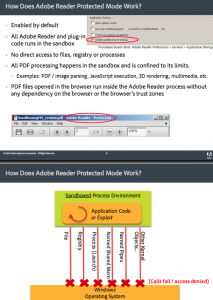
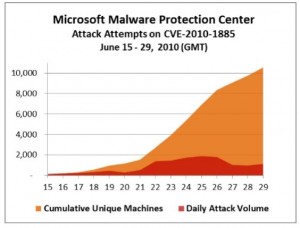
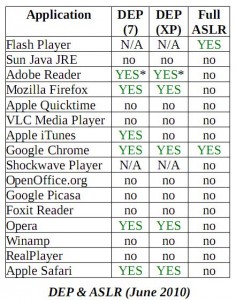
Virus writers and botmasters increasingly are turning to new subscription services that test when and whether malicious links have been flagged by Web reputation programs like Google Safe Browsing and McAfee SiteAdvisor.
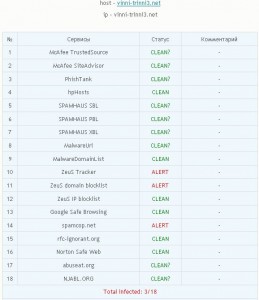 Nothing puts a crimp in the traffic to booby-trapped Web sites like being listed on multiple Internet reputation services that collect and publish information on the location of nasty Web sites. People who maintain the bad sites can stay ahead of such services by moving their malware to new domains once the present hosts start showing up on too many blacklists. But constantly checking these lists can be a time-consuming pain.
Nothing puts a crimp in the traffic to booby-trapped Web sites like being listed on multiple Internet reputation services that collect and publish information on the location of nasty Web sites. People who maintain the bad sites can stay ahead of such services by moving their malware to new domains once the present hosts start showing up on too many blacklists. But constantly checking these lists can be a time-consuming pain.
Enter sites like check-crypt.com. For a mere 20 cents, subscribers can check to see whether their malicious sites are flagged by any of 18 different blacklists, including Spamhaus, ZeuSTracker, SpamCop, SmartScreen (anti-malware and anti-phishing technology built into IE7/IE8), Norton Safe Web, Phishtank, Malwaredomainlist and MalwareURL.
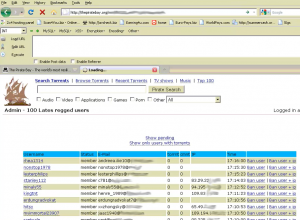
As we can see from the screen shot here, this service acts as a kind of Virustotal for bad domains, listing the percentage of blacklists that detect any submitted malware sites.
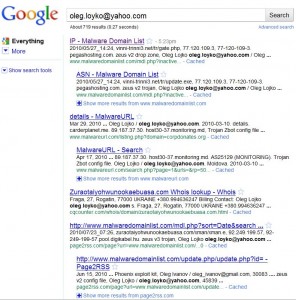 The name and address of the person who registered check-crypt.com is protected by a domain privacy service, but if we dig far enough back in the WHOIS history we see it was registered to someone named Oleg Lojko in Rogatin, Ukraine. A search for the e-mail address attached to that record turns up a domain (vinni-trinni3.net) that a couple of the malware blacklists have flagged for distributing the infamous Zeus Trojan, a powerful password-stealing strain of malicious software.
The name and address of the person who registered check-crypt.com is protected by a domain privacy service, but if we dig far enough back in the WHOIS history we see it was registered to someone named Oleg Lojko in Rogatin, Ukraine. A search for the e-mail address attached to that record turns up a domain (vinni-trinni3.net) that a couple of the malware blacklists have flagged for distributing the infamous Zeus Trojan, a powerful password-stealing strain of malicious software.
I wanted to test this service, and so I thought I’d pick on vinni-trinni, because that site was first flagged by Malwaredomainlist and MalwareURL back in March of this year. The results were underwhelming: As we can see from the above screen shot, this service detects that three out of 18 blacklists have flagged it as malicious, but the author’s own service fails to show listings by either Malwaredomainlist or MalwareURL.