In response to a series of costly online banking heists perpetrated against towns, cities and school districts, Sen. Charles Schumer (D-NY) has introduced legislation that would extend those entities the same protections afforded to consumers who are victims of e-banking fraud.
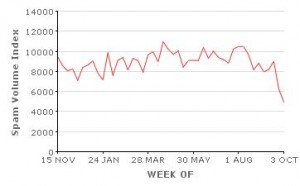
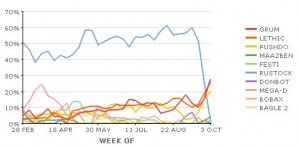
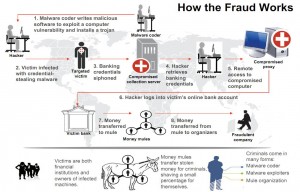
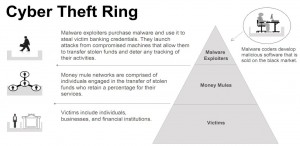
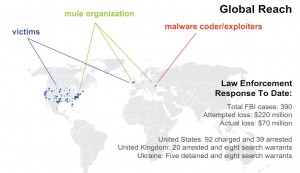
Under “Regulation E” of the Electronic Funds Transfer Act (EFTA) consumers are not liable for financial losses due to fraud — including account takeovers due to lost or stolen usernames and passwords — if they promptly report the unauthorized activity. However, entities that experience similar fraud with a commercial or business banking account do not enjoy the same protections and often are forced to absorb the losses. Organized cyber thieves, meanwhile, have stolen more than $70 million from small to mid-sized businesses, nonprofits, towns and cities, according to the FBI.
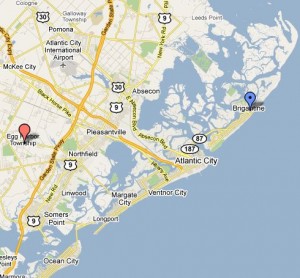
On Sept. 29, computer crooks stole $600,000 from the coastal town of Brigantine, N.J.; seven months earlier, computer crooks stole $100,000 from Egg Harbor Township just 20 miles away. In late December 2009, an organized cyber gang took $3.8 million from the Duanesburg Central School District in Schumer’s home state. In that attack, the bank managed to retrieve some of the money, but the district is still missing roughly $500,000.
The same day as the Brigantine breach, Schumer introduced S. 3898, a bill that would extend EFTA’s Regulation E protections to certain local government entities, including municipalities and school districts. The Board of Governors of the Federal Reserve System is to define which entities are included in the categories of “municipality” and “school district.”
Steve Verdier, executive vice president and director of congressional affairs for the Independent Community Bankers of America, said the thinking behind the current law is that banks can absorb the losses from this type of fraud when it happens to consumers because there is usually a comparatively smaller amount of money involved.
“The bank is probably in no better position to protect against this type of fraud than the [business] account holder,” Verdier said. “Whereas consumers may not be as good a position to protect themselves against these types of losses, you would hope a government or school district would have employee procedures to guard against this type of thing. And if the bank is forced to start making good on these losses, that weakens its ability to serve consumers and they’re going to have to price that risk into all of their services.”
Avivah Litan, a financial fraud analyst with Gartner Inc., said there are a number of promising new technologies that banks can make available to their customers that help guard against these attacks, referring to several products that use specially encoded USB keys to load a virtual operating system on the customers computer and encrypt the keystrokes between the bank and the customer.
“Also, why limit this to schools and municipalities? Small businesses have just as much risk as school districts, as do churches for that matter,” Litan said. “So does that mean that small businesses have more resources to deal with this type of fraud than cities and counties do?”
There isn’t much — if any — likelihood that the bill will be acted upon before the November elections, in which case Schumer will need to reintroduce the bill when the 112th Congress convenes early next year.
A copy of Schumer’s bill is here (PDF).