The sextortion email scam last month that invoked a real password used by each recipient and threatened to release embarrassing Webcam videos almost certainly was not the work of one criminal or even one group of criminals. Rather, it’s likely that additional spammers and scammers piled on with their own versions of the phishing email after noticing that some recipients were actually paying up. The truth is we may never find out who’s responsible, but it’s still fun to follow some promising leads and see where they take us.

On August 7, 2018, a user on the forum of free email service hMailServer posted a copy of the sextortion email he received, noting that it included a password he’d formerly used online.
Helpfully, this user pasted a great deal of information from the spam email message, including the domain name from which it was sent (williehowell-dot-com) and the Internet address of the server that sent the message (46.161.42.91).
A look at the other domain names registered to this IP address block 46.161.42.x reveals some interesting patterns:
46.161.42.51 mail25.uscourtsgov[.]com
46.161.42.52 mail24.uscourtsgov[.]com
46.161.42.53 mail23.uscourtsgov[.]com
46.161.42.54 mail22.uscourtsgov[.]com
46.161.42.55 mail21.uscourtsgov[.]com
46.161.42.56 mail20.uscourtsgov[.]com
46.161.42.57 mail19.uscourtsgov[.]com
46.161.42.58 mail18.uscourtsgov[.]com
46.161.42.59 mail17.uscourtsgov[.]com
46.161.42.60 mail16.uscourtsgov[.]com
46.161.42.61 mail15.uscourtsgov[.]com
46.161.42.62 mail14.uscourtsgov[.]com
46.161.42.63 mail13.uscourtsgov[.]com
46.161.42.64 mail12.uscourtsgov[.]com
46.161.42.65 mail11.uscourtsgov[.]com
46.161.42.66 mail10.uscourtsgov[.]com
46.161.42.67 mail9.uscourtsgov[.]com
46.161.42.68 mail8.uscourtsgov[.]com
46.161.42.69 mail7.uscourtsgov[.]com
46.161.42.70 mail6.uscourtsgov[.]com
46.161.42.71 mail5.uscourtsgov[.]com
46.161.42.72 mail4.uscourtsgov[.]com
46.161.42.73 mail3.uscourtsgov[.]com
46.161.42.74 mail2.uscourtsgov[.]com
46.161.42.75 mail1.uscourtsgov[.]com
46.161.42.76 mail[.]commarysmith[.]com
46.161.42.77 mail.joancooper[.]com
46.161.42.78 mail.florencewoods[.]com
46.161.42.79 mail.ednawest[.]com
46.161.42.80 mail.ethelwebb[.]com
46.161.42.81 mail.eleanorhunt[.]com
46.161.42.82 mail.sallypierce[.]com
46.161.42.83 mail.reginaberry[.]com
46.161.42.84 mail.junecarroll[.]com
46.161.42.85 mail.robertaharper[.]com
46.161.42.86 mail.reneelane[.]com
46.161.42.87 mail.almaaustin[.]com
46.161.42.88 mail.elsiekelley[.]com
46.161.42.89 mail.vickifields[.]com
46.161.42.90 mail.ellaoliver[.]com
46.161.42.91 mail.williehowell[.]com
46.161.42.92 mail.veramccoy[.]com
46.161.42.93 mail.agnesbishop[.]com
46.161.42.94 mail.tanyagilbert[.]com
46.161.42.95 mail.mattiehoffman[.]com
46.161.42.96 mail.hildahopkins[.]com
46.161.42.97 beckymiles[.]com
46.161.42.98 mail.fayenorris[.]com
46.161.42.99 mail.joannaleonard[.]com
46.161.42.100 mail.rosieweber[.]com
46.161.42.101 mail.candicemanning[.]com
46.161.42.102 mail.sherirowe[.]com
46.161.42.103 mail.leticiagoodman[.]com
46.161.42.104 mail.myrafrancis[.]com
46.161.42.105 mail.jasminemaxwell[.]com
46.161.42.106 mail.eloisefrench[.]com
Search Google for any of those two-name domains above (e.g., fayenorris-dot-com) and you’ll see virtually all of them were used in these sextortion emails, and most were registered at the end of May 2018 through domain registrar Namecheap.
Notice the preponderance of the domain uscourtsgov-dot-com in the list above. All of those two-name domains used domain name servers (DNS servers) from uscourtsgov-dot-com at the time these emails were sent. In early June 2018, uscourtsgov-dot-com was associated with a Sigma ransomware scam delivered via spam. Victims who wanted their files back had to pay a bitcoin ransom.
In the months just before either the password-laced sextortion scam or the uscourtsgov-dot-com ransomware scam, uscourtsgov-com was devoid of content, aside from a message promoting the spamming services of the web site mtaexpert-dot-info. Uscourtsgov-dot-com is now offline, but it was active as of two weeks ago. Here’s what its homepage looked like:
The domain uscourtsgov-dot-com was redirecting visitors to mtaexpert-dot-info for many months up to and including the sextortion email campaign. Image: Domaintools.com
Interestingly, this same message promoting mtaexpert-dot-info appeared on the homepages of many other two-name domain names mentioned above (including fayenorris-dot-com):
In the email delivery space, MTA stands for mail transfer agent, and this MTA Expert company is essentially an anonymous spamming service. The screen shot below is from an Internet Archive cached copy of mtaexpert-dot-info:
Mtaexpert-dot-info doesn’t disclose who owns the site, and current WHOIS registration records for the domain are obscured by privacy services. But thanks to a historic WHOIS record lookup at Domaintools.com [full disclosure: Domaintools is an advertiser on this site], we can see that for about a week in May 2018 the WHOIS privacy veil briefly dropped off and revealed the following record:
Registrant Name: HICHAM AALLAM
Registrant Organization: investissonsorg
Registrant Street: RED ANASS BLOC 26 N 3 ROUTE DE TETOUANE
Registrant City: TANGER
Registrant State/Province: Tanger-Tetouan
Registrant Postal Code: 90001
Registrant Country: MA
Registrant Phone: +212.626280317
Registrant Phone Ext:
Registrant Fax:
Registrant Fax Ext:
Registrant Email: hicham.aallam60@gmail.com
Who is Hicham Aallam? According to his LinkedIn page, he is an email marketer living in Morocco and working for a company called Active Sun Network. His resume says he also works for AdGenics, which according to anti-spam group Spamhaus is a well-known spamming operation with a long, sordid history. AdGenics, a.k.a. Cabo Networks a.k.a SIFT Logic, is currently Number Six on Spamhaus’ Top Ten Worst Spammers list.
Contacted via LinkedIn, Aallam said he was unaware that his email service was used in either the sextortion or ransomware campaigns linked to the above-mentioned domains. He said an ad for Mtaexpert-dot-info automatically gets shown on the home page of any site that is configured to use his email-sending scripts.
Aallam says he charges customers to use these scripts, but that he only had one semi-recent customer: A person who contacted him using the Skype name “brian.ortega_4” paid roughly $250 worth of the cryptocurrency Ethereum (ETH) on Apr. 3, 2018 for a license to MTA Experts’ mailing script. Here is a record of that transaction. All of the ETH transactions attributed to and from that account can be seen here.
Okay, so we still might not know who’s responsible for sending some of these sextortion emails, and it could well be one of Aallam’s other clients behind these two schemes. Nevertheless, it’s always fascinating to see how far one can get just by following a few breadcrumbs.
One final breadcrumb to follow: The Internet address space occupied by the uscourtsgov-dot-com and the sextortion-related domains — 46.161.42.0/24. In May 2018, RiskIQ published a detailed report (PDF) about a complex phishing scheme that used an address adjacent to uscourtsgov-dot-com in a bid to steal Ethereum from MyEtherWallet users.
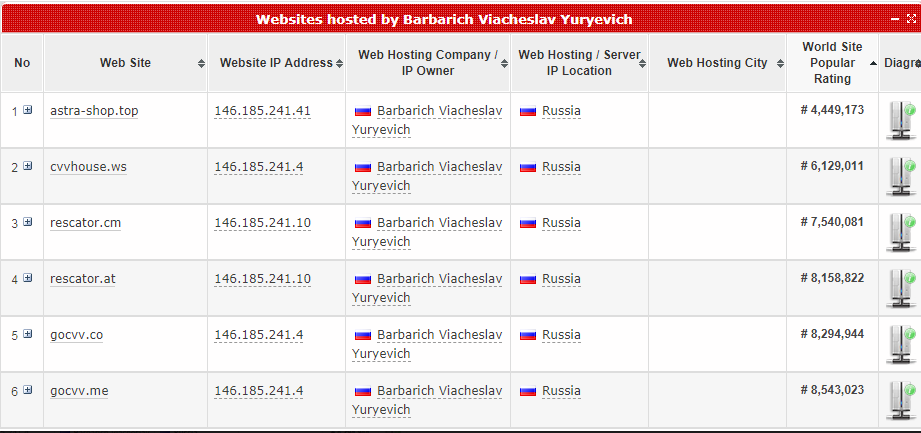
The registered owner of the Internet address space is a “Barbarich_Viacheslav_Yuryevich,” which is the same name as the owner of the network AS41995, a.k.a. web-shield-dot-biz. 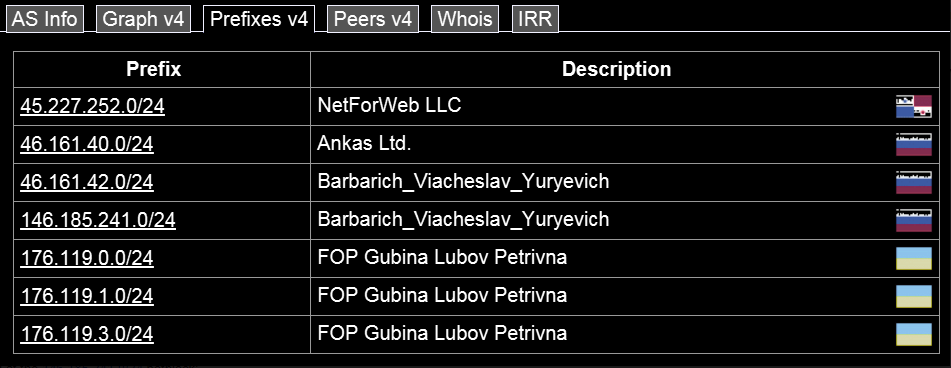
A different block of addresses that we can see in the graphic above assigned to Web-Shield — 146.185.241.0/24 — contains a metric truckload of domains involved in selling stolen credit cards.
Loyal readers of this site will notice a familiar domain there: Rescator. It belongs to a seasonsed cybercriminal by the same name who has been closely linked to the Target and Sally Beauty breaches, among many others. To this day — almost four years after the Target breach — the home page to Rescator’s stolen card shop includes a picture of Yours Truly as a postage stamp that reads, “As advertised by Brian Krebs.”
KrebsOnSecurity would like to thank security researcher Troy Mursch and anti-spam crusader Ron Guilmette for their assistance in this research.





Brian, namecheap that registered all those domain names is also a Russian company. They don’t disclose it. But pretty much everyone who works there has Russian sounding names.
Just because Namecheap’s customer support is Russian, which I am sure they are, that doesn’t mean the company is Russian. FWIW, Namecheap’s customer support is the best of any hosting service I have used, and that includes a lot of big names. It certainly is true that a lot of “bad” domains get registered through Namecheap.
I asked one Namecheap support agent where she was from and she said the Ukraine. I have no reason to doubt it. I also have found Namecheap support to be extremely good on all support areas.
As a customer of Namecheap (previously of GoDaddy) I can confirm that their support, admittedly rarely needed, is first class. It’s a very professional operation. I aim to use only the best and most ethical service providers, and always willing to vote with my feet.
This is a good point. I know lots of folks who farm their support out to Russian companies while the servers and the users are in the US.
I wonder how many of those sites have been used as cover by the FSB?
You must be a Democrat… Help, there’s a Russian under my bed
Dennis, There are culpable hosting companies in the United States that participate in criminal enterprises. I found a scammer that poses as a staffing company that convinces his targets that he needs their SSN and DOBs. He registers a large number of domains and uses US based hosting companies for his fake company web site and email service. I warned a hosting company based in Bria California about what was going on and they replied they did not care. Even though the scam was specifically against their terms of service. I built a blogger site under an alias to warn others (since its an alias I don’t have a financial connection).
https://fakestaffing.blogspot.com
mine seems to have come from kiolliefkp@outlook.com.
http://whois.domaintools.com/104.47.1.227
People have been using a lot of free email services- outlook.com in particular- to spread this one. Sometimes (but not always) the full header will reveal an IP of origin.
Great informative article as always !
In the examples I’ve seen of this particular spam, the sending hosts were:
navigantenergy.net [90.156.139.163]
prstene.com [90.156.139.160]
philadelphiametalscene.com [193.124.202.154]
benhaimfamily.com [185.197.75.120]
which are all in Russia.
The earliest one dates from 28 May 2018.
That name Hicham Aallam looks really familiar; I’m sure he’s come up in some of my recent research. A surprising amount of spam advertising French companies seems to come from Moroccan bulkmail outfits, and it’s possible that that’s where I saw it. But given that this scammer seems to be using more than just Aallam’s servers to send, maybe it’s not so important.
Incidentally, Namecheap seems to be a US company (founder is American, official address is in LA), but they employ a lot of Ukrainian — not Russian — support staff.
I am available for gumshoe investigation to the sources.
410-903-2759
Thanks Judge Bartel.
Very interesting findings… It is good to recall, that the world today is increasingly global, so identities like Russians, Americans or Malaysians, to name a few at random, carry less and less significance. These old schemes of identity of course can be useful in tracking down traces, yet, attribution by nationality should be avoided. I do not know about Russiansa, but to my understanding, their “communities” are actually stronger outside of Russia than inside. Let me have it wrong there. And if tha is the case, the valid question remains, should one create attribution to the host-country or the legacy concept of nationalism?
My guess is that if you want to spam the western world it is good to rent your infrastructure in an eastern country and vice versa. Which means that I wouldn’t be surprised if many mails that spam Russia were be sent using servers that stand in the USA.
The names “Barbarich_Viacheslav_Yuryevich”, “NetForWeb LLC” and “FOP Gubina Lubov Petrivna” appear in the recently published report “BGP / DNS Hijacks Target Payment Systems” https://blogs.oracle.com/internetintelligence/bgp-dns-hijacks-target-payment-systems
Namecheap is good company you can buy cheap good domain with good price !
And what is very good is you can use bitcoins every eastern europeans russians ukrainens use bitcoins.
Bitcoin is good money payment thing.
I think russians should say fck off to western investihation guy
s putin should protect own people !
Doesnt matter if crimimals western.society is so vulnebre
Smart russians offcourse take from western countries.
Offcourse they steal from soft western people
Baron – your logic is lamentable and exactly recalls that of Hitler’s supporters. Do you know how that worked out? Remember it when China moves in to take the soft Russian east. Meanwhile, enjoy what is essentially still a slave life in your mafia-run fake democracy, with a brain shaped by 24/7 state propaganda.
Today there are 2 live sites from the list:
florencewoods[dot]com has address 46.161.42.78
joancooper[dot]com has address 46.161.42.77
Both redirect to
Automated Mailing Server Installer {LINK:}http://mtaexpert[dot]info- Bulk Emailing Made Easy!
But as already noted, mtaexpert has been suspended by Namecheap with
Name Server: BLOCKEDDUETOSPAM.PLEASECONTACTSUPPORT.COM
We as a card payment network company have found tens of phishing domains registered on Namecheap and have a continuous problem in this regard. I don’t know what is the advantage of Namecheap for phishers.
Among the advantages: “cheap.”
Excellent research work as always Brian.
Thank you for all that you do for us.
I have a ton of these (30-50) I’ve seen hitting our own domain. I somehow doubt poring over them would turn up anything revelatory.
Still, if it interests.
Allowing anonymous domain registrations was one of the worst things for the internet. A requirement for a valid, working email address, mail address, and contact phone in order to keep the domain active would make most of these scammers up and quit their job.
Wrong! They would just use some poor smack from the street – pay him $20 and the results would be the same. This is what they do with bank accounts today – you are not allowed to have a checking account opened without verifying your identity, yet these guys have hundreds of accounts at their disposal… Most if not all opened in exchange for a few beers or few grams of some white powder…
The team at Joy of Tech were inspired by the screencam extortion scam and created a cartoon. They normally focus on Macintosh and social media news.
https://www.geekculture.com/joyoftech/joyimages/2541.gif
I have been reading JoyOfTech for years. They are funny.
Now if the US Postal Service would just give you the same honor, Brian! 🙂
I was going to joke that it would not be a good thing for Brian if that were to happen since the USPS has had a long-standing policy of only honoring *dead* people on stamps. But that policy was rescinded in 2011.
Excellent research. You sir are truly doing what you were meant to do! Between you and Steve Gibson I can get my daily fix of techno-sleuthing… 🙂
I was the recipient of one of these, and am wondering if the amount “requested” of me is a record: most of the others I’ve seen or have seen reference to mention amounts of less than $1k or so. My requested “donation” was $7k!
The inclusion of the old password made me think it was quite real, but the devil is in the details…for example, I don’t have a FB account, and the incoming mentioned that my FB account was among the sources of my contacts. The big tip off was the supposed camera hijack: I have no webcam on this machine.
I’ve kept a copy in case anyone wants to see it. It came to me from Kristofer Bunker
Thanks for all the good work.
jkl
Excellent article. My org received quite a few of these. Thankfully, our security awareness training is excellent.
Hello, Many thank you for sharing. the article gives more information and helpful for me and I like the writing ability. I know and recognize the records in your article. I will use it to be beneficial
is anyone – ANYONE – going to do anything about Namecheap? Nope, let’s just lie down and take it up the rear with Vaseline.
It’s great we’re all talking about them, writing about them – yet in the meantime they’re responsible for millions in criminal acts.
Or more – who knows whether they didn’t have a huge part in Wannacry, NotPetya, SamSam, or other distribution.
Yet global authorities – LEO and Interpol and the FBI – are complete joke outfits staffed by cyber wannabe clowns with law degrees.
How can we get in contact with you? We have a lot of very important information that I would like to share about a very big Russian group that has and is not only scamming or catfishing for money but there is extortion and violence also. I do not want to leave a lot of info here but would like to be able to talk to you via email or even phone if possible or anyone who can help myself and my family. Please respond (we are considering going to the FBI or IC3 ) as we have been advised to by someone FROM this group, that is how bad it has become. Thank you