Many of the most widely used third-party software applications for Microsoft Windows do not take advantage of two major lines of defense built into the operating system that can help block attacks from hackers and viruses, according to research released today.
Attackers usually craft software exploits so that they write data or programs to very specific, static sections in the operating system’s memory. To counter this, Microsoft introduced with Windows Vista (and Windows 7) a feature called address space layout randomization or ASLR, which constantly moves these memory points to different positions. Another defensive feature called data execution prevention (DEP) — first introduced with Windows XP Service Pack 2 back in 2004 — attempts to make it so that even if an attacker succeeds in guessing the location of the memory point they’re seeking, the code placed there will not execute or run.
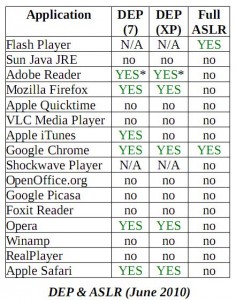 These protections are available to any applications built to run on top of the operation system. But according to a new analysis by software vulnerability management firm Secunia, half of the third party apps they looked at fail to leverage either feature.
These protections are available to any applications built to run on top of the operation system. But according to a new analysis by software vulnerability management firm Secunia, half of the third party apps they looked at fail to leverage either feature.
As indicated by the chart to the right, Secunia found that at least 50 percent of the applications examined — including Apple Quicktime, Foxit Reader, Google Picasa, Java, OpenOffice.org, RealPlayer, VideoLAN VLC Player, and AOL‘s Winamp — still do not invoke either DEP or ASLR. Secunia said DEP adoption has been slow and uneven between operating system versions, and that ASLR support is improperly implemented by nearly all vendors.
“If both DEP and ASLR are correctly deployed, the ease of exploit development decreases significantly,” wrote Alin Rad Pop, a senior security specialist at Secunia. “While most Microsoft applications take full advantage of DEP and ASLR, third-party applications have yet to fully adapt to the requirements of the two mechanisms. If we also consider the increasing number of vulnerabilities discovered in third-party applications, an attackers choice for targeting a popular third-party application rather than a Microsoft product becomes very understandable.”
I followed up with the makers of all eight products that Secunia said ignored both DEP and ASLR, and received a few encouraging answers. VLC maker VideonLAN said the most recent version — v. 1.1.0- takes advantage of both features. Foxit Software said its Foxit Reader will support ASLR and DEP in the next major release. I will update this post if and when I hear from other vendors. A Google spokesperson said the company plans to implement these features in a future release.
Windows does have other built-in security features, such as user account control (UAC, on Windows Vista and Windows 7) and a limited user account (especially important for Windows XP users). XP users who can’t be bothered to adopt the limited user approach would do well to consider something like Drop My Rights for specific Internet-facing apps. Sandboxie is another application that allows users to box in or “sandbox” specific applications, such as browsers, IM clients, media players and the like, to block potential exploits from forcing these apps to write to other portions of system memory or the hard drive.
In the final analysis, Secunia notes, there is no substitute for applying security updates as soon as they’re made available, and Secunia itself makes one of the best apps for helping users stay on top of this regular chore. The free Personal Software Inspector application sits in the background, alerts users when it finds programs that are out of date, and provides a central, one-click place for downloading the latest application updates.
Earlier this year, I wrote about an upcoming release of the PSI tool that lets users choose to have PSI automatically download and install updates for third-party applications as they become available. Secunia is currently testing a limited technology preview version (that is, pre-beta, so install at your own risk) of this new feature, available here. I’ll post a longer review of this software in a future article, but so far the auto-patch feature appears to be unobtrusive and working as advertised, at least on my Windows 7 test system.
The full report is available from Secunia’s site, at this link.




Hey Brian,
What are the asterisks next to Adobe Reader for in the chart?
Sorry, Russ. I should have just answered your question. Secunia says the asterisk means that “exploitation techniques defeating the feature are publicly known.”
Hey Russ. I just updated the bottom of the above blog post with a link to the study.
Note that PSI can only run on limited accounts if the account is first logged in as an Administrative account. I do a PSI scan and then change the account to limited. And during the day I hibernate, which fixes PSI to the limited account.
– David
Norton Utilities reported this Sandbox download site as unsafe.
http://www.brothersoft.com/download-sandboxie-60880.html
That’s not a site – that’s a drive-by download. What are you trying to do to people?
The sandboxie URL at http://www.brothersoft.com/download-sandboxie-60880.html is presented on the main sandboxie.com web site.
Sorry, this is either AV FUD or just your typical false positive.
In fact, the Brothersoft link specifically states “Sandboxie 3.46 – Tested by 3 antivirus solutions; this software does not contain any kind of trojans, spyware or viruses.”
But, just curiosity’s sake, using a virtual machine with PC Armor (which tracks and can completely reverse ALL installs), I traveled to the Brothersoft link in question and downloaded Sandboxie 3.46. According to PC Armor, no drive-by install was attempted or succeeded. Then, I uploaded the Sandboxie file to VirusTotal.com, where it got a clean bill of health from all 42 anti-malware products. See link below:
http://www.virustotal.com/analisis/8e6cace5c716902733adc1508e5898cff36136709d3093089c2c6c5d52332ec6-1278837896
I am running Firefox 3.6.6. I used Process Explorer (Sysinternals tool from Microsoft) to look at the Firefox process. According to Process Explorer, DEP is permannet and ASLR is enabled. What version of Firefox was tested to determine that ASLR wasn’t implemented?
Mike — the report is posted (pdf) at the link I added to the bottom of the story, so you can review the specifics of the versions tested and the basic results. It looks like the version tested in this report was 3.6.3 (current version is 3.6.6), so they may have addressed this already.
From that report, here’s the bit appropriate to Mozilla:
4. Mozilla Firefox
NX_COMPAT was first set in version 3.0 (June 2008). Again, this is not sufficient for DEP
compatibility on Windows versions before Vista.
A call to “SetProcessDEPPolicy()” was added to xul.dll in version 3.5.2 (July 2009) for the 3.5.x
branch. Although the 3.0.13 version was released at the same time as 3.5.2, the 3.0.x branch correctly
applied DEP on all systems only in the following 3.0.14 version, released approximately one month
later.
ASLR cannot be properly applied to the latest 3.6.3 version, which has 10 DLLs with a fixed base
address. The following DLLs have a pre-defined base address of 0x10000000:
• plds4.dll
• ssl3.dll
• plc4.dll
• nss3.dll
• smime3.dll
• nssutil3.dll
• softokn3.dll
• nspr4.dll
• nssckbi.dll
• freebl3.dll
As a consequence, nspr4.dll is always loaded at address 0x10000000.
We just got ASLR patches for those libraries into the tree last night. That means Firefox 3.6.8 (?) and Firefox 4 should have ASLR for all libraries.
Details: https://bugzilla.mozilla.org/show_bug.cgi?id=559133 for NSPR, https://bugzilla.mozilla.org/show_bug.cgi?id=567134 for NSS.
pre-release test builds of Firefox 3.6.x with full ASLR available at http://ftp.mozilla.org/pub/mozilla.org/firefox/nightly/latest-firefox-3.6.x/
Thanks much for the reply. I will take a closer look at the PDF. As always, you do a great job. Thanks
DEP often needs to be turned on in BIOS you might want to make sure that’s not compliance verse actually on. grc.com has a free tool that will scan your motherboard to check to see if you have DEP support.
Great article! Always wondered which vendors were finally going to wake up and smell the coffee!
Is it just me or does anyone else find it really convenient that all these application vendors are claiming that DEP and ASLR will be fully implemented in their NEXT update (right after the release of the Secunia report)?
This seems to add a tinge of irony to the “dump Adobe install Foxit” argument.
As was noted in Security Watch, “Foxit Software appears to be putting a lot less effort into their security than Adobe.”
If FoxIT doesn’t allow executable code to run from a PDF by default or JavaScript to run then the likely hood of maleware creeping in is significantly lowered… Whether DEP is implemented or not. IF Adobe still continues to allow a PDF to launch any Executable and run Javascript willy nilly it won’t even matter if its DEP compliant or not… because it builds in exploit functionality. Its like saying that the Download manager is DEP compliant but if you download a bad executable what’s the difference. Executables are designed to execute.
Good point. As demonstrated at http://www.blade-defender.org/eval-lab/ , 60% of drive-by exploits are targeting Adobe Reader. Thus, it doesn’t appear that hackers are too concerned about the implementation of DEP in Windows XP and 7.
Your point’s well taken but installing other pdfreaders for Adobe is based on obscurity (small market share) and not because they are more secure. They’ll attract malware with increasing market share and users have to judge whether to keep them or install something else (which includes Adobe).
Brian I appreciate the focus on DEP and ASLR I’ve been wanting to hear more about this and its effectiveness.
Yet your definition of DEP “attacker succeeds in guessing the location of the memory point they’re seeking, the code placed there will not execute or run.” is a bit different from what I’ve heard.
Steve Gibson on Security Now! did a analysis and as I understaood it it was a method to prevent buffer over-runs from leading to the execution of arbitrary code or malicious code. I typical buffer over-run occurs when a program injects code or utter crap into a legiment data stream (like a URL, password field, username, some sort of API call). The program has inadequate filters and it causes a crash and while its still sucking in data the maleware coder can on the tail end of the crap or code insert an executable string in th hopes that the computer will execute just like ti was code in the program. DEP as I understands it provides a framework that is rooted in some low level BIOS technology that allows memory to be segregated into executable spaces and data spaces. When the programs implement DEP if they have a buffer over-run the crap code just fills up the memory allocated for data but can not cross over into executable space. So there’s my two cents.
http://www.grc.com/sn/sn-078.htm
By the way a lot of those programs mentioned above just open MP3s, JPEGS, etc. Data files. Not that they shouldn’t run in DEP but aren’t exploits in this arena a bit narrow…. rare.?.?
Setsafer is an an alternative for DropMyRights, also from Michael Howard, and has a GUI. It’s the first thing I install on a fresh windows XP:
http://blogs.msdn.com/b/michael_howard/archive/2006/05/07/592136.aspx
Although you have to type config .xml file by hands. Google can find you some examples, e.g.
http://www.instantfundas.com/2008/02/how-to-run-applications-as-non-admin-in.html
I am puzzled by Secunia’s results. I have XP Pro SP2 and ProcessExplorer tells me that Hardware DEP is ON for all processes except the GUI for ProcessGuard. It’s driver and other processes though have DEP enabled. I have Open Office 3.0.1, Winamp 5.551, an older version of Sun Java 1.6.0.07, etc. I have many of the programs Secunia says don’t have DEP on. Gee, I even use the ancient Firefox 1.5 on this host computer (mostly use Opera 1.54 experimental though) and even it has DEP on.
I used to have a lot of programs that were excluded from Hardware DEP by their makers (including Word 2002, IE6, Winamp. But with the exception of Snagit 7 and the GUI for PG, I can enable Hardware DEP for all of them and they will run with DEP ON and don’t get shut down by DEP. The only one that has a problem with that is Fx 1.5 which will eventually get shut down by DEP. Snagit, I cannot even start until I exclude it from DEP because DEP shuts it down as it tries to start.
Looking at the report on Secunia’s site, they are looking at the situation where an app has to make the api call to invoke DEP. I’m thinking that you can go to the control panel of Win 7 & XP SP2 in the performance tab and change the default setting to turn on DEP for all programs, thus allowing the protection to apply even if the app itself doesn’t turn it on. Of course, it helps if your processor supports hardware-based DEP.
jrj, yes, you can turn on hardware (meaning CPU supports it) DEP in Performance Options in System Properties. You have 3 options, Opt In (default), Opt Out and Always but the last one is not available in Performance Options. If you set it to Opt Out and then notice that a program is opted out and you change it so that program is opted in you will likely not be able to start the program as you will get a popup from DEP saying it has shut the program down (before it even started) to protect the computer or the program will start and run for a bit and then you get the DEP popup stating that Windows has shut the program down to protect the system. You will then have no choice, if you want to use that program but to put it back in the Opt Out list. IE6 and Word 2002 were opted out of DEP for years and I tried to turn on DEP for them several different times. DEP would popup that message when I would try to start them. So, I had no choice but to opt those two programs (and Firefox) out of DEP for a long time. Then Mozilla made Fx compliant and eventually Microsoft did the same for Word 2002 and IE6.
You cannot just turn on DEP for all programs (except by forcing Always On by changing the boot.ini). Each program has to be made compatible by its developer. What is really interesting is if you are brave enough to set DEP to Always On. I don’t know anyone who has been able to run XP for more than a few minutes with Hardware DEP set to Always On which means ALL processes always run with DEP applied. Plus, the only options for DEP in Performance Options in System Properties is either Opt In or Opt Out. You CANNOT turn on Always On there. You have to do it manually by altering the boot.ini file.
@Mele – Thanks for your detailed analysis. On Win 7 you can use the command line utility BCDEDIT to modify the boot parameters to set DEP to always on, but it seems to me that if you set DEP to Opt Out in the control panel and don’t specify any exceptions, then you are essentially running as “always on”.
From Microsoft’s site:
•“Opt-In” – In this mode of operation DEP is enabled only for processes that explicitly opt-in to DEP. This is the default configuration for client operating systems such as Windows XP and Windows Vista.
•“Opt-Out” – In this mode of operation DEP is enabled by default for all processes except those that explicitly opt-out of DEP. This is the default configuration for server operating systems such as Windows Server 2003 and Windows Server 2008.
•“Always On” – In this mode of operation DEP is always enabled for all processes regardless of whether the program is compatible with DEP or not.
•“Always Off” – In this mode of operation DEP is always disabled for all processes.
Brian –
This is good and interesting stuff, but could you follow it up with another column about programs that simply will not run under limited user accounts? I know you have addressed the subject in the past, but given that a program that will only run correctly as Admin is a greater security threat than a program that doesn’t fully support DEP and ASLR, then IMO it is time to revisit the issue.
I further suggest that at the top of the list should be Quickbooks – it is reprehensible that a program that asks you to trust it with your finances doesn’t run under a LUA. Maybe this has finally been fixed in the latest version, but the version I am forced to support on a client’s machine, even when fully patched, simply craps the bed when you try to run under a LUA, and I was forced to use runasSpc, available here:
http://www.robotronic.de/runasspcEn.html
to let the user run Quickbooks from his LUA, but of course QBs is then running as Admin. Even worse, another client needed QBs to be able to connect to the Quicken website, and I couldn’t get it to work, and Quicken “tech support” actually told me that the solution was to turn IE security down to low, and run as Admin – they refused, or didn’t know / didn’t care, to give me the URL that I needed to add to the IE “trusted sites” list, and No, it wasn’t http://www.quicken.com, but I finally was able to figure it out by sniffing the network traffic. As far as I’m concerned, the designers and programmers at Quicken are clueless idiots and clowns, but that’s just my opinion.
@dward:
>>>>DEP as I understands it provides a framework that is rooted in some low level BIOS technology that allows memory to be segregated into executable spaces and data spaces.<<<<
It's time that we realize that we have outgrown the Von Neumann architecture, and that we actually did so some time ago, and that it is now a major part of the inherent insecurity of PCs. For example, on my quad core machine, core #1 is used almost exclusively for the OS, so why not have the OS only run on certain cores, or better yet on a seperate CPU, and user apps only run on the other cores, and also physically separate data and program memory. Yes, you lose flexibility in assigning resources, but the average user doesn't use their PC's full potential anyway, and we could reduce a lot of unnecessary complexity and insecurity that comes with forcing everything through the same pipe.
Also, in regards to buffer over-runs, when are they finally going to write compilers that make those bugs all but impossible?
For LUA-incompatible software, start with MVP Susan Bradley’s “Admin/Power User Hall of Shame” at:
http://www.threatcode.com/
It’s in no particular order, often doesn’t give affected versions of software, and I don’t know how often she updates it, but she’s compiled an astonishing list of software that requires admin or power user rights.
Most of the things you mention have already been done. Write XOR Execute is supported *in hardware* for a lot of non-i386 architectures. Look at the work OpenBSD is doing if you want to see compiler improvements (and library improvements, like malloc() ) aimed at defeating buffer overruns.
These improvements just have to filter out to the wider software community.
Two major lines of defense… Yeah Yeah. Don’t believe this anti-microsoft propaganda.
Yanno…this all boils down to if Windows was actually secure by design.
It’s not. They’ve hacked it. Microsoft has literally hacked this thing into a hodge-podge of nothing but “we have security, but it’s optional” as is clearly the case.
The problem is that it’s too damn easy for someone to exploit a privileged account in Windows because it’s originally a single-user OS, not a multi-user OS.
It’s a target – a big red target. Nothing will ever change that until Microsoft takes the Windows design back to the drawing board and is open to risk breaking backwards compatibility with legacy applications by forcing them to secure themselves instead of making it an “option,” which is what it should do.
Look at what they did with my favorite games that only ran in XP or even 98 – can’t run Neverwinter Nights in Vista reliably, nor can I use the expansions.
It appears the priorities at MS are somewhat…backwards?
@BK: Did any of the developers give a reason NOT to use the available MS tools? Especially the ones w/ otherwise good reps?
Google is clearly attentive! Now if they can just get the hang of dealing w/ non-US govts!
Nope. Haven’t receive a response from any of the program makers defending their status.
What, no GIMP, Photoshop, or Paint.NET? 🙂
I am quite surprised to see there is little to no interest in Integrity Levels of Vista, and now Win7…
IL’s could also provide security by removing the ability to interact with important files or configuration items, by placing the browser at the lowest of integrity levels. I’ve only covered the basics here, because IL’s can go much further…
Microsoft is not promoting this technology to any degree, and as I hear, Firefox is a pain to make it work at low level.