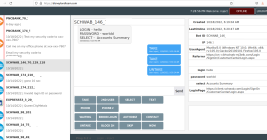
Disneyland Malware Team: It’s a Puny World After All
A financial cybercrime group calling itself the Disneyland Team has been making liberal use of visually confusing phishing domains that spoof popular bank brands using Punycode, an Internet standard that allows web browsers to render domain names with non-Latin alphabets like Cyrillic and Ukrainian.