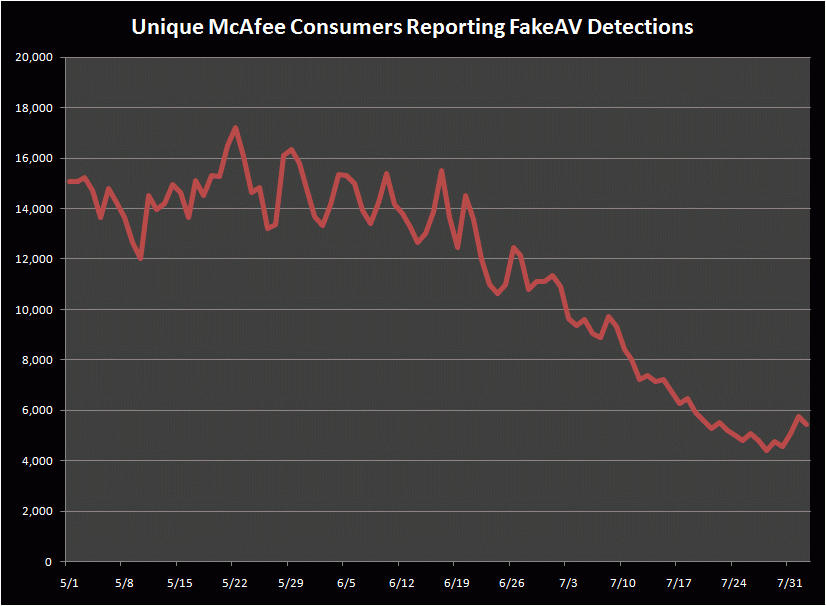
On Wednesday I wrote that many of the top fake antivirus distribution programs had ceased operations, citing difficulty in processing credit card transactions from victims. Others are starting to see the result of this shakeup: Security firm McAfee says it has witnessed a dramatic drop in the number of customers reporting scareware detections in recent weeks.
McAfee has tracked more than a 60 percent decrease in the number of customers dealing with fake AV since late May. “From McAfee’s vantage point, we are seeing a significant decline in detections reported from customers as well as the discovery of new FakeAV variants,” said Craig Schmugar, a security threat researcher for McAfee.
These extortion scams persist because criminal hackers get paid between $25-35 each time a victim relents and provides a credit card number. If fake AV distributors can’t get paid for spreading the scam software, they’ll find some other way to make money.
Fake AV bombards victim PCs with misleading alerts about security threats and hijacks the machine until the user pays for bogus security software or figures out how to remove it. For better or worse, it is likely that the dearth of credit card processors serving the fake AV industry has eliminated the first option for many people dealing with infections.




I’ve been reading your column for a few years and have really learned from it. Since you left the Washington Post, it sure “ain’t” the same.
I just wondered if you ever go out to the Black Hat Conference in Arizona. I think it serves an important purpose, but don’t you think the cyber-criminals go to it, also?
Another feather in the cap for those fighting the war against cyber-crime! Thanks Brian!
Detection numbers can be misleading. They tell you what AV vendors can already detect. The hitch is that if AV vendors were great at detecting FakeAV in the first place this would be a moot issue. So I guess that tells me that their insight into the problem from a macro level is already a little less detailed than one would hope.
Those numbers indicate a drop in distribution for the types of FakeAV they can already see. The question is, how many people are still getting victimized by FakeAV overall. That is is a number which AV vendors are poorly situated to come up with. I guess distro numbers are indicative, likely better than nothing.
To your point though it could also mean they are shifting vectors, finding another way to the money and the FakeAV distribution is languishing as a result.
al
What you say about detection is correct however it still gives an adequate picture of a decline in infections. Unless you suppose that for some reason many FakeAV producers/distributors had suddenly decided to drastically change their methodology and hence avoid detection which seems unlikely. It seems reasonable enough to attribute this to the squeeze on payment systems as outlined in the article.
As far as detection goes well really it’s not the fault of AV vendors if they cannot detect various malware until they’ve added it to definition files – they can’t protect against what they don’t know about (disregarding heuristics which is of limited utility and implemented far to aggressively by many AV vendors IMO). That’s just the nature of the beast, the way it is.
Neej,
I am not sure it does give an adequate picture (and I am not sure it does not). I would lean towards yes, but… As I pointed out, AV detections on average fall in the category of things they already ‘know’. Generally this means dated malware for the most part when your dealing with on disk sigs (which I think most Mcf desktops are outside of the enterprise).
Those detection stats reflect that they are seeing a drop in a known portion of the FakeAV space. That’s it. It says nothing about the net ‘new’ variants they do not yet detect. Those variants are the ones that sting.
As for your comments on heuristics – that’s a broad topic with a lot of different approaches. I will agree sometimes vendors can get too aggressive with generic detections (I know we do at times) but it’s because we are trying to snag malware that is challenging to detect without it. Slippery slope of course because they cause problems. Damned if you do, Damned if you do not.
al
Ironically, I’ve never needed anti-virus/malware to defeat fake AV of any kind. I simply end the process in task manager and run CCleaner, and voila! No problem.
Since I started training my clients to do the same, there hasn’t been a problem once.
The main problem right now, for my folks, is remembering to password protect the console of their favorite security vendor. The malware has the capability to change settings in well known AV/AM products and avoid detection that way. Things go south fairly quickly when that is left out of the check list of things to do; because the malware eventually invite all their buddies into the PC to finish doing their dirty work.
MBAM and AdAware seem to be immune to such manipulations so far.
The FakeAV itself is often not tough to disable. The problem lies in the friends it invites to the party. For example we often see Conficker on-boarded PDQ when the FakeAV starts up. Same is true for Sality etc. etc.
Looking at some stats this morning (this is anecdotal I looked at a few dozen hosts) and systems that see FakeAV typically have half a dozen other detections as well.
al
Definition based detection is definitely obsolete. This is why I include items in my blended defenses that don’t necessarily need definition updates. The overlap has saved my bacon more than once.
Kernel based solutions like these are increasing quite a bit lately.
Hmm, I do not think they are obsolete. Definitions are often quite generic in their nature. A lot depends on how the def was written. They still have primacy in nearly all AV products and they are easy to control FP’s with (generally). I just think they cannot be the only tool in the tool bag or you’re in trouble.
al
I still use them just to clean up after it is too late. But I don’t think they will last long in this environment. Some say Viper is the only true zero day solution, but I found it bogged my system down too much to tolerate. Supposedly, they gather new signatures in seconds. I must admit, they did update at least every fifteen minutes or sooner.
I can’t say how effective it is, but since it is the engine AdAware uses, I can attest that it did find one Trojan none of the other solutions did; but since AdAware is pretty poor at updating behind the gateway, I imagine that one was in the file structure for a few days at least!
CCleaner to remove and infection? Now there’s someone who’s clients are compromised. Scary! More money for the rest of us professionals.
I’m going to chime in here…
I live in Canada and last month I received (as did a number of my co-workers) at least two phone calls to my home phoneline from the “Operations Center for Windows”. Now not to discriminate but each time I conversed with the people on the other end of the line, they had East Indian accents. I am going to assume then (since I spoke to a total number of 6 or 7 individuals) that they are using a Skype type of service and hail from India.
Admittedly it was fun wasting their time and hearing them struggle with the language and scripted dialogues. They tried to inform me all the warning and error logs within my Event Viewer were viruses, or that the windows\inf\ folder contained nothing but “infections”. All this before trying to direct me to a website I can only assume was riddled with malware and FakeAV marketing.
Either way, I can only hope they too are feeling the hit of the recent “credit card processing shakeup”.
Don,
I got the same phone call actually. I am also in Canada.
al
I received a call like that about six months ago although they claimed to be “Microsoft Technical Support Center”. The caller didn’t even give their identity before screaming that “your computer is infected” and tried to sell me anti-virus software. A check on Google showed that this was a scam at least two years old originating in India.
@Don: did you write down the URL they were telling you to visit?
@AlphaCentauri no, unfortunately I did not retain the URL but if you’re really interested I can ask some of my colleagues if they have. I honestly wasn’t expecting anyone would truly be interested.
@AlphaCentauri Amazingly enough they just called again!!
So no to answer your question they attempted to direct me to www. ammyy .com (obviously without the spaces). Again I calmly gave the person an earful asking how he would feel if his grandmother was on a limited income and someone was bilking her out of her limited monies…. he promptly hung up. For anyone interested this time they had me open a command prompt and they read off the clsid key to “prove” it was my machine which was apparently “broadcasting on the Internet” that I was riddled with infections.
Apparently they are still making money ;(
Hmmm, it looks like ammyy.com is just a site that distributes a free remote desktop utility — The scammers were going to have you go there to download software that would allow them to take control of your computer.
Ammyy.com was registered in 2008, a long time ago for a scam site to be surviving. Although the fact that the registration is anonymous, it’s registered with Namecheap/ENom, and it’s hosted with a Russian host are a bit suspicious, it may be difficult to prove ammyy.com is in any way complicit in how their free product is being used, any more than LogMeIn or GoToMyPC would be if theirs was used instead.
It doesn’t mean no one could be getting a commission for steering traffic to ammyy.com, a site I would never have heard of otherwise, but I don’t know how you would go about investigating that possibility.
You cannot count on people always being as quick thinking as you people are. Many will not handle it as quickly and deftly as you did. The risk here is not the particular web-site, who it is registered to, or where it is located geographically. Any software that can be used to give access to your computer by others is inherently dangerous. hosts-file.net blocks only the ammyy.com host and classifies it as a phish since it is the one used (so far) in the English speaking scams. Airelle (rlwpx.free.fr/WPFF/hosts.htm) also includes gotomypc.com so it is probably used for at least French speaking scams. I haven’t blocked any at securemecca.com / hostsfile.org until now because I felt it was a personal decision. But that was before they were being used for scams. Even though they are a potential risk I would add them into my header with a comment, rather than in the risk section. But if I blocked them I would have to block all of them. What happens if the scammers use LogMeIn or one of the others next? Are there any more? I would much rather have them blocked than explain to a person why I didn’t block the one that nailed them. They are always free to make up their own minds whether to install or not, later. But I don’t want them installing it for specious Microsoft support or some other other scam . By giving them that block at that crucial point when they are called on the phone what I am giving them is some extra time to think about it. If they want to install later that is up to them but at least they hopefully will learn how to do it properly to minimize their risk. Will I install any of these on the almost unused Windows side of my machines? No.
This hit the press in my area today:
http://www.calgaryherald.com/technology/Albertans+targeted+antivirus+scam/5216078/story.html
This is great news but i am certain the fraudsters will try to make a comeback unfortuanatly.
This is more justification for the use of multiple AV engines, as individual engines aren’t able to provide the same levels of detection as using a multi-scanning product. I run all suspicious files through http://www.metascan-online.com to search for threats using 19 engines simultaneously.