An underground service that is selling credit and debit card accounts stolen in a recent data breach at retail giant Target has stocked its virtual shelves with a new product: Hundreds of thousands of cards issued by non-U.S. banks that were used at Target across the United States during the retailer’s 19-day data breach. It’s not clear how quickly the non-U.S. cards are selling, but they seem to be fetching a much higher price than those issued by U.S. banks.
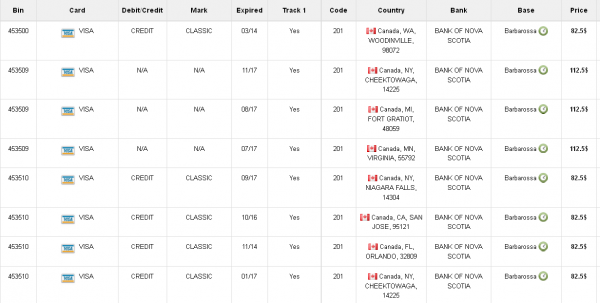
On Dec. 20, this blog published a story about the “card shop” rescator[dot]la. That piece explained how two different banks — a small, community bank and a large, top-10 bank — had bought back their customers’ stolen cards from the fraud service and discovered that all of the purchased cards had been used at Target during the breach timeframe. The shop was selling data stolen from the magnetic stripe of each card, which thieves can re-encode onto new, counterfeit cards and use to go shopping in bricks-and-mortar stores for items than can easily be fenced or resold.
As I wrote in that story, a key feature of this particular shop is that each card is assigned to a particular “base.” This term is underground slang that refers to an arbitrary code word chosen to describe all of the cards stolen from a specific merchant. In this case, my source at the big bank had said all of the cards his team purchased from this card shop that matched Target’s N0v. 27 – Dec. 15 breach window bore the base name Tortuga, which is Spanish for “tortoise” or “turtle” (also an island in the Caribbean long associated with pirates). The small bank similarly found that all of the cards it purchased from the card shop also bore the Tortuga base name, and all had been used at Target.
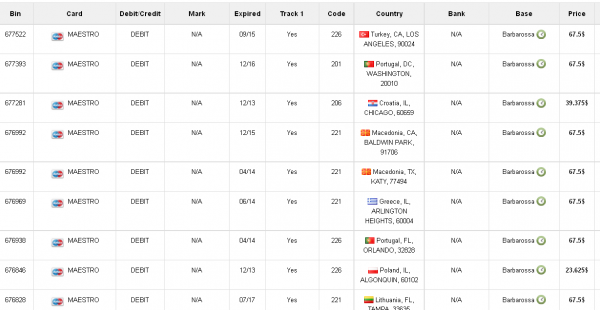
On Friday, the proprietor of this card shop announced the availability of a new base — “Barbarossa” — which consists of more than 330,000 debit and credit cards issued by banks in Europe, Asia, Latin America and Canada [side note: one Russian expert I spoke with said Barbarossa was probably a reference to Operation Barbarossa, the code name for Germany’s invasion of the Soviet Union during World War II].
According to one large bank in the U.S. that purchased a sampling of cards across several countries — all of the cards in the Barbarossa base also were used at Target during the breach timeframe.
As with cards sold under the Tortuga base, debit and credit cards for sale as part of the Barbarossa base list the country of origin for the issuing bank, and then directly underneath include the state, city and ZIP code of the Target store from which the card numbers were stolen.
When I first became aware that this card shop was selling only cards stolen from Target stores, I noticed a discussion on a related crime forum wherein customers of this shop seemed very enthusiastic about this ZIP code feature. I couldn’t figure out what the big deal was: I’d assumed the state, city and ZIP described the bank that issued the card.
Later, I learned from a fraud expert that this feature is included because it allows customers of the shop to buy cards issued to cardholders that live nearby. This lets crooks who want to use the cards for in-store fraud avoid any knee-jerk fraud defenses in which a financial institution might block transactions that occur outside the legitimate cardholder’s immediate geographic region.
Non-U.S. cards used at Target generally fetch higher prices than U.S. cards, between $67 and $100 apiece.
The cards for sale in the Barbarossa base vary widely in price from $23.62 per card to as high as $135 per card. The prices seem to be influenced by a number of factors, including the issuing bank, the type of card (debit or credit), how soon the card expires, and whether the card bears a special notation that often indicates a higher credit limit, such as a Platinum card.
The prices also appear to be influenced partly by how rare it is to find cards for a specific bank available on the black market. The highest-priced cards I found for sale were issued by banks in Singapore, South Korea and the United Arab Emirates.




I am sure that our heroes from NSA will come to rescue us. So, we shouldn’t be worried about it too much. Right? NSA will keep us safe.
I’m sure NSA is probably the cause of this breach. They must’ve forced Target to keep some back-doors open, you know for national security that the hackers conveniently made use of.
Oh puhleeze put your tinfoil hat back on CORRECTLY; this is the NSA, not the IRS (and even the IRS doesn’t go THAT far). It’s more likely the NSA will hack into the thieves’ sites to track them down, if they haven’t already.
Great PR opportunity for the NSA
to help catch this gang of miscreants.
It would be a great, positive
public -image uplift
for how the NSA
is now generally perceived by the public…
I imagine they monitor this thread
and Brian’s Blog…so do something.
Well, the NSA does like going above and beyond its chartered mission – so why not track down some Russians.
No kidding ..:)
Debit cards are listed… but how do criminals use a debit card without a PIN?
Target (like many retailers) promotes its own line of “Red Cards,” some debit only, some credit.
I wonder if any of its cards have been sold, and what Target’s mitigation approach is going to be, whether it will be more or less aggressive, since they have the most information about the incident.
Target’s email to me (as someone with a Target store credit card) indicated the security problem included Target Red Card store cards as well as the Target debit cards.
The Target debit cards seem like a particularly bad idea. For those who are unfamiliar, a consumer applies for one of these cards, and whenever you use it at Target, the money is debited immediately from your checking account. Target offers these cardholders the same deal they extend to regular store card holders – an automatic 5% discount on purchases. You can spend $1 and get an immediate 5% discount on your purchase.
The discount wouldn’t be worth it for me to extend any retailer into my bank account with each transaction. At least being a holder of a Target Red Card store credit card, I can just pay the bill in full when the statement arrives each month.
As a REDcard Debit card holder, that’s not all true. Its just like writing a check to Target. It takes a few days for it to hit my account. And sure, they have my routing and bank account numbers, but those numbers would be completely visible to anyone looking if I were actually writing a check.
As for them storing my account information, my student loan company, my car insurance, and my employer (and their outsourced paycheck company) all have and store the same information. That’s why I make it a point to check on my account at least once a week.
Excellent point Shannon!
Almost all debt cards can also be used as credit cards, although from my understanding the target redcard cannot be used without a pin. Bank issued debt cards almost always carry the visa or mc logo and can be run as credit only requiring a signature. It’s not currently known if the PIN numbers of the target victims were compromised, although early indications are that pins were not stolen.
Barbarossa just seems to be a continuation of the pirate theme (ie Tortuga). he was an ottoman pirate… or the pirate from pirate of the carribean movies (which also talks about Tortuga). if the next batch is labeled Sparrow, we’ve got some Disney fans.
Or, it could refer to Frederick Barbarossa, Holy Roman Emperor. Or, more likely it is just a good name that sounds good. Don’t read too much into it.
I agree – it’s a pirate theme. Not sure why it’s taken most other people so long to pick up on that, unless everyone else was just looking up “Tortuga” and “Barbarossa” on Wikipedia, where the relationships of those terms to piracy are not made very clear.
Barbarossa could also be Hayreddin Barbarossa. I can understand the slowness of “Tortuga” but soon as “Barbarossa” popped up it should have clicked. Esp if you think pirate. Granted it is just Barbossa in the films, but can be taken as Barbarossa if combined with Hayreddin. Or could have been shortened due to verbal speaking and someone missed the repeat of “bar”… But thinking of films, then the “captain” or “premium” label would work in this case.
They were going to make his name “Barbarossa” in the film but Johnny Depp pronounced it “Barb-barb-oh-so” and couldn’t keep a straight face when he had it in his lines. Watch the DVD commentary, it’s in there.
So I assume the .la is Latvia or some such place. Why cannot Interpol find the customer of the ISP who is hosting the card site?
The Domain code .la was originally assigned to Laos; but it seems to be currently assigned to Los Angeles:
https://www.la/e/about
Los Angeles promotion of .la
http://en.wikipedia.org/wiki/.la
Historical assignment of .la
I am going to get smog.la, gangs.la, crime.la, congestion.la, overpricedhouses.la and getmeoutof.la. I tried to get in.la but it is already registered.
Not Los Angeles: http://whois.domaintools.com/www.la
Still Laos: http://simple.wikipedia.org/wiki/List_of_Internet_top-level_domains
https://www.la/
The TLD is owned by Laos but they are marketing it to Los Angeles people because Americans are willing to pay more.
It can’t be Los Angeles , because then it would have to be in this type of TLD format ” domain-name.us. la.” to signify that it’s a city within the United States
Ok, ‘rents’, ‘affiliates’, ‘does something with’ Los Angeles.
http://investvine.com/laos-sells-la-domain-to-los-angeles-businesses/
I sourced my info. I don’t speak on behalf of it.
Officially it belongs to Laos, just like .tv still officially belongs to Tuvalu. (Same for any other two-letter Internet domain.) Still, that doesn’t prevent the official registrar from selling .la addresses as meaning Los Angeles (or Louisiana), just as .tv addresses are more likely to mean “television” than Tuvalu.
I understand that. I was just throwing into the woodpile info in regards to the domain listing.
rescator.la is less than a year old. It’s proxy registration service is in Hong Kong, which has strong cybercrime enforcement. Its nameservers are through Cloudflare, a US company, that has to provide data to US law enforcement if presented with a valid subpoena. Rescator’s clients are lining up to buy cards based on their zip codes being in their geographical area, and the data included is only enough for in-person purchases, where there will be security cameras, not on line purchases.
Is this a stupid crooks story?
Not sure how this is a stupid criminal story. Any carder worth their salt has a crew of drug addicts, homeless people, and other dirtbags that are willing to go into stores to use cards. Keeping your face off camera while still making money isn’t a particularly difficult obstacle.
Those “dirtbags” are victims too. They are in a bad spot which forces them to compromise their morals for survival. I reserve “dirtbags” for those who make more than a days sustenance off the crime.
Don’t let your heart bleed too much. They are victims by their own choice. They know what they’re doing and know it’s a crime. I don’t shed any tears over junkies.
Go away, teabagger troll.
These cards have probably already been used to commit millions of dollars of online and e-commerce fraud. They will be used to commit millions more in the next hours and days.
The cards cannot be used online because online merchants require the 3-digit security code on the back of credit cards and debit cards. That CVV number was not part of the info on the mag strips so the thieves MUST use make counterfeit credit cards to use at retail brick and mortar stores- ones you walk in.
Again- the security code on the back of the card was not part of the stolen info so online purchases cannot be made according to the most recent info
Sorry LindA, that is not true. There are quite a few places on the web that take cards and don’t ask for the CVV #.
I make most of my online purchases without having to offer up my CVV#. One of the reasons I chose to accept a Target store credit card and refuse their offer of a debit card attached to my checking account was because a scammer once got hold of my Paypal debit card number, which worked exactly the same way a Target debit card does. I wasn’t pleased with Paypal’s sluggish response, and decided the cash back percentage, which I believe for me was 7% at the time, just wasn’t worth the risk.
Like one of the other commenters here, I tend to watch my financial situation closely, and the Paypal scammer only grabbed about $60 in transactions from my checking account before I became aware there was a problem. I highly recommend people sign up for any alerts their credit/store/bank cards offer them, especially real-time text alerts.
When I dropped my Bank of America credit/debit card in a subway terminal, I found out within 24 hours, because I had alerts set up to inform me when my card was used, and also when my balance hit below $500, which is the minimum I keep in this account. I was able to cancel the card over the phone, even though I was on the other side of the world at the time. I didn’t even realize the card wasn’t in my wallet until I started getting a flurry of text message alerts.
I follow these rules because they are prudent.
1. Make purchases ONLY with credit cards. Doing so puts a “wall” between your money and the bad guys because there is no link to your checking account. Fraudulent charges have much less impact on your financial status than fraudulent withdrawals.
2. Use your debit card ONLY for making ATM withdrawals or deposits. Thus money flows out of your checking account when you use an ATM, write a check or authorize an ACH debit, actions that require your involvement. In this paradigm, the ACH is the weakest link IMHO.
Brian has provided other advice for using ATMs.
You also get some protection from debt cards with the Visa logo on it if you don’t type in a pin code
This is the thing that makes no sense to me (outside of my understanding of the esoteric economics of the payment industry). The regulation on how and when a PIN is encrypted is very specific, even in this “total breach” they were not able to walk away with any valid PINs. And yet, not using a pin and instead using a signature-only card is the “suggested” method?
LindA;
I have seen others post the same info regarding the CVV not being compromised and Target actually declared the same in the FAQ of their letter they put out.
However, The mag stripe on a card carries 2 distinct tracks of data. Track1 and Track2. Within both of these tracks there is a data placeholder that is described as “discretionary data”. While it may contain other values, it is acceptable for it to contain the CVV value.
Given that Target is not the card issuer, it is a broad stroke to say that some other card issuer, (small bank or CU etc) may have that data on the mag stripe.
See: http://en.wikipedia.org/wiki/Magnetic_stripe_card for more info on the fields on the mag stripe of a card.
With 40 million potential numbers at risk I think it is too early to tell if CVV is in the wild. That is unless Target has verified with each card issuer whether this is included on their cards. That is a longer list than the major card brands.
I believe you’re mistaken. There is NO valid reason for a bank to include a CVV2 in its magstripe; the CVV2 is specifically intended for “card not present” transactions, and I doubt card networks would tolerate its inclusion in the magstripe of ANY issuer’s card (even in an “other” field where a perp would have to GUESS it’s a CVV2).
The reason for the confusion is the similar names for the codes (CVV/CVV1 vs. CVV2), and Target’s own confusion in the first version of its announcement. There is *NO* way a card reader could read the CVV2 from the *ONLY* place it’s supposed to appear on the card — numbers PHYSICALLY printed on the card (4 digits on front for Amex’s CID; otherwise 3 digits in or near the signature block).
I think it is worth mentioning that this is a 3 digit code which is far from unbreakable or difficult to guess.
Especially if you have a nice piece of custom software to repeatedly guess every single single possible combination only three single digits.
So? You think the bank is just going to sit there through 500 guesses (the average it would take to find the right number) without realizing something was fishy and deactivating the card?
I’d be surprised if they got through more than 10 guesses (or 1% of the possible numbers)
Herb, I don’t just think that, I KNOW it.
To prove it I tried it myself with my own card on PayPal. I was allowed as many guesses as I wanted at my super-secret 3 digit code. After hundreds of attempts, neither PayPal nor my card issuer made any attempt to stop me or even apparently noticed anything was wrong.
interesting….this may not bode well for PIN guessing (assuming the same principle applies for some banks of allowing tries)…the average for truly random distribution would be 5000 (although we know most people will not choose randomly). Maybe they can guess 30%-40% of PINs? Using some software they could even limit consecutive tries per day if some banks block cards after a certain number of consecutive failures.
Another real good article. Why isn’t Interpol involved in this credit card breach or are they?
Furthermore, I am sure the N.S.A. can track the meta data across the globe to catch the cyber criminals behind this credit card breach against Target.
I’m sure your a twit after reading that.
ping to me for email notifier
Interesting base name, but if I was attending their brain storm meeting to come up with a catchy “base” name, I don’t think I’d suggest “Operation Barbarossa” or any reference to Barbarossa. If my memory serves me correctly, I don’t think that operation’s end result were very successful for the parties who tried implementing that plan. At least they didn’t name it “Operation Stalingrad”, so they have that going for them.
Brian,
That is pretty sharp if the sellers providing zip codes since banks often block cards from being used by their customers when they are in states that generate more fraud than others.
Hope they are making progress with their forensics!
Thanks so much bud!
Scott
Rescator from Lampeduza? These guys love historic names, don’t they
Target Breach: What Happened?
Expert Insight on Breach Scenarios, How Banks Must Respond
htxx://www.bankinfosecurity.com/target-breach-what-happened-a-6312/p-1
All – Just wanted to say this. As an ex-fraud investigator with over 10 years in the credit card industry, I say THANK YOU BRIAN!
You site has brought so much needed awareness to the public eye, and not just because of this breach but all of your information. I find so many people are following your post on this breach who are now closer then ever to remaining safer or at less risk then they were 5 minutes before visiting your site. Hoping you and your family have a great holiday.
How is it possible that the rescator website is still up and running? Isn’t the NSA or someone able to take it down. I just looked at it. It is obviously a criminal activity. They are selling stolen cards and make no attempt to hide what they are doing. And I know a million more will pop up in its place, but c’mon shut it down.
And again, Brian, darn nice work. This story is huge. But it will blow over. And next Christmas we will still be using 40 year old mag strip technology here is the good ole US of A, whilest the rest of the world uses chip technology.
Really?
Your kidding right? The NSA? How is this a matter of National Security?
And why are you advocating that an arm of the US gov’t has the right to reach across international borders and shut down a website or retail site?
Turn the tables; Let’s say you are in the business of running a photo selling website and you have a catalog of pretty women in revealing clothing, (Not Porn), and let’s say that some other country has laws against that. Is it ok for them to reach out and shut you down?
I get it. This is criminal. But it is not something that can be controlled. These servers come and go so fast it makes finding Bin Laden a walk in the park.
“Really?
Your kidding right? The NSA? How is this a matter of National Security?”
Are you serious? When a criminal is able to steal credit card information from 40 million people it is a matter of national security.
“And why are you advocating that an arm of the US gov’t has the right to reach across international borders and shut down a website or retail site?”
You really don’t get out much do you? The crime was committed in the USA. Do you read? Just because the server is over seas does not negate the fact that a crime was committed. Other countries cooperate with the USA all the time to take down serves. Did you ever hear of a guy named Kim Dotcom?
“Turn the tables; Let’s say you are in the business of running a photo selling website and you have a catalog of pretty women in revealing clothing, (Not Porn), and let’s say that some other country has laws against that. Is it ok for them to reach out and shut you down?”
Let say you compare apples to Volkswagons.
I get it. (No you don’t…but go ahead)…This is criminal. (Yes it is). But it is not something that can be controlled. (Yes it can but go on…)..These servers come and go so fast it makes finding Bin Laden a walk in the park. (No, it takes time money and resources to set up a server and let people find you….for example silk road…)
I am guessing you live in a foreign country and not the USA.
It is funny. From your response I would have guessed that you were the one who did not get out much. But this probably suits your daily life and how you live. I still cannot understand why Americans are so in love with a true nanny state. Then I realize they do not realize it is one, like a frog in a hot pot of water.
But it uses cloudflare a US company for its DNS.
“one Russian expert I spoke with said Barbarossa was probably a reference to Operation Barbarossa, the code name for Germany’s invasion of the Soviet Union during World War II”
Barbarossa is a strange choice given that the credit card operation was run by Russians. Uranus (the Soviet pincer movement in the battle of Stalingrad) would have been more appropriate considering how Soviet forces surrounded the Nazis without them being aware of the threat.
Excellent reading Brian, you never disappoint.
1) Why is the site still up and running ? Good question given that the Gov had foreign intelligence services go after Mega and other torrent sites , why haven’t they gone after sites like these. It’s not even darknet ? How hard can it be, I mean they ( Dept of Justice) confiscated entire domains not that long ago…
If only rescator had hosted some movies…. he’d be in prison by now.
2) Was it only mag stripe , or were they in the system and able to intercept chip comms ? Truth be told, I can’t remember the last time “swiped any card, it’s all chips ( or god forbod, RF)
“Was it only mag stripe , or were they in the system and able to intercept chip comms ? Truth be told, I can’t remember the last time “swiped any card, it’s all chips ( or god forbod, RF)”. During a recent trip to Menards I noticed they were selling RF proof wallets. Google “rf proof wallet” for products, stories and home made solutions. I searched Amazon using “RFID blocking wallet” and got many hits. Read: http://krebsonsecurity.com/2012/09/researchers-chip-and-pin-enables-chip-and-skim/ . Additional info welcomed.
And now the Rescator site keeps on sending people in circles with a captcha challenge that never accepts you. Wonder if it’s the fact I’m going to it via Tor browser and anonymized.
This is a fairly (but not totally) common problem tor users face… it is an issue with timing, more often than not. If somebody else visits from the same IP then you may wind up cycling each other out since the captcha will never match.
“My account was dinged on Friday” Transaction made in Scottsdale, AZ – live in Fl – purchased at Target in Missouri on 11/27 ” Bank has identified my card as one being compromised but no call made or alert to me on Friday when it occurred. Card was used at Maceys – tried to call their security department on Saturday after I cancelled my card – what a joke no one could really help me at all. I want a # to call where I can complain.
Barbarosa = Red Beard the Pirate
rosa = red
baraba= beard
A banking safety tip: if you have card (or Paypal) linked directly to a checking account, it behooves you to consider have a separate checking account for that. In which you maintain a low balance.
Depending on your bank’s relationship/service level, this could be free. I only keep about $100 in my Paypal debit account, and adjust as needed. Any errant transaction will bump into this balance issue (no auto overdraft either).
I’ve closed the checking account linked to paypal years ago. Now I always need to change the paypal paying method to my credit card. This is a little inconvenient as paypal always defaults to the (non existing) checking account, but it is worth the extra layer of protection for me.
I wonder when paypal will find out that there is no checking account linked anymore.
Your idea is an interesting one, having a second checking account to be used as an escrow account. The account could also be used for ACH transactions thus removing your primary checking account from any ACH based problems. The first problem would be estimating your monthly ACH needs. If you are happy with the current arrangement then keep it. I still prefer to have the credit card as the payment method for reasons indicated in other entries.
I find it curious that Citi and Target have limited the amount of money people can withdraw and purchase using their debit cards (if you shopped at Target within the time period in question).
I thought we merely had to monitor our card activity? That we aren’t liable for unauthorized activity on our card? We’re advised to not rush out and get a replacement card, but a bank and Target are now limiting their exposure on a grand scale, aren’t they?
Are they going to stand by and help you if someone uses your card to open a line of credit at other stores? I think not.
First, any limitations are imposed by the *ISSUER*, which (except for REDcards) is *NOT* Target. Virtually *ALL* issuers have limits debit card transactions; they’re just making them tighter as a precaution. (Chase specifically said their limits were a temporary measure until they could cancel & reissue the affected cards AFTER the holidays.) Obviously it’s a CYA measure for the banks to reduce THEIR potential losses.
I’ve been saying from the beginning that it’s a good idea for affected bank cardholders (debit OR credit) to have their cards cancelled & reissued, since their magstripes can be used to make purchases at almost *any* store *without* a PIN — especially if your bank can issue new cards on the spot. What you’re parroting is Target’s own advice, but IMO that’s not adequate for bank cards until they can clarify WHICH cards were actually compromised. (They’re now saying NOT all cards swiped during this time were affected, but that doesn’t say WHICH ones.)
REDcard is trickier because (a) they can ONLY be used at Target (thus they’re FAR less valuable on fraud sites than bank cards), (b) Target is more likely to eat the charges since it’s their OWN cards, (c) Target is swamped with complaints and their card reissuance department will probably be swamped too, and (d) REDcard debit generally *requires* a PIN. As of today, Target now suggests all REDcard debit holders change their PINs; I did that overnight Thursday (after the first reports broke but before Target confirmed). **FOR NOW**, that may be enough for REDcard, whether they have PINs or not; but don’t be surprised if Target starts reissuing ALL affected cards after Xmas (especially REDcard credit which does *NOT* require a PIN).
Finally, it is HIGHLY unlikely that a stolen card ALONE would enable someone to open a line of credit in your name. The ONLY way SSNs could have made it to compromised registers and/or card terminals was the few people who signed up for REDcards at checkout during the breach (or used ID from one of the few stupid states, if any, that still puts SSNs on driver’s licenses); even then it’s unclear if the perps captured it (or even KNOW they captured it). This is generally a case of card theft, NOT identity theft.
Just to clarify: So far there is *NO* evidence that the thieves *EVER* had access to the database that contains REDcard debit holders’ bank account numbers. Except for new customers, those numbers are in a CORPORATE database; all indications are this was a STORE-level breach. That won’t prevent fraudsters with a card number *AND* PIN from using it at Target, but it *DOES* prevent other means of access to the bank account itself (third-party ACH debits, forged checks, etc.)
Ironically, checks are LESS secure in this type of breach than REDcard debit, as Target registers scan them to generate “e-checks”. If (as many suspect) the hack was actually in the register, the hacker COULD have direct access to the bank accounts of those who wrote checks to Target in that timeframe.
*DUDE*
Why do you put an asterisk on both sides of the words you are typing in upper case anyway. It’s like shouting but with an anal retentive side that was amusing a few days ago but now it’s getting old.
You have some good comments, it’s just a bit strange. I tired to just read the capped stuff, thinking well maybe it’s code, but no it’s just annoying.
Happy Christmas *ANYWAY*
I agree with you but with a caveat — by selling via zip with name, you can access address via OSINT. By finding address you often find phone number at the same place. With an address and name you can access credit headers to obtain SSN. With SSN you can obtain past addresses and perform a more thorough history. This is how fullz come about.
But it is a lot of work for a criminal who has a very limited timeframe and there’s no reason to believe you’d be much more targeted than anybody else in a phone book, linkedin, or online site with address information, etc. The only thing it might give is information that yes, indeed, the person is creditworthy and may be worth targeting. The truth is most people just aren’t that special or unique, and accessing information via phishing and malware is far more useful and quick to any criminal who was interested in this sort of thing.
Which is to say, while things could get worse, they probably won’t, and risk analysis is necessary. Just like more people are worried about plane crashes than car crashes or terrorism instead of drowning in a bathtub, people always miscalculate actual risk and make their own lives more miserable.
It’s better just to assume that crime *might* happen and be prepared to deal with the possibility of it, but not ruin one’s life about the possibility.
Cards issued by Brazilian Banks ? Totally worthless since the country are 100% Chip and Pin (of course if used for online purchases)
“This lets crooks who want to use the cards for in-store fraud avoid any knee-jerk fraud defenses in which a financial institution might block transactions that occur outside the legitimate cardholder’s immediate geographic region.”
Another part of the reason that knowing the ZIP code is so valuable it because it allows a card to be used more easily outside of the immediate geographical area. If say, a person who lives in New York travels to Florida and attempts to use their card, they will likely be asked (possibly just on the first use) to verify their ZIP code. This can be done either by the machine (i.e. gas pump) or the cash register attendant.
The nonprofit, tax-exempt http://www.cloudflare-watch.org/target.html has filed an abuse complaint with CloudFlare, requesting that they terminate their connections with rescator.la immediately.
I expect that they will ignore it, because I believe that CloudFlare is some sort of honeypot. See the bottom of the home page about this. I began suspecting this last Spring, when they kept exposed.su and exposed.re online for days on end, despite an outcry in the press.
They keep saying that they can’t take down content. But they can make it unreachable within a few minutes by pulling the DNS records, and have done so when it suits them.
Target is now aggressively adverting on the Fox network to shop at their stores.
It looks to me like some sort of “damage control” by the executive morons.
RBBritain – Target RedCards are Visa Cards and can be used anywhere that Visa is accepted.
rguy – Just because you shopped at a particular store, doesn’t mean that your zip code matches the store. Of the three potential Targets near me, my zip code matches none of them. This was not the case before we moved but even the Target that my mom shops at is in a totally different state (though before it moved across the border, I guess it would have had her same zip code.) – Now I’m not sure if I’m disagreeing or seeing your logic. LOL
All –
I know some of you might think this way already, but this is not going to be the last major breach of the next 13 months.
The smart card solution recently talked about on NBC Nightly News will add security. However, as one of the first smart card users testing the first smart card in 1997, it’s not new, and that means the bad guys have already figured it out. Brian has already shown that they cracked how to skim a smart card 2 years ago.
There is NO Silver Bullet!! Us, people, the humans….we are the best defense. We have to stop looking at convenience as more important than our own security.
I have been that person…in fact I was managing a fraud investigation group at a card company when my identity was stolen. I did something I thought was stupid, but it wasn’t, I just didn’t know any better.
Look, I guess my point is that we all need to start to be a little more careful not to jump before looking to see if the pool has water in it, or is it just painted so it looks like it does.
Crime is the oldest profession, even older then prostitution. It’s not gonna stop looking for the shortest path to your money anytime soon.
Take your 10 % discount and shut the hell up .
Drink it up and then drink some more
Light it up and let’s let it blow
Any sites up yet like a pastebin that has a dump of all compromised numbers? How easy is it to get an account at rescator [dot] la?