Over the holidays, I heard from a number of readers who were seeing strange, unauthorized charges showing up on their credit and debit cards for $9.84. Many wondered whether this was the result of the Target breach; I suppose I asked for this, having repeatedly advised readers to keep a close eye on their bank statements for bogus transactions. It’s still not clear how consumers’ card numbers are being stolen here, but the fraud appears to stem from an elaborate network of affiliate schemes that stretch from Cyprus to India and the United Kingdom.
 One reader said the $9.84 charge on her card came with a notation stating the site responsible was eetsac.com. I soon discovered that there are dozens of sites complaining about similar charges from similarly-constructed domains; for example, this 30-page thread at Amazon’s customer help forums includes gripes from hundreds of people taken by this scam.
One reader said the $9.84 charge on her card came with a notation stating the site responsible was eetsac.com. I soon discovered that there are dozens of sites complaining about similar charges from similarly-constructed domains; for example, this 30-page thread at Amazon’s customer help forums includes gripes from hundreds of people taken by this scam.
I did a bit of digging into that eetsac.com domain, ordering a historic WHOIS report from domaintools.com. The report shows that the domain eetsac.com was originally registered using the email address walter.kosevo@ymail.com. Domaintools also reports that this email address was used to register more than 230 other sites; a full list is available here (CSV).
A closer look at some of those domains reveals a few interesting facts. Callscs.in, for example, is a Web site for a call center and a domain that has been associated with these $9.84 fraudulent charges. Callscs.in lists as its local phone number 43114300. That number traces back to a call center in India, Call Connect India, Inc., which registers its physical address as Plot No 82, Sector 12 A, Dwarka. New Delhi – 110075.
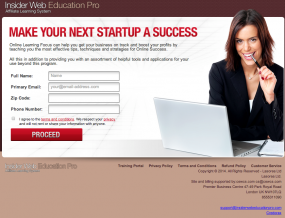 The next site like that one on the list — cewcs.com — references the domain insiderwebeducationpro.com, another domain on the list of sites registered to that ymail.com email address. The homepage of insiderwebeducationpro.com lists the following contact information:
The next site like that one on the list — cewcs.com — references the domain insiderwebeducationpro.com, another domain on the list of sites registered to that ymail.com email address. The homepage of insiderwebeducationpro.com lists the following contact information:
Copyright © 2014. All Rights Reserved – Lasorea Ltd
Lasorea Ltd.
Site and billing supported by:cewcs.com cs@cewcs.com
Premier Business Centre 47-49 Park Royal Road
London UK NW107LQ
8555311090
A search at companieshouse.gov.uk, a government site which maintains records about companies based in the United Kingdom, turned up incorporation records (PDF) showing that Lasorea Ltd. was founded in January 2013 by Emil Darbinian, a 28-year-old self-described accountant from Nicosia, Cyprus. Other records searches on Mr. Darbinian indicate he owns at least two other companies at the same address, including Testohealth Labs. Ltd — which appears to be a software company — and a firm called Levantos Venture Ltd. Mr. Darbinian did not return messages seeking comment.
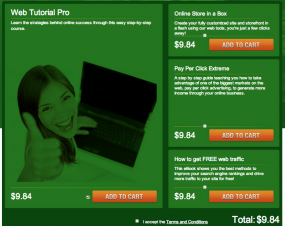
Another domain on the list — etosac.com — is listed as the support and billing site for webtutorialpro.com, a site which bills itself as an “affiliate learning system.” In fact, of the 235 domains registered to walter.kosevo@ymail.com, all seem to be either affiliate programs of one kind (diet pills, work-at-home) or support/call center sites.
Webtutorialpro.com lists on its homepage a company named Lukria, Ltd., and an address at the same London business park as Mr. Darbinian’s companies. If we step through the signup process to become an affiliate at Webtutorialpro.com, we can see that everything — from the “online store in a box” to “pay per click extreme” and the tutorial on “how to get FREE web traffic — all retail for….wait for it….$9.84!
Lukria, according to incorporation documents (PDF) purchased from companieshouse.co.uk, was created on the same day as Lasorea Ltd., and lists as its director a Sergey Babayan, also from Cyprus. According to the Facebook pages of both Mr. Darbinian and Mr. Babayan, the two men are friends. Mr. Babayan has not responded to requests for comment.
Mr. Babayan’s Facebook profile says he works at a company called Prospectacy Limited, which LinkedIn says is an accounting firm in Nicosia, Cyprus. According to Prospectacy’s Web site, this company specializes in “corporate services,” including “company formation,” “banking,” and “virtual office” services. The company seems to be in the business of establishing offshore firms; according to a reverse WHOIS record lookup from domaintools.com, the email address used to register Prospectacy’s domain also was used to register at least ten other domains, including registerincyprus.com, registerinuk.com, setupincyprus.com and setupineu.com.
A number of these affiliate sites include on their home page links to credorax.com, a Southborough, Mass. based acquiring bank Malta-based acquiring bank that is in the business of processing credit and debit card payments for merchants. It’s not clear whether either cewcs.com or insiderwebeducationpro.com use Credorax Inc. for payment processing, but it seems to suggest that by association. I reached out to Credorax to learn whether this site (and perhaps others that are the subject of this story) are customers, and will update this story if I hear back from them.
Update, 12:43 p.m. ET: I heard from Michael Burtscher, vice president of acquiring risk and fraud management at Credorax. Burtscher clarified that his company has offices in the U.S. but is based in Malta. Burtscher confirmed that Credorax had until recently helped to process cards for the network of sites named in this story, but that the company has severed that relationship. He declined to say when exactly the relationship ended, or indeed whether my information about the client’s identities was accurate. Burtscher would only say that Credorax terminated its relationship with the client in response to consumer complaints about the fraudulent charges. “This was one of those cases where when we onboarded them it looked like a legitimate account, but when we saw there were issues we decided to take action.”
Original story: If I had to hazard a charitable guess about what is going on here, I would say some ambitious “affiliates” associated with these moneymaking schemes were abusing the system and pushing through charges on stolen credit cards. But it is difficult to escape the conclusion that this is little more than an elaborate (and probably successful) scam set up to steal little bits of money from lots and lots of people.
By the way, this is not a new type of fraud, nor is this particular fraud a recent occurrence — although the bogus $9.84 charges do appear to have spiked around the holidays. Most of the domains involved in this scheme were registered a year ago or more, and a quick search on the amount $9.84 shows that the fraudsters responsible for this scheme have been at it since at least the first half of 2013.
If you see a charge like this or any other activity on your credit or debit card that you did not authorize, contact your bank and report the fraud immediately. I think it’s also a good idea in cases like this to request a new card in the odd chance your bank doesn’t offer it: After all, it’s a good bet that your card is in the hands of crooks, and is likely to be abused like this again.
In the hopes that my listing them here makes this scam less successful, here are a bunch more domains apparently involved in this scam:
callscs.in
cewebcs.com
cs-casa.com
cewcs.com
eduacc.in
educs.in
eetsac.com
etosac.com
feosac.com
foculu.com (portuguese)
homecs.in
iawcs.com
iewcs.com (offline)
livecs.in
netcs.in
ntccs.in
ntsupp.com
onwsac.com
premcs.in
profcs.in
quikcs.com
sacluc.com
sacsis.com
sewcs.com
suppcs.in
tdwcs.com
techcs.in
vagacs.com
webcs.in
Update, Jan. 15, 5:46 p.m. ET: An earlier version of this story incorrectly stated that the domain profcs.com was associated with this scam; the correct domain is profcs.in. The above story has been modified. I regret any confusion this may have caused.




Great post Brian! Hopefully people will be aware of these scams now.
Theres no affiliates here — it’s the advertiser themselves. You know this beyond reasonable doubt because they split their cancellation/customer care over 100 different domains and, without even clicking any of those links, i guarantee they make it extremely simple to cancel (in order to reduce chargebacks). The use of digital products is because those are easier to set up and the product is just an excuse to charge cards.
They will get away with it. This is commonplace. I work with entire firms set up to help people process unauthorized transactions. I could link you to a thousand other domains and know of another party who processed over 100MM USD and ended up buying an influencing share in a bank.
I wouldn’t call that beyond a reasonable doubt. I doubt a court of law would either.
brian brian your our man if you cant leak it no one can go brain go brain
so what your trying to say is the nsa did the target breach And 9/11?
Thank you for these posts! Explaining how you research these issues is very interesting and far more valuable to me than a simple warning. What internet security software do you use that allows you to visit these sites safely?
I don’t know how Brian does it, but many in my camp simply use a junk computer that is just for honeypot work, and a virtual machine hosting your favorite operating system, whatever that may be.
This machine is sometimes setup on a DMZ or otherwise separated from the local LAN.
Most have no more security other than what is already built in the operating system, if they are using some Windows variant, perhaps Defender, for example. A virtual machine is not a guarantee, you won’t get popped – but on a junker like that, nobody cares.
You could always put a Puppy Linux LiveCD in your optical drive, if you have one, or a USB boot stick, and try that. Good luck though!
Replacing credit cards every 6 months or so should become a routine practice for anyone, whether using using the net or not.
Why? Regulation E and Regulation Z exempt you from the fraudulent charges. It’s the bank’s problem.
If I had to guess, I’d say his thought was to aggregation — over a long enough time period if you make enough transactions your odds of being skimmed or defrauded increase over that time period, but this is not generally a function specifically of time — it’s more a function of online use, in the case of places where card data is stored and can be used months or years later. In that particular instance he might have a point.
Few skimmers though would wait that long to use a card, though, in which case his logic is flawed unless it were a card taken in a very long-term drawn-out breach where the connections were not made (like happened a lot more often in the mid-2000s, on both stored data and long-term accounts, not just unencrypted card data on servers).
I would say if a person ever found a test charge or dispute on their bill that they cannot place, even if it is somewhat small and they cannot track down how it might have occurred, it might make sense to consider changing the card then canceling the prior one in case it was a prelude to identity theft. This is more of a vigilance issue than a ‘replace every 6 months’ issue, not just on the bank’s part but also on the consumer’s.
(And while his logic might be flawed and it is indeed the bank’s “problem”, it takes consumers hours/days/weeks/months of waiting and headaching to sort this out. What is that saying of yours? Time is money? Stress has costs too.
You are correct. For banks and credit unions the $9.84 charge is not high enough to request the money back. Visa charges a fee that makes it cheaper to just take the loss and reissue the card. The labor and paperwork alone to deal with card fraud is pretty high.
It is annoying at the least, and something needs to be done to hold networks liable for allowing these fake business to pull transactions from stolen credit cards. The technology and reporting from these networks is still the equivalent of a website developed in the 1990s.
“The technology and reporting from these networks is still the equivalent of a website developed in the 1990s.”
While this may be true, it is sometimes that very fact that makes them harder to breach. The more complexity, sophistication and new technology you add to a system the more chance you have of being breached. On the other hand, how many hackers under 35 or 40 really have that much experience with OS/400, OS/390, QNX, and the like with remote terminals and sometimes proprietary protocols? In the case of a banking network, I’d say security via obscurity is far far better than in the case of any random machine on the internet.
Lance, if you are reading this, or anybody else that might be reading this with experience on the subject — do you know how many honeypots there are that emulate this sort of environment instead of the usual Windows/Solaris/Linux honeypots? If somebody cannot practice in a live environment the chances of a successful breach drop to almost (but not quite) zero by an outsider.
I’ve had one fraudulent charge in the last three years, it was an airline ticket from Argentina to Miami . It took me less than 30 minutes to clear that up. Changing cards every 6 months also means changing everything that card is linked to (Cell phone, vonage, amazon, Netflix…). So while you make a reference to time and money, you neglect the time it takes to constantly change cards – which for me is far more than dealing with one fraud incident every few years. Another thing you ignore is the credit rating hit you’ll take if you are constantly applying for new cards.
Excuse me, I was talking about the time and money on both sides of that — to deal with it and to change it. There is something to be said for linking a prepaid card that you can change the linking to also. What does applying for new cards have to do with anything? I was talking about debit/ATM cards (actually I guess the original poster was not, I don’t really even believe in credit cards 🙂 — you are right in that they are much easier to deal with because you do not bear the burden of being out of the money while the issuer clears those up).
As to applying for new credit cards… you do not apply for new credit each time you replace a card with the same card (‘lost’ or otherwise), unless something has changed since I looked last. Do they do a credit check again there (this is the only thing I can think of, and this does impact your rating but only slightly).
Did you mean to reply to the original poster? I was agreeing with you. 🙁
Interesting story,
Another possible lead:
E-mail address walter.kosevo@ymail.com suggests that in this case we are probably dealing with someone from Balkans.
Walter is a hero from partisan movie Walter Defends Sarajevo (real hard core bad-ass Nazi killer ), while Kosevo (Koševo) is urban neighbourhood in Sarajevo.
Walter was nom de guerre of Josip Broz.
Well researched and documented article – thanks
and is likely to *be* abused like this again.
Great explanation… great, but very scary.
Excellent investigation. I’ll bet these guys have been running the same scam for years, as shown in the 50 page thread of investigations by MGD: http://www.dslreports.com/forum/r19620593-Ebook-websites-fraud-charges-Devbill-DigitalAge-Pluto , however MGD was not able to lay a finger on the possible perpetrator’s identity.
A big component of this scheme is the ‘Work at Home’ business owners who register an LLC for the web site that processes the fraudulent charges. All they have to do is submit payments to Cyprus and answer the phone to reverse charges for those who complain.
One interesting aspect is that some of these guys were able to place charges on cards that were never used otherwise – leading to speculation that they had stolen account information from a card manufacturing facility.
re: “leading to speculation that they had stolen account information from a card manufacturing facility.”
Or they just generate random card numbers and test them against random online merchants.
Actually, Moike, he was able to find out. It was ChronoPay.
As a longtime subscriber to Domain Tools, I have greatly enjoyed reading your reports on the use of the service in your forensic investigations. One of the recurrent breaks I find in cases is the propensity of the bad-guys to continue to use Domain Names, Email Accounts and IP Addresses, long after their security is compromised. These breaks occur with such regularity, that one of the first things I check in Domain Tools is WhoIs history. Through the extensive forensic database in Domain Tools and the ability to virtual time-travel via the Wayback Machine, many cases can be solved. The trick is to identify objects know to be associated with the suspect and then trace the use of those objects through time. Once you start tracing one tagged object, that object will in turn compromise additional objects, resulting in a data cascade.
In The Godfather movie, I am reminded of the restaurant scene where Michael shoots Sollozzo and McCluskey with an un-traceable gun which is fingerprint proof. After Michael executes both men, he drops the gun as instructed and walks out of the restaurant. Fortunately many of the people we investigate don’t appear to be fans of The Godfather and keep reusing the same gun.
https://www.youtube.com/watch?v=kSQqv2UuvC0
Keep up the good work,
Mike
Another good tip is to have bank security emails or phones text’s sent to you, if their is any type of suspicious activity on your bank or credit card accounts. Also enable two factor authentication on your accounts if your bank provides that option
All this reminds me of a hack some dishonest company from China had circulating several years ago, where many cell phones were already setup upon original purchase, to charge .10 cents every so many days. One of my phones came already with this ruse, so I simply blocked it using the phone’s own controls. So I get a new one, and something is charging me .90 cents, but at more random times – the crooks were getting smarter. So I replace the battery, and voila! No more mysterious charges! I’d lay odds, there was a chip in the original battery, that somehow, could cause the phone to access data services to line somebodies pocket. Maybe my provider? Hmm?! :/
@JCitizen, that’s not likely. Most batteries don’t even have digital interfaces – they have two conductors for DC power, and possibly a third conductor to an analog temperature sensor to detect dangerous overheating during charging. If the fraudulent charges were even related to your phone, it could have been due to malware that was destroyed when the phone lost power. Possibly something in your internet browser cache was the cause of your troubles: if this happens again, look back through your browser history to see where you might have picked up such an infection.
I actually didn’t suspect the battery until changing it ended the charges very abruptly, and at the same time. So you will never convince me they didn’t have some kind of chip in there, maybe a Bluetooth wireless or something that was capable of initiating some kind of data session or commanding such. It wouldn’t do it through the power wires of course, unless a bypass circuit with a transistor was built into the phone mother board. Of course I’m not going to take it out and look.
They’ve found malicious chips in keyboards going to Apple Mac Air factories, what’s stopping crooks from sneaking something like that at any place in the supply chain. If I had suspected this before I threw the battery away, I would have taken it apart to see if my suspicions had merit – but as it stands, it looks to me like it was the obvious culprit. The battery I took out, was not a standard Motorola OEM battery, but some cheap Chinese knock off, where the one I replaced it with, was OEM equipment, and came in marked that way.
Also I should mention this is basically a dumb phone, although it is capable of browsing the internet. I must admit, I have put a ringtone in there that came from a well rated site, and I put it in there as a Bluetooth transfer from my PC. The only thing about that theory, is I haven’t lost any information in the changing of the battery. My ringtone is still in there, all my contacts and photos, are still in there – if there were malware in there it should still be operational from what I understand about how malware get into the phone firmware. I will also admit that I do have limited understanding about mobile architecture, but then I’m a electrical technician, and have repaired more sophisticated circuits and controls than that, and have degrees in engineering, so I’m not a total chump on this kind of tech, either.
This is not relevant whatsoever. Please refrain from posting such nonsense in the future.
Also the behavior started immediately from when I bought the phone Verizon and the phone store I bought it from were clueless about the origination of the fees, I think they just thought I was spoofing them when I said I didn’t initiate the data sessions.
Fortunately the money I lost only added up to around $1.80 a month, but just like Brian’s article suggested, just think of the millions someone is making off these illegal charges. At 90 cents a pop coming from potentially billions of phones – world wide! It is staggering, when you think about it.
This is off topic and no one cares. Thanks! -The Internet
JCitizen, you sir, are quite the dufuss!
We at the NSA also agree
😀 ]:)
“immediately from when i bought the phone[,] Verizon”
Stop right there, we found the answer. I am unfortunately still a verizon customer (they are the only platform with sufficient coverage in all the areas I do business) but they absolutely SUCK when it comes to extra/hidden fees. My wifes phone (not a smartphone) came from the store (software VERIZON wrote) set up to do all kinds of ringtone and wallpaper crap, for a price of course, and opting out was painful. I was never closer to abandoning them as after the fury over that stupid phone, but alas they have what I need and no other network does…
I can sympathize, but I wasn’t given a choice, and Verizon was ‘acting’ clueless to the charges. This was the 1st relatively ‘smart’ phone I’d had, so I had to investigate the services I had to shut down. Unfortunately the few I COULD shut down were minimal!
On face value, you would suspect Verizon was the one benefiting solely from these scams, but I’ve been around long enough to know even the ISP’s get chumped, and the criminals love incriminating someone else, for their dastardly deeds! Not that I’m ready to let any big telco off the hook!
Thanks for all the work, Brian. It’s another good reason to read Krebs On Security!
Regards,
I somehow think that the issuing and use of credit card is a bit too easy to use on internet. And the credit card company won’t go after these scammers a little harder. Ultimately the cost of these lost are not bear by company but consumer.
What if the 4th largest credit card processing company in the world was started using illicit funds via fradulent credit card transactions on the second floor of a bank in Cyprus ?
What if that same firm, had offices in the USA, and was indirectly responsible for laundering millions of credit cards back to associates in Cyprus and Russia, to launder the cards?
What if the Target theft involved this same group ?
Yes, I bring up a TON of questions, but the secret Service refused to investigate ni 2009, and the crimes continue.
The FTC investigated, prosecuted, and was told the agencies were shut down, but they continue to operate. Two of the individuals involved with the original scam are on the FBI most wanted cyber crime list. They live in Switzerland, and Interpol has confirmed their addresses, and where they live, but they cannot be returned to the USA for crimes committed here.
Interested, contact me directly for more info,.
John Ervin,
I would like to know more.
Cheers,
Kandy
Yes John, more info please!!!
MVD?
I meant MGD?
MGD is the nickname of a very active member of the DSL Security Reports forum (linked in this blog’s blogroll). MGD did some incredibly detailed and as far as I can tell accurate sleuthing on the companies behind a rash of these tiny-charge scams. Most of them seemed to lead back to front companies that were set up by various members of ChronoPay’s staff.
Here’s just one of many such reports that MGD put together:
http://www.dslreports.com/forum/r19620593-Ebook-websites-fraud-charges-DevbillDigitalAgePluto~start=1040
Sorry, language problem. Yes, I know. I was asking if he was related to MGD (or perhaps was MGD but using a different name). His style and manner are very similar. 🙂
I did some research and found over 46 cards with charges of $9.84 amount in just the past month on debit cards.
The problem is that even though this is ongoing fraud, the recent breaches with Target and URM have a much more over reaching effect that we will have to wait until we are finished with these before we can tackle these smaller charges.
The one thing that concerns me is that some of them go undetected by our fraud system, while some of them are just barely scoring low enough to be noticed. Some cards are charged multiple times with different domains.
Brian,
Again, this is exactly the type of story that truly brings awareness with solutions and suggestions. I say this because some of the news out there is only on the subjects that might be a hot topic at the time. I have shared this post on several of my social media sites in the hope to touch more people who may not know what this charge is, and hopefully they will not ignore it and just move on in their life.
Thanks for always posting useful, consumable, defensive information.
Folks are probably still so caught up with this Target stuff that $9.84 might slip past them. It’s a small charge would be likely to skate past a lot of people…they’ll give it a quick glance, probably figure it was for some takeout they had the other day and never even notice….so thanks for this post.
I’m OCD about checking my bank activity after every purchase (I keep all my receipts until the payment clears) so a random charge for $9.84 is something I’d notice, but I’m sure many of us have realized that the majority of people tend to not be as meticulous.
These criminals are quick clever. A small charge for a little less than $10 is a lot less likely to raise eyebrows than a sudden drop of $750…
*quite clever
Certainly the card issuers’ are aware that they can put systems in place to regularly change the key Id numbers on the credit cards? Say, the main number is maintained but a “hidden on card” secondary number is changed every 6 months. Issuing new cards on a, for example, 6 monthly interval as a part of normal banking practice would solve many issues I feel and also reinforce the security relationship between card issuer and card holder. An expected routine card number change is a lot more acceptable than an “unknown ID theft” I would think… as the cost of insecurity is tremendously high!
…just thoughts.
The FTC went after a similar operation a couple of years ago, see http://www.ftc.gov/news-events/press-releases/2010/06/ftc-obtains-court-order-halting-international-scheme-responsible.
The FTC’s memo in support of injunctive relief gives some interesting insight how the operation worked, see http://www.ftc.gov/sites/default/files/documents/cases/2010/06/100628adeletro.pdf
These scams are ancient, used to run on checks.
This old (and incoherent, was pre-blog) web page of mine is all that remains to document the Netfill small fee international credit card charge scam of the 90s. Due to their nasty banks Japan is often a primary target.
http://www.faughnan.com/ccfraud.html
Very timely article. Our account was taken over this last week by malicious folks. The amounts were different, but show Paypal for $8.47, Domino’s Pizza for $61.34, Blizzard Ent for $9.23, Facebk www. fb.me for $5.00 (twice) and then another Facebk for $1.08 with a return of $1.08 as well. I called the credit union last night, but they couldn’t place a hold on it because they were closed for the day. Thankfully, no new charges appeared as of this morning. All charges are being reversed.
I incurred one of these $9.84 charges but it did NOT come through a credit card or bank card. I thought it did, I told my bank (B of A) that it was a fraudulent charge and they reimbursed me. That’s not the problem, the problem is the ROUTE used to access my bank account.
I bought a rubber stamp for deposits of business payments for my business account. I bought it through Amazon. I’ve always had very positive experience with Amazon and thought nothing of buying the stamp … with my account number on it.
The stamp says-
For Deposit Only (B of A)
(My business name/DBA)
(My Personal Name)
(My Business Checking Acct. Number)
Now I know some are going to say “What were you thinking putting your account number out there?”
Again, Amazon is very reputable as are sellers on Amazon so I really didn’t worry about it … that is until I saw a $9.84 charge on my account. Then found out that the charge had been incurred by DIRECTLY accessing my account without any involvement with a check/debit/credit card.
So, being as that account number hasn’t been out “in the wild” EXCEPT for this one instance and being as this one instance immediately coincides with the purchase from Amazon, there really is no doubt HOW that account number fell into the hands of the bad guys. Is there?
So I called Amazon. To make a long story short(er) they are investigating the merchant and it is my sincere wish to make this merchant lose their Amazon privileges. It didn’t even cost me $9.84 BUT it’s going to cost them a lot more in lost business.
What goes around comes around.
CloaknDagr: Since the start of the Amazon forum mentioned in BK’s investigation there has been much speculation about where our card numbers were leaked and trying to find some common denominator (or even a couple). Thus far the only posts that have been truly informative are the one or two (think that’s all) where the cedit/debit card had never been used “in the wild.” So, of course that led me, and many others who were already leaning toward it not being some common retail outlet (or Amazon itself), but a payment processor or a bank INTO going up one more level of that chain…
And ever since I first read about the results of BKs investigation (Thank You So Much BK!–haven’t found the time to say that yet) the subject has remained very much on my radar. As one of the intel junkies who has been trying to piece together this puzzle since 12/18 (and stupidly trying to do it without a subscription to domaintools), poking around every single day for connections on the web, googling a billion different things, contemplating each new post on Amazon, etc., let me just say that your story really intrigues me (that’s an understatement actually).
Now that I’ve had a couple days to glue together some of my random pieces of info (and especially after reading the follow-up comment from Credorax, then spending a day googling more info on Credorax any time I can squeeze it in)…well, I don’t know what to think quite frankly. I’m hoping that some sleep will help (connecting dots and googling for more dots to connect has cut into my sleep as well). So apologies to all if this was way too long and rambling. Hope we’ll hear some more of your story.
If one crooked rubber stamp printer wanted to do something with your bank info what are the chances he/she’d just randomly decide to go spend it at EETSAC/ONWSAC/FEOSAC/et al? The feeder source for their fraudulent bank info just has to be huge.
clokndagr, how can you assume your bank account information was compromised by the stamp maker when in fact you are using the stamp to publish your bank account number, stamping it on every check you tender?? Don’t you realize that the payees are receiving images of the tendered instrument? You’re providing every customer (and their staff members, and their banks staff members) with enough information to charge your account. i think you are inviting trouble anytime you publish your name and account number on the same piece of paper, i am surprised the stamp maker actually agreed to make the stamp for you. i bet you also own a signature stamp, since it is a time saver, but if you do you should lock both stamps in the safe at all times, since a stamped signature is a legal instrument wtith the same authority as your pend signature.
CloaknDagr: I hope you’ll post this info over on the Amazon forum (or allow me to do it FOR you).
Thank you so much! I got hit on two cards with this scam and it was due to recur each month. Your article is enormously helpful.
No surprise or anything, but just wanted to pass on that there was a report of a charge by the EETSAC/Et Al group on 1/6 (same day Credorax reported they were no longer going to be their one-stop payment gateway/financial institution), but also would not say when, meaning exactly “why,” they had made that decision.
Amazing how merely shedding some light on things tends to make cock-roaches go running for cover.
Yes MGD was onto Pavel many years before Brian started this blog. His research still shows how a single individual can trace cybercriminals activities and then watch how LE does nothing. How long did it take for Pavel to actually start his forced vacation? Is he still on holiday?
Still: nice research Brian!
My bank further enhance the security of your system. Quick to credit cards
Stolen immediately be identified. However, the changes also may open new credit card. The same problem came again.