Santrex, a Web hosting provider that has courted cybercrime forums and created a haven for a nest of malicious Web sites, announced last week that it is shutting its doors for good, citing “internal network issues and recent downtime.”
Couldn’t have happened to a nicer company. Rarely has a Web hosting firm so doggedly cornered the market on so-called “bulletproof hosting” services. These are essentially mini-ISPs that specialize in offering services that are largely immune from takedown requests and pressure from Western law enforcement agencies.
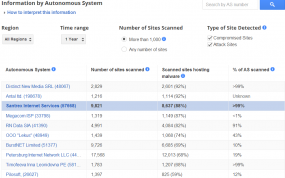
If there were a Hall of Infamy for hosting providers, Santrex would be near the top. That’s hardly an exaggeration: According to Google — which tracks top malicious hosts via its safebrowsing program — Santrex was among the Internet’s top three most malicious hosts over the past year. Google’s data indicates that nearly 90 percent of the sites on Santrex’s network tried to foist malicious software on visitors, or hosted malware that was used in attacks against other Web sites.
I first read about the news of Santrex’s demise in a thread at vpsboard.com titled “Ding! Dong! Santrex is Dead!” I followed up with Santrex via its Web site, and asked for confirmation that the closure was for real. I received a reply from Mikkel Thomsen, a sales rep at Santrex, who stated simply that, “Yes we are no longer offering any services.”
My guess is that after years of turning a blind eye to abuse complaints about malware and dodgy customers on its network, Santrex found that most — if not all — of its assigned Internet address space was listed on one blacklist or another. A search for “Santrex” on the forum webhostingtalk.com, for example, shows that more users know this ISP by different name: “Scamtrex.”
Prior to its demise, it appears that Santrex played one last scam on its customers and the rest of the world. Santrex was founded in the United Kingdom in 2009. According to documents obtained from Companies House, the entity which maintains records on U.K. firms, Santrex was declared insolvent by a U.K. court as far back as April 22 of this year.
Apparently, the hosting provider neglected to pay its bills to Bellcom UK Ltd., a London-based data center infrastructure provider. The court ordered Santrex’s assets to be liquidated. Perhaps that explains Santrex’s problems with the “internal network issues and recent downtime,” they cited in their emails to customers.
Rest in pieces, Santrex. You will not be missed.





There are a few out of Brazil that need there doors shut as well.
Its a good day…Look at this post on ISC.sans.edu
Blackhole Exploit Kit Author Reportedly in Custody
Russian authorities have reportedly arrested a man believed to be the author of the Blackhole exploit kit, widely used by cybercriminals to exploit vulnerabilities in Web browsers and other software to infect user computers with malware.
Maybe the Feds and officials in other countries are taking down whoever they can now, for fear that their tools will soon be either silenced or declared inadmissible in court.
Good news! Good riddance! 😀
The I.S.P. Santrex was a big bullet proof host for Phishing Scams over the last five years. Enough said …..
Waiting for that new Paunch/ Blackhole Exploit article from K.B. The site Sophos Naked Security ran a real good article today on the subject.
Correction I meant B.K. , on the above post
They have started long time ago in 2001 I think.
They were offering shell account etc. in dal.net (carding channels). The boss of the company was always a guy with nick name “masrawyz”. I hope they have made a lot of cash in the shiny era of Liberty Reserve and now they are gone 🙂
Broadly speaking, Whois shows Creation Date: 16-jan-2008.
They were operating before with name ConnectPower and domain I think connectpower.com.
Hello Brian i have an e-mail from Adobe :
Important Password Reset Information
To view this message in a language other than English, please click here.
We recently discovered that an attacker illegally entered our network and may have obtained access to your Adobe ID and encrypted password. We currently have no indication that there has been unauthorized activity on your account.
To prevent unauthorized access to your account, we have reset your password. Please visit http://www.adobe.com/go/passwordreset to create a new password. We recommend that you also change your password on any website where you use the same user ID or password. In addition, please be on the lookout for suspicious email or phone scams seeking your personal information.
We deeply regret any inconvenience this may cause you. We value the trust of our customers and we will work aggressively to prevent these types of events from occurring in the future. If you have questions, you can learn more by visiting our Customer Alert page, which you will find here.
Adobe Customer Care
Do we have to reset our passwords?
Hrm. I’m guessing you somehow missed this story:
http://krebsonsecurity.com/2013/10/adobe-to-announce-source-code-customer-data-breach/
“Adobe said the credit card numbers were encrypted and that the company does not believe decrypted credit card numbers left its network. Nevertheless, the company said that later today it will begin the process of notifying affected customers — which include many Revel and Creative Cloud account users — via email that they need to reset their passwords.”
I beg to differ, seeing as how I have first-hand knowledge they are(my mate has all the cc#’s decrypted).
The Adobe problems have caused a ripple at Sony’s ebook store, with a request for a password reset for all its customers.
The news are the LT company BalticServers are taking all their customers onboard.
In New Zealand
I’m a mere user
I received the email notification here. In spite of Adobe Systems claiming it had notified banks my bank, an international one, had not heard about it.
An ereader firm, not the one mentioned may be implicated, I think.
I changed passwords everywhere I can think of 🙂
This shall not be for santrex alone but also for other scam sites. Their days are numbered.