First, the good news: The past year has witnessed the decimation of spam volume, the arrests of several key hackers, and the high-profile takedowns of some of the Web’s most notorious botnets. The bad news? The crooks behind these huge crime machines are fighting back — devising new approaches designed to resist even the most energetic takedown efforts.
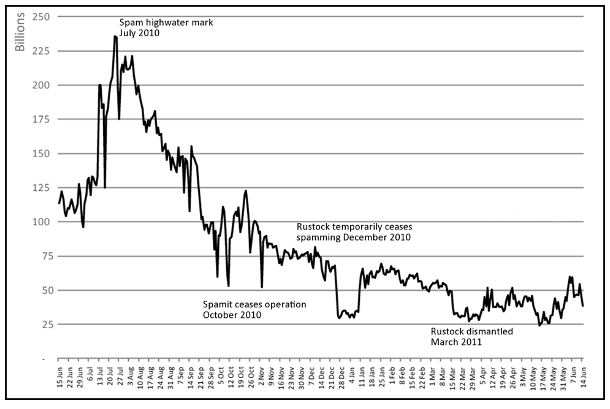
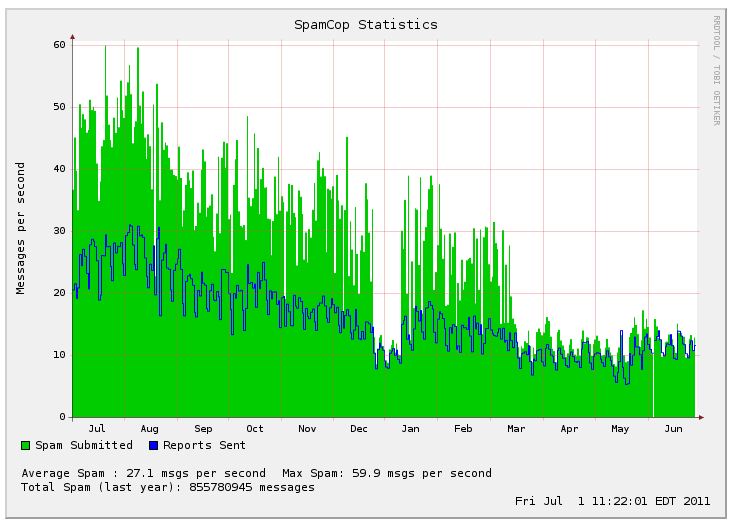
The volume of junk email flooding inboxes each day is way down from a year ago, as much as a 90 percent decrease according to some estimates. Symantec reports that spam volumes hit their high mark in July 2010, when junk email purveyors were blasting in excess of 225 billion spam messages per day. The company says daily spam volumes now hover between 25 and 50 billion missives daily. Anti-spam experts from Cisco Systems are tracking a similarly precipitous decline, from 300 billion per day in June 2010 to just 40 billion in June 2011.
There may be many reasons for the drop in junk email volumes, but it would be a mistake to downplay efforts by law enforcement officials and security experts. In the past year, authorities have taken down some of the biggest botnets and apprehended several top botmasters. Most recently, the FBI worked with dozens of ISPs to kneecap the Coreflood botnet. In April, Microsoft launched an apparently successful sneak attack against Rustock, a botnet once responsible for sending 40 percent of all junk email.
In December 2010, the FBI arrested a Russian accused of running the Mega-D botnet. In October 2010, authorities in the Netherlands arrested the alleged creator of the Bredolab botnet and dismantled huge chunks of the botnet. A month earlier, Spamit.com, one of the biggest spammer affiliate programs ever created, was shut down when its creator, Igor Gusev, was named the world’s number one spammer and went into hiding. In August 2010, researchers clobbered the Pushdo botnet, causing spam from that botnet to slow to a trickle.
But botmasters are not idly standing by while their industry is dismantled. Analysts from Kaspersky Lab this week published research on a new version of the TDSS malware (a.k.a. TDL), a sophisticated malicious code family that includes a powerful rootkit component that compromises PCs below the operating system level, making it extremely challenging to detect and remove. The latest version of TDSS — dubbed TDL-4 — has already infected 4.5 million PCs; it uses a custom encryption scheme that makes it difficult for security experts to analyze traffic between hijacked PCs and botnet controllers. TDL-4 control networks also send out instructions to infected PCs using a peer-to-peer network that includes multiple failsafe mechanisms.
Getting infected with TDL-4 may not be such a raw deal if your computer is already heavily infected with other malware: According to Kaspersky, the bot will remove threats like the ZeuS Trojan and 20 other malicious bot programs from host PCs. “TDSS scans the registry, searches for specific file names, blacklists the addresses of the command and control centers of other botnets and prevents victim machines from contacting them,” wrote Kaspersky analysts Sergey Golovanov and Igor Soumenkov.
The evolution of the TDL-4 bot is part of the cat-and-mouse game played by miscreants and those who seek to thwart their efforts. But law enforcement agencies and security experts also are evolving by sharing more information and working in concert, said Alex Lanstein, a senior security researcher at FireEye, a company that has played a key role in several coordinated botnet takedowns in the past two years.
“Takedowns can have an effect of temporarily providing relief from general badness, be it click fraud, spam, or credential theft, but lasting takedowns can only be achieved by putting criminals in silver bracelets,” Lanstein said. “The Mega-D takedown, for example, was accomplished through trust relationships with registrars, but the lasting takedown was accomplished by arresting the alleged author, who is awaiting trial. In the interim, security companies are getting better and better about working with law enforcement, which is what happened with Rustock.”
Attacking the botnet infrastructure and pursuing botmasters are crucial components of any anti-cybercrime strategy: TDSS, for example, is believed to be tied to affiliate programs that pay hackers to distribute malware.
Unfortunately, not many security experts or law enforcement agencies say they are focusing attention on another major weapon in battling e-crime: Targeting the financial instruments used by these criminal organizations.
Some of the best research on the financial side of the cybercrime underworld is coming from academia, and there are signs that researchers are beginning to share information about individuals and financial institutions that are facilitating the frauds. Recent studies of the pay-per-install, rogue anti-virus and online pharmacy industries reveal a broad overlap of banks and processors that have staked a claim in the market for handling these high-risk transactions. Earlier this week I published data suggesting that the market for rogue pharmaceuticals could be squashed if banks and credit card companies paid closer attention to transactions destined for a handful of credit and debit card processors. Next week, I will publish the first in a series of blog posts that look at the connections between the financial instruments used by rogue Internet pharmacies and those of the affiliate networks that push rogue anti-virus or “scareware.”




What we’re seeing at Barracuda is that although the volume of spam is down, if anything it’s malicious nature is worse. Perhaps you’re not getting the same about of viagra or rolex spam, but the spam that remains is deliberately targeting financial professionals and delivering Zeus, sometimes manually and even lately by using exploit kits. See our latest example at blog.barracuda.com
I think Dave is right. I am personally seeing more Nigerian-type emails and virus attachments just now than I did a year ago. The English is worse, and I think a new group of scammers must be trying their hand.
Regards,
I’ve read about this in a few places but no one is getting too specific with what “custom encryption” means exactly. Are they saying these guys created their own encryption algorithm? That would be beyond outrageous. Look at how complex and lengthy the process behind SHA3 is and it should show the major undertaking that is involved. The entity cranking this out must be financed like all get out. Otherwise a handful of Rainman-esque cryptogeeks would’ve torn this homemade encryption apart already.
The armchair conspiracist in me wonders if all this consumer level fraud is just a big huge (profitable) beta test for something bigger and more sinister. Probably I’m just watching too many Hollywood productions.
Russ,
Saddly it is not difficult to write reasonably secure crypto.
What is difficult is efficient highly secure crypto that is used for tens of billions of transactions an hour.
Not being funny a few minor modifications to DES software bassed on throwing a pair of dice will give you a better than reasonably secure solution.
Likewise cobbling together well known primatives in a conservative design will give you a high degree of security.
For instance take the rounds structure of DES modify it slightly to give different SBoxes and replace the static key expansion system with a dynamic one such as a modified version of ARC4.
One moodification to ARC4 you could easily make is to add a Blum Blum Shaub (BBS) random stream generator that outputs a bit every full round of the Iptr and either increments or decrements the Jptr depending on if the BBS bit is a one or zero.
Even simpler is too use a modified version of ARC4 to add whitenning (ie as a stream generator) to the data before DES encrypting.
Neither are particularly efficient but then neither is effectivly brakable currently with the resources available on the open market.
It is self-evident that they are trying to target people who have lots of money.
Does this mean that those of us who do not have lots of money, do not have e-commerce credit card stuff on our PCs, are relatively safe?
I guess not, we are still targets for being placed on bot nets.
What I’m talking about specifically is that we’re seeing messages that are crafted to appeal to financial professionals. Topics include wire transfers and business tax payments. Spam still goes out to everyone, but more and more it’s made to catch the eye of people that are responsible for a pile of money, like a controller or accountant.
Dear Brian, takedowns of botnets imho are just side-effects of Microsoft’s and Adobe’s security updates. If you plot those security updates into the charts you might find some indications. – While we have had noneffective botnet takedowns in the past that leaves the question about the driving force open.
I bet those are the same folks that motivated US government to discuss cybercrime with the russians. You know, the same folks that own the States and most of the rest of the world in terms of debts. => Targeting the financial instruments could be opposing their agenda…
Btw: You know you’re scripting on a blockbuster, don’t you? 😉
Hmkay, hide this away and pray I’m wrong… 😛
My machine running XP was recently crashing quite a bit and ultimately Microsoft’s crash disgnosis pointed to the Belkin Pre-N Adapter and to the supposed need to update drivers [no updates were available] and it then suggested removing the adapter and presto, no more crashes.
So after a number of years of reliable service SOMETHING precipitated a hardware failure in the adapter. Now Belkin has agreed to fire off a newer USB style adapter to me which I should get sometime next week, but am I right to presume that something like Brian is referencing would not cause a hardware failure in an adapter, which is clearly above the operating system.
Just how would one go about looking for this new type of threat anyway?
Until next week my computer access is limited but my Samsung Charge is working fine for e-mail until then.
Thanks
Spam has been on the decline for many, many years – in popularity if not in volume as the number and availability of infected computers has increased. It’s simply a lot more complex and risky to make money from spam than other uses of malware. Over the past couple of years we have the growth of fakeAV, which provides an easy low-risk income source for distributors. In fact I would guess that this is the single largest contributor for the graph above.
As for security updates having anything to do with it … no. Even ignoring the fact that essentially noone gets malware infected via bugs in Microsoft products anymore (newest MS/IE bug commonly seen in exploit packs is the MDAC ActiveX bug(s) that date to 2006 or so), an overwhelming majority of malware infections don’t use 0days or unpatched vulnerabilities.
The two most common vectors are the Java deserialization and method chaining vulnerabilities (100% reliable, silent, never crashes, does it get any better?), and a bunch of Adobe Reader ones which happen to have reliable public exploits.
We are talking bugs that in most cases got fixed over a year ago. And despite having existed long before that – in several cases over 10 years (the Java bugs are due to fundamental misdesigns in the Java applet security model so they have existed _since Java was first introduced_, but perhaps not had viable vectors for arbitrary code execution before specific APIs were added).
Why? Easy – economics. These bugs (even with a standard exploit pack) easily nets 10-20% infection rates. Even if you had some mythical 0day that yielded a 100.00% infection rate, it’s obvious that it’s easier and cheaper to increase the amount of traffic 10x than finding/buying a single major 0day and exploiting it on a massive scale without killing it.
Security updates are not necessarily just vulnerability patches… (besides 2010 was the first year of declining spam volume in history of the internet, fakeAV spreading through spamvertised sites and users commonly reinstalling their systems with up to 10 year old WinXP installation CDs…)
Yes…for me, Autopatcher is a Godsend, it prevents me from having to start from scratch over and over again when trying to download patches for vulnerabilities eliminated over the past decade.
TEST
Thought I just posted something about one hour ago, but I don’t see it here ???
Neither Java or Acrobat Reader are Microsoft products and/or updated by Windows Update. The actual percentage of users vulnerable to MDAC (which I think is WinXP SP2 and older) is in the range of 3%.
However, especially Java is often included with OEM installations or installed when you need it for something and then forgotten (I’ve actually been bitten by the latter, since it’s needed to access some remote KVMs like HP iLO).
(MacOS X Snow Leopard ships with a vulnerable version by default though but it hasn’t been targeted)
FakeAV in some form has existed for quite some time (I’d even claim that it was pioneered by a certain AV vendor, complete with their free security scan alerting you that you should by their AV to get rid of 100 tracking cookies…), but it hasn’t gotten really big, aggressive, or distributed by infecting users instead of tricking them into installing it until more recently.
2011 startet with 2 billion useres worldwide, so 3% are 60.000.000 with “WinXP SP2 and older”…
Symantec Security Response lists quite a bunch of vulnerabilities: 1.051 out of 1.211 start with “Microsoft”. [1]
Maybe if we agree that their security updates include updates for Microsoft Security Essentials (MSE) we get the bigger picture? – Yes, I see Java and stuff over there on the right side… 😉
And yes, I observed about three hundred million nasty mails disappear from filters per month linked to nearly every patch Microsoft (and Adobe) shipped since June 2010. (That’s close to senderbase.org’s 18 month global spam volume history [2], beside they stayed at 84% spam and we’re down to approx. 10% now.)
[1] http://symantec.com/business/security_response/ => Vulnerabilities
[2] http://senderbase.org/home/detail_spam_volume?displayed=last18months
Hello, i have been searching around on the internet trying to learn how to program , code, and deciefer malware. do you have any suggestion on website that can help teach me the ways of programming and coding? thank you
Brian,
The article on TDL said that it installs a rootkit in the MBR. If one has a clean machine, from, say, a clean install, couldn’t a copy of the MBR be made with software, such as that from Firesage Solutions, MBRWizard, and restored if you get a rootkit in the MBR?
It appears that by backing up daily and backing up the registry, the MBR, and the computer files, a complete restore could eliminate most malware infections, including MBR rootkit infections. Is this right, or am I missing something?
Thanks for this article and for a great blog!
I don’t know anything about those products you’ve mentioned. But the trick in fixing the MBR is that if the infection has subverted the OS as well, then it may just reinfect the MBR once you boot back into the OS. I don’t know if this particular malware has that capability, just illustrating the difficulty with this type of attack.
I’ve often urged readers to use a whole backup system, something like Acronis True Image, which can take a snapshot of your machine in a pristine state, and then periodic snapshots going forward, and this includes the MBR. So, I think the approach of restoring from a known good backup is the soundest with this and most other malware these days.
According to http://www.securelist.com/en/analysis/204792157/TDSS_TDL_4 it does ensure that the MBR is updated if it finds a non-TDL MBR:
“In addition to all of the above, this rootkit component uses a watchdog thread that checks that system objects are hooked and that the MBR contains an infected copy of the sector. In the event that any differences are found, the MBR is re-infected.”
Though I’m not sure how TDL is supposed to be loaded if the MBR is no longer infested. If int 13 is not infested then the kdcom.dll cannot be replaced and it cannot be loaded. But since the malware has been installed there is probably a security hole on the system which means that it can be reinstalled again..
But I really like their simple obfuscation of their “enhanced” MBR 🙂
For full system backups, CloneZilla (open-source Linux live CD) works really well if you’re not intimidated by a really old-school text menu interface, and is free. Boot off the CD, answer a few questions, and your system’s hard drive is imaged to your brick.
“Where have all the spambots gone?”
Maybe their owners had been notified, and clean up those malware-infected computers subsequently? That is, in my opinion, the only effective way to deal with the botnet problem.
It is quite easy to identify botnets from spam with fake open relay and greylisting. With timely notification to the victims, hackers will find their botnets shrink continuously. The drop of global spam might indicate that there are less malware-infected computers now, or the hackers refrain from sending spam to avoid botnet detection.
Brian,
I said some time ago on various blogs that ‘botnets’ for spam etc are a compleate waste of resources for the bot hearders.
I have suggested repeatedly that this missuse of the resource was because the hearders lacked the imagination to use the resource more effectivly.
If I had a million or so user PC’s under my control from what is effectivly a fire and forget attack method I would not be wasting them by using them in a way that clearly advertised they were owned by high bandwidth activities (ie as Spam or DDoS bots) for just a few cents a machine.
I would instead be using them to look for certain document types and other information that indicated who the owner was and who they worked for and then via low bandwidth techniques use the information from select bots to get valuable information that I could use (ie effectivly insider trading) or sell on to others.
The simple fact is that although these bot hearders have smarts in a very limited direction they lack the knowledge to significantly capitalize on their investment.
I suspect that we will see APT type attacks and insider dealing start to make a noticable apperance as either the bot hearders or others wise up to the oportunities.
. o O ( Imagine they do all of the above and some other bad things for years now…)
Almost utterly resistant, but Botnets are not entirely inevitable. Simple yet highly effective practices — such as limited and secured computer access, and regularly updated anti-spyware or anti-malware software — can decrease the chances of becoming part of a bot.
Contrary to how IT managers think, vulnerability scanning using open source tools doesn’t do much of the job.
It is an arms race on both sides. In the recent report Cisco sees recent sharp decrease in spam traffic as the result of :
1) indeed many botnets take downs;
2) spammers getting financially smarter and switching from ‘spray and pray’ to ‘target and get paid ‘ spam attacks as ROI on targeted spam (spearphishing) attacks is higher than on old-style mass mailing ones.
Link to original whitepaper from cisco:
http://www.cisco.com/en/US/prod/collateral/vpndevc/ps10128/ps10339/ps10354/targeted_attacks.pdf
It’s funny; I used to get almost no spam, and now I’m getting a few messages a week in one of my accounts.
There are several ways that spammers can get your email address: Crawling the web, making good guesses, tricking your friends, hacking someone you trusted, buying lists…
I’m not quite sure if this is the whole truth. Personally I’m experiencing more or less the same spam in my inbox and filters and sometimes I even think it’s getting worse.
There’s a difference between the mails in your inbox and the mails those freaks talk about: They see / filter / block mails server-side (in most cases the obvious stuff) and your inbox in general reflects just the rest. That’s why in most cases users don’t have to worry about server-side spam attacks.
I’ve read in some research that spammers make 100% of their money with less than 0.2% of the spammails. The remaining 99.8% are just a waste of bandwidth semi-skilled cockroaches could handle. (Remember me the next time someone praises their 99% spam recognition rate. ;-))
I noticed the same on your server. We filtered some thousand mails each day early 2011. Now we filter less than 100 mails each day.
“Where Have All the Spambots Gone?”
Bitcoin mining!
http://forum.bitcoin.org/index.php?PHPSESSID=e1bc876b2bf4c1b866f53100859142c3&topic=7760.msg325573#msg325573
The most popular botnets have been taken down. The Spam filtering is improved and more AntiSpam techniques together can significantly reduce the junk emails in our inboxes. Nevertheless, Spam it is still far from its end.
Spam in translation: http://www.paolorovelli.net/weblog/?p=788