-Sept. 9, 12:30 p.m. CT, Yucatan Peninsula, Mexico: Halfway down the southbound four-lane highway from Cancun to the ancient ruins in Tulum, traffic inexplicably slowed to a halt. There was some sort of checkpoint ahead by the Mexican Federal Police. I began to wonder whether it was a good idea to have brought along the ATM skimmer instead of leaving it in the hotel safe. If the cops searched my stuff, how could I explain having ultra-sophisticated Bluetooth ATM skimmer components in my backpack?
The above paragraph is an excerpt that I pulled from the body of Part II in this series of articles and video essays stemming from a recent four-day trip to Mexico. During that trip, I found at least 19 different ATMs that all apparently had been hacked from the inside and retrofitted with tiny, sophisticated devices that store and transmit stolen card data and PINs wirelessly.
In June 2015, I heard from a source at an ATM firm who wanted advice and help in reaching out to the right people about what he described as an ongoing ATM fraud campaign of unprecedented sophistication, organization and breadth. Given my focus on ATM skimming technology and innovations, I was immediately interested.
My source asked to have his name and that of his employer omitted from the story because he fears potential reprisals from the alleged organized criminal perpetrators of this scam. According to my source, several of his employer’s ATM installation and maintenance technicians in the Cancun area reported recently being approached by men with Eastern European accents, asking each tech if he would be interested in making more than 100 times his monthly salary just for providing direct, physical access to the inside of a single ATM that the technician served.
One of my source’s co-workers was later found to have accepted the bribes, which apparently had only grown larger and more aggressive after technicians in charge of specific, very busy ATMs declined an initial offer.
My source said his company fired the rogue employee who’d taken the bait, but that the employee’s actions had still been useful because experts were now able to examine the skimming technology first-hand. The company tested the hardware by installing it into ATMs that were not in service. When they turned the devices on, they discovered each component was beaconing out the same Bluetooth signal: “Free2Move.”
Turns out, Free2Move is the default name for a bluetooth beacon in a component made by a legitimate wireless communications company of the same name. I also located a sales thread in a dubious looking site that specializes in offering this technology in mini form for ATM PIN pads and card readers for $550 per component (although the site claims it won’t sell the products to scammers).
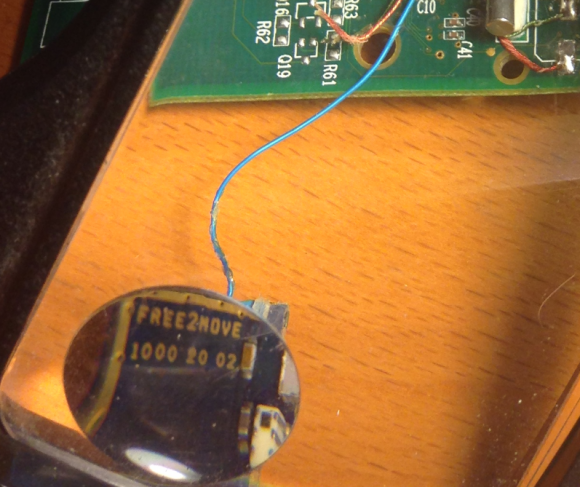 The Bluetooth circuit boards allegedly supplied by the Eastern Europeans who bribed my source’s technician were made to be discretely wired directly onto the electronic ATM circuit boards which independently serve the machine’s debit card reader and PIN pad.
The Bluetooth circuit boards allegedly supplied by the Eastern Europeans who bribed my source’s technician were made to be discretely wired directly onto the electronic ATM circuit boards which independently serve the machine’s debit card reader and PIN pad.
Each of the bluetooth circuit boards are tiny — wafer thin and about 1 cm wide by 2 cm long. Each also comes with its own data storage device. Stolen card data can be retrieved from the bluetooth components wirelessly: The thief merely needs to be within a few meters of the compromised ATM to pull stolen card data and PINs off the devices, providing he has the secret key needed to access that bluetooth wireless connection.
Even if you knew the initial PIN code to connect to the Bluetooth wireless component on the ATM —the stolen data that is sent by the bluetooth components is encrypted. Decrypting that data requires a private key that ostensibly only the owners of this crimeware possess.
These are not your ordinary skimming devices. Most skimmers are detectable because they are designed to be affixed to the outside of the ATMs. But with direct, internal access to carefully targeted cash machines, the devices could sit for months or even years inside of compromised ATMs before being detected (depending in part on how quickly and smartly the thieves used or sold the stolen card numbers and PINs).
Not long after figuring out the scheme used by this skimmer, my source instructed his contacts in Cancun and the surrounding area to survey various ATMs in the region to see if any of these machines were emitting a Bluetooth signal called “Free2Move.” Sure enough, the area was blanketed with cash machines spitting out Free2Move signals.
Going to the cops would be useless at best, and potentially dangerous; Mexico’s police force is notoriously corrupt, and for all my source knew the skimmer scammers were paying for their own protection from the police.
Rather, he said he wanted to figure out a way to spot compromised ATMs where those systems were deployed across Mexico (but mainly in the areas popular with tourists from Europe and The United States).
When my source said he knew where I could obtain one of these skimmers in Mexico firsthand, I volunteered to scour the tourist areas in and around Cancun to look for ATMs spitting out the Free2Move bluetooth signal.
I’d worked especially hard the previous two months: So much so that July and August were record traffic months for KrebsOnSecurity, with several big breach stories bringing more than a million new readers to the site. It was time to schedule a quasi-vacation, and this was the perfect excuse. I had a huge pile of frequent flier miles burning a hole in my pocket, and I wasted no time in using those miles to book a hotel and flight to Cancun.
CANCUN
There are countless luxury hotels and resorts in Cancun, but it turned out that the very hotel I picked — the Marriott CasaMagna Hotel — had an ATM in its lobby that was beaconing the Free2Move signal! I had only just arrived and had potentially discovered my first compromised ATM.
However, I noticed with disappointment that for some reason all of my Apple devices — an iPhone 5, a late-model iPad, and my Macbook Pro — had trouble reliably detecting and holding the Free2Move signals from one of the two ATMs situated in the hotel lobby.
I decided that I needed a more reliable (and disposable) phone, so I hopped in the rental car for a quick jaunt down the road to the local TelCel store (TelCel is Mexico’s dominant mobile provider and a company owned by the world’s second-richest man — Carlos Slim). After perusing their phones, I selected a Huawei Android phone because — at around USD $117 — it was among the cheapest smartphones available in the store. Also, the phone came with plenty of call minutes and a semi-decent data allowance, so I could now avoid monstrous voice and data roaming charges for using my iPhone in Mexico.
Nearby the TelCel store was Plaza Caracol — a mall adjacent to a huge tourist nightlife area that is boisterous and full of Americans and Brits on holiday. The car parked in the mall’s garage, I pulled out my new Huawei phone and turned on its bluetooth scanning application. The first ATM I found — a machine managed by ATM giant Cardtronics — quickly showed it was beaconing two Free2Move signals.
Returning to the Marriott hotel, I found that the two Free2Move bluetooth signals showed up consistently and reliably on my new phone’s screen after about 5 seconds of searching for nearby bluetooth connections. The compromised ATM in the hotel also was a Cardtronics system.
At this point, I went to the front desk, introduced myself and asked to speak to the person in charge of security at the CasaMagna. Before long, I was speaking with no fewer than six employees from the hotel, all of us seated around a small coffee table overlooking the crystal-blue ocean and the pool. I explained the situation and everyone seemed to be very concerned, serious, asking smart questions and nodding their heads.
A man who introduced himself as the hotel’s loss prevention manager disclosed that Marriott had recently received complaints from a number of guests at the hotel who saw fraud on their debit cards shortly after using their ATM cards at the hotel’s machine. The loss prevention guy said the company responsible for the ATM — Cardtronics — had already sent someone out to review the integrity of the machine, but that this technician could not find anything wrong.
[SIDE NOTE: That technician may have only inspected the exterior of the machine before giving it a clean bill of health. Another explanation is that the technician that was sent to find skimming devices didn’t report their presence because he was the one who installed them in the first place!]
That same day, I phoned Giovanni Locandro, senior vice president of North American business development at Cardtronics. He told me the company conducts periodic “sweeps” in Mexico to look for skimming devices on its machines and that it was in the process of doing one at the moment down there, although he didn’t acknowledge whether he was familiar with the exact scheme I was describing.
“We are doing another sweep as we speak down there,” Locandro said. “We do random sweeps, especially in tourist areas to check for those devices. But we haven’t heard of any cards being cloned. Any devices we receive we take those to our internal security folks, and then we contact the authorities.”

I couldn’t dissuade these young ladies and many others from using the compromised machine on my second evening at the hotel.
I showed the hotel folks the bluetooth beacons emanating from the ATMs in the lobby, and showed them how to conduct the same scans on their phones. Everyone roundly agreed that the technician had to be called again. But there were two ATMs in the lobby — one dispensing Mexican Pesos and another dispensing only dollars. How to know which ATM is compromised, they asked? Unplug them one by one, I replied, and you’ll see very quickly which cash machine is hacked because the bluetooth beacon would shut off.
Despite more head nods and a round of verbal agreement from the hotel staff that this was a good idea, to my surprise nobody at the hotel bothered to touch the machine for two more days. I watched countless people withdraw money from the hacked ATM; some of those I warned while in the lobby were appreciative and seemed to grasp that perhaps it was best to wait for another ATM; others were less receptive and continued with their transactions.
The next morning — after verifying that the hotel’s ATM was still compromised and trying in vain to hail the security folks again at the hotel — I headed out in the rental car. I was eager to visit some of the other more popular tourist destinations about an hour to the south of Cancun, including Playa del Carmen, Tulum and Cozumel. I wanted to see how many of those towns were hacked by this same skimming crew.
I was about to learn that the true scope of this scam was far larger than I’d imagined.
If you haven’t already done so, please check out Part II and Part III of this investigative series:






Wow, great story Brian! I was curious as to what happened to the technician who installed the skimmers in the ATMs. I know you said he was fired, was he ever arrested or anything of the nature?
Having lived in Baja, Mexico for about 8 years, I am not at all surprised that there was no action taken at the hotel. My experience has been that many employees here are not empowered to act outside their daily responsibilities. It wouldn’t even surprise me if you’d said you’d gone to a bank and they hadn’t deactivated a compromised ATM.
This is probably in part II but can you connect to the Bluetooth signal and access the data? That is just crazy. You would think they would protect it with a pincode of some kind. I wonder if anything like that is happening in the U.S. Great story!
It is explained in the article 🙂
“Even if you knew the initial PIN code to connect to the Bluetooth wireless component on the ATM —the stolen data that is sent by the bluetooth components is encrypted. Decrypting that data requires a private key that ostensibly only the owners of this crimeware possess”
Wow… .. I’m assuming that in an operation that pulls in this much money, the people that operate it are not “nice”.. do you have any concerns ?
@Ricardo:
“Even if you knew the initial PIN code to connect to the Bluetooth wireless component on the ATM —the stolen data that is sent by the bluetooth components is encrypted. Decrypting that data requires a private key that ostensibly only the owners of this crimeware possess.”
Great Article! I was just visiting Puerto Morelos and am always paranoid about sketchy ATM’s. The hotel had a USD ATM that charged an arm and a leg in the lobby for guests, and a second ATM hidden in the employees area downstairs in the basement. I was contemplating a withdrawal and I asked a worker that I had befriended about ATM fees and he directed me to the employees ATM, mentioning something about how the lobby ATM was not safe and a rip-off. I wonder if the lobby ATM was giving the Bluetooth signal? On the 10th the lobby machine had an out of order sign on it. Coincidence?
I’m looking forward the the next article.
I guess we are going back to 1960’s style traveler’s checks and adding the 1 or 2 hours it takes to exchange them to your vacation schedule.
Did you check bank ATM’s on this trip? HSBC, Banamex, Banco Azteca, Bancomer etc? What models of ATM are effected by this? Give us something to go on so we don’t get ripped off. Mexico is filled with thousands of American expat tech works living in $250/month apartments. You can live for a year on what one month of rent in SF costs.
Why can’t the ATM’s be configured to work with Apple Pay or Google Wallet?
Thank you for your article. So important. While my mother was dying her VISA bank card was skimmed in Mexico. For some reason, her card was attached to her investment account, which had a substantial amount of cash in it. By the time, she had died and all her paperwork had been processed a year later, the account had lost around $90-thousand dollars. That would have been my inheritance. Skimmers had been holidaying in the Dominican Republic taking out small amounts of money at a time–usually $267.00 or $216.00–thereby avoiding setting off any alarm bells. I was only reimbursed half of that money. It was heartbreaking. If my mother had lived, and not figured it out, she would have found herself aging and penniless in Mexico! It’s so important that people be made aware of this. But how are we to protect ourselves in future?
Well, that is one reason why you should not attach your main accounts to a card. Rather, keep only one account attached – a checking account – and keep a minimum amount of money in there.
Keep in mind too that most banks (even credit unions) will not reimburse for money taken via debit cards. So anything lost is your loss. You’re quite lucky they reimbursed you 50%.
Sadly, one of the main reasons people do attach larger accounts to their debit cards is the transaction fees that banks often put in place, even when you’re transferring your own money between accounts at the same bank!
“Keep in mind too that most banks (even credit unions) will not reimburse for money taken via debit cards. So anything lost is your loss. You’re quite lucky they reimbursed you 50%.”
True if you live (and bank) in the backwater of banking technology and regulation that is the United States of America. Not true anywhere with competent banking regulation (Canada, the UK, most of western Europe). The US is so astonishingly behind on payments tech and regulation that it is appalling.
Well, when I was living in Arizona, U.S.A. (2010), and had my debit card # ripped off for about $1,200.00. I was reimbursed for all but $1.00.
Be careful of declaring the U.S. as a backwater environment. You might just be incorrect on several accounts.
I just came back from the Playa area late August and my wife had noticed when she got back, her credit card company informed her that someone tried to user her card in Cancun.
Great piece of investigative journalism! I’m eager to read part II.
Side question, is there any good reason for a non compromised ATM to emit a BlueTooth signal?
If no, I assume it’d be best practice to do a quick scan with our smartphones before using any ATMs.
There are so many bluetooth signals in a well traveled area that you would have to able to tell apart legitimate ones from the ones from an ATM.
At the point of the end of this episode, aren’t you worried all the hotel management are in on it and will have you murdered before you find out more?
I wonder what the ATM machines at banks were like.
I typically try to avoid any ATM machine that is movable. In the US, at home, I’ll use my grocery transactions to make withdrawls when I need cash; however, when abroad I’ve tried to stick only to ATMs embedded in bank walls, and stick with the same bank throughout the trip if at all possible, and to a specific amount so that all the transactions are the same.
So just curious whether that would end up being any safer in the schemes…
“How to know which ATM is compromised, they asked? Unplug them one by one” – having to point this out to them speaks volumes about their ability to troubleshoot and contain the risk
Nice piece of work Brian. Next time – take a real vacation!
Might be worth it to do a little bluetooth ATM wardriving here in the U.S.
Can you reveal the process and/or program you used so that we can also detect the bluetooth signal? Would be nce to check before using an ATM. I live in the Mayan Riviera and the problem has been epidemic here.
Frank,
I just used a smartphone. Most smartphones have a feature in the settings that lets you search for bluetooth devices to connect to. That’s all this was.
Temporal Being and Patrick,
Have you ever heard of Regulation E? Before you spout absurdities about US banks and credit unions “choosing” how much they will reimburse consumers for fraudulent transactions, I would suggest you read it.
Not to mention Visa’s zero-liability policy banks have to uphold for the privilege of issuing Visa cards. MasterCard has a similar policy. The reimbursement of only 50% was likely due to reporting timeframe expiration of the fraud.
Great article Brian, really looking forward to part 2.
One thing that puzzles me with such a sophisticated operation such as this…. Why would the criminals leave these Bluetooth devices in discoverable mode broadcasting it’s name for anyone with a smartphone to see. With a name like Free2move, maybe they were trying to incognito as a free WiFi provider, but surely the logical step would have been for the attackers to keep the devices in non discoverable mode and just have a map of the rigged atms. Or maybe I’m completely overlooking something, perhaps a Bluetooth technical limitation?
I live in Playa del Carmen and everyone I know there has had their credit cards hacked…including me. Thanks for teaching the locals how to assess the situation…I hope they learn how to stop it.
I contacted u about target Walmart and more.I am in trouble.Big my twitter is locked and I will create a new account tomorrow .I have to get a new phone number.My place was robbed of just an iPad phone and SD card.I cannot go to police I need help real bad.After police and firemen have attacked me I am involved in Justin Ross Harris case.Help what can I do
Take your meds.
I used to work for a consultation firm and had a bid on auditing a gas station that has the problem of the same technique but against gas pump this was in the US. FYI.
Very interesting information. Thanks! I live in this area and read this just before I was heading out to the ATM, so I checked, but saw no Free2Move signals in the vacinity of the ATMs at Centro Maya in Playa del Carmen, or the Chedraui in Puerto Aventuras. Interestingly, the Santander ATM inside the gated marina community of Puerto Aventuras, and the Santander in Centro Maya, were switched off a while ago, and left off for some time (last I checked the one in Puerto was still down). Not sure if this is related to this type of scam being exposed and Santander taking measures against it.
So only ATM’s that have been hacked will emit a Bluetooth signal?
“…the stolen data that is sent by the bluetooth components is encrypted. Decrypting that data requires a private key that ostensibly only the owners of this crimeware possess.”
Because heavens know you don’t want someone stealing the data you just stole. CLASSIC
Thanks a lot for the article! I live in Playa Del Carmen and last year had my card hacked. I was lucky I was able to get my $700 back from the bank but needed to change cards, accounts and so on. Now I am very wary of using ATMs but this article will help me. Thanks again!
So did you ever figure out why your I-devices weren’t able to detect the free2move Bluetooth beacon?
Brian, you better watch yourself there…it sounds very dangerous…the criminals dont mess around with people who disrupt their “business”…I am really concerned for your safety….hotel personnel are probably in on the scam…please be careful
Brian,
Great article and research! Makes me equally curious what you might find from a trip across Eastern Europe!
Doug
Hi Brian,
Please be careful – as other posters have said I imagine that many of the people involved in this are used to settling thing violently and you are going to be pretty obvious to the bad guys… In Mexico one clearly has to live with a different set of boundary conditions than in the US and it may be very hard to tell the good guys from the bad guys. I enjoy computer forensics which luckily I rarely have to do but when I do I am in the US where I know the lay of the land.My hat is off to your unnamed source for taking such a huge risk and telling you his or her story.
Fred
I can see the day where all ATM cards will have to be equip with a token versus just a simple pin. Insert your card, enter your pin (something you know) + whatever the random generated token is. That would render all forms of skimmers irrelevant. The crooks could get the card #, the pin and whatever token was, but all of that would be useless for future transactions.