Big Tech’s Mixed Response to U.S. Treasury Sanctions
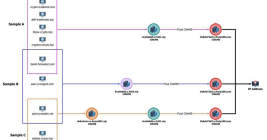
In May 2025, the U.S. government sanctioned a Chinese national for operating a cloud provider linked to the majority of virtual currency investment scam websites reported to the FBI. But more than a month later, the accused continues to openly operate accounts at a slew of American tech companies, including Facebook, Github, LinkedIn, PayPal and Twitter/X.