Spammers are abusing ill-configured U.S. dot-gov domains and link shorteners to promote spammy sites that are hidden behind short links ending in”usa.gov”.
 Spam purveyors are taking advantage of so-called “open redirects” on several U.S. state Web sites to hide the true destination to which users will be taken if they click the link. Open redirects are potentially dangerous because they let spammers abuse the reputation of the site hosting the redirect to get users to visit malicious or spammy sites without realizing it.
Spam purveyors are taking advantage of so-called “open redirects” on several U.S. state Web sites to hide the true destination to which users will be taken if they click the link. Open redirects are potentially dangerous because they let spammers abuse the reputation of the site hosting the redirect to get users to visit malicious or spammy sites without realizing it.
For example, South Dakota has an open redirect:
http://dss.sd.gov/scripts/programredirect.asp?url=
…which spammers are abusing to insert the name of their site at the end of the script. Here’ a link that uses this redirect to route you through dss.sd.gov and then on to krebsonsecurity.com. But this same redirect could just as easily be altered to divert anyone clicking the link to a booby-trapped Web site that tries to foist malware.
The federal government’s stamp of approval comes into the picture when spammers take those open redirect links and use bit.ly to shorten them. Bit.ly’s service automatically shortens any US dot-gov or dot-mil (military) site with a “1.usa.gov” shortlink. That allows me to convert the redirect link to krebsonsecurity.com from the ungainly….
http://dss.sd.gov/scripts/programredirect.asp?url=http://krebsonsecurity.com
…into the far less ugly and perhaps even official-looking:
http://1.usa.gov/1pwtneQ.
Helpfully, Uncle Sam makes available a list of all the 1.usa.gov links being clicked at this page. Keep an eye on that and you’re bound to see spammy links going by, as in this screen shot. One of the more recent examples I saw was this link — http:// 1.usa[dot]gov/1P8HfQJ# (please don’t visit this unless you know what you’re doing) — which was advertised via Skype instant message spam, and takes clickers to a fake TMZ story allegedly about “Gwen Stefani Sharing Blake Shelton’s Secret to Rapid Weight Loss.”
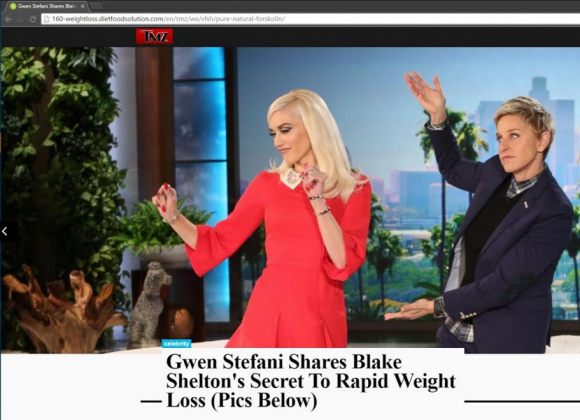
Spammers are using open redirects on state sites and bit.ly to make spammy domains like this one look like .gov links.
Unfortunately, a minute or so of research online shows that exact issue was highlighted almost four years ago by researchers at Symantec. In October 2012, Symantec said it found that about 15 percent of all 1.usa.gov URLS were used to promote spammy messages. I’d be curious to know the current ratio, but I doubt it has changed much.
A story at the time about the Symantec research in Sophos‘s Naked Security blog noted that the curator of usa.gov — the U.S. General Services Administration’s Office of Citizen Services and Innovative Technology — was working with bit.ly to filter out malicious or spammy links — pointing to a interstitial warning that bit.ly pops up when it detects a suspicious link is being shortened.
KrebsOnSecurity requested comment from both bit.ly and the GSA, and will update this post in the event that they respond.
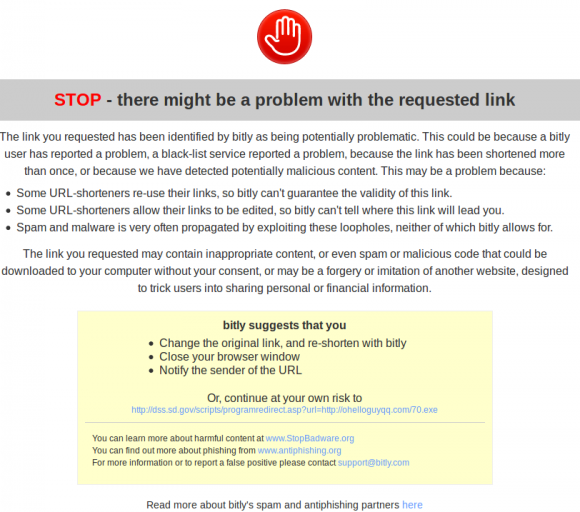
I wanted to get a sense of how well bit.ly’s system would block any .gov redirects that sent users to known malicious Web sites. So I created .gov shortlinks using the South Dakota redirect, bit.ly, and the first page of URLs listed at malwaredomainlist.com — a site that tracks malicious links being used in active attacks.
The result? Bit.ly’s system allowed clicks on all of the shortened malicious links that didn’t end in “.exe,” which was most of them. It’s nice that bit.ly at least tries to filter out malicious links, but perhaps the better solution is for U.S. state and federal government sites to get rid of open redirects altogether.
I generally don’t trust shortened links, and have long relied on the Unshorten.it extension for Google Chrome, which lets users unshorten any link by right clicking on it and selecting “unshorten this link”. Unshorten.it also pulls reputation data on each URL from Web of Trust (WOT).
Fun fact: Adding a “+” to the end of any link shortened with bit.ly will take you to a page on bit.ly that displays the link actual link that was shortened.
How do you respond to shortened links? Sound off in the comments below.
Update, Mar. 22, 6:20 p.m. ET: A GSA spokesperson said that When GSA learns that an open redirector is being used for 1.usa.gov links, “we reach out to the owner and ask that it be shut down. We are also working with Bitly to remove 1.usa.gov links with open redirectors that aren’t shut down at our request. GSA will continue to take the necessary steps to keep .gov domains secure, and we encourage anyone who discovers an open redirector in the .gov space to notify the affected agency so that it can be disabled.”




I would send this over to the folks at 18F Digital Services Delivery https://18f.gsa.gov/
Small Typo towards the bottom where you reference NORTH Dakota rather than SOUTH Dakota as the link in the pictures would suggest.
“…So I created .gov shortlinks using the North Dakota redirect, bit.ly, and the first page of URLs listed….”
This is just poor programming , security 101. Unvalidated redirects are #10 on the OWASP top 10 for secure programming for web developers. https://www.owasp.org/index.php/Top_10_2013-A10-Unvalidated_Redirects_and_Forwards
I’m with the government, I’m here to help… Eyes rolling.
When I report spam using http://www.spamcop.net there are almost always URLs that redirect to the target site or sometimes a second url that directs to the target site. Bit,ly use to be popular, but due to their proactive stance on abuse goog.le has become a top choice. But anyone can buy a cheap domain and set one up with freely available scripts (google.com/search?q=url+shortener+script) or just by creating an redirect file (domain.us/official-looking-text/).
What I generally do is click on the link in the spam and add all the URLs I find that way into my spam report. That way, even if the URLs in the spam stop working, there will be a report sent to the systems that host the target URLs. These are generally affiliate sites and the URLs generally have an ID for the affiliate that will profit from the spam. That way the affiliate site can take action against affiliate and close their account.
What we need is spam detection software that runs at the server level which can detect outgoing spam and alert the hosting provider of possible abuse at the account level. Just blocking incoming spam doesn’t really do very much.
Thank you for the article Brian
Great to know about the + with bit.ly
There is only so much time in the day. My stance has been if the URL is shortened, I’ll spend my short amount of time somewhere else. Most of us are not typing URLS – if it’s not on a billboard why do they need to be obfuscated?
URL shorteners began during the prime years of Usenet, when some posting programs would spread a long URL over multiple lines and make it unclickable; providing a link that didn’t have to be copied and pasted was seen as courteous. In recent times shorteners have been heavily used by posters trying to post a link while staying within the character limit on Twitter.
Then you have the jokesters who came up with sites like hugeurl, which provided massively long links, as well as “urlshorteningservicefortwitter”, a shortener with a domain name so long it intentionally made itself undesirable for its ostensible use.
Well I guess it could be worse:
http://www.thelongestdomainnameintheworldandthensomeandthensomemoreandmore.com/
Great heads up post. I’ve always been worried about url shorteners because they have been great obfuscation tools for nefarious links. Early on, users trusted these way too much and I did not, but now I have trust in the big name ones like youtu.be or the sort. I would imagine google does a decent job of using some sort of 3rd party or internal reputation/filtering/sandboxing of URL destinations before allowing the redirect to be successful. It looks like bitly has some very weak filtering working based on what you reported. Also, bit.ly, being solely in the business of url redirection, has some sort of conflict of interest in deploying stronger safe guards because they can’t afford to have too many false positives compared to competitors.
The combination of bitly and the gov redirect is really scary because it creates a 2nd hop of indirection making some of those url shortener sites reputation/filtering protections useless. I would imagine this attack happens at many trusted websites that have open redirects, not just .gov
Thanks for the unshortener extension! Will be using that to help from now on for sure!
that stream was fascinating, I saw several really strange things go by… this one was very strange. why would someone in china care about the traffic cams in the US? but when you try to go to that ftp site, it stops and that novotny folder is gone…. surveillance drop for a spy maybe?
{“h”:”1micznz”,”g”:”1micznA”,”l”:”anonymous”,”hh”:”1.usa.gov”,”u”:”ftp://ftp.dot.wi.gov/dtsd/stoc/EricH/Novotny/US1218@JohnNolen_20140630.avi”,”r”:”direct”,”a”:”Mozilla/5.0 (Windows NT 5.1; rv:6.0.2) Gecko/20100101 Firefox/6.0.2″,”i”:””,”t”:1458258254,”k”:””,”nk”:0,”hc”:1404254350,”_id”:”047e2cc9-298e-13a9-4c0e-8272b0e8011f”,”al”:”en-US”,”c”:”CN”,”tz”:”Asia/Chongqing”,”gr”:”30″,”cy”:”Shenzhen”,”ll”:[22.5333,114.1333],”sl”:”1micznz”}
I just regard any shortened link as malicious and don’t mess with them.
Regards,
As of 9 pm eastern time, the Krebs redirect doesn’t work. Could it be that North Dakota is more concerned about a safe, but publicly embarrassing link than it might be about a lesser-known, but malicious link? Just askin’.
I tried the “krebsonline” redirect and it timed out. I replaced Brian’s site address with my own, same result.
yay. looks like SD removed its open redirect.
It’s not too difficult to find another one. I did in like 5 minutes.
Who said .gov domains could be trusted in the first place?
wow you reading my mind again lol. good story.
I use this URL shortener:
http://www.checkshorturl.com/expand.php
I honestly don’t see this as bit.ly’s problem at all. They’re shortening URLs, which is exactly what they’re supposed to be doing. There’s always going to be some risk in shortened URLs. That’s never going away. The open redirect, on the other hand, is lazy and shameful.
So, we shouldn’t trust anything ending in .GOV. I don’t see why this is a bad thing.
Use the Lenny Zeltser meat grinder of Reputation checkers
https://zeltser.com/lookup-malicious-websites/
I use goo.gl to shorten links all the time:
1. Makes email look nicer. Friends and Family are much more afraid of long, impossible for a novice to parse.
2. Email is often directed to smart phones these days with impossible to read copy/paste tiny screens.
3. Google lets me know how many links were exercised, which is feedback on whether my efforts is worth it.
4. Hover on the google links and they will show you the recipient what the real link is ( and as I recall a thumbnail of the site).
Yes, I look suspiciously at short links on web pages and email from people I don’t know.
C’mon, life’s too short, url’s are not. 🙂
And to think I was going to talk to soomene in person about this.
Can’t say I’m surprised at the government being exploited by cybercriminals … it’s outrageous though!
Maybe it’s just me but the beauty of this attack is in having the link show the real authentic website so the victim doesn’t question it. Using a shortened URL brings about suspicion even if it says usa.gov.
The attack should have the authentic site and the parameter should be URL encoded so they don’t know where they will ultimately go.
I notice that the only extension in the Chrome store is Unshorten.link
The Unshorten.it is a website where you have to paste the link in to see where it will take you.
It may work on an Android device, but not in the Chrome browser.
Well maiaadmca nuts, how about that.
I comment whenever I especially enjoy a article on a site or I
have something to add to the discussion. It is triggered
by the fire communicated in the post I looked at. And on this article Spammers Abusing Trust in US
.Gov Domains — Krebs on Security. I was moved enough to drop a
comment 😛 I do have 2 questions for you if it’s okay.
Could it be simply me or does it give the impression like some of these remarks look
as if they are written by brain dead individuals? :
-P And, if you are writing on other online social sites, I would like to keep up with you.
Would you make a list every one of your social sites like your Facebook page, twitter
feed, or linkedin profile?
For Firefox I use http://www.longurlplease.com to expand compressed links from link services.
I am not sure how any web site could pass an audit with an open redirect exposure.
As a security professional, I tend to visit shortened links from a Linux VM running an intercepting proxy so I can see what all is going on. Depending on how much time/boredom I have to spare, and how suspicious the traffic looks, sometimes I’ll mess around with wget using various user-agents, or will visit the link through some sandboxes and see what happens.
More time than they probably deserve, but I have a bit of an “Ooo shiny!” mindset when it comes to potential badness.
I have learn several good stuff here. Certainly price bookmarking for revisiting.
I surprise how so much attempt you put to make this sort of great informative website.
Taking the oveeivrw, this post hits the spot
Many thanks extremely practical. Will share website with my friends.|
It’s an amazing piece of writing designed for all the
web people; they will get advantage from it I am sure.
Hello, I wish for to subscribe for this weblog to get latest updates, thus where
can i do it please help.
What’s up everyone, it’s my first visit at this website, and paragraph is truly fruitful for me, keep up posting these posts.
The link to malwaredomainlist.com does not work in Chrome : it’s blocked, with a Chrome error page that says (in part) :
“malwaredomainlist.com normally uses encryption to protect your information. When Google Chrome tried to connect to malwaredomainlist.com this time, the website sent back unusual and incorrect credentials. … Your information is still secure because Google Chrome stopped the connection before any data was exchanged.
You cannot visit malwaredomainlist.com at the moment because the website sent scrambled credentials that Google Chrome cannot process.”
It may be that the Chrome connection stipulates the use of https and the website can’t or won’t set up a secure connection. Or perhaps (as the error message says) “an attacker is trying to pretend to be malwaredomainlist.com, or a Wi-Fi sign-in screen has interrupted the connection”.
Anyone else getting this?