Borrowing from the playbook of corporations seeking better ways to track employee productivity, some cybercriminal gangs are investing in technologies that help them keep closer tabs on their most prized assets: “Money mules,” individuals willingly or unwittingly recruited to help fraudsters launder stolen funds. It seems that at least one mule recruitment gang employs custom software to spy on new recruits.
Last month, I heard from a reader in North Carolina named John who’d been roped into working for a company that claimed to be in the digital concierge and outsourcing business. John became suspicious that he was involved in something shady when they told him he should expect a transfer of nearly $10,000 to the personal bank account that he’d provided to his erstwhile employer in order to eventually receive a paycheck.
The firm that hired John, a fictitious company called VIP One, recruits mules to help process fraudulent transfers from businesses victimized by account takeovers. Prior to sending its mules money, VIP One has prospective mules spend several weeks doing relatively meaningless busy work, for which they are promised payment at the end of the month.
VIP One requires all new recruits to install a “time tracking” application, basically a digital stopwatch that employees are expected to use to keep track of their time “on the job.” John was kind enough to let me take a peek inside his account at VIP One, and to download the time tracking software. It’s safe to say that time is certainly not the only thing being tracked by this program.
I installed the application in a Window XP virtual machine equipped with Wireshark, a free program that lets you inspect the data packets going in and out of a host machine. I pressed start and left the software alone for a few hours. A review of the Wireshark logs showed that the time tracking tool periodically and surreptitiously took screenshots of my system, uploading them to a site called gyazo.com. This Web site appears to be associated with a legitimate screen-grabbing application that automates the grabbing and posting online of screen captures.
My test machine also had several peripherals plugged into it, including a Webcam. To my surprise, further review of the logs showed that the time tracking tool hijacked my machine’s Web cam and took several pictures, also posting them to gyazo.com.
I have no idea how long this mule recruitment operation has been in business, or how many mules it has corralled to date, but even if there were only a handful they must have collected thousands of images of the mules and their desktops. I’m guessing that the mule recruiters use this tool to keep tabs on their employees, and to make sure that mules are acting quickly to withdraw the fraudulent transfers.
No doubt this software comes in handy for prodding mules who are lazy, prone to procrastinating, or perhaps even thinking of pocketing the entire transfer amount. I imagine the following scenario:
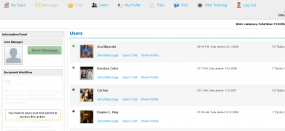
Fake user profiles of other VIP One “concierges” make it seem like all the cool kids are doing it these days.
VIP One mule recruiter: Hi, there’s a new task ready for you to process. Please go to your bank now and withdraw $4,933, keeping 8 percent ($399, minus wire fees) and split the money into to Western Union payments to the payees listed in the file we sent you earlier.
VIP One money mule: Okay, I’m going now.
5 minutes later, the mule recruiter calls again.
Recruiter: Hey, why aren’t you on your way to the bank?
Mule: I am!
Recruiter: No you’re not! You’re sitting there in front of your computer checking your fantasy sports team scores. Get off your butt and get down to the bank, NOW!



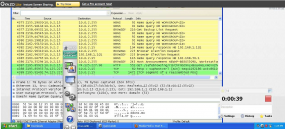

With the use of a legit screenshot and photo site, are you aware of any difference in the use of the site? User agent, Http method…? Thanks.
I thought about this, but no, it looked like normal usage, just an unencrypted POST request.
lol :))))
“You have to pass your trial period to access this action.”
Nice. Makes it sound like an up-sell.
I wonder how long it will be before some enterprising hacker decides to recruit a bunch of people (or even create a bunch of fake people), submit them as money mules to various unwitting cybergangs – then take all the money they’re supposed to pass on to the gang for themselves.
It’s an obvious hijack. May already have happened for all I know. For a few weeks “busy work”, the hijackers could nail probably $50-100K depending on how much is being passed through the mules in a given month.
I’m obviously in the wrong line of work. 🙂
I was thinking about the webcam’s images they were taking from their mules computers, and maybe they can use those images to create fake profiles over the net.
We see a lot of Twitter bots daily, and almost all have generic or stock photos in their profiles, and here they are creating they own stock of profile photos using their mules.
It’s just an idea :P.
How come the hackers are experts at transferring money out of victim accounts, but not out of mule accounts? Especially when the mule has a trojan on his computer. Is it the “Western Union” part that they need done manually, and that they are totally dependent on? Why aren’t they using the mule/victim accounts to purchase some trusted (by them) online currency?
I think they are using Western Union to make is more difficult to track who the true recipients are. It essentially turns electronic currency to cash by stealing the money and directing the mule to send it Western Union (which is a cash only transaction generally). The thieves then receive cash on the other end, or a check which they likely cash immediately. I can’t imagine that the police or banks would have a very easy time tracking that. If it always stays as some from of electronic currency I would think tracking it would be a lot easier. All they need with a Western Union transfer is a fake id and the details of the transfer and they can remain anonymous.
When the criminals want to trade money among themselves in an untraceable manner they don’t use Western Union.
But I see now – one of the ways to (pay an Exchange to) deposit into Liberty Reserve is with Western Union.
The real issue is speed and the fact that once a Western Union transfer is completed, it’s as good as gone and is hard to reverse – especially if there are guys on the far end ready and waiting for an email from the mule stating the MCTN number needed to pick up the transfer immediately.
Does the software only track when they users is “clocked in?” or does it also take pictures and screenshots at other times? If so (or even if not), it seems like the hypothetical scenario at the end of the post might be about as benign as one could hope for. Round-the-clock snooping could result in scenarios much more vicious, such as:
Recruiter: I think you should send me an extra $1,000 from your bank account this month.
Mule: Why should I do that?
Recruiter: Because otherwise I might have to post these compromising photos to your Facebook wall.
Ick, that first sentence was embarrassingly incoherent. Should read “… only operate when the user is …”
Pete, you’re right. My scenario was an example of the least that the fraudsters could do with this access.
To your question, it wasn’t clear to me what triggered the screenshots. They seemed to be taken at random intervals.
I bet they look at the webcam to see if anyone is wearing a uniform or to see if it’s in a police station or something.
Perhaps. And I suppose that they could tell whether you were forwarding the requests to law enforcement, or to other crooks. There is no honor among thieves, after all.
Can one hijack a built in webcam and have it running without the little LED next to it shining?
Yes.
Yes, they can. Remember, that when you install software of unknown origin, it can make many types of modifications to your system. But even if this time tracking software did not do those things, a snapshot would only last a fraction of a section, so it’s unlikely that you’d notice the light on.
Yes, LED off option.
This made me lol – Recruiter: Hey, why aren’t you on your way to the bank?
Mule: I am!
Recruiter: No you’re not!
Keep up the good work man, atleast your a true security researcher 🙂
2 solutions to this 🙂
1) disconnect webcam
2) do what I do and wear a balaclava when using a computer like all bad guys apparently do (according to security vendor marketing paraphernalia)
🙂
Or how about disabling the camera it in the bios (questionable effectiveness) and putting a sticker over the lens.. Standard practice here..
Jason
Many WU shacks are run by gang members, other WU shacks are run by independant criminals who cash in MTCN numbers without any identification for 15% of the amount!
The classical ” send the money to your brothers/fathers/mothers name” does not need fake ID´s! Its the thousands of WU shacks themselves and WU seems to look the other way! Moneygram seems a bit tighter but is also used. Often the gangs have hundreds of accounts and move the money within minutes to other accounts and from there to the next account and so on.
I have a sticker over the lens….
In certain countries (Germany) WU is strict and they need fake ID´s. These fake ID´s have blank fields for name and surname. The arrows (money mules who cash in the WU MTCN numbers) have special printers to print names on transparent plastic with adhesive. This is stuck over the fake ID to change names.
Countries where WU is not strict?
Romania-Bulgaria-Italy-Spain-United Kingdom to name a few….WU has been earning its 8-10% on Billions of illegal, fraudulent transfers the last 20 years. But what are WU compared to the banksters?
This is why I put a little mirror in front of my webcam. The eastern Europeans see a camera in their video window and immediately panic. You can almost hear them slam the laptop shut and start to run down the halway in a full adidas track suit. Almost..
“full addidas track suit” that’s gold