Not long after I launched this blog, I wrote about the damage wrought by the Eleonore Exploit Kit, an increasingly prevalent commercial hacking tool that makes it easy for criminals to booby-trap Web sites with malicious software. That post generated tremendous public interest because it offered a peek at the statistics page that normally only the criminals operating these kits get to see. I’m revisiting this topic again because I managed to have a look at another live Eleonore exploit pack panel, and the data seem to reinforce a previous observation: Today’s attackers care less about the browser you use and more about whether your third-party browser add-ons and plugins are out-of-date and exploitable.
Hacked and malicious sites retrofitted with kits like Eleonore have become more common of late: In a report issued this week, Web security firm Zscaler found that roughly 5 percent of the browser exploits they identified during the first quarter of this year were tied to hacked or malicious sites that criminals had outfitted with some version of Eleonore.
Like most exploit kits, Eleonore is designed to invisibly probe the visitor’s browser for known security vulnerabilities, and then use the first one found as a vehicle to silently install malicious software. The hacker’s end of the kit is a Web-based interface that features detailed stats on the percentage of visitors to the booby-trapped site(s) that are successfully attacked, and which software vulnerabilities were most successful in leading to the installation of the hacker’s malware.
This particular Eleonore kit — which is currently stitched into several live adult Web sites — comes with at least a half-dozen browser exploits, including three that target Internet Explorer flaws, two that attack Java bugs, and one that targets a range of Adobe PDF Reader vulnerabilities. According to this kit’s stats page, the malicious adult sites manage to infect roughly every one in ten visitors.
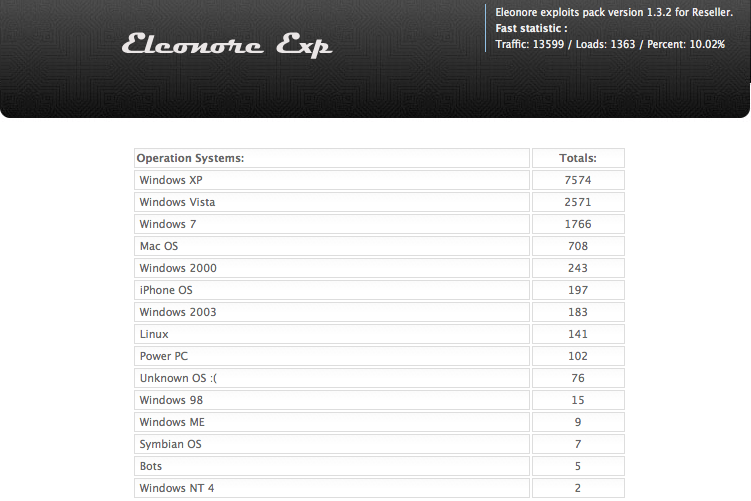
As we can see from the landing page pictured above, Windows XP users represent by far the largest group of users hitting these poisoned porn sites.
Once again, Eleonore shows just how heavily Java flaws are now being used to infect computers (the above graphic shows the number of successful malware installations or “loads” per exploit). The last time I reviewed a working Eleonore admin panel, we saw that Java flaws were the second most reliable exploits. This time around, Java was the biggest source infections. In the Eleonore kit I wrote about earlier this year, some 34 percent of the systems that were successfully exploited were attacked via a Java flaw. In this installation, four out of every ten victims who were hacked were compromised because of they were running an outdated version of Java.
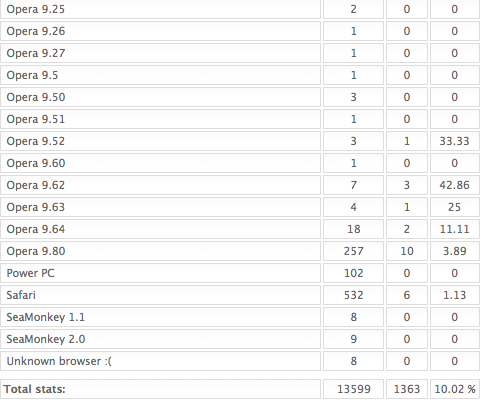
Nearly one-third of all successful attacks from this Eleonore kit leveraged flaws in older versions of Adobe’s PDF Reader. People often scoff when I recommend an alternative to Adobe for displaying PDFs, saying that criminals can just as easily target security vulnerabilities in those applications, which ship far fewer security updates than Adobe. That may be true, but I haven’t seen much evidence that hackers are going after flaws in non-Adobe PDF readers at any appreciable or comparable level. Incidentally, if you use the free PDF reader from Foxit, an Adobe alternative I’ve often recommended, you should know that Foxit recently shipped a new version — v. 3.31 — that includes security improvements.
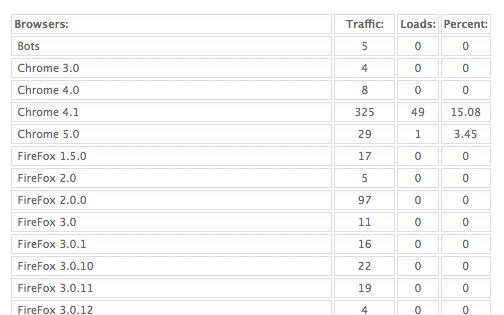
I also found this time around similar percentages of exploit victims among those surfing with different versions of Internet Explorer. With this Eleonore kit, more than one-third of those who visited the exploit site with IE6 were loaded with malicious software. The Eleonore admin panel reported that more than 12 percent of IE7 users and 20 percent of IE8 surfers visited and subsequently were infected with malware. The prevalence of IE users among the victims may be due in part to the fact that half of the exploits used by this particular kit target IE security holes.
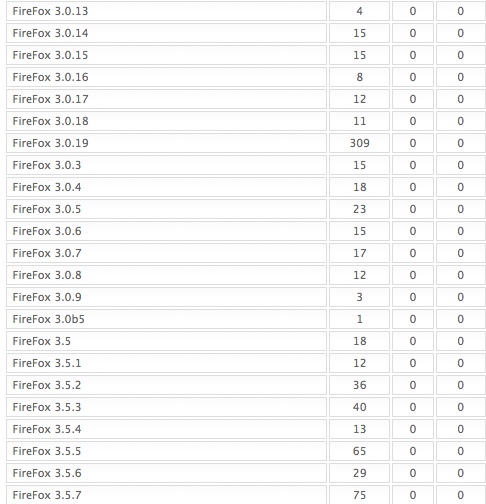
Annoyingly, this Eleonore admin page doesn’t resolve one of the open questions I heard most frequently after my last story on Eleonore: Where are all the Firefox victims? I still don’t have a decent answer to that puzzle, but I do have a couple of guesses. For one thing, unlike the last Eleonore kit I examined, this one does not include an exploit specifically for Firefox. It’s also possible that these kits are detecting Firefox visitors as users of some other browser (the report indicates, for example, that 15 percent of Google Chrome users browsing with version 4.1 were successfully attacked). Whatever the reason, it seems highly unlikely that all of the nearly 5,600 Firefox users who visited the exploit sites detailed here escaped unscathed.
Anyway, below are the stats, which start with those of Chrome and Firefox visitors:
…more Firefox stats and then IE, Opera and Safari…






Hi Brian
I’m looking forward to reading more on the Chrome/Firefox puzzle…
Firefox and Seamonkey check for updates for add-ons and plug-ins every time you launch them. It makes it much less likely that you’ll have a vulnerability that’s been around long enough to be incorporated into a canned software program for use by malware distributors without their own skills. It doesn’t mean there are no Firefox or Seamonkey people being infected; it means that looking at only people infected via Eleonore is a sampling error.
Of the 1363 successful loads, 1289 exploited some version of MSIE. That’s 94.6 % of the successful loads.
Friends don’t let friends drive IE.
It would be more meaningful to look at the number of successful loads as a percentage of the total number of computers using IE. Considering the popularity of IE, the percentage would be minuscule.
According Net Applications, MSIE’s world market share is 59%. In this sample, MSIE accounted for just 47% of the total traffic. That means IE’s traffic was actually under-represented compared to its world market share, yet (if you believe the Firefox numbers) it still accounted for a stunning 94.6 of the successful loads .
That said, I agree with Brian’s statement…”it seems highly unlikely that all of the nearly 5,600 Firefox users who visited the exploit sites detailed here escaped unscathed.”
I agree TJ;
Most of the FF users I know make it a habit to “approve all on page” using the NoScript control wide open.
With that set that way there is less advantage on page protection, unless they are at least using ABP.
How many of these are government workers (browsing porn) who are stuck on older versions of IE and/or have IE, Adobe Reader, and Java installed as part of the default Windows configuration. All three are part of a base install in many organizations! 🙁
This also reinforces my strict practice of limiting what software is installed in order to reduce the attack surface of my systems. (Ex. no Java or Adobe Reader)
xAdmin, why pick on government workers? Any hard data to validate your prejudice? Or just blind bias?
fyi I run Firefox as do many of my colleagues and our customers in this government agency. Before joining the Feds I was at a bank that forced everyone to use IE, so my experience is exactly opposite what you suggest.
While it was somewhat in jest, Google “SEC porn” 🙂
With regards to Java, I now go into the Java panel and configure it to check for updates every *day*, rather than just the default of checking once a month. I wonder if Oracle will ever configure Java to default to checking on a daily basis.
Thanks for the timely warning, Brian. I’m a Foxit user, but don’t want the toolbars that come with the new version. I’m waiting for them to contact me about getting the modified version they say is available.
I don’t visit the adult sites (I hate it that such places are called ‘adult’. Why not use the word ‘porn’ or think of another way term? ‘Adult book stores’ always ticked me off, too. There were ‘children’s booksstores. Maybe the rest of us grown-ups should go with grown-up to designate suitable for us! But I digress!), but just in case… I’ll avoid Foxit until I get the new version.
And I’ll check on Java, too, but the last offering of that seemed to be a beta…
To avoid the browser toolbar offers, use the zip version and just extract the exe file to where you want it and create a shortcut to it.
Foxit made it easier to get the zip, just click on “zip” next to the version you want on the downloads page:
http://www.foxitsoftware.com/downloads/index.php
To add extra security, you can also easily disable Javascript in Foxit by going to “Tools, Preferences, Javascript” in the program and uncheck “Enable JavaScript Actions”.
If you’re talking about toolbars within Foxit, again go to “Tools, Preferences, Internet Search” and ensure there is a check mark next to “Hide Ask.com Search Button”.
(No, I don’t work for Foxit! Just passing along what I’ve learned 🙂 )
As to Java, if you really don’t need it, I would highly recommend uninstalling it!!!
And while your in Preferences, click on Trust Manager and enable safe reading.
Does anyone know which specific Oracle Sun Java exploits, the latest Eleonore is using? CVE-2010-0842 (MixerSequencer) is a new exploited vulnerability which I believe was patched in March 2010 with JRE 6 Update 19.
@Dan
I’m seeing:
MidiSystem.getSoundbank(new URL(s3));
in the lastest two decompiled java files from Eleanore 1.4.1.
So whats the solution to Java/Adobe problems? To update those packages you need to be an administrator (I think) but giving users that sort of access isn’t good.
If you are running a Windows domain environment, use the Software Distribution GPO component of Group Policy to push out Adobe Reader and Java. The install occurs under the machine account when the system is rebooted, before the user logs on.
Brian, the latest Foxit version should be 3.3.1 rather than 3.31.
Thanks for the Foxit heads-up. Secunia doesn’t seem to check with them, or at least they didn’t flag my older 3.2.1 version.
Dear Bart;
Secunia PSI does track Foxit: Here is the last exploit:
http://secunia.com/community/forum/thread/show/4295/foxit_reader_embedded_program_execution_vulnerability
I am using version 3.3.1.0518
I rarely see Foxit flagged by Secunia, because my FileHippo update checker keeps me informed of new updates long before the vulnerabilities are discovered. [so far]
This single time I noticed it was flagged, there was a solution to that in the Secunia PSI console link.
Secunia PSI will only show you updates that are known to fix a vulnerability – if you installed version isn’t “dangerous” it won’t complain.
Yes, Wladimir, of course. Thank you!
I was just saying that Secunia did not flag my 3.2.1 version on their weekly scans.
Yes of course, any version including and after version 3.2.1.0401 is secure, even if it is not the latest version.
That is probably why it is not flagging it. I guess I just assumed folks could read between the lines; I digress.
This is a great article and presents the opportunity for further discussion and investigation. If you were to visit one of these sites on a machinge running a new installation of xp with the latest patches installed and no 3rd party software installed (java, Adobe, Word..), would you be vulnerable?
There are exploits for Foxit reader and Firefox, but they are generally safer to use, could say the same for Unix systems – generally safer.
About Firefox, I imagine most people install some add-ons after a while using Firefox, for example Web of trust and No script are recommended for install by Mozilla on their add-on page… it could effect the statistics they could block exploited pages.
Don’t forget that you can find more rotten apples in the biggest orchard, in this case IE and Adobe software.
The more competent bad guys will possibly include Firefox, Foxit reader or Unix exploits on compromised websites, but statistically you are much safer with those(among other things).
General knowledge about malware installing methods and being a bit computer savvy will keep you more safe but the low amount of users who qualify to this category do not change the statistics.
Yes, the Firefox stats remain puzzling. Your guess that “these kits are detecting Firefox visitors as users of some other browser” isn’t really likely – Firefox visit numbers make total sense. Maybe the exploit kit can correctly recognize Firefox visits but not infections through Firefox. But given that for the latter the browser is probably not used at all I cannot see how this can be.
Btw, thank you for this Foxit hint – for some reason Foxit didn’t notify me about an update yet.
Hey look… there are six people running Safari on Windows!
I’m also using Safari on Windows, though I generally use a different browser when accessing adult sites (therefore I’m probably not one of the six in the statistics) 🙂
Haha. Yes, and 197 people surfing porn with their iPhones!