New Protections for Food Benefits Stolen by Skimmers
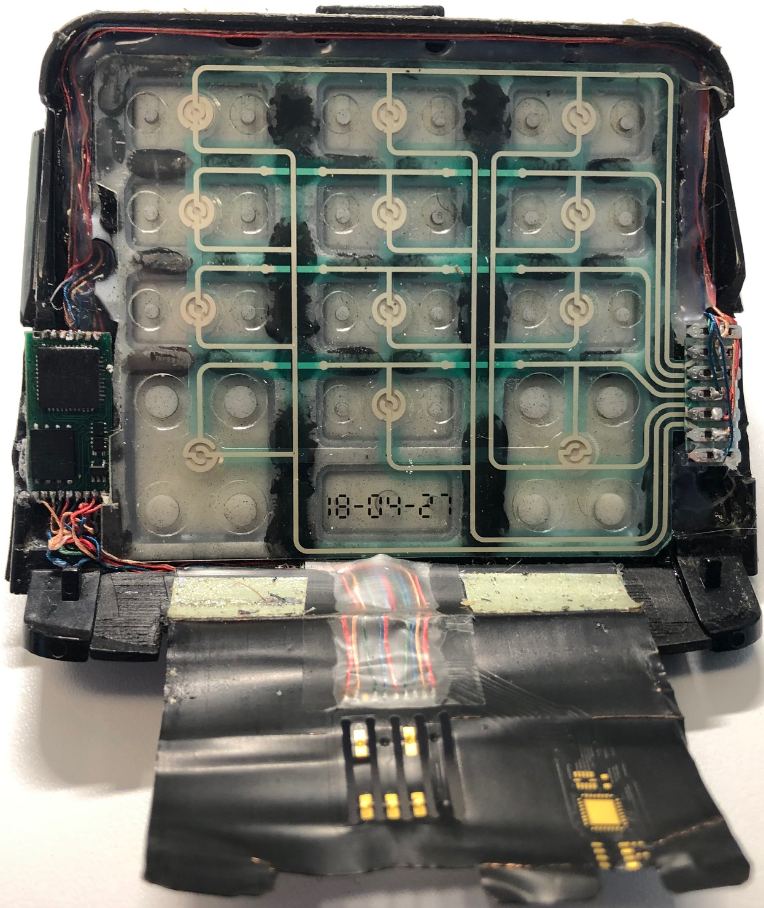
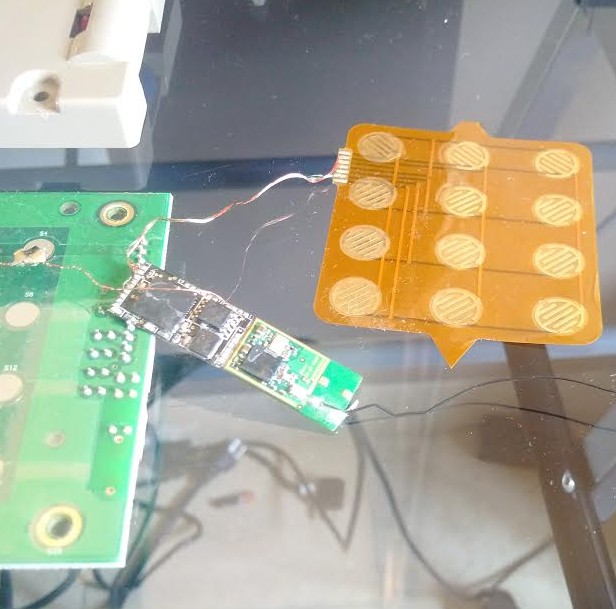
Millions of Americans receiving food assistance benefits just earned a new right that they can’t yet enforce: The right to be reimbursed if funds on their Electronic Benefit Transfer (EBT) cards are stolen by card skimming devices secretly installed at cash machines and grocery store checkout lanes.