-Sept. 9, 12:30 p.m. CT, Yucatan Peninsula, Mexico: Halfway down the southbound four-lane highway from Cancun to the ancient ruins in Tulum, traffic inexplicably slowed to a halt. There was some sort of checkpoint ahead by the Mexican Federal Police. I began to wonder whether it was a good idea to have brought along the ATM skimmer instead of leaving it in the hotel safe. If the cops searched my stuff, how could I explain having ultra-sophisticated Bluetooth ATM skimmer components in my backpack?
The above paragraph is an excerpt that I pulled from the body of Part II in this series of articles and video essays stemming from a recent four-day trip to Mexico. During that trip, I found at least 19 different ATMs that all apparently had been hacked from the inside and retrofitted with tiny, sophisticated devices that store and transmit stolen card data and PINs wirelessly.
In June 2015, I heard from a source at an ATM firm who wanted advice and help in reaching out to the right people about what he described as an ongoing ATM fraud campaign of unprecedented sophistication, organization and breadth. Given my focus on ATM skimming technology and innovations, I was immediately interested.
My source asked to have his name and that of his employer omitted from the story because he fears potential reprisals from the alleged organized criminal perpetrators of this scam. According to my source, several of his employer’s ATM installation and maintenance technicians in the Cancun area reported recently being approached by men with Eastern European accents, asking each tech if he would be interested in making more than 100 times his monthly salary just for providing direct, physical access to the inside of a single ATM that the technician served.
One of my source’s co-workers was later found to have accepted the bribes, which apparently had only grown larger and more aggressive after technicians in charge of specific, very busy ATMs declined an initial offer.
My source said his company fired the rogue employee who’d taken the bait, but that the employee’s actions had still been useful because experts were now able to examine the skimming technology first-hand. The company tested the hardware by installing it into ATMs that were not in service. When they turned the devices on, they discovered each component was beaconing out the same Bluetooth signal: “Free2Move.”
Turns out, Free2Move is the default name for a bluetooth beacon in a component made by a legitimate wireless communications company of the same name. I also located a sales thread in a dubious looking site that specializes in offering this technology in mini form for ATM PIN pads and card readers for $550 per component (although the site claims it won’t sell the products to scammers).
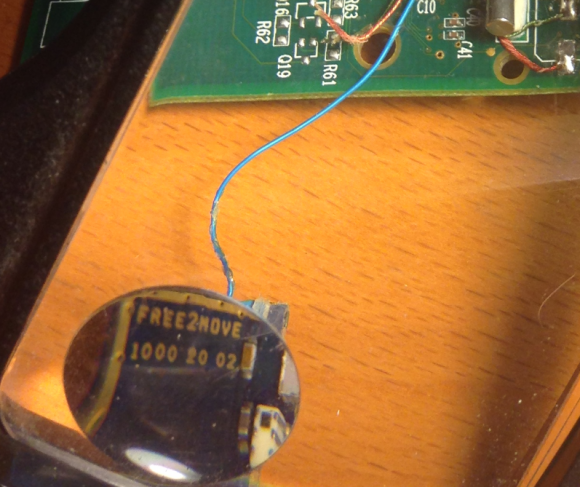 The Bluetooth circuit boards allegedly supplied by the Eastern Europeans who bribed my source’s technician were made to be discretely wired directly onto the electronic ATM circuit boards which independently serve the machine’s debit card reader and PIN pad.
The Bluetooth circuit boards allegedly supplied by the Eastern Europeans who bribed my source’s technician were made to be discretely wired directly onto the electronic ATM circuit boards which independently serve the machine’s debit card reader and PIN pad.
Each of the bluetooth circuit boards are tiny — wafer thin and about 1 cm wide by 2 cm long. Each also comes with its own data storage device. Stolen card data can be retrieved from the bluetooth components wirelessly: The thief merely needs to be within a few meters of the compromised ATM to pull stolen card data and PINs off the devices, providing he has the secret key needed to access that bluetooth wireless connection.
Even if you knew the initial PIN code to connect to the Bluetooth wireless component on the ATM —the stolen data that is sent by the bluetooth components is encrypted. Decrypting that data requires a private key that ostensibly only the owners of this crimeware possess.
These are not your ordinary skimming devices. Most skimmers are detectable because they are designed to be affixed to the outside of the ATMs. But with direct, internal access to carefully targeted cash machines, the devices could sit for months or even years inside of compromised ATMs before being detected (depending in part on how quickly and smartly the thieves used or sold the stolen card numbers and PINs).
Not long after figuring out the scheme used by this skimmer, my source instructed his contacts in Cancun and the surrounding area to survey various ATMs in the region to see if any of these machines were emitting a Bluetooth signal called “Free2Move.” Sure enough, the area was blanketed with cash machines spitting out Free2Move signals.
Going to the cops would be useless at best, and potentially dangerous; Mexico’s police force is notoriously corrupt, and for all my source knew the skimmer scammers were paying for their own protection from the police.
Rather, he said he wanted to figure out a way to spot compromised ATMs where those systems were deployed across Mexico (but mainly in the areas popular with tourists from Europe and The United States).
When my source said he knew where I could obtain one of these skimmers in Mexico firsthand, I volunteered to scour the tourist areas in and around Cancun to look for ATMs spitting out the Free2Move bluetooth signal.
I’d worked especially hard the previous two months: So much so that July and August were record traffic months for KrebsOnSecurity, with several big breach stories bringing more than a million new readers to the site. It was time to schedule a quasi-vacation, and this was the perfect excuse. I had a huge pile of frequent flier miles burning a hole in my pocket, and I wasted no time in using those miles to book a hotel and flight to Cancun.
CANCUN
There are countless luxury hotels and resorts in Cancun, but it turned out that the very hotel I picked — the Marriott CasaMagna Hotel — had an ATM in its lobby that was beaconing the Free2Move signal! I had only just arrived and had potentially discovered my first compromised ATM.
However, I noticed with disappointment that for some reason all of my Apple devices — an iPhone 5, a late-model iPad, and my Macbook Pro — had trouble reliably detecting and holding the Free2Move signals from one of the two ATMs situated in the hotel lobby.
I decided that I needed a more reliable (and disposable) phone, so I hopped in the rental car for a quick jaunt down the road to the local TelCel store (TelCel is Mexico’s dominant mobile provider and a company owned by the world’s second-richest man — Carlos Slim). After perusing their phones, I selected a Huawei Android phone because — at around USD $117 — it was among the cheapest smartphones available in the store. Also, the phone came with plenty of call minutes and a semi-decent data allowance, so I could now avoid monstrous voice and data roaming charges for using my iPhone in Mexico.
Nearby the TelCel store was Plaza Caracol — a mall adjacent to a huge tourist nightlife area that is boisterous and full of Americans and Brits on holiday. The car parked in the mall’s garage, I pulled out my new Huawei phone and turned on its bluetooth scanning application. The first ATM I found — a machine managed by ATM giant Cardtronics — quickly showed it was beaconing two Free2Move signals.
Returning to the Marriott hotel, I found that the two Free2Move bluetooth signals showed up consistently and reliably on my new phone’s screen after about 5 seconds of searching for nearby bluetooth connections. The compromised ATM in the hotel also was a Cardtronics system.
At this point, I went to the front desk, introduced myself and asked to speak to the person in charge of security at the CasaMagna. Before long, I was speaking with no fewer than six employees from the hotel, all of us seated around a small coffee table overlooking the crystal-blue ocean and the pool. I explained the situation and everyone seemed to be very concerned, serious, asking smart questions and nodding their heads.
A man who introduced himself as the hotel’s loss prevention manager disclosed that Marriott had recently received complaints from a number of guests at the hotel who saw fraud on their debit cards shortly after using their ATM cards at the hotel’s machine. The loss prevention guy said the company responsible for the ATM — Cardtronics — had already sent someone out to review the integrity of the machine, but that this technician could not find anything wrong.
[SIDE NOTE: That technician may have only inspected the exterior of the machine before giving it a clean bill of health. Another explanation is that the technician that was sent to find skimming devices didn’t report their presence because he was the one who installed them in the first place!]
That same day, I phoned Giovanni Locandro, senior vice president of North American business development at Cardtronics. He told me the company conducts periodic “sweeps” in Mexico to look for skimming devices on its machines and that it was in the process of doing one at the moment down there, although he didn’t acknowledge whether he was familiar with the exact scheme I was describing.
“We are doing another sweep as we speak down there,” Locandro said. “We do random sweeps, especially in tourist areas to check for those devices. But we haven’t heard of any cards being cloned. Any devices we receive we take those to our internal security folks, and then we contact the authorities.”

I couldn’t dissuade these young ladies and many others from using the compromised machine on my second evening at the hotel.
I showed the hotel folks the bluetooth beacons emanating from the ATMs in the lobby, and showed them how to conduct the same scans on their phones. Everyone roundly agreed that the technician had to be called again. But there were two ATMs in the lobby — one dispensing Mexican Pesos and another dispensing only dollars. How to know which ATM is compromised, they asked? Unplug them one by one, I replied, and you’ll see very quickly which cash machine is hacked because the bluetooth beacon would shut off.
Despite more head nods and a round of verbal agreement from the hotel staff that this was a good idea, to my surprise nobody at the hotel bothered to touch the machine for two more days. I watched countless people withdraw money from the hacked ATM; some of those I warned while in the lobby were appreciative and seemed to grasp that perhaps it was best to wait for another ATM; others were less receptive and continued with their transactions.
The next morning — after verifying that the hotel’s ATM was still compromised and trying in vain to hail the security folks again at the hotel — I headed out in the rental car. I was eager to visit some of the other more popular tourist destinations about an hour to the south of Cancun, including Playa del Carmen, Tulum and Cozumel. I wanted to see how many of those towns were hacked by this same skimming crew.
I was about to learn that the true scope of this scam was far larger than I’d imagined.
If you haven’t already done so, please check out Part II and Part III of this investigative series:






Damn you! Why did you end the video/article I was loving it ;(
Great work. Wow those hotels/atm owners don’t give a crap about their customers.
I could be wrong, but from what Brian wrote, it seems it was someone in the ATM business that leaked the story?
Someone had to give a crap!
ummmm… I think the words are “in cahoots”… hotel security was bought out, too… now, if this was escalated to Marriott Corporate then sh!t would be hitting the fans. Local pockets is the theme here…
Excellent article! Well, all KOS articles are excellent. But for this article it seems like I’m watching a movie full of thrills. I can’t wait to read the next part. Bryan, I think you should consult Hollywood for a movie.
Thanks.
It might be too late for that, I think Sony Pictures bought the rights (or at least were interested in buying the rights) to the life story of Brian Krebs.
http://krebsonsecurity.com/2014/03/sony-pictures-plans-movie-about-yours-truly/
I would love see this movie please make it happen!
Wow, Brian! That reads like a spy novel. When this security thing peters out (hah!), you might have a career in spy fiction. Just don’t get thrown in some Central American jail, never to be heard from again researching your stories! Please be careful.
Please, more installments. Soon!
+1
You are a braver man than I telling the Marriott guys about this. Next thing, they have you arrested and thrown in jail for 6 months.
Allowing the compromised ATM to function while the loss prevention team liases with the criminals to ensure all losses happen AFTER the customer departs the premises is far better for business than trying to fight off the cartels.
One assumes there’s kickbacks, too.
Now waiting impatiently to see if that’s what Brian found. POST YOUR NEWS FASTER, damnit.
wow
Great story! Did you have any hesitation divulging the scam details to the 6 Mariott employees? 6 is a lot of people. What if any one of them were in on the scam, or other scams?
In a corrupt society, it is better to alert more people than less, in the hopes of getting the information to someone who isn’t corrupt.
It may be said that you are increasing the risk to yourself of some form of comeback, but by entering into that scene to start with you wither go balls deep or don’t bother. You know what you are getting yourself into.
Marriott employees don’t have access to ATMs, other than using the space in the lobby they are not under Marriott control . The only person able to insert the device would be an ATM tech or an impersonator of such a tech. A Marriott employee messing with ATM will arise suspicion right on.
Great story Brian. That’s what I call an interesting vacation. Can’t wait to hear the rest.
So we should do a Bluetooth security check on the ATM before we draw cash!
Easy!
Another great piece Brian Krebs although not a surprise, I recall a conversation with a Bank Security head from Mexico at an organised crime conference in Atlanta GA back in the mid 1990’s. He voiced concern over drug cartels potentially buying/moving into legitimate Bank Technology manufacturing suppliers with a view to compromising technology at the point of manufacture. Although this never knowingly came to fruition, the ever increasingly sophisticated attacks on compromising POS terminals has since the early 1990’s has continued over the decades despite huge efforts by manufacturers to render devices ‘tamper proof’ the last huge tranche of attacks swept across central Europe and the US from eastern Europe just a few years ago and again involved attached blue tooth devices and circuit board capturing data and on these occasions once full dialing out and downloading via a Canadian based web site from which the data was harvested.. As in your current mode of compromise on ATM’s the common weak link continues to be the ‘human factor’ where authorised staff are recruited by very large cash payments threats or bribery, the downside for such corrupted employees is that they are the ones who end up behind bars…. greed is a great driver..
Given that they were informed of a potential breach, understood and ‘recognized’ that there were compromised machines but did nothing; Wouldn’t they now be on the hook with credit card companies for taking no action?
Be careful down there, Brian. Don’t gangs down there play much rougher than Russians?
—
Congratulation on a well-deserved trip to fight cyber crime at beach resorts — an awesome tax deduction verified by this article. What’s next? Cyber fraud at Club Meds? No really, I kid. Well done: sleuthing and scuba.
My only advice: don’t buy a timeshare.
Well, the main difference is that in Russia it is the government that is killing you. The maffia is actually a part of the official system.
the damn MARRIOT does not act after 2 days!?!? With the outrageous charges they apply, if the MANAGEMENT outside of mexico of this chain does not fire everyone involved immediately or remove the marriot name from it, they should be sued in some international courts.
This may be happening in Bali, too, especially in the Kuta/Cangu. My card was compromised from only ATM usage there. Same with a few others in our travel network. Pretty regular occurrence.
Insider fraud and bribed employees are difficult to detect but is there a chance that some if not many of these devices are being planted by fake technicians dressed in work attire, carrying a tool box? This could partially explain why so many are compromised as I believe it would be far less risky to do the fake tech approach rather than trying to find ATM techs who will take a bribe, although Mexico is full of bribe takers, so perfect target choice.
Why does Mexico continue to exist?
In para. 5, I think you mean to write “had still been useful,” not “had still be useful.” Really engaging – one of your best stories yet!
“Mexico’s police force is notoriously corrupt”
Now, there is a true statement!
I speak from personal experience.
Brian, can you provide a list of the ATMs that you found? It would help a great deal in identifying potentially compromised cards.
“If the cops searched my stuff, how could I explain having ultra-sophisticated Bluetooth ATM skimmer components in my backpack?”
American cops wouldn’t even know what that was.
“It’s for my iPhone”…
I think this article shows the virtue of concern over stolen data in Cancun and perhaps in greater Mexico as well by the lack of concern from the Hotel management. How could any security professional advise the availability of hacked systems to unwitting customers? It’s insane.
I’m excited for Part II of the series and it is a refreshing change with your VLOG, I don’t believe I’ve seen you do this before in the better part of 8 months that I’ve been following you, perhaps I’ve missed it. Maybe the juice will take you into the U.S. and discover more eye-opening stuff.
Moral of the story: you can’t count on an iphone to detect rogue bluetooth signals (totally in jest). I do look forward to part 2.
This is a great story! I used to work for NCR as a technician on ATM’s I would love to see pictures of what they did and how they did it. We were taught the basics of what to look for on the outsides of machines, but not the insides. I don’t work there any more but am still fascinated with how sophisticated criminals are getting.
Are you traveling with a security detail? If this is cartel, I can’t imagine them taking lightly to you blowing their skimming-op wide-open.
Not only excellent writing but kudos fo4r taking a vacation and being able to write it off your taxes too!
Years ago, my sister warned me about using ATMs. She was an attorney who was periodically assigned pro-bono cases by the court. Most of them required her to defend men who robbed people using an ATM. So I never got in the habit—and also did not have to pay the ridiculous fees.
I fear for you publishing this while still in Mexico. The criminals are much more powerful than anyone else there. Body count and public executions for trivial things means nothing to those animals.
I got back from Cancun on Thursday. There’s no way I would have published this while still there.
Yeah… I also noticed that you waited for two pretty gals to withdraw money before you took that photo… LOL 😉
🙂
Two of my family members ATM Cards were skimmed at the ATM outside the Chedraui in Puerto Aventuras (between Playa and Tulum) and then the cards were immediately “used” at the Tommy Hilfigers at a shopping mall in Cancun and a hostel in Playa. So there are inside guys who are merchants in the area and probably controlled by the Zeta. So PLEASE, YOU BE CAREFUL!
When you uncover a huge and this is huge crime syndicate like this your first recourse is to report the story to a big news org (AP, UPI, etc) and when you find such a machine in a hotel lobby, report it to the CORPORATE HQ in the US. Corporate Headquarters, speak to their Director of Security at
10400 Fernwood Road • Bethesda, Maryland 20817-1102 • 1.301.380.3000
The problem is neither Marriott nor Cardtronics has any real skin in the game. The only one that does is the cardholder’s bank which has no direct control over the compromised ATMs.
Hi Brian- thanks so much for sharing this piece. Maybe this is in part II, but I’d be interested to know if these thieves have infiltrated airport ATMs as well, and/or whether these ATMs are considered more “safe” than those in resorts.
Yes, I found an ATM at the airport in Cancun that was compromised as well. That’s in Part II.
If a financial institution seems lax about security, who can serve as a reality check on whether their actions are actually aboveboard, and if they’re likely not, who would you tell?