The Associated Press today points to a remarkable footnote in a recent State Department inspector general report on the Hillary Clinton email scandal: The mail was managed from the vanity domain “clintonemail.com.” But here’s a potentially more explosive finding: A review of the historic domain registration records for that domain indicates that whoever built the private email server for the Clintons also had the not-so-bright idea of connecting it to an Internet-based printer.
According to historic Internet address maps stored by San Mateo, Calif. based Farsight Security, among the handful of Internet addresses historically assigned to the domain “clintonemail.com” was the numeric address 24.187.234.188. The subdomain attached to that Internet address was….wait for it…. “printer.clintonemail.com“.
Interestingly, that domain was first noticed by Farsight in March 2015, the same month the scandal broke that during her tenure as United States Secretary of State Mrs. Clinton exclusively used her family’s private email server for official communications.
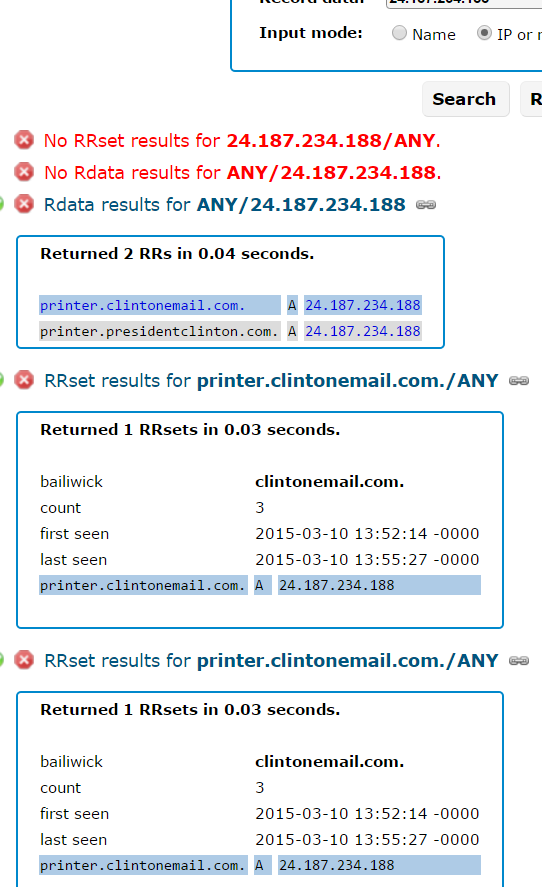
Farsight’s record for 24.187.234.188, the Internet address which once mapped to “printer.clintonemail.com”.
I should emphasize here that it’s unclear whether an Internet-capable printer was ever connected to printer.clintonemail.com. Nevertheless, it appears someone set it up to work that way.
Ronald Guilmette, a private security researcher in California who prompted me to look up this information, said printing things to an Internet-based printer set up this way might have made the printer data vulnerable to eavesdropping.
“Whoever set up their home network like that was a security idiot, and it’s a dumb thing to do,” Guilmette said. “Not just because any idiot on the Internet can just waste all your toner. Some of these printers have simple vulnerabilities that leave them easy to be hacked into.”
More importantly, any emails or other documents that the Clintons decided to print would be sent out over the Internet — however briefly — before going back to the printer. And that data may have been sniffable by other customers of the same ISP, Guilmette said.
“People are getting all upset saying hackers could have broken into her server, but what I’m saying is that people could have gotten confidential documents easily without breaking into anything,” Guilmette said. “So Mrs. Clinton is sitting there, tap-tap-tapping on her computer and decides to print something out. A clever Chinese hacker could have figured out, ‘Hey, I should get my own Internet address on the same block as the Clinton’s server and just sniff the local network traffic for printer files.'”
I should note that it’s possible the Clintons were encrypting all of their private mail communications with a “virtual private network” (VPN). Other historical “passive DNS” records indicate there were additional, possibly interesting and related subdomains once directly adjacent to the aforementioned Internet address 24.187.234.188:
24.187.234.186 rosencrans.dyndns.ws
24.187.234.187 wjcoffice.com
24.187.234.187 mail.clintonemail.com
24.187.234.187 mail.presidentclinton.com
24.187.234.188 printer.clintonemail.com
24.187.234.188 printer.presidentclinton.com
24.187.234.190 sslvpn.clintonemail.com




ISPs and cloud providers do not typically allow layer 2 access between clients, so the idea of obtaining a “nearby” IP address and sniffing is most likely not viable. 24.187.234.186 belongs to cablevision, DOCIS definitely doesn’t allow Layer 2 access between different customers.
“…sniffing is most likely not viable…”
Does that = impossible?
Ron,
Nothing is impossible, and we don’t have enough information to say for sure. Sniffing upstream of customer premise equipment would be more viable, but if an attacker had that access, the print queues are probably the very least interesting things to look at.
The printer queue to a pimple faced hacker wouldn’t be of interest but for a state intelligence agency it would be a jackpot. Some of the greatest intelligence is gathered from the trash still today. Don’t think that the printer queue would not be interesting to a knowledgeable party.
She is of interest to everybody, especially those trying to make a name for themselves. If her security was that bad, the pimple faced hacker would be the first one to go public with proof. Thats what they live for. Look at all the celbrities, Michelle Obamas Email, The CIA director, the guy who hacked a Clinton aide. Hillary is one of the few people with the guts to even use email in congress and I’m sure she didn’t hire a dummy to set up her personal server. It was attacked constantly. The pimple faces were trying to ddos’ it all the time. Never phased her.
As far as NSA level actors go, the only way to stay secure from them is not use digital communications. I don’t care how guru you think you are. Email isn’t secure anyways unless using pgp keys with who you are communicating. And i doubt diplomats and gov’t officials from other countries she was talking to were doing that. Hillary is more sophisticated then most but in general society is not. And encryption doesn’t even matter when endpoints are not that secure. cough…whatsapp on smartphones…cough… When its super sensitive you don’t use your email at all…
Looks like the pro-clinton astroturfers are out in full force with this comment and the one below it being exact dupplicates.
She is of interest to everybody, especially those trying to make a name for themselves. If her security was that bad, the pimple faced hacker would be the first one to go public with proof. Thats what they live for. Look at all the celebrities, Michelle Obama’s Email, The CIA director, the guy who hacked a Clinton aide. Hillary is one of the few people with the guts to even use email in congress and I’m sure she didn’t hire a dummy to set up her personal server. She knows you can get way more done with emails then not. The pimple faces were attacking it all the time, but in vain.
As far as NSA level actors go, the only way to stay secure from them is not use digital communications. I don’t care how guru you think you are. Email isn’t secure anyways unless using pgp keys with who you are communicating. And i doubt diplomats and gov’t officials from other countries she was talking to were doing that. Hillary is more sophisticated then most but general society is not. And encryption doesn’t even matter when endpoints are not that secure. cough…whatsapp on smartphones…cough… When its super sensitive you don’t use your email at all…
Wow how much did correct the record pay you for THAT crap? it is NOT “brave” to send emails – it is security naive! You DO realise that “pimple faced hackers” get their kicks from getting in and out UNDETECTED. You do realise security systems even the best in the world are breached ALL THE TIME! Which is WHY ultra secret ones are sent by HAND!
And explain the BS that you can get more done by an email than not – that makes NO SENSE!
So let me get this straight. YOUR “defence” of her is that she was “brave” to use emails to get MORE done, thereby using emails was more critical to how she works than other “less brave” people, yet you ADMIT that by using digital communications it is NOT secure!
How are you THAT stupid? If you take information from an ENCRYPTED system – which the state department uses, and put that same info onto an UNSECURED server with ZERO oversight, you STILL try to claim she did no wrong!?
LAUGHABLE!
Correct the record -> showing Clinton for the insane narcissist criminal psychopath she and her supporters are!
Good luck trying to convince ANYONE sending TOP SECRET information over an UNSECURED line doesn’t warrant prison!
guess you like to ignore the facts about celebrities that got hacked, the CIA directors email, Michelle Obama’s email, The President, Congress…. They all were public. Criminal thiefs after money or gov’t spies are the ones who would keep quiet about something like that. Not somebody trying for bragging rights.
IN nerd terms linuxmint.com, linkedln…etc…
And even in this political climate, noone has any proof against her except to try and grasp straws with some domain with one of the most famous people on the planet’s name in it. /trying too hard…
My defense is that she was way more secure and private then using the state department network. If you wanna say she broke the rules fine. But to claim it made her less secure or private, makes you the stupid one.
So… You want me to believe that Hillary’s personal email server sat behind MILLIONS of dollars of security infrastructure to keep it protected? And that it employed D.O.D. grade 2 factor authentication, disk encryption, and had a team of the worlds best security professionals monitoring all traffic to/from the server and the network itself?
I doubt it.
millions of dollars? lol you mean the computers Hillary had to update, that haven’t been updated since Condoleeza Rice? Whom i might add never used an email personal or gov’t related… You can thank Hillary for them at least having secure boot possibly now.
Dod level encryption? haha Like OPM data was encrypted? You have a real fantasy view of how you think most of the governments computer networks are administered. They aren’t the NSA or Navy military buddy. They are pretty piss poor security wise, as described in this latest report itself related to the state department.
Yes the traffic was highly monitored, in fact in the report it states certain times her staff was telling diplomats and foreign officials not to email her because they were stopping attacks… While the republican inspector general might paint that as a scary a picture. I say bravo.
The best security professionals in the world unfortunately don’t work for the gov’t they work for private companies. And Hillary has the money to hire some good ones. So not only did she have physical security around her and her home at all times, she had a computer security team as well.
Secure, nonsecure, whatever. If she had used State’s email server, then 1) copies would have been on their server when she left office, 2) the Benghazi Commitee would have been able to wrap up its investigation 2 years ago, 3) if State’s computers were hacked, that wouldn’t be her responsibility, and 4) due to her choices, she’s on the hot seat insisting she didn’t do anything wrong. She made her bed and now has to sleep in it.
Serious astroturfing going on in these replies.
Don’t you remember? Clinton assured us that the Secret Service was on the job, at her home, protecting her server.
They were protecting her physically too, its their job. Someone was definitely monitoring traffic to know when it was being “attacked” and to “warn officials not to email her during those times” as stated in the report.
“My defense is that she was way more secure and private then using the state department network. If you wanna say she broke the rules fine. But to claim it made her less secure or private, makes you the stupid one.”
Here is a video interview that is by far the most thorough, informed, legal analysis of all of the rules and laws she’s broken:
C-Span Washington Journal
MARCH 18, 2016
http://www.c-span.org/video/?406228-4/washington-journal-joseph-digenova-hillary-clintons-emails
Investigation Into Hillary Clinton’s Emails – Former U.S. Attorney for the District of Columbia Joseph diGenova talks about the investigation into emails sent to and from Hillary Clinton’s personal email server during her time as Secretary of State.
Here is what we peons get for far less as found in a column about the scandal a few months ago:
“Consider this. In the past month, the Department of Justice indicted a young sailor who took a selfie in front of a sonar screen on a nuclear submarine and emailed the selfie to his girlfriend. It also indicted a Marine who sent an urgent warning to his superiors on his Gmail account about a dangerous Afghani spy who eventually killed three fellow Marines inside an American encampment. The emailing Marine was indicted for failure to secure classified materials. Gen. David Petraeus stored top-secret materials in an unlocked desk drawer in the study of his secured and guarded Virginia home and was indicted for the same crimes. And a former CIA agent was just sentenced to three years in prison for destroying one top-secret email.”
If she wasn’t royalty, she and everyone on her staff involved in this would have been in orange jumpsuits a year ago shortly after this story broke. At the very least, she and involved staff members should have their security clearances permanently revoked for the GROSS mishandling of highly classified materials up to and including Top Secret SCI Noforn (above TS) materials.
You have GOT to be joking.
This can not even be considered a sane response to the actions of Hill!
As stupid as we come to discover Hill! really is, she is a genius next to those who continue to support her. This issue is not just about our upcoming presidential election but one of trust to every ally we hold in the world. Hill! and her supporters intend to take it all down with her, rather than admit maybe a better path would be a more qualified candidate.
“get their kicks from getting in and out UNDETECTED”
And?
His point is correct, they then like to get credit for it and announce to the world that they did it. This is selfie obsessed, “look at me” generation their Skippy
@notme – I noticed you tried to leave the same comment about 20x. Contrary to the sentiment you expressed in your various usernames, I don’t censor comments in general, and I haven’t with yours. one reason that the system flags otherwise innocent comments as spammy has to do with the velocity with which a given IP submits comments. Do it too fast and too often, and it will assume you are a bot. So, if your comment gets moderated by my automated system, don’t lash out at it; that won’t help your comments get approved any faster. Thanks.
Yea it takes a lot of guts to purposefully bypass FOIA requests.
Headline today:
State Department Official Thought Clinton Used Personal Email for ‘Family and Friends’
“A longtime State Department official said he assumed that then-Secretary of State Hillary Clinton was using her personal email to “stay in touch with family and friends”, not conduct official business.”
What complete and utter bologna. The question, “Gee, why do we never see a .gov domain on her official email correspondence” never came up? Or why FOIA searches would have always turned up NOTHING from her?
Calm down. Unless there’s relevant info in that news report that you didn’t copy and paste into your comment, this State Department official obviously never got an email from her. And were any FOIA requests for her emails made before the post-Benghazi inquiries began?
The C-SPAN interview with former U.S. Attorney for the District of Columbia Joseph diGenova I linked to above was a real eye opener for me to how HUGE this scandal actually is.
Once one is aware of the details, one can easily see through all of the many intentional red herrings and half truths thrown out on this by Clinton and her campaign. What is absolutely, positively amazing to me is how they have been able to get away with it since it really doesn’t take much investigative effort at all to expose their spin job for what it is.
Some of the lame excuses now coming from the State Department are a hint that officials there are also vulnerable to the very major repercussions that SHOULD come from this.
Every one of the 127 to 150 (depending upon who you listen to) FBI agents investigating this and every person in the intel community knows darn well that if any one of them had done even the tiniest fraction of what has been done by Clinton and her crew, their security clearance would have been immediately revoked, they would have been indicted and, most likely, imprisoned.
That is why, as revealed in the C-SPAN interview with Joseph diGenova who has a current Top Secret clearance himself and has his ear to the conversation within the retired DOJ and intel community in DC, there would likely be a revolt within the FBI and intel community if there are no indictments on this. Why?
Well, first, there is that “Think of what would have happened to ME if I’d done even a tiny fraction of this.” Second, the failure to indict and prosecute would set a dangerous precedent that would make the successful prosecution of anyone guilty of the mishandling of classified materials and avoidance of public record FOIA inquiries difficult if not impossible.
@notme and other defending Hillary Fanbois: There is tons of evidence it was not way more secure than a DOD platform and she didn’t use a qualified individual to set up the email server.
It was an out of the box config with little or no effort to obfuscate the domain / service. I highly doubt the server or IIS had been harden and I’d have to profile it was out of ignorance. No doubt all default vulnerabilities where unaddressed and patches weren’t in effect if a reboot was necessary
How do we know this??? Just a little recon. As you know whatever you post may never go away… Same goes for domains. Enter one of my favorite Internet recon tools The Way Back Machine. If you don’t know it, search for it and do a little research.
When the default IIS page comes up for the mail domain and the auth login page shows up for at the default OWA address, we can comfortably conclude this was a lame chatty effort. At least ssl was being used (by default no doubt):
https://mail.clintonemail.com/owa/auth/logon.aspx
Had someone intended to provide a layer of security by hiding her email, it never EVER would’ve been via that silly domain. An obfuscated domain would’ve been irrelevant and distasteful i.e. openmalwarehere.com
You highly doubt? or is there “tons of evidence” ? make up your mind… You sound like that hacker from jail talking hot air. Like all the hot air in this article.
ROFLMFAO… That’s all you’ve got Hillary? Can’t actually dispute anything right? Hotair article just way too much for a Fanboi to take? Fanboi, Fanboi, Fanboiiiiiii
Sorry to deface your blog Brian, please deleat as seen fit. Couldn’t help myself.
Assuming the ISP has decent security..
https://www.youtube.com/watch?v=XGmDBo-00mY
That is a GREAT Youtube video. I’ve only gotten through the first 10 and a half minutes of it so far, and I had to stop watching it for a bit, because I was laughing my ass off so hard that tears were rolling down my cheeks.
Looking forward to the additional amazing absurdities revealed in the NEXT 40 minutes of this video.
You can’t make stuff like this up.
Could also DNS poison. They are not connecting to the printer via IP probably if they are setting up A records for it. Also don’t underestimate how many routers on the web are hacked, and I am talking up stream core routers.
But why are we even talking about eavesdropping a connection? You can usually trivially compromise a printer (likely default admin creds) and just capture each print job that is sent to the printer using the printer itself. Copy each job onto the filesystem memory on the device and FTP it out. Most all HP and other network capable printers support it or just upload your own firmware.
They’re talking about it because the Clinton camp keeps saying that there’s no evidence (proof) that the server was compromised (even though it almost assuredly was). So they’re saying that the network was so insecure that they might not even had to.
> just upload your own firmware.
Wow. And have it sniff the local net for you and upload the results.
You’d be swamped by Bill’s porn collection.
So let me get this straight, she COULD have been sending stuff involved with Black ops over an unencrypted link, and POTENTIALLY those files could have been printed off ANYWHERE in the world, and people are STILL defending her actions!
Did it happen – IRRELEVANT! The very notion that she made it POSSIBLE means she breached national security!
Would anyone else who did this be allowed in public yet alone to run for POTUS!?
Why haven’t the DNC disqualified her already?
She is DONE
Many printers have more than one port and protocols in use. That means several different ways of establishing a connection to that printer and not just layer 2.
The intercepting of data is also somewhat unlikely. Without knowing how they got internet access you can’t say infallibly if it was sniffable. Over a fiber circuit she likely had a CIDR block and there wouldn’t have been anyone else to sniff it. Over DOCSIS they would need to break BPI+, and be on the local RF segment. Both create extraordinarily unlikely scenarios for sniffing.
Also you sent me on a confusing wild IP goose chase… You have both 24.187.234.188 and 24.197.234.188 listed in the story.
Thanks. Fixed that. Should only be 187
The BPI+ reference refers to the current situation of DOCSIS 3.x I believe. It may not have been like that during the 1.0/2.0 era, please note “printer.presidentclinton.com”.
An interesting report from 2011:
http://www.nbcnews.com/business/consumer/exclusive-millions-printers-open-devastating-hack-attack-researchers-say-f118851
“In one demonstration, Cui printed a tax return on an infected printer, which in turn sent the tax form to a second computer playing the part of a hacker’s machine. The latter computer then scanned the document for critical information such as Social Security numbers, and when it found one, automatically published it on a Twitter feed…”
So, um, leaving aside the narrow possibility of printer traffic sniffing, I believe that it might be accurate to say that most printers these days have memory… lots of it… and thus, it would seem to be not entirely beyond the realm of the possible to imagine a scenario in which a less-than-perfectly-secured printer which happened to also have a PUBLIC internet address, might perhaps be induced to give up its secrets to some remote attacker, e.g. the last five or ten documents that were printed.
The media and the Republicats are all gaga about the security of THE SERVER, but if I was an attacker, with or without the backing of a foreign government, I’d have been poking at THE PRINTER in the first instance, because (a) its security is likely to be weaker and also (b) its entirely less likely that there would be any logs produced or kept of my poking around.
“1) Assigning a *public* IPv4 address to a printer opened up at least the theoretical possibilities that either (a) printer traffic could be sniffed or (b) that the printer itself could be compromised.”
This presupposes that the device sitting at the printer subdomain is actually a printer, and not a print server, and not a MakerBot. It also presupposes that if there really is a printer there that it’s not using an encrypted transport.
Now you’re saying that not only was a printer available on this subdomain, and there was no firewall and no encrypted transport, but it was actually one of a particular series of HP LaserJet printers that allowed for a firmware upgrade upon receiving a new print job?
After a few ifs, I agree this could look bad. But, Ron, you’re piling on the if after if after if and stating factually that this was bad. Again, what we have is a subdomain with printer as the name. There’s a ton of things in between that what you’re trying to have poor Brian conclude.
Directly connecting a computer to the internet without any firewall or hardening, bad idea. Directly connecting a printer to the internet without any firewall or hardening, yes, this too is a bad idea. Too bad we’re playing hopscotch because of a subdomain name. Not like this: http://210.125.31.xxx/hp/device/this.LCDispatcher?nav=hp.EventLog
“Now you’re saying that not only was a printer available on this subdomain, and there was no firewall and no encrypted transport…”
Yes, that’s exactly my fear. Can you prove otherwise?
“…but it was actually one of a particular series of HP LaserJet printers…”
No. Over time, security vulnerabilities have been either suggested or actually demonstrated in VARIOUS brands of printer… certainly not just HP.
Canon:
http://arstechnica.com/security/2014/09/hacker-exploits-printer-web-interface-to-install-run-doom/
Toshiba:
http://www.pcworld.com/article/239456/a_hidden_security_threat_beware_the_office_multifunction_printer.html
Samsung:
http://www.csoonline.com/article/2132624/application-security/samsung-printers-contain-hardcoded-backdoor-account–us-cert-warns.html
Brother:
https://www.cvedetails.com/vulnerability-list/vendor_id-1287/product_id-27224/Brother-Mfc-9970cdw.html
Brother, Canon, Epson, Fujitsu, Hewlett-Packard, Lexmark and Xerox:
http://www.computerworld.com/article/2553841/security0/smart-printers–scary-printers.html?page=2
Check this interesting Wayback Machine history out. Looks like the Clinton server was hosting adware, possible malware, on February 7, 2011.
https://web.archive.org/web/form-submit.jsp?type=prefixquery&url=https://clintonemail.com/
Ummm… Maybe advertising.
This brings up another interesting thing I just learned about the clintonemail.com domain. The FSI passive DNS data bases knows of about 10,000 subdomains of that domain. I was flaberghasted by this at first, but then I realised the real reason for this. (No, that domain DOES NOT actually have anywhere near that many REAL subdomains):
http://serverfault.com/questions/582962/unused-domain-name-getting-routed-to-double-click
http://www.theregister.co.uk/2008/04/11/network_solutions_sub_domain_parking/
The simple answer is that NetworkSolutions points your parked domains at their advertising. (That’s not actually remarkable at all. That’s just what pretty much every company that does domain parking does.)
The more interesting thing is that in the cases of your live/active/non-parked domains for which NetSol provides DNS, they wildcard these domains, so that any time anybody punches in a misspelled subdomain name, they end up at NetSol’s advertising partner, DoubleClick.
This is arguably an underhanded thing for NetSol to be doing, but hey! It’s (apparently) in the contract, so it _is_ explicit to the customer, and NetSol isn’t in business for its health. It’s a commecial enterprise, so they can’t be blamed for trying to make a buck, here and there.
But all this info about the DNS really brings up some other issues. Let’s say, just for the sake of argument, that Hillary’s server was, in actual fact, as tight as a snare drum with respect to security. There’s still the question of her login credentials for her NetSol account. If those had gone walkaround… well… you can imagine the scenarios.
The Wayback links I provided are NOT for subdomains or parked domains. They are for the clintonemail.com domain, for the time period in question that a breach may have occurred. The URL strings captured show (at least) questionable adware running on this box, and I’m really surprised no one is looking at that. The &poru= string is tied to some very dubious adware, for example.
So no evidence except wild speculation based on a sub domain name? I used to have a few sub domains such as router.mydomain voip.mydomain admin.mydomain netgear.mydomain setup as a honeypots. My plan was to script any ips buzzing them had all their future traffic dropped for several days. But alas I never got around to completing it.
Gosh! I had no idea, up until this moment, that Hillary was so sophisticated that she was even running her own honeypots!
🙂
Returning to this planet for the moment, I’d just like to emphasize that, as I told Brian, there are really two core points here:
1) Assigning a *public* IPv4 address to a printer opened up at least the theoretical possibilities that either (a) printer traffic could be sniffed or (b) that the printer itself could be compromised. We can debate all day the actual pragmatic level of risk associated with each of these two possibilities, but I think that it is non-zero in both cases, and in any case, perhaps this all misses the point.
2) Perhaps even MORE importantly, the assignment of a static public IP address to the printer speaks to the general level of network security competence (or lack thereof) of whoever was setting up and maintaining this equipment for the Clintons. And what it says is not good at all. I don’t think that many either would or could disagree with that. And this is the more troubling aspect of the whole story. If the Clinton’s sysadmin messed up even this simple and obvious thing, then what ELSE did he or she mess up, security-wise?
Assigning a *private* IPv4 address to a printer also opens up at least the theoretical possibilities that either (a) printer traffic could be sniffed or (b) that the printer itself could be compromised. You want a secure printer, go get that shielded centronics cable.
There’s nothing wrong with giving a printer a static public IP address as long as it is appropriately protected. Given a large enough static netblock, I’d claim that giving a printer a public address blocked at the firewall is less error-prone than setting up a private netblock for it. Insisting on a private IP address is cargo-cult security.
Putting anything on the internet opens up the theoretical possibility that’s its traffic could be sniffed. So, unless that’s the threshold, in which case she’s as secure as anything else on the internet, what’s the point of the outrage?
“Putting anything on the internet opens up the theoretical possibility that’s its traffic could be sniffed. So, unless that’s the threshold, in which case she’s as secure as anything else on the internet, what’s the point of the outrage?”
Actually, yea, you’ve made a good point. But let’s dissect it a bit.
In theory, at least, server-to-server e-mail transmission can be protected from prying eyes via TLS encryption. I personally don’t know how well deployed that (TLS) is at the present moment, but let’s just say for the sake of argument that it’s 50/50, i.e. half the time Hillary’s inbound and outbound messages, e.g. to various world potentates, were protected in transit from sniffing and/or MITM attacks, and the other times they weren’t.
More to the point, let’s assume, for the sake of argument, that she at least understood the possibilities of her e-mails being spied upon… which, in the post-Snowden era, at least, she certainly should have understood… and as a result, she was at least smart enough not to send out e-mails like “Yea, let’s drop those bombs now Bibi!” as some clever wag here said.
Contrast this with her probable level of caution when it came to simply *printing* some draft document… which could be equally or perhaps even more revealing and/or inflamatory… to the printer sitting right there next to her desk in her home office.
(As someone suggested, it is at least theoretically possible that data transport to the printer might be encrypted, but in practice, probably not.)
So Hillary is sitting there, and she prints a draft of a document she’s working on called “State Department Post-Invasion Plan for Crimea”. She doesn’t worry about the security implications of “sending” that document out over the Internet, because, as far as she knows, it is actually just going from the screen on the physical desk right in front of her just over to the printer which is sitting right at her elbow. As far as her (possibly technically naive) perceptions go, the document is just being printed, and isn’t ever even leaving the room she is sitting in. So her _perception_ is that printing the document is utterly safe and secure.
But this is the whole point here. Maybe that document could be sniffed. Even if that’s not a realistic possibility, the printer itself could be directly compromised, and made to give up its secrets.
The apparent high probability that (a) she had a home printer and that (b) this printer had a public Ipv4 address… which was ridiculously easy to find, by the way… and that (c) she probably was NOT just using that printer as a paperweight or a doorstop and (d) the undeniable possibility that said printer could perhaps have been “hacked”… perhaps even via something as simple as remote login using admin/admin… all adds up to what, in my book at least, seems to be a “Holy s**t!” type of scenario.
The fact that the FBI apparently didn’t bother to impound her printer when it impounded the rest of her gear is perhaps even more troubling.
For all we know, as we speak, that printer may be sitting exposed in some landfill somewhere in the hills of Westchester County, just waiting for some dumpster diver with an eye for valuable e-waste to come along, fish it out, plug it in, login with admin/admin, and then print out copies of the last 20 documents.
I think that it is safe to say that such a scenario probably would not be fully conformant with State Department rules & regulations with respect to the security of electronic documents.
Firstly I live on thw other side of the world & really couldn’t care less about US politics.
Secondly, why would you think politician would setup their own IT? 99% of them couldn’t even spell IT.
Why is it so hard to think they’d setup a honeypot subdomain? I’m just an idiot joe blow & I was thinking about it.
This story is just clickbait (& i fell for it). Even if they found a printer connected it doesn’t really mean much. But they didn’t even fimd tht. It was just a subdomain. If I call my dog “Tiger” is doesn’t mean its a tiger. Just like I had netgear.mydomain pointing to my BSD NAS box it doesn’t mean its a bit of Netgear kit.
Maybe pull your head out of planet US Politics and back to reality and look at the no-story story for why it is, purely clickbait speculation that belongs on the NY Post, not KrebsOnSecurity
Pardon my ignorance, but what about that URL tells you it’s malware?
Subdomain names mean little to nothing. Someone could guess what an IP address served based upon the subdomain name, or the domain name itself, but that is silly.
What exactly is an “internet based printer”? I’m not sure if there’s a technical person trying to sound not technical and using random jargon or if it’s a non-technical person trying to sound technical. Let’s try and define some terms maybe?
24.187.234.188 sounds very much like it was from the optimum online network block, and a quick whois shows that currently it does belong to them. That sounds about right because they provide services around the area Hillary Clinton called home. Optonline does provide static IP addresses. But I have to wonder, are these terminated in the house? Do we know if the email server everyone is so hip to talk about was actually located at Clinton’s house or was it in a DC (rack, not washington)? If it was in her house what was the connection? Did this IP reside on a cable modem? Was it a DSL line? Fiber? That area wasn’t know for it’s way updated and trendy transport. Did the carrier provide the equipment? Did Clinton hire a complete idiot to put the email server directly connected to the internet or was there a firewall in front of it?
How likely is it that there was a firewall of sorts in front of the mail server and any printers that were likely there? Pretty damn likely. She didn’t buy services from Stooges r Us. And even if she did, they would probably set up a firewall. That’s all saying that the vendor supplied equipment didn’t perform some firewalling technology. Anyone in the IT field would see this as not very likely outside of pre mid 90s.
For the printer subdomain name, we think that the printer actually had IPP or something? LPD? Are you suggesting, but not saying, that Clinton set up a printing device directly on the internet so that while she was traveling around wherever she was when not at home and printing to that printer? That doesn’t even make sense. Or are you suggesting, but not saying, she decided this fancy new printer she saw at Office Depot would look nice with a subdomain sitting next to her email server? And, now she could actually print stuff while she was outside in the yard or upstairs in the bedroom? Oh, it was connected to the internet? Really? “I didn’t know it was on the internet even though I somehow called and registered a subdomain so I could get an external IP address for it. And I just plugged this big old CAT5(e)/6 cable into my printer directly from the wall???”
Factually we can say the following: 4 subdomains pointed to 2 IPs. 2 subdomains use the English word “mail” and 2 subdomains use the English word “printer”.
Do we know that some mail transfer agent was listening on the mail domain? I assume someone knows this, but I’ve not seen any documentation on this, haven’t looked, barely care. Do we have any open ports on this other IP? Did anyone do some research? Why don’t you contact Robert Graham and ask him if masscan hit those IPs and what ports were open. Maybe he doesn’t like reporters, but you can ask nicely. Tell him some guy on the internet told you about masscan and that Rob probably had some port information about those IPs.
“Do we know if the email server everyone is so hip to talk about was actually located at Clinton’s house or was it in a DC (rack, not washington)? If it was in her house what was the connection? Did this IP reside on a cable modem? Was it a DSL line? Fiber? That area wasn’t know for it’s way updated and trendy transport. Did the carrier provide the equipment? Did Clinton hire a complete idiot to put the email server directly connected to the internet or was there a firewall in front of it?”
These are all GREAT questions, many of which the FBI, in its usual half-assed manner, is probably not even thinking about, let alone actually asking. Do you have any of the answers to any of the questions that you yourself have raised? I mean DEFINITIVE answers, rather than just your personal speculations?
“How likely is it that there was a firewall of sorts in front of the mail server and any printers that were likely there? Pretty damn likely.”
And you are basing that opinion/supposition on what, exactly?
“She didn’t buy services from Stooges r Us.”
Ummm… she did, actually:
https://www.wired.com/2015/03/clintons-email-server-vulnerable/
http://bigstory.ap.org/article/467ff78858bf4dde8db21677deeff101/only-ap-clinton-server-ran-software-risked-hacking
As detailed in both of the above news stories, whoever set up Clinton’s network was probably a relative of Professor Irwin Corey.
She used a SUPER USER from State to set it up for her… he is not an engineer. Just a Manager that worked for a year ‘managing’ remote connectivity for foreign Embassies…. he did not go to school for CS or engineering and he has no training either. He was given immunity by the Justice Dept and was then fired by the State Dept so obviously he did something wrong. If you read Brian’s post on FB — all of this is explained in the comments below his post with citations/links.
Yes, she had a CIDR block:
https://whois.arin.net/rest/net/NET-24-187-234-184-1
The CIDR block 24.187.234.184/29 was allocated to Clinton’s home. If the network was configured following standard practices, traffic between systems inside that CIDR block would not have left Clinton’s LAN, and most definitely would not have been “sent out over the Internet”. Guilmette’s comments about vulnerabilities and wasting toner assume incompetence and a total absence of firewalls. What evidence we have is that the people who setup Clinton’s home LAN knew enough to configure a router, a firewall, a VPN, and some basic CIDR netmasks.
NAT is not a security fix-all, not using NAT is not a sign of vulnerability or incompetence.
“If the network was configured following standard practices, traffic between systems inside that CIDR block would not have left Clinton’s LAN…”
And if perchance it WASN’T configured following standard practices, what then?
Does the FBI know what how the network was actually configured? Does anybody?
“Guilmette’s comments about vulnerabilities and wasting toner assume incompetence and a total absence of firewalls.”
Absolutely. Is there any publically known reason to grant the sysadmin(s) who set this stuff up any more generous assumptions vis a vis their competence? The AP and Wired news stories about this whole issue (of the security of the server) catalog an entire boat load of security screw ups. They don’t exactly inspire confidence in the competence of the people who set this stuff up.
“What evidence we have is that the people who setup Clinton’s home LAN knew enough to configure a router, a firewall, a VPN, and some basic CIDR netmasks.”
I can teach an 8th grader of average intelligence how to do all that stuff in 1/2 hour. Teaching him/her how to do it SECURELY takes a bit longer.
The good news is that people with no more intelligence that a bag of hammers can nowadays wander down to the local BestBuy, purchase a network printer and a router, take them both home, plug them in, and they just seem to work. The bad news is that people with no more intelligence than a bag of hammers can nowadays wander down to their local BestBuy, purchase a network printer and a router, take them both home, plug them in, and they just SEEM to work.
The mere existance of this network isn’t proof that it was secure in any sense. It isn’t even evidence of that.
Agreed. The information in this article is largely speculation based on one piece of information meta data (a DNS record).
Whether a printer existed is speculation; Whether said printer was connected to the internet is speculation (having an IP does not equal internet connectivity); If said printer existed, and if said printer was internet connected, any vulnerabilities in the printer itself or in the communications path are also speculation.
It gets better. Do a dig mx clintonemail.com. You’ll see that the machine’s incoming email was filtered by mxlogic.net, a spam filtering service that works by received all your emails, filtering out the spam, and forwarding you the rest.
This is because the hosting provider, Platte River Network, sold a package along with the hosting. The package included spam filtering and full-disk off-site backup (since then seized by the FBI).
So every email received by Clinton was going through many unsecured places, including a spam filtering queue, a backup appliance and an off-site backup server. Which has already been documented.
“It gets better. Do a dig mx clintonemail.com. You’ll see that the machine’s incoming email was filtered by mxlogic.net, a spam filtering service that works by received all your emails, filtering out the spam, and forwarding you the rest.”
That arrangement appears to have only been in effect since circa June, 2013. We should think also about the time BOTH before and after that.
;; bailiwick: clintonemail.com.
;; count: 5454
;; first seen: 2013-06-24 21:27:43 -0000
;; last seen: 2016-05-26 12:57:43 -0000
clintonemail.com. IN MX 10 clintonemail.com.inbound10.mxlogic.net.
clintonemail.com. IN MX 10 clintonemail.com.inbound10.mxlogicmx.net.
“This is because the hosting provider, Platte River Network, sold a package along with the hosting. The package included spam filtering and full-disk off-site backup (since then seized by the FBI).”
Was that all in the report? I guess I’ll have to go and read that whole thing now.
Interesting footnote: On tonight’s NBC Evening Nudes, they mentioned that the FBI had seized Clinton’s server, and also a USB thumb drive in August of last year. No mention of any PRINTERS being seized. (Typical incompetent FBI, still operating in the Louis Freeh era. The man didn’t even know how to use a computer, and didn’t want to.)
“So every email received by Clinton was going through many unsecured places, including a spam filtering queue, a backup appliance and an off-site backup server. Which has already been documented.”
Um, yep. You’re right. Arguably, the security of Clinton’s e-mails were even WORSE after the switch in June, 2013, than it had been before that.
And let’s not forget that the Stored Communications Act makes it perfectly legal for any service provider who happens to have YOUR e-mails on THEIR hard drives to peek at those e-mails, pretty much as they see fit, as long as doing so is ostensibly or arguably for “technical” reasons having to do with the management of the service they are providing.
(Google goes further and has software that looks at everything, for marketing/advertising purposes. All 100% legal, based on their end luser contracts, I’m sure.)
So this is basically like when some NSA people got caught peeking at the NSA’s records on their love interests. When they get caught, they just shrug, promise never to do it again, and nobody goes to jail.
How many sysadmins at MXLogic had access to Clinton’s emails? If the one lone guy who pulled the graveyard shift poked around into those e-mails, at say 3AM, would anybody even know that had happened? (Even the NSA didn’t know what Snowden had looked at until he was already long gone, and even then, they weren’t entirely sure.)
If Hillary couldn’t use a desktop computer at State, and we know from reports that she couldn’t. She sure as hell wouldn’t have been able to figure out how to use VPN.
You may want to consider checking out PassiveTotal when researching infrastructure like domains or IPs. We are showing hundreds of subdomains for the clinton-based emails you mention in the post. Could be more leads there. Our service offers a free level of support most users use for doing ad-hoc queries.
“We are showing hundreds of subdomains for the clinton-based emails you mention in the post.”
Emails don’t have subdomains. Only domains do. (Duh!) If you’re gonna try to slip some advertising into the middle of a technical discussion, at least use proper terminology.
Anyway, I already posted a follow-up about the OPTICAL ILLUSION… which is also present in Farsight’s historical passive DNS data… that the clintonemail.com domain *appears* to have actually THOUSANDS of subdomains. (See above.) In actual fact, it doesn’t. This is just an artifact of the disreputable practice of NetworkSolutions, which takes all of the domains that it provides DNS service for and adds a WILDCARD record to the DNS for each of these, so that even misspelled subdomain names DO resolve to something. What they resolve to is the IP address of an ad server that belongs to NetworkSolutions, and which apparently contains content provided by their good friends at DoubleClick.
But you knew that, because you are selling a passive DNS service, and because you thus know all about the ins and outs of DNS, right?
Just to add, we don’t exactly know what was on that printer.clintonemail.com. Could have been another windows print server for all we know, could have never been anything.
that exact disclaimer is in the story, Rafik.
Ah, Brian, it appears that both the Chinese and the Russians had complete access to Hillary’s rogue mail server going back to 2013. I’m not sure there’s any point in talking about the printer.
A Romanian cab driver, known as Guccifer and now sitting in a U.S. jail, claimed to have found her mail server and gotten complete access to it in 2013, up to two years before Farsight discovered it in March 2015.
But there is a subsequent story that claimed that Guccifer tried to hack into Russian systems which the Russians discovered. They, in turn, planted malware on Guccifer’s computer that allowed them to see everything that he was able to hack into. It’s likely that the Russians have every piece of email that went through Hillary’s server. If there are any missing, we should ask them about it.
http://www.wsj.com/articles/hillary-gets-guccifered-1462487970
The Wall Street Journal has a paywall but I’m a paid subscriber. I believe that when I get a link from them, it puts a hole in the paywall so I can share it with others. If you can’t read the story, please post a comment to let me know.
the wsj story is blocked
For any WSJ story…
Grab the first sentence in the article. Do a google search for the text with quotes at the start and end. Google returns a URL, click that link and read the story.
like most hackers, hes a pathological liar. Its in their nature. He came out real quick to brag and prove how he hacked a clinton aid. But didn’t want to tell anybody until he went to jail and she runing for president that that he hacked clintons emails? I call total BS.
Nobody with any brains believes the recent headline-grabbing pronouncements from this criminal Guccifer. He’s pretty obviously just failing around and hoping that he can come up with some topical story that will get him in the newspapers and maybe… if they are really dumb… entice his prosecutors into cutting him some sort of a deal if he “talks” about his alleged break-in to the Clinton server. But so far, he hasn’t produced a single shred of credible evidence to back up his wild claims, and as someone pointed out, it is really rather absurd, even or especially for someone in his position, to VOLUNTARILY cop to yet another federal felony.
The smart money says that if anyone ever did compromise any part of Clinton’s network, that party will be smart enough to NEVER talk about that, except to his paymasters, or to whoever is willing and able to purchase the exflitrated data, with utmost confidentiality and discretion, obviously.
> A clever Chinese hacker could have …
Why “Chinese hacker”? Why not just “hacker”?
Because a chinese hacker means that the chinese had access to the national security of the US!
I assume that when China, Russia, Israel, Germany, Britian, India, Pakistan, etc… reconnoitered Secretary Clinton’s web presence and discovered her use of a private email server and printer, they would have devoted the required time and resources to compromise them, one way or the other. That’s what state-sponsored intelligence services do. If I were either Clinton, I would assume my email was compromised and assume my nation-state adversaries have everything … just the same as if I used the State Department’s email system.
Ironically, she would have been better off using the State Dept. email system: she would have known from the start that eventually every message would be in the hands of our adversaries.
Sounds like a false positive Brian. Reminds me of anti piracy sites accusing “internet printers “of downloading torrents cause they saw the ip in the swarm but never actually direct connected to it. Totally meaningless.
All I know is that congress computers are constantly hacked by the chinese, russia, and even our own CIA was reprimanded for hacking them. The presidents computer and ipad was hacked and so was the first ladies emails.
But the closest anyone ever got to Hillary that we know of was a Bill Clinton aide. She probably had the most secure email in congress, although thats not saying much, most of them don’t even use email for fear of their privacy or for some because they don’t know how. So if security is peoples concern over this issue then they don’t realize most people are less secure then she ever was.
The bigger focus should be on how to make congress and state department networks more secure in general which this new report claims are pretty lacking. At least when Hillary was there she got the computers updated and made everybody learn how to use them…
She was the Secretary of State of the United States of America, not some housewife at home trying to set up her own computer for the first time. She wasn’t doing anything herself. She also had physical security and bodyguards around her at all times. When she becomes President she will have body doubles.
On another note it must be real hard for women to get respect in the computer industry too….
When she was Secretary of State, Hillary Clinton worked and lived in Washington, DC. Why would she have wanted to print out emails in Chappaqua, NY?
The printer could have resided anywhere. Just because the IP is hosted in NY, doesn’t mean the printer is there, just the print queue
I’ve had a printer exposed to the Internet for quite some time and I don’t get any random jobs submitted to it. Sadly, that’s exactly what I want. It prints directly to PDF.
My only worry is that the voting populace of America will be misled by the TV spin masters (right & left) who will take all of this “simple to understand” technical jargon and trivialize it as fairy tales dreamed up by paranoid pimple faced boys in their Mom’s basement….. It makes clear sense to us geeks, maybe we need a translator… 🙂
VTF
BTW – the dig mx ‘domainname’ command was brilliant !
Any indication what kind of printer she was using? Maybe even knowing the printer from the driver loaded on her server?
Many higher end MFP type printers have hard disks and are capable of permanently storing copies of every page they see or print – and they have plenty of open ports to attack – even Telnet is on by default on these things.
I wonder if an investigator has collected and audited the printer itself. Might give us some good ideas as to what she was up to that she had to hide it on her own personal stuff.
Two points:
1. DOCSIS – LOL.
While her cable company’s DOCSIS 3.1 does have encrypted features to prevent someone on the copper from doing the equivalent of ARP poisoning to pretend to be her gateway, I have not yet – anywhere in New England or the Mid Atlantic – found those encryption features enabled. They are left off intentionally by every provider I have tested probably for bandwidth profit reasons. Her packets were sniffable. Period.
2. FOX level hypocrisy detected.
Let’s not forget that Rove and Cheney ran the US government for years during a time of war using an Exchange 2003 RNC server. When called on it, suddenly (Oopsy, TeeHee!) all the millions of those email messages – and their backups – got ‘accidentally’ deleted rather than letting the world + dog see what those two chimps were trusting Microsoft security to keep safe. Any talk of Orange suits needs to put those two at the front of the line.
As far as I’m concerned with Hillary, I’d like to see her precedent more widely adopted – hardened personal mail stores to restore privacy. Screw the folks who think snooping everyone’s email is their personal right under some secret law.
“More importantly, any emails or other documents that the Clintons decided to print would be sent out over the Internet — however briefly — before going back to the printer. And that data may have been sniffable by other customers of the same ISP, Guilmette said.”
How/why would this be the case?
I can see if we make the assumption of all machines using internal IPs so packets headed to 24.187.234.188 would route out then bounce back in … but if it was local net, or if it was defined in hosts or the router (also assumptions) then it would never have to bounce out except for a a lookup.
or am I missing something here ..?
Did the sysadmin(s) who set up the mail and printer systems have security clearance(s) to read all the Mrs. Clinton’s mail and print jobs?
Because she certainly gave the sysadmin(s) the ability to read her mail and print jobs. archive the data, and transport the data anywhere. If that was not all done by State Department IT employee(s). how is this not a punishable offense?
It boggles my mind to think that anyone could defend Mrs. Clinton for this blatant breach of national security.
I dont have time to sift through the comments to see if anyone addressed the issue of the printer itself. If the printer isn’t secured, and is internet capable, that itself can be an attack avenue into the network and a person can gain a foothold much easier.
Not knowing the type of potential printer, I am sure some of them offer some sort configuration that can send the printable information through some sort of loop, allowing the traffic to be sniffed while being printed. I do NOT know if your are in the web view (http: ip address of printer) and the GUI allows you to view recently printed documents from the GUI. But if you have access to the GUI – you can adjust settings and I am sure can manipulate many things to gain an insiders view from the outside.
This is a pathetic long history about some one in power – be it somewhat limited in power, that appears not to give a flying leap about national security. A person can play stupid all day long. All it takes is one email with the marking removed, and proof that she read the same message with the markings intact and her “goose” is cooked.
It will be a SAD day should any official who is elected to a higher office does what she did.
All it is going to do is open up the gaping void of questions – SHE did it and it was OK, so why can’t I ?
noone even knows if there was really a printer there, thats whats laughable. I don’t understand how we are even talking about this.
And as far as “she did it so why can’t I ?” You have it totally backwards. everybody else does it, so why can’t she?! Even the head of the republican committee that was originally investigating her. had a gmail account on his business card. If anything, we can thank Hillary for a wake up call if OPM wasn’t enough.
At this point what does it matter? Mrs. Clinton can do NO wrong as far as her liberal fans go. She could kill and eat a baby on TV and her fans would still vote for her.
I thought thats what Trump said about his fans? haha
why must we always pick on someone that you do not always know the whole truth at all. maybe there is more than you know. she is always had the country at heart and always wants the best and so her husband was just as great. who do you want to win her or donald trump!
stop jumping on people until you know the whole truth. you have better things to do then think of bad things about people you do not know and their intentions.get a job and you will not have to worry.get a life and start to worry about your self because you can not change the world about your opinio, thats your own. get a life!!!!!!
“…she is always had the country at heart…”
Yea, and she has apparently gotten rich in the process. (Just a coincidence, I’m sure.)
“…who do you want to win her or donald trump!”
Neither! I stand shoulder to shoulder with 60% of the American public. All of us want a do-over for this whole rotten stinking fetid mess of a political year.
http://www.nbcnews.com/politics/2016-election/poll-majority-americans-dislike-hillary-clinton-donald-trump-n578926?cid=sm_tw&hootPostID=b1a8ae1c0d0ec893e65545bb564b8578
And just in case anybody here got the Wrong Idea and assumed that I was either a shill for, or a lackey for the Red Team, please, please, please, a beg you to tweet & retweet the following URL as often as possible. (This is a little something that I cooked up a couple of months ago, and I’m kinda proud of it. I did this even *before* someone clever snookered Trump into retweeting Mussolini quotes.)
http://tinyurl.com/h22cq5l
HA ! Your talking about Politicians. I personally will not be gullible to think there is no wrong doing here. And since this office is unwilling to do anything about it, it does not make it right.
My understanding is that the same person who set up Bill Clinton’s website and email after he left office set up Secretary Clinton’s; hence, the shared IP addresses for similarly worded domains. Also, wasn’t the same server used for both?
I think this person was granted immunity.
Worrying about whether an indictment is in the future is like wondering what verdicts a jury is going to return. That is something that I learned from a veteran attorney.
So I am in the printer industry, and this story is interesting for a couple of reasons.
1) Most IP based printers (read connected via ethernet card rather than USB “local” connection) allow for users and administrators to log in to the printer via the IP address and adjust settings, install new firmware, and so forth. For a state hacker, this could be gold – and the default “service” logins and passwords can typically be found in service manuals readily available on the web.
2) On that issue, one of the things that a lot of multi function devices (“all in one”) allow for is “multi plexing”. “Multi plexing” is performing multiple functions with a single job submission. For example, there are machines that can receive an incoming fax, print that fax out, forward the fax using SMB to an archive (typically, but not always on the same subnet), forward that fax via email to a recipient, forward that fax to another fax machine using telephony, forward that fax to a fax server using LAN faxing, and so on. You can see how tempting a multifunction machine would be to a a state intelligence service.
3) All the components in a machine are commercially available, from limited manufacturers – there are only so many manufacturers for memory, motherboards, etc. For a state intelligence service with a lot of money – setting up a clone in a lab to use as a template to re-engineer would be relatively cheap.
4) Many PostScript enabled printers allow for firmware upgrades as a PostScript print submission – so the printer could be reprogrammed with new firmware (essentially re engineered) remotely by anyone with access to the IP. Essentially, the multi plexing could be reprogrammed to sent print submissions out to a server controlled by a foreign intelligence service. Now, this isn’t something that a pimply faced hacker could do. Too expensive, and too time consuming. But if you had an organization that could figure out how to reprogram centrifuges…
5) Many printers by default “assign themselves” ports with known weaknesses (I’m looking at you, Port 8xxx), and open those ports up to allow communication over a network – for example, the “flag” that pops up on your computer to let you know the printer is out of paper. Depending on how a printer is set up for internet printing, this may or may not apply. Experienced IP administrators will go back, and change the port settings – if they think of it. But in many cases it is not something that they are thinking about.
I say follow the money. Look at the links between Clinton Foundation and classified information.
She setup a private email server knowingly to exempt her from compliance. Now, the after the fact doesn’t really matter. And she knows that… A .gov address would have full rights to all corispondance as the information belongs the the government and can be requested by ant civilian…
When I look up clintonmail.com….it appears to be owned by a woman living in Westmont, IL whose name is Clinton. The address checks with the white pages. Took me two minutes in Google.
Note the difference: clintonemail.com vs. clintonmail.com