Muzzling buggy and insecure Web browser plugins like Java and Flash goes a long way toward blocking attacks from drive-by downloads and hacked or malicious Web sites. But leaving them entirely unplugged from the browser is not always practical, particularly with Flash, which is used on a majority of sites. Fortunately for many users, there is a relatively simple and effective alternative: Click-to-Play.
 Click-to-Play is a feature built into both Google Chrome, Mozilla Firefox and Opera (and available via add-ons in Safari) that blocks plugin activity by default, replacing the plugin content on the page with a blank box. Users who wish to view the blocked content need only click the boxes to enable the Flash or Java content inside of them.
Click-to-Play is a feature built into both Google Chrome, Mozilla Firefox and Opera (and available via add-ons in Safari) that blocks plugin activity by default, replacing the plugin content on the page with a blank box. Users who wish to view the blocked content need only click the boxes to enable the Flash or Java content inside of them.
To enable click-to-play on Chrome: From the main menu, click Settings, then in the search box type “click to play,” and click the highlighted box labeled “content settings.” In content settings, scroll down to the “plug-ins” section, and change the default from “run automatically” to “click to play”. To enable exceptions so that certain sites (krebsonsecurity.com?) are allowed to load Flash and other content by default, click the “manage exceptions” box. Alternatively, this can be done in Chrome through the address bar: when you browse to a site that has content blocked by the click-to-play feature, an icon will appear on the far right side of the address bar that allows you to add an exception for the current site.
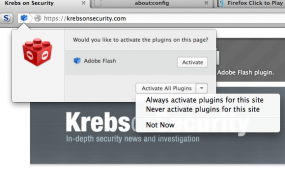 To enable click-to-play in Firefox: Open a browser window and type “about:config” without the quotes. In the search box at the top of the resulting window, paste the follow “plugins.click_to_play”, again without the quotes. Double click the entry that shows up so that its setting under the “value” column changes from “false” to “true” (hat tip to F-Secure.com for this advice). To enable per-site exceptions, look for the blue lego-like icon in the lefthand portion of the URL bar, and click it; click the “activate” button to enable plugins just for that session, or to make it permanent for that site, click the down arrow next to “activate all plugins” and select the “always activate plugins for this site” option.
To enable click-to-play in Firefox: Open a browser window and type “about:config” without the quotes. In the search box at the top of the resulting window, paste the follow “plugins.click_to_play”, again without the quotes. Double click the entry that shows up so that its setting under the “value” column changes from “false” to “true” (hat tip to F-Secure.com for this advice). To enable per-site exceptions, look for the blue lego-like icon in the lefthand portion of the URL bar, and click it; click the “activate” button to enable plugins just for that session, or to make it permanent for that site, click the down arrow next to “activate all plugins” and select the “always activate plugins for this site” option.
Opera users interested in this feature can enable it by clicking “Ctrl+F12”, and then the “Advanced” tab, then “Content,” and then enabling the “Enable plug-ins on demand” option.
Safari users can get a click-to-play like experience using either the ClicktoFlash extension – which, as its name suggests blocks Flash content – or the more comprehensive ClickToPlugin extension.
Getting a click-to-play like feature working in Microsoft‘s Internet Explorer seems to be a bit more complicated. Internet Explorer 10, which includes its own version of Flash, uses a Microsoft-provided whitelist of websites that are allowed to play Flash content by default. IE10 users on Windows 8 can add any site they like to the whitelist, but the steps for doing so are hardly straightforward. See this writeup for more information on how to do that (if someone knows of an easier way with IE10, please leave a comment below). PCMech.com explains how to sort of get click-to-play working in IE9, but this option may produce incessant pop-up prompts.
I mentioned at the outset of this post that some of these approaches can be used to block Java content from running by default, but a far safer approach with Java is simply to unplug it from the browser until and unless you need it (or uninstall it completely). If you need an idea of why I recommend this, have a gander at just a few of the most recent posts on Java.
One final note for those who decide to keep Java; unplugging it from the browser is a good idea, but keep in mind that Oracle’s Java installer re-enables the plug-in when the program is updated (shakes fist at Oracle).




Good advice Brian!
In my case, (FF16.02/XP-Sp3)
I let the “NoScript” FF extension, block Flash.
To enable a Flash object in the page
(movie, etc),
I have to actually click it to “authorize”.
Same effect.
(I realize many ppl. don’t have “NoScript”).
Again,
thanks for all the good advice!
(preventive AND corrective…).
And in IE, there’s ActiveX Filtering. To enable it, click the gear icon, choose Safety, then click ActiveX Filtering. On a site with blocked content, you can click the blue circle-with-a-slash in the address bar and enable ActiveX content if desired. To subsequently manage which sites a control can run on, it’s the gear icon > Manage Add-Ons, then double-click the one in question. One could always wish for further granularity, but hey. Centrally manageable via Group Policy too, of course.
I switched the SOHO work fleet to ActiveX filtering enabled, and occasionally have to remind my users to watch for the blue-circle cue if they’re not getting the expected results at a site. But they’re catching on 🙂 Whether it’s ActiveX Filtering or Click To Play, I see the merit in a default-deny approach.
Oh, and speaking of default-deny, another tweak you security-conscious folks might want to make is to disable the automatic downloading of fonts by browsers.
Twitter follower Jim (@ExtremeStorms) writes: can also type in “chrome://settings/content” in address bar
Twitter follower @G_a_l_i_l_i_o writes: To enable click to play in Opera you go to “Ctrl+F12>Advanced (cont) tl.gd/l9dna6
Note that the developer of ClickToPlugin states on his web site “Note. ClickToPlugin does not block elements. These elements are used to embed Java applets into web pages and launch a Java plug-in. The reason is that they cannot be blocked.”
Click-to-play on Opera does not impose using on Turbo feature.
Preferences -> Advanced -> Content -> Enable plugins only on demand
I prefer to just permanently disable plugin’s instead of using a third party extension. Once you disable them, then you don’t have to worry about ongoing vulnerabilities and or updates.
J.S.
Great article Brian, and great comments by the gentlemen/women visiting here! 🙂
I’m very appreciative here!
Thanks once again, Brian, for keeping us up to date and for providing a place for discussion and information dissemination! I learn a lot from you and many of your knowledgable readers.
My preferred solution for Firefox. One-click enable/disable toggle in status bar. Red icon = off, Blue = on. I keep Java disabled this way.
QuickJava 1.8.0
by Doug G
Allows quick enable and disable of Java, Javascript, Cookies, Image Animations, Flash, Silverlight, Images, Stylesheets and Proxy from the Statusbar and/or Toolbar.
https://addons.mozilla.org/en-US/firefox/addon/quickjava/
I’ve been using the Firefox browser since version 2, and prior to that I used Netscape (on Win 98) . I am not a big fan of Internet Explorer with it’s Active-X controls. I always like that with Firefox , you can save the session using a extension, install updates, then restart back to where your browser was previously without a machine reboot. The Firefox extensions are great however on some machines it may end up doing things like leak memory, hang the browser or simple won’t give a user the results they are looking for. I would fully test out “ClickToPlugin” for Firefox on websites that contain Java and Flash Player to see how it effects the browser functionality . I would also use Firebug extension along side “ClickToPlugin” if you end up having problems blocking plug-ins such as Java or Flash Player
J.S
Very same thing I’ve been pushing in the comments lately. I tried getting rid of Adobe Flash, my last plugin, but this method has been serving me well.
Thank you!!
Best plan for your site is to ditch Flash and switch to HTML5 for videos.
Warning: HTML5 Video and Audio only move the problems to another layer. HTML5 Video and Audio suffer with similar problems like Flash et.al. in the future because videos and audio files are active content too and can also be compromised (manipulated length byte, buffer or stack overflow, injected program content in the video code to exploit possible security holes in HTML5 player implementations like gstreamer etc.).
Aditionally several HTML5 players need JavaScript switched to “on” to run the videos, which opens a different can of worms (JS NOP-slides and filling the RAM with generated content to circumvent ASLR etc.).
My approach:
All active content like JavaScript, Audio, Video and Plug-Ins of all kinds set to “off ” in the browser for all pages unless really needed for trusted pages.
Other pages only in a virtual machine. Setting up a virtual machine is not that difficult nowadays and avoids many problems.
Online banking or any other kind of financial transaction in the Internet only by using a hardened live system running from CD.
I recently filed a bug report with Chrome about click-to-play bypass, thinking just like you that click-to-play is a security feature. It turned out that it’s not, you can read what Chrome engineers have to say about this here:
https://code.google.com/p/chromium/issues/detail?id=174963
It’s rather shocking to read that a feature that seems like a security layer, is not even intended to be one.
“Click to play is not actually a security boundary.”
Correct, click-to-play is not a security boundary because it’s UX is in the frame, and thus any implementation is susceptible to clickjacking. However, as the response to that bug points out, plugin blocking is a security boundary because it relies on interacting with the context menu chrome, which cannot be clickjacked (or even bypassed a compromise renderer process).
So, use click-to-play for convenience, but use blocking if you don’t mind the extra click and want a security guarantee.
hey krebs, check out exposed.su and do a story on that plz.
thx
Another very helful thread…Thank you, Mr Krebs!
Seems that as of today Microsoft did away with the whitelist approach in IE10 and went with a Blacklist approach instead?
http://arstechnica.com/information-technology/2013/03/windows-8s-flash-whitelist-goes-black-turns-on-flash-almost-everywhere/
(if someone knows of an easier way with IE10, please leave a comment below).
MS has a patch in the works that will change this from a whitelist to a blacklist. The whitelist apparently irks users, who’da thunk it. Of course, this will negate the already negligible security benefit of this particular behavior of the app. As for a better solution? I don’t know, use something other than IE.
*Patch is part of this batch of patch Tuesday, as it turns out. So if you patch the function reverses behavior. Interesting.
Drafty, I think ActiveX Filtering is IE’s closest equivalent (I posted some info on that above), with one caveat: I don’t see how one would use ActiveX Filtering in the Metro version of IE10 on Win8. Desktop IE10 is easy, three clicks and it’s done. Gear icon > Safety > ActiveX Filtering. Now visit your usual sites and whitelist as desired.
Like other whitelisting approaches, its downfall is when a trusted site becomes compromised and is directly hosting exploits that target your browser plug-ins. From my sysadmin days, I always remember how I was setting our fleet’s default homepage to our own non-profit’s public website, because hey, that’s sure to be safe content. Well, you can guess what happened. Our hosting provider got pwned and our own site was trying to exploit our own computers every time someone opened a web browser.
And the moral of that story, is defense-in-depth. The exploits were not expecting Restricted Users, backed by a behavior-blocking rule that arbitrarily forbade execution of dangerous filetypes like .EXE from within a user’s profile. Game over. In the case of a whitelisted site attacking a browser plug-in, do we have Plan B in place?
Hi thanks for such an effective tip, simpler than “noscript”
Thanks so much for this invaluable tip. Enabling “click to play” made it possible for me to read some of my favorite sites again without having pages autostart unwanted videos. I had begun to actively avoid sites like the huffingtonpost due to those intrusive videos which had sound that was often disruptive. I probably should have known about the click-to-play fix, but didn’t. Once again, Krebs to the rescue. 🙂
Brian –
You might tell your advertisers that your readers are generally leery of Flash, and that Flash ads, like the one on this page, won’t be reaching their intended audience.