Previous stories on this blog have highlighted the damage wrought by an identity theft service marketed in the underground called ssndob[dot]ru, which sold Social Security numbers, credit reports, drivers licenses and other sensitive information on more than four million Americans. Today’s post looks at a real-life identity behind the man likely responsible for building this service.
![The administration page of ssndob[dot]ru. Note the logged in user, ssndob@ssa.gov, is the administrator.](https://krebsonsecurity.com/wp-content/uploads/2014/03/ssndobadmin-600x444.png)
The administration page of ssndob[dot]ru. Note the logged in user, ssndob@ssa.gov, is the administrator.
Last summer, ssndob[dot]ru (hereafter referred to as “SSNDOB”) was compromised by multiple attackers, its own database plundered. A copy of the SSNDOB database was exhaustively reviewed by KrebsOnSecurity.com. The database shows that the site’s 1,300 customers have spent hundreds of thousands of dollars looking up SSNs, birthdays, drivers license records, and obtaining unauthorized credit and background reports on more than four million Americans.
Private messages and postings on various crime forums show that the service offered at ssndob[dot]ru was originally registered in 2009 at a domain called ssndob-search.info. A historic records lookup purchased from domaintools.com shows that ssndob-search was first registered to an Armand Ayakimyan from Apsheronsk, Russia. This registrant used the email address lxg89@rambler.ru.
In 2013, a copy of the carding forum carder[dot]pro was leaked online. Forum records show that the lxg89@rambler.ru address was used by a member who picked the username “Zack,” and who told other members to contact him on the ICQ instant messenger account 383337. On Vkontakte.ru, a popular Russian social networking site, Mr. Zack is the name of a profile for a 24-year-old Armand Ayakimyan from Sukhumi, a city in western Georgia and the capital of Abkhazia — a disputed region on the Black Sea coast.
Mr. Zack lists his date of birth as August 27 and current town as Sochi, the site of the 2014 Winter Olympics, (although the Mr. Zack account appears to have been dormant for some time). We can see some pictures of Mr. Ayakimyan (DOB: Aug. 27, 1989) at this profile by the same name at promodj.com, a music mixing site. That profile is tied to a group profile created by an Armand Ayakimyan in Sochi.
Mr. Ayakimyan appears to have used a number of different nicknames on various forums, including “Darkill,” “Darkglow” and “Planovoi”. That’s according to the administrators of verified[dot]cm, a top Russian crime forum at which he had apparently created numerous accounts. In an amusing multi-page thread on verified, the administrators respond to multiple member complaints about Plaovoi’s behavior by “doxing” him, essentially listing all of the identifiers that point from various email addresses, ICQ numbers and aliases back to accounts tied to Armand Ayakimyan.
KrebsOnSecurity attempted to reach Ayakimyan via multiple email addresses tied to his various profiles, including Facebook. An individual responding at the main Jabber address used by the operator of SSNDOB — ssndob@swissjabber.ch — declined to comment for this story, saying only “Я против блога. Выберите другой сервис,” or, “I am against the blog. Choose another service.” This reply came immediately after the user of this profile updated his status message notifying customers that his identity theft service was just freshly stocked with a huge new update of personal data on Americans.
The conclusion that Ayakimyan is/was involved with the operation of SSNDOB is supported with evidence gathered from Symantec, which published a blog post last week linking the young man to the identity theft service. According to Big Yellow, Ayakimyan is but one of several men allegedly responsible for creating and stocking the ID theft bazaar, a group Symantec calls the “Cyclosa gang.” From their report:
“To keep their store stocked, the Cyclosa gang had to continue to attack companies for their databases of personal data. Along with the major breaches covered in Krebs’ report, Symantec found that the Cyclosa gang compromised a number of other firms. In May 2012, the Cyclosa gang breached a US-based credit union. A few months later, they compromised a bank based in California, USA, and a Georgian government agency. While the Georgian agency may not have a lot of information pertaining to US and UK citizens, it’s possible that this attack was of personal interest to the Cyclosa gang, considering Armand’s background.”
“At the start of 2009, evidence emerged of Armand’s partnership with three other people who used the handles ‘Tojava’, ‘JoTalbot’ and ‘DarkMessiah’ on cybercrime forums. There may be other players involved with this organization but these four individuals appear to be the main actors in this group. The four of them carried out numerous acts of cybercrime, such as conducting malware-based search engine optimization and pay-per-click schemes. They also bought and sold hijacked chat accounts, botnet traffic, and personal and financial information. Armand’s relationship with Tojava was vital for the formation of SSNDOB. Tojava was allegedly responsible for introducing Armand to the world of cybercrime and carding. We believe that Tojava created many of SSNDOB’s technical features, such as its search engine and its social security number query scripts.”
I created the following mind map to keep track of various identities and contact addresses apparently used by Ayakimyan over the years. 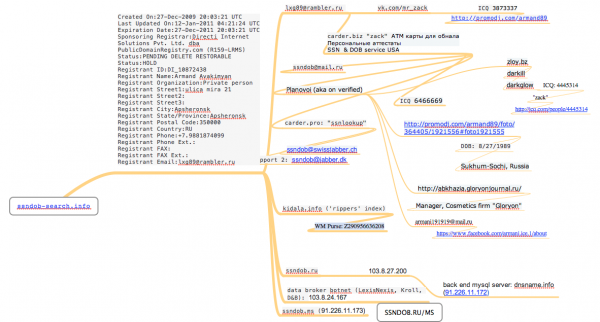
DATA BROKER BOTNET
As Symantec alludes, the owners of SSNDOB appear to have supplemented their stock of personal data by hacking into some of the largest data brokers in America. As I wrote in a September 2013 exclusive story — Data Broker Giants Hacked by Identity Theft Service — the operators of SSNDOB also ran a very small botnet that hooked directly into servers owned and operated by some of the biggest personal information brokers on the planet — including LexisNexis, Kroll and Dun & Bradstreet.
There is no direct evidence that the hackers behind SSNDOB managed to tap directly into consumer data stores maintained by these brokers; LexisNexis said it found no signs of consumer data exfiltration, and the other two firms acknowledged the break-ins but left it at that. But given their line of work, it seems unlikely that the hackers wasted such an opportunity; the person(s) in control of that botnet had access to the hacked servers for at least five months before they were discovered.
Meanwhile, it’s unclear whether Ayakimyan is still involved with SSNDOB. As Symantec notes, “Armand appears to have made a few career moves throughout his adult life, including working in a photo studio and becoming a sales manager for a cosmetics firm. He also considered using his technical skills for legitimate work, as he discussed creating an online dating service and a real estate website for properties in Abkhazia. However, neither of these services became a reality. In 2013, Armand appeared to be working at a church in Russia.”
As I mentioned at the top of this post, sometime in 2013, SSNDOB was hacked — its entire store of four million consumer records plundered (these were merely the records that customers of SSNDOB had paid the service to look up). According to information obtained by KrebsOnSecurity, the database and service was compromised by the same group of young American hackers responsible for launching exposed[dot]su, a site erected to leak the personal data of celebrities and public figures, including First Lady Michelle Obama, then-director of the FBI Robert Mueller, and U.S. Attorney General Eric Holder, among many others (see screen shot below).



![Exposed[dot]su was built with the help of identity information obtained and/or stolen from ssndob[dot]ru.](https://krebsonsecurity.com/wp-content/uploads/2014/03/exposed-su-600x462.png)

If he lives in western Georgia why FBI from Atlanta can’t catch him?
Because it is another country, not USA:)
Wrong Georgia.
Really?
They mean Georgia the country (next to Turkey and Russia). No Atlanta there…
I think that’s just an Internet rumor, like, there’s a country called Turkey!
He lives in the Eastern European country of Georgia. Not the US state that shares the same name.
First Crimea, now Georgia! Can no one stop these Russian invaders?! Nyet! 🙂
I’d say first Georgia (2008 Russo-Georgian War), then Crimeea.
Chuck Norris. He did it back in the 80’s, he can do it again. 😉
or “Criminy! doxed again!’
* http://www.oxforddictionaries.com/us/definition/american_english/criminy
Since when is Georgia part of Europe?
Fine example of the average American’s world view.
Or a fine example of the difficulty of conveying sarcasm through text.
Amazing, you can tell he/she is an American from the thirteen broken English words he/she posted.
Fascinating
https://www.cs.drexel.edu/~sa499/papers/oakland-deception.pdf
Unless the writer was intentionally deceptive, in which case they came to an entirely wrong conclusion.
(I don’t put much weight in it, either way)
Are we seriously having this conversation?
For the geographically challenged among us, I have provided the following YouTube video entitled “1996 Atlanta Opening Ceremonies – Parade of Nations 5/13” ( http://www.youtube.com/watch?v=5Fmk2bS8OWk ). The location of the 1996 Olympics was Atlanta, Georgia, United States. Starting at 5:20, the nations of Gabon, Gambia and Georgia are introduced. Note the cheer from the audience when Georgia is introduced.
Well played sir.
>a real-life identity behind the Russian man
Cmon Brian, He is not russian. He is Georgian or Abkhazian (if you recognize this country) but he is not russian.
Fair point, because I truly don’t know if he was born in Georgia or Russia. He lists his hometown as a city in Georgia, but he lists his previous address as Sochi, and his FB profile says Krasnodar, which of course is in Russia.
He’s of Armenian descent judging by his last name. Probably an ethnic Armenian, born in Sukhumi/Abkhazia and currently residing in Sochi. Everyone in Abkhazia holds Russian citizenship, so he’s most likely Russian by nationality
Fine follow up Brian!
There must have been quite a lot of foot work on this one.
Thanks again for your journalistic skills and ability to ferret out the details needed to put the picture together in a way that provides useful insight into the dealings of these particular criminals.
The information provides me with good background on the motivations and general operational scope of the guys I try to avoid.
Cheers!
The above commentary is reminiscent of the story that went around when Russia did invade Georgia (the country) when the problems existed with Ossetia: as it was told, upon the news that Russia had invaded Georgia, all of the gun shops in Alabama, Mississippi and South Carolina quickly sold out of ammunition that day….
http://www.imdb.com/title/tt0060921/
Surely not even American rednecks could be that st….
Oh. Right. What am I saying.
Wow, racist much?
Great Story Brian! Don’t know how you do it, but it was a very (but scary) interesting technical read.
Did the SSNDOB plunder include the product (victim) database, or only the customer database? It would seem an ID “recovery” service could make a killing by seeking out and offering services to those known to be compromised.
It would also be useful to be able to query a sanitized victim database to see if one’s self was was compromised.
I just re-read your last paragraph and see that you do say the consumer records were plundered. Are you aware of any open sources where one could see if their name was in that database?
Bryan, nice piece of investigative work. Please keep digging as you are one of a VERY few sources of relevant and accurate information in this space.
The Symantec ‘s “Cyclosa gang” blog has some real good information on it. Very Interesting stuff
Kudos to Krebs! I mean that.
My head was spinning at the inherent complexities of all of this cyber detective work……then……I tried to look at that chart!
And, translate back and forth like changing baseball caps from Russian to English and back into Russian.
[I’m still struggling from the transition for Windows 7 to Apple’s OSX…….sigh.]
Thanks, Brian Krebs.
See! …….really addled…..correct …” from the transition for” to read “..with the transition from…”
No problem. To be having variety of grammar eccentricities makes the analysis of the individual many more difficult (stylometry) . 🙂
http://cci.drexel.edu/faculty/jli/docs/Jounals/Zheng_2006JASIST_AuthorshipIdentification.pdf
It’s worth a read, but I question question it’s value against sophisticated adversaries as it often comes down to “do they know, that you know that they know that you know.. ” sort of thing.
So his previous address was where the Olympics were located? The same Olympics with the stories of hacking, video cameras in the bathroom, Russians saying you should have no expectation of privacy….that Sochi?
Not to seem overly paranoid but a number of conspiracy theories could be derived out of that correlation.
Putin just played the Epic Face Palm Card.
http://www.reuters.com/article/2014/03/27/us-ukraine-russia-putin-payments-idUSBREA2Q0TU20140327
Putin tells West Russia will develop own card payment system.
…”It is really too bad that certain companies have decided on … restrictions,” Putin said, without naming Visa or MasterCard. “I think this will simply cause them to lose certain segments of the market – a very profitable market.”
I think the Daily Show has it nailed:
http://thedailyshow.cc.com/videos/5h8y05/putin-doesn-t-give-a-s–t?xrs=share_copy_email
I saw that one. It would have been more impressive if they hadn’t censored it.
Doesn’t our CIA take care of this kind of thing for American citizens? or are they too busy?
If you mean by “take care” that they assassinate foreign citizens, then sure, they have been known to take care of these kinds of things.
Since stealing identities is worse than stealing a horse, maybe this scale crime should be a capital one, and that Ayakimyan be the recipient of something fatal.
What’s up with the ssndob@ssa.gov login? Bogus, hacked, or ?
Lets just hope Turkey can keep the Russian newly expanded Navy within the Black Sea.
Notice the site is down, but ssndob. so is up. Same guy?
Hey Brian. I donno if you’ll see my tweets. here’s some more information for you:
his email gloryon.armand@yandex.ru
blog: http://abkhazia.gloryonjournal.ru/
skype: gloryon.armand (probably not using it)
domain registered on email: UCXOD.SU (dead already)
another domain: http://www.ucxod.ru
whoishistory for it: http://who.ru/simplesearch?domainsimple=ucxod.ru&sortby=asc
vk’s group of that church: vk.com/id167407009
twitter: twitter.com/ucxodchurch
and there is a “friend” of that vk’s group: http://vk.com/armandii (Armand, DOB: August 27 1989, lives in Krasnodar)
his cell-phone number: +79384165916
both the .so and .cc sites are up and going strong, hosted on cloudflare, or crimeflare as we call it. same guy, more than likely. folk’s this is about as close to America as these pukes will ever get. and most of them don’t live that long that play in this arena. so just pick up the pieces, dust yourselves off and move along. after a while the problem usually takes care of itself.
If I were a resident of Nevada I would not vote for you. I also do not plan on voting for Christie.
you’re funny FARO, you really think Harry M. Reed wrote this? heheh. Harry doesn’t even remember he says stuff that is recorded of him saying it! you’re a good sport though. Harry may not even know how to read without a teleprompter, just like his hero.
have a great weekend
harry m. reed [not]
Admitting I have not read your article in its full length, I’d like to have pointed out that SSN stands for social security # and DOB is refering to date of birth.
Given the continued vast geographical and cultural ignorance and apparent accompanying glee and non-understanding of anything out of most peoples’ worldviews in general (CIS, Ukraine, Russia, Georgia), let me just say I am disgusted that so many of you seem so willing to place judgments on what is or is not right for countries, yet you do not even know what is Europe from not Europe, and (looking at you Brian) seem to think this is some Cold War Adversarial Shit. The ones who don’t think so simply know who you are, and you have my respect; to the rest, perhaps you should stop trying to tell everybody else what is right for them if you do not even know that Georgia is a country.
This said, here we are again with yet another of these ‘doxings’ that make Brian litle more than a script kiddie himself, trouncing all over the rights of non-convicted people and doing more than the people he is writing about as far as invading privacy. Do I know this person? No. But neither do you. Does not mean I support it, and should not have to to see that this sort of thing is unethical at its core at worst and at best about as mature as a 12 year old girl.
And it remains that any idiot can still go online through the site’s data source itself or any of a hundred other web sites and get the same information as this guy offered — maybe even cheaper — so what the point is to even attempted ‘exposes’ on this shit any way continues to elude me. This is like blaming the dog for pooping on the floor when you did not do the responsible thing and take care of it in the first place — and then shaming the dog. This data should not be available “legitimately” to anybody so why should it be so much better or worse depending on who you bought it from? Almost all data sellers are data resellers — and the ones that are not are still selling it to the resellers. Change the way shit is done. This guy is a minnow.
The attitudes in these blogs and the comments bother me too much to read much any more, especialy with all that is going on here, but I know you have come to expect my responses to these ‘doxings’, Brian, and I hope that some day the hypocrisy will stop and it will be just as illegal to do this as what you scorn them for doing. Maybe if you ever do a technical story again, I will reply, as always, with informative answers, but this is turning into more and more of a ‘gossip magazine’ with every day.
Please, enjoy your life story movie and continue to ignore the larger issues. You always have, and it would be a shame for you to adopt an integrationist thought process this late in your life. 🙂
Ah yes, I just made my first comment in several weeks and it apparently is moderated. Oh well.
Generally, those laced with profanity and insults against other readers get automatically moderated without my help. This is one example. There have been countless other comments of yours that land in moderation without any help from me.
I can’t say I’m sorry to see you go, Voksalna. You continue to angrily blame everyone else *except* the very people responsible for engaging in computer crimes, or cause a lot of hand waving over how there are more important things for reporters to be concerned with (such as the NSA, etc).
That’s funny. The way I see it those things — and many others — are crimes as well — you just choose to pick what you agree with and don’t agree with. The world is not so simple. This has always — ALWAYS — been my point. There is no black or white. You are certainly not totally white and they are certainly not totally black. Everything has a pushback. I never said I didn’t blame the people responsible for computer crimes — you put these words in my mouth, and I have repeatedly said I do not support it — the difference between us, I believe, that is most fundamental, is that you only see as a crime what is convenient, even though the other stuff will almost certainly have a far greater impact on your own life. I don’t just mean the government shit and I never repeated over and over you should cover it — but why should you ignore it either? And how can you not see ‘Big Data’ as just as much at fault for using and abusing people as you see people making a few thousand dollars a month. Sure it’s illegal. I’m not supporting that. But I’m baffled at how you continue to not see the other side of the story, ever.
No big data, no big data breaches. Privacy in place, no chance to invade privacy. How is this complicated?
Voksalna, I am confused. You point to the presence of big data complicating things, while acknowledging that the theft of that data is illegal. It would seem to be no different than saying that a neighborhood of gigantic mansions filled with expensive things complicates our perception regarding a rash of thefts in that same neighborhood. Additionally, maintaining a secure environment is a constantly evolving challenge. New exploits, new tools, new angles approached by new people. The only way to completely secure yourself is to unplug. It’s not grey. Innocent people have their financial identities completely messed up. Not very grey. Last of all, there are plenty of people out there who are speaking about the NSA, etc. This is Kreb’s site, and he writes about what he thinks is important. He does not have to give every idea or opposing view a platform. That’s a silly expectation (a fallacy in logic, really).
Hello Brandon,
I am not sure how you came to this conclusion, so perhaps I did not express myself very eloquently (likely, given my mood — my apologies).
My argument is that Big Data should not be allowed to collect these things, warehouse them, buy them, and sell them. If you are American, you may not know most of the data from sites like these came from Social Security Headers, DMV records, Voting (yes voting) registration, and the like. You do not have the right or ability to ‘opt out’ — and this is older, far older, than you probably realise — many decades. Research things like TRW 50 years ago.
My argument is that this data should not be permitted to be collected by any person other than who collected it (I am not so unreasonable as to think people do not need to keep records at all), nor aggregated, and certainly not sold to random people — also not new with the web. Now multiply this by the power of the web and you have a far larger problem — exposure that it exists.
This is where breaches begin and end: something can not be taken or stolen if it is not permitted to be bought or sold for profit by a company or your very own government in any way other than how you agreed for it to be used.
To give another example – a lot of the Target mess is precisely a result of their massive data warehousing. The cards can be and mostly are being replaced, but the extensive PII they collected should have never been permitted by law or otherwise; if this is not collected, aggregated, and used for ‘marketing purposes’ then this cannot be sold — or accessed by somebody. You cannot access what does not exist, and all data will be abused if it can be abused. It is generally poor form to believe anything other than that any database that exists can and will be exploited and/or hacked — if not by an outsider, then by an employee or the company itself.
Voksalna, thanks for the reply. From what I understand about the Target situation (and I may be wrong on this), the breach was capturing data as it was being processed, as opposed to an actual collection of previously stored data. In regards to the CC info, the only way around that is to not take cards (I am hopeful that we move to the pin & chip format one day).
Yes, I think our misunderstanding was the use of the term big data, which I assumed you meant in a very general sense. It’s true, the collection and dissemination of PI is a source of concern, and I don’t think that BK would argue that point. We do find ourselves at greater risk in an environment that does not always completely regulate how that data is stored and used, in a nation where corporate security is also not regulated.
However, even if less data was stored, and even if regulations were implemented or improved, the fact is that this information would still be out there, CC’s would still be used, and the draw of lucrative theft would still result in people attempting to get that information. Furthermore, the nature of technology assumes that people with skill will always find new and inventive methods of being successful. This is why websites like this are imporant. It’s a place where we can read about how to protect ourselves from these bad actors. It doesn’t mean that the other issues don’t exist, that information is out there, and there are pages dedicated to those subjects. But you have to admit that BK providing this information empowers those of us who are entrusted with PI to think and act, and potentially be prepared for the fallout of acting. It’s all instructive.
Debate is good, and nothing beats a calm, reasoned point of view. 🙂
And where did I insult anybody? ‘Ignorance’ is a word meaning ‘not knowing’; I can see no reason in a world where almost all human information is available a click or a web search away to not look at a map or ‘Google’. I never said ‘stupid’. In general I believe people choose not to be informed because the alternative is very often painful and cognitively dissonant.
I guess that means you will not be posting it, then. Pity. I suppose it is not good to point out a cognitive bias in general on a blog — can look too much like trolling. On a blog. It is merely my belief that a journalist should have in mind the bigger picture. It is an insult to me to say that I condone crime — my posts have never condoned crime. I’ve only (repeatedly) tried to emphasise that criminals on BOTH sides be treated with the same stroke of the pen. That is what journalism is supposed to be, or rather the journalism that I used to respect from your country. But this is a blog so I probably am in the wrong place any way.
I never positioned myself as your enemy so it comes as somewhat of a surprise that you would see me as ‘black’ here — and it probably shouldn’t. And that is my ignorance.
Be well.
You continue to think that I am moderating your comments Voksalna when I am not. I’ve tried to explain this to you and others who complain about moderated comments that if you choose to use profanity in your posts, you can expect them to get held in the spam folder, which means they could stay there.
And I would humbly appreciate if you would post my response to your response. Thank you.
“An attacker who successfully exploited the vulnerability could gain the same user rights as the current user and then elevate those rights to those of a domain administrator.”
I do not see that in the advisory you are linking to. Did Microsoft remove it?
In any event, its poorly worded as it makes it sound like the exploit will allow one to become a domain admin just through this exploit. However, the current wording states that the attacker will gain the same rights as the compromised user, so if they have domain admin rights then the attacker will as well.
I apologize – for some reason this comment posted under the wrong article.
wefewf
I no longer use my real name and date of birth on web sites and e mail programs requiring details.