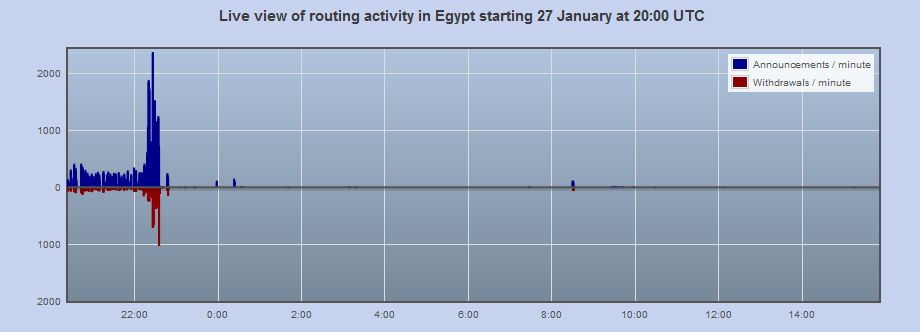
In October 2010, I discovered that the authors of the SpyEye and ZeuS banking Trojans — once competitors in the market for botnet creation and management kits — were planning to kill further development of ZeuS and fuse the two malware families into one supertrojan. Initially, I heard some skepticism from folks in the security community about this. But three months later, security experts are starting to catch glimpses of this new hybrid Trojan in the wild, with the author(s) shipping a series of beta releases that include updated features on a nearly-daily basis.
It probably didn’t help that the first report of a blended version of SpyEye/ZeuS (referred to as SpyZeuS for the remainder of this post) — detailed in a McAfee blog post — turned out to be a scam. But a little more a week ago, Trend Micro spotted snapshots and details of SpyZeuS components, noting that the author appears to have received help from other criminals in polishing this latest release; in particular, an add-on that grabs credit card numbers from hacked PCs, and a plugin designed to attack the anti-Trojan tool Rapport from Trusteer. (Trusteer’s Amit Klein addresses this component in a blog post here).
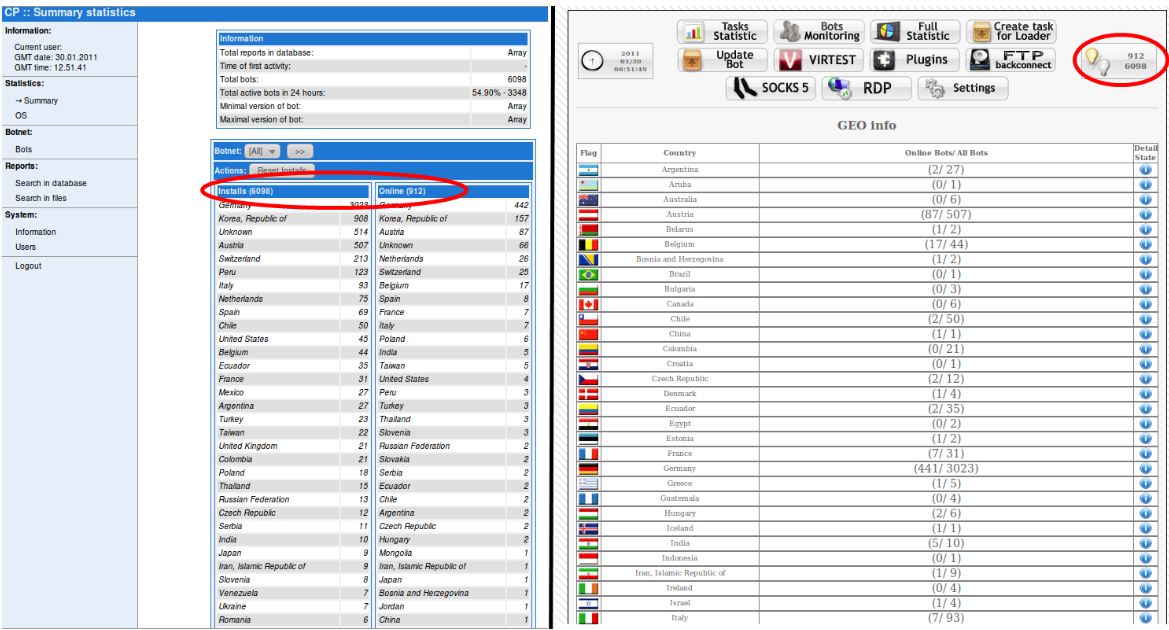
Seculert, a new threat alert service started by former RSA fraud expert Aviv Raff, includes some screen shots of the administrative panel of SpyZeuS that show the author trying to appeal to users of both Trojans, by allowing customers to control and update their botnets using either the traditional ZeuS or SpyEye Web interface.