The Common Vulnerability & Exposures (CVE) index, the industry standard for cataloging software security flaws, is growing so rapidly that it will soon be adding a few more notches to its belt: The CVE said it plans to allow for up to 100 times more individual vulnerabilities to be indexed each year to accommodate an increasing number of software flaw reports.
 Currently, when a vulnerability is reported or discovered, it is assigned a CVE number that corresponds to the year it was reported, followed by a unique 4-digit number. For example, a recent zero-day Java flaw discovered earlier this year was assigned the identifier CVE-2013-0422. But in a recent publication, The MITRE Corp., the organization that maintains the index, said it wanted to hear feedback on several proposed changes, such as modifying the CVE to allow for up to 999,999 vulnerabilities to be cataloged annually.
Currently, when a vulnerability is reported or discovered, it is assigned a CVE number that corresponds to the year it was reported, followed by a unique 4-digit number. For example, a recent zero-day Java flaw discovered earlier this year was assigned the identifier CVE-2013-0422. But in a recent publication, The MITRE Corp., the organization that maintains the index, said it wanted to hear feedback on several proposed changes, such as modifying the CVE to allow for up to 999,999 vulnerabilities to be cataloged annually.
“Due to the increasing volume of public vulnerability reports, the Common Vulnerabilities and Exposures (CVE) project will change the syntax of its standard vulnerability identifiers so that CVE can track more than 10,000 vulnerabilities in a single year,” CVE Project announced last month. “The current syntax, CVE-YYYY-NNNN, only supports a maximum of 9,999 unique identifiers per year.”
It’s not clear if this shift means software is getting buggier or if simply more people are looking for flaws in more places (probably both), but new research released today suggests that bug finders have more incentive than ever to discover — and potentially get paid handsomely for — new security holes.
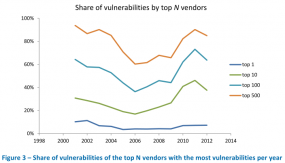
For example, one of the hottest areas of vulnerability research right now centers on the industrial control system space — the computers and networks that manage critical infrastructure systems which support everything from the power grid to water purification, manufacturing and transportation systems. In a report released today, Austin, Texas based security firm NSS Labs said the number of reported vulnerabilities in these critical systems has grown by 600 percent in 2010 and nearly doubled from 2011 to 2012 alone.
NSS’s Stefan Frei found that 2012 reversed a long running trend of decreasing vulnerability disclosures each year. At the same time, NSS tracked a decline in vulnerabilities being reported by perhaps the top two organizations that pay researchers to find bugs. For example, Frei noted, iDefense‘s Vulnerability Contributor Program (VCP) and HP Tipping Point‘s Zero Day Initiative (ZDI) each reversed their five-year-long rise in vulnerability reports with a reduction of more than 50 percent in 2012.
Frei suggests one major reason for the decline in bugs reported by ZDI and the VCP: researchers looking to sell vulnerability discoveries today have many more options that at any time in the past.
“The year 2012 saw many reports regarding a change and expansion of vulnerability and exploit markets,” Frei said. “More software vendors started to offer (or increased) rewards to researchers submitting their findings.”
In addition, many underground “black” markets are starting to more openly solicit and purchase exploits and vulnerability information, as has been documented numerous times on this blog and elsewhere.
But Charlie Miller, a well-known bug finder and big proponent of researchers getting paid for finding flaws, said these numbers also reflect the reality that it is getting harder to find major bugs in big-name products from companies like Apple and Microsoft. Miller said if vulnerability numbers are increasing year over year, it is because more people are looking at more products.
“Vulnerabilities in ‘things we care about,’ by which I mean things that we personally use or will personally have to patch, have either gone down or haven’t gone up much,” Miller said. “The products that have been hammered on for a long time tend to be getting pretty secure. Its all these new things nobody has ever audited that are accounting for all the new bugs. Its pretty easy to find vulnerabilities in products that have never undergone security review and I think this is what we are seeing.”
Indeed, NSS tracked a significant increase in new software vendors that were found to have vulnerable products in 2012. It also found that both Microsoft and Apple operating systems in 2012 saw their largest decline in vulnerability disclosures in the last decade.
If you need help keeping up with patches available for third-party applications, consider using patch management tools such as Secunia’s Personal Software Inspector or FileHippo’s Update Checker.
The NSS Labs vulnerability trends analysis is available from this link.



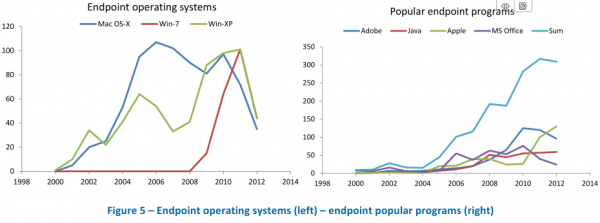

Looking at Fig. 5 Endpoint operating systems; I’m rather surprised at the precipitous drop in XP vulnerabilities. I also wonder why Win 7 shot up so fast? Let me guess – .NET
It seem like Redmond just can’t get that part of the platform straight.
The decline in XP vulnerability probably mirrors the reason 7 is on an upswing. The public and corporate world started moving off XP and onto 7, a process that accelerated in 2012, so they can be fully transitioned off XP before it goes off long-term support.
In addition the situation that Brian touched upon, where old products that have already undergone a lot of security review end up being pretty secure so vulnerabilities are fewer in number and harder to spot, is undoubtedly at work here. For better or worse Vista represented a large change from the XP code base, and all those wholesale changes mean more possibilities for security holes in new components, and 7 inherited them (in addition to the new-for-7 components).
If you zoom into the graphic you find the red Win-7 line continuing under the green Win-XP line, which may indicate that Win-7 exploits persist in Win-XP and vice versa. So the drop in both Win*-graphs and OSX may indicate that Microsoft and Apple now reach a niveau eight years ago, which problably could be an effect of grown security awareness of investors, public, customers and authorities on one side and rivaling Linux and Android on the other?
While I appreciate the impact of the numbers, at the end of the day they’re just a representation of the vulnerabilities that were publicly disclosed – not the number of vulnerabilities actually found in a piece of software attributed to its vendor.
On top of that, the CVE process doesn’t account for cloud-based software. Where do the hundreds of vulnerabilities disclosed to, and fixed by, Twitter or SalesForce.com appear? As more business critical software migrates to third-party cloud platforms, these metrics will become more and more academic to the situation.
WORLD ELITE WILL SAY TAHNK YOU FOR russian eastern european cyber criminals and others!
couse they wanted to control people now just normal people can not control them money…
they have money witraw limits
they have transfers limits and so one.goal is done in usa uk people have no control over them money.
and also we see cash is bad we need microchips simple:)
Thank you for another great post about the mysterious “them”. Those guys are behind everything.
Then they’re just like women, eh?
Curmudgeon’s cryptic comments create confusion.
Kudos Krebs!!
Brian, that headline is just alliterative genius! It took me a minute to figure out what it might actually mean when I saw it in my feed reader! Had to read the article! 🙂
same here, had to read it out loud trice,brilliant
Thanks. 😉 I usually stink at headlines, but this one came in a flash for some reason.
Should’nt the leather punch be adding holes to the end of he belt to allow for expansion? Still a great headline though.
Thanks Brian Krebs.