasn’t worth it. With so many companies going to them to keep their data, it’s no wonder they were targetted though. It gives the attackers a wide range of poptential victims.
As I’ve now received the email from 2 different companies alerting me to the breach… I really hope they’re right and nothing other than email was lost – I never click on anything from an email anyway (go directly to their site), so I can survive just deleting more junk… and I hope that the majority of those impacted are the same… but if it goes deeper than email, there’s a whole lot more at risk than extra spam and possibly infected computers!
Here is the Robert Half notification email:
From: Robert Half
Dear Valued Customer,
Today we were informed by Epsilon Interactive, our national email service provider, that your email address was exposed due to unauthorized access of their system. Robert Half uses Epsilon to send marketing and service emails on our behalf.
We deeply regret this has taken place and any inconvenience this may have caused you. We take your privacy very seriously, and we will continue to work diligently to protect your personal information. We were advised by Epsilon that the information that was obtained was limited to email addresses only.
Please note, it is possible you may receive spam email messages as a result. We want to urge you to be cautious when opening links or attachments from unknown third parties. We ask that you remain alert to any unusual or suspicious emails.
As always, if you have any questions, or need any additional information, please do not hesitate to contact us at customersecurity@rhi.com.
Sincerely,
Robert Half Customer Care
Robert Half Finance & Accounting
Robert Half Management Resources
Robert Half Legal
Robert Half Technology
The Creative Group
2011 Robert Half International, Inc. An Equal Opportunity Employer. For more information, please visit roberthalf.us.
If you prefer not to receive future general email broadcasts from Robert Half International, please click here to unsubscribe. You may also mail your unsubscribe request to the address below. Thank you.
Robert Half | Attn: Marketing | 2884 Sand Hill Road, Suite 200 | Menlo Park, CA 94025 USA
The headers (I got one too) indicate that the message was sent by…. ta Dah!… Bigfoot. I haven’t exchanged any correspondence with Robert Half in years, so it’s more than ironic that this is the first e-mail I’ve received from Bigfoot on their behalf (it’s entirely possible that it all ends up tossed as spam).
More amusing than the headers, is this:
If you prefer not to receive future general email broadcasts from Robert =
Half International, you can copy and paste the link below into your brows=
er.
http://email.rhi.com/…
You may also mail your request to the address below.
Who owns email.rhi.com? You guessed it:
m3047@hera:~> dig email.rhi.com
[…]
;; ANSWER SECTION:
email.rhi.com. 3600 IN A 208.70.143.2
;; AUTHORITY SECTION:
email.rhi.com. 3600 IN NS ns3.rhalf.com.
email.rhi.com. 3600 IN NS ns4.rhi.com.
email.rhi.com. 3600 IN NS ns5.rhi.com.
email.rhi.com. 3600 IN NS ns.rhalf.com.
email.rhi.com. 3600 IN NS ns2.rhalf.com.
email.rhi.com. 3600 IN NS ns3.rhi.com.
;; ADDITIONAL SECTION:
ns3.rhi.com. 3600 IN A 204.75.80.155
ns4.rhi.com. 3600 IN A 204.75.80.156
ns5.rhi.com. 3600 IN A 204.75.84.160
[…]
m3047@hera:~> dig -x 208.70.143.2
[…]
;; QUESTION SECTION:
;2.143.70.208.in-addr.arpa. IN PTR
;; ANSWER SECTION:
2.143.70.208.in-addr.arpa. 86400 IN PTR drd.bfi0.com.
;; AUTHORITY SECTION:
143.70.208.in-addr.arpa. 86400 IN NS ns.bigfootinteractive.com.
143.70.208.in-addr.arpa. 86400 IN NS ns1.bigfootinteractive.com.
;; ADDITIONAL SECTION:
ns.bigfootinteractive.com. 1477 IN A 206.132.3.8
ns1.bigfootinteractive.com. 1477 IN A 66.7.58.148
[…]
Thanks for posting up the email, Paul! I just got it, too, and wasn’t sure how to forward on to here. Of course a quick copy & paste was too easy for me to think of (duh).
I wonder how much Epsilon really coughed up…
I just received an e-mail this morning from Best Buy Rewardzone stating the same thing. My e-mail address was exposed. Here is the first paragraph.
Dear Valued Best Buy Customer,
On March 31, we were informed by Epsilon, a company we use to send emails to our customers, that files containing the email addresses of some Best Buy customers were accessed without authorization.
Add Best Buy to the list, if not already there. Got my notice this AM…Epsilon breach, says only email addresses were obtained (not even names).
Robert Half can be added to this list as well..
Please add Citi credit card services to this list. Received a notification about the Epsilon breach this morning. Thank you!
@Kjohnson and Zippi — Please see today’s story on this breach, which includes an updated list of affected companies.
http://krebsonsecurity.com/2011/04/epsilon-breach-raises-specter-of-spear-phishing/
Obviously, with 2500 clients, each of whom probably had hundreds or thousands of registered users, this is/was a hacker and spammer’s dream. They may have spent months or years trying to get in to exfiltrate all those live email addresses. What a treasure trove.
And let’s also remember that a company like McDonald’s wants to drive consumers to their website and restaurants so they try to get folks to sign up with the promise of coupons or specials or deals. It is common practice for these non-technical companies to outsource the emailing of said coupons to their customers who signed up. You want to keep track of your Monopoly pieces at McDonald’s website, so you sign up for their emails. Hence, regardless of who actually sends you the email/coupons/promotions (Epsilon), you have opted in with your McDonald’s registration.
So, further, Epsilon is the place to hack into if you want the customer information. But I agree with two other sentiments posted here– 1)Epsilon should have done a better job protecting that customer data and 2)A determined hacker will get in, eventually.