An online criminal enterprise, as tightly structured as any legitimate business corporation, was exposed in 2010. Emails and documents taken from employees of ChronoPay — Russia’s largest online payments processor — were shared with a select group of law enforcement agencies and with KrebsOnSecurity.com. The communications provide the strongest evidence yet that a notorious rogue online pharmacy and other shady enterprises are controlled by ChronoPay executives and employees.
The leaked ChronoPay emails show that in August 2010 co-founder Pavel Vrublevsky authorized a payment of 37,350 Russian Rubles (about $1,200) for a multi-user license of an Intranet service called MegaPlan. The documents indicate that Vrublevsky used the service to help manage the sprawling projects related to ChronoPay’s “black” operations, including the processing of payments for rogue anti-virus software, violent “rape” porn sites, and knockoff prescription drugs sold through hundreds of Web sites affiliated with a rogue online pharmacy program Rx-Promotion.com.
ChronoPay employees used their MegaPlan accounts to track payment processing issues, order volumes, and advertising partnerships for these black programs. In a move straight out of the Quentin Tarantino film Reservoir Dogs, the employees adopted nicknames like “Mr. Kink,” “Mr. Heppner,” and “Ms. Nati.” However, in a classic failure of operational security, many of these folks had their messages automatically forwarded to their real ChronoPay email accounts.
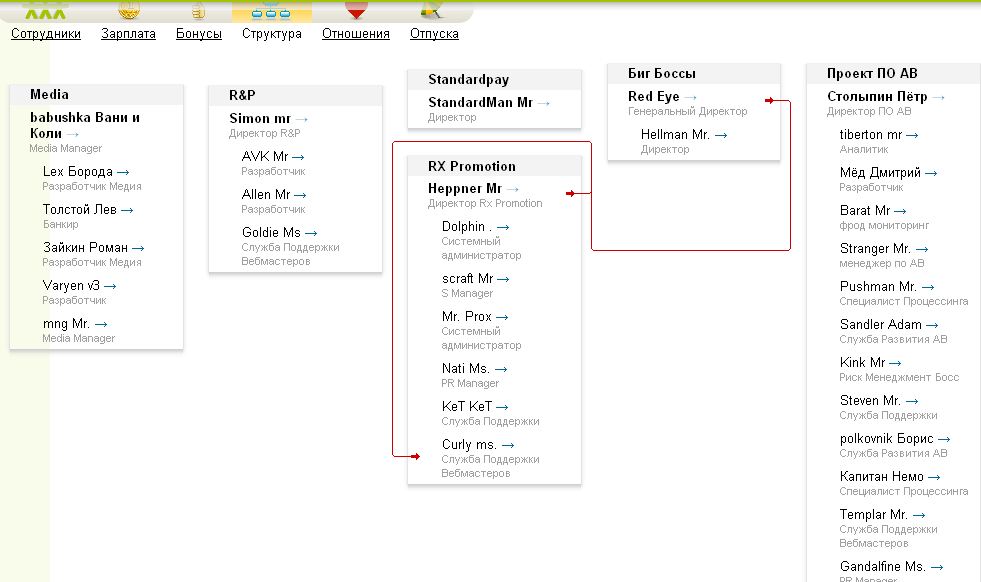
MegaPlan offers an application that makes it simple for clients to create organizational charts, and the account paid for by ChronoPay includes a chart showing the hierarchy and reporting structure of its dark divisions.
Black Ops, Dark Divisions
Media: This division oversees ChronoPay clients and services that specialize in selling steeply discounted MP3 music files. ChronoPay saw the profit potential of dodgy music resellers early on, and is probably best known for being the processor for AllofMp3.com, a controversial Russian online music sales company. The wrath of the U.S. entertainment industry in 2006 created an international trade dispute between Russian and the United States.
R&P: Short for “Red & Partners,” this division was founded by Vrublevsky early in his career, and is responsible for processing payments for adult Web sites that specialize in violent “rape” photos and videos. ChronoPay emails show company slush funds routinely are used to process payments for the infrastructure used by dozens of these extreme adult sites. ChronoPay emails reveal that the director of R&P — listed in the graphic above as “Mr. Simon” — is ChronoPay employee Alexandr Alyushin.
StandardPay: A company founded by Vrublevsky that specializes in offering payment solutions for the extreme adult sites. Processing payments for pornography can be tricky in many countries, including Russia — where it is technically illegal to produce or sell pornography. “Mr. StandardPay” is a Russian named Mikhail Mikryukov, who uses the nickname “Human.” Along with RedEye (Vrublevsky), Human is an administrator of Crutop.nu, a 8,000 member Russian adult Webmaster forum that also is used to recruit affiliates for Rx-Promotion and rogue anti-virus sales.
Big Bosses (“биг боссы”): ChronoPay CEO Pavel “RedEye” Vrublevsky, and Yuri “Hellman” Kabayenkov. ChronoPay emails show that these two men are 50/50 partners in the pharmacy program Rx-Promotion.
Rx-Promotion: ChronoPay emails and documents show that “Mr. Heppner” is Stanislav Maltsev, a former Russian police investigator previously responsible for heading up a criminal investigation of Vrublevsky in 2007. That investigation remains open but appears to have gone nowhere, and Maltsev now works directly for Vrublevsky.
An individual listed in the ChronoPay MegaPlan account under the alias “Ms. Curly” does not appear to be a ChronoPay employee. Curly is named as a customer support representative for Rx-Promotion.com, and a user “Curly” also is listed as the support lead at the Rx-Promotion forum for affiliates of the rogue pharmacy program. Curly appears to be a pseudonym for Katya Ivanova, a slender, curly-haired redhead from Moscow shown in this this profile on Vkontake, a major Russian social networking site.
ChronoPay emails show that Ms. Nati, listed in the MegaPlan chart above as the public relations manager for Rx-Promotion, is a ChronoPay employee named Natalia Miloserdnaya. Members using the names Curly, Nati and Hellman also can be seen fielding questions from Rx-Promotion affiliates in that organization’s online forum.
Project for AV: In previous investigations, I’ve shown that ChronoPay has consistently been among the biggest processors of rogue anti-virus software or “scareware.” Last month, I blogged about ChronoPay paying for several domains that were used in recent Mac Defender attacks. A study released this week (PDF) by researchers at the University of California, Santa Barbara looked at three rogue anti-virus distribution services, and found they all processed payments through ChronoPay.
When I visited Vrublevsky in Moscow in February, he told me of plans to launch a ChronoPay-branded anti-virus solution, and many of the documents included in this section of ChronoPay’s MegaPlan installation are technical papers referencing the development of different anti-virus software modules. The documents suggest that the company has hired programmers to reverse-engineer the free version of the commercial anti-malware product Malwarebytes.
Banking on Indifference
Another area of ChronoPay’s MegaPlan installation shows contact information for strategic and advertising partners. Among them is a bank in Azerbaijan called Azerigazbank that until recently processed Visa and MasterCard payments for Rx-Promotion customers, among a half-dozen other rogue Internet pharmacy programs. This is not your everyday, risk-averse financial institution: AG Bank’s slogan loosely translates to “Options for the Rich,” and this bizarre commercial for their services features scantily-clad women on a yacht tossing handfuls of huge diamonds into the sea while helicopter gunships circle overhead.
According to a UC San Diego research paper (PDF) released in May that analyzed spam from more than 30 illicit online pharmacy programs, Rx-Promotion-branded pharmacy sites were the most actively promoted via spam. As I’ve noted in previous stories about Rx-Promotion, it is one of the few remaining pharmacy programs that sells prescription drugs (no prescription required) that are highly controlled in the United States, including addictive painkillers Valium, Percocet, Tramadol, and Oxycodone.
As the academic paper and my reporting make clear, the traditional methods of exposing these programs — “outing” the merchant banks and shining a spotlight on the main actors — has little effect when the organizers live in countries that willingly turn a blind eye to this activity. I’ve been eager to write more about this treatise since it was first featured in a New York Times story last month. In a future blog post, I will discuss the potential impact of the main policy alternative outlined in that paper: Convincing a handful of card-issuing banks here in the United States to stop processing payments for a handful of merchant accounts known to be tied to illicit online pharmacies.




Nice writ brian excellant work lol I have to change my nick name . Also it shows what the extent they will do to cripple
Malwarebytes .
Great post, Brian, with some excellent work.
One question: when you say that ChronoPay is working on its own anti-virus solution, do you mean something that is supposed to actually remove malware and stuff and not just scare people into believing they are infected?
I was supposed to be a real antivirus product that ChronoPay was thinking it would market and sell, not a fake av product.
Another sterling piece of investigative journalism. Truly outstanding!
Why can we not have more of your ilk doing this kind of proper journalism instead of the relentless and utterly pointless attention on which celebrity was in a state of undress last night?
Sigh…
“…Convincing a handful of card-issuing banks here in the United States to stop processing payments for a handful of merchant accounts known to be tied to illicit online pharmacies.”
Why is this so difficult? The US government was able to convince payment processors MasterCard, Visa, and PayPal to stop processing donations to WikiLeaks virtually overnight.
Reasons: 1. Money – even ill gotten money is money in the bank. and if you have to give it back – oh well in the mean time the banks have invested it and earned a bit on it.
2. WikiLeaks just p— off alot of people so its easy to agree not to process payments for them
Because that was a “national security” issue, whereas this is merely commerce.
This is the tip of the iceberg in terms of “national security” but non-IT people are too dumb to understand it yet
The massive amount of money involved is one reason. Another is that Wikileaks publishes any proof of corruption they get. They exposed a few banks already. Mastercard and Visa probably considered Wikileaks as much a risk to them as to “national security.”
USA maintains a Specially Designated National and Blocked Persons List; when and how such a list could include this type of criminal enterprise remains a question.
US treasury makes it easy to DL a file to integrate into payment processing so transactions and accounts can be identified. Name collisions and aliases make the job real hard but the criminals in this case make it easy as some of the accounts are fictitiously obvious.
This is not an IT issue but a criminal issue that involves IT.
Its not that these guys dropped from the sky and began their criminal careers with IT. More likely they were involved in other things and shifted into the IT space when they discovered it to be a perfect harvest of marks for their con games.
As for funding a reverse engineering of malwarbytes this really concerns me; its equivocal to digging a narco-tunnel under a national boarder or bankrolling narco-subs.
The next phase is quite possibly actual real intimidation, threats bribery and coercion of anti-malware programmers/developers. Either to stop their work or to turn them for the mafias benefits.
Hi Krebs. I saw some news about you and your friend. You have been arrested for frauding?
@hix, it appears Pavel and Chronopay reveal their character by the company they keep. Fraud-news.com has removed the article you mention and replaced it with this notice:
ARTICLE REMOVED
by
FraudNews
Published on 06-12-2011 05:31 PM
Note by the Admin of Fraud-News:
A fake article titled “Well-respected security researchers arrested in credit card ring” was posted by someone who gained unauthorized entry into fraud-news.com. The article contents have been removed as it was a malicious and deliberate post by an unidentified hacker with the intention of tarnishing the names of F-Secure chief security researcher Mikko Hyponnen and well-known security journalist Brian Krebs. We are investigating into this. More details to follow.
Get out the popcorn, folks, Chronopay is running scared.
Here is the cached image of the original page:
https://imageshack.us/f/17/fraudnewscom.jpg/
For your convenience, the text is as follows:
Well-respected security researchers arrested in credit card ring
by
FraudNews
Published on 06-12-2011 05:31 PM
Two well-respected security researchers have been indicted for running an organized credit card counterfeiting ring that netted more than 1,5 million stolen account numbers, the U.S. Secret Service said today.
Brian Krebs, 39 and his boyfriend, Mikko Hyppönen, 42, were arrested in June for trafficking in credit cards they allegedly fabricated using legitimate account numbers purchased online from other criminals.
Using legitimate companies to front with such as F-Secure and a blog called “Krebsonsecurity” they are believed to have been operating for years disguised as security researchers.
Investigators said they traced communications between Krebs — using the online screen name “BlazinKrabz” — and Hyppönen (Alias ‘WhiteHippo’) who authorities alleged were sending large payments to cyber crooks in Eastern Europe in exchange for tens of thousands of stolen credit card numbers.
Those numbers were then used to fabricate fake credit cards in several production centers throughout Finland and US.
Neither indictment includes this information, but a press release from the Secret Service said the men paid for the goods via Chronopay, an online payment service that is allegedy ran by Russian criminals.
Government documents indicate the counterfeit cards fetched a high price. According to a copy of the indictment, Krebs sold 50 fabricated credit cards with security features and counterfeit images to an undercover agent at a cost of $15 each.
The government alleges the ring was responsible for total fraud losses of more than $75 million.
If convicted, both could face sentences ranging from 17-and-one-half to 47 years in prison.
Below is a picture taken from an underground forum (Courtesy of Federal Bureau of Investigation)
>Hyponnen
Nobody can spell Mikko Hypponen’s name right 😛
(not poking fun at you, poster, but at Fraud news)
I’m guessing they don’t spell check stuff posted by hackers 😉
lmaooooooo! pavel thats you right?
Bunch of bullshit about ChronoPay again.
Krebs You get paid for this or what?
Chronodefenders attack! I think even a blindman can see now what is Chronopay). Great job.
Get ’em Brian ! Hopefully you can help make the Internet cleaner. You are like the Wikileaks of the Interwebs.
A++ reporting, Brian.
I don’t understand this Vrublevsky, he could well stick to legal or quasi-legal activities, such as processing payments from adult-sites operators and make sufficient money he would not be able to spend his entire life. Once you made the first few millions in forte currency, do one really need more to improve further one’s lifestyle ?
As it seems from some of the previous (negative) comments, Pavel or his “cronies” (no pun intended) are active in the comments section attacking Brian, perhaps they are willing to shed some light on why it was really necessary to expand into fake-antivirus and massive spam business….
He do have legal activities, but they are mostly unprofitable because to make such thing profitable you should work really hard. Even to make profitable illegal activities You should work hard, but not that hard. I think this is the answer.
@george, I’ve added some information in reply to the negative comments above that you mentioned.
@daddy, do you think antis are stupid enough to attack a site linked in your signature without checking out whether there’s any likelihood you actually own it?
Поздравляю, преступление раскрыто!