Proxy Services Feast on Ukraine’s IP Address Exodus
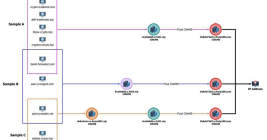
Ukraine has seen nearly one-fifth of its Internet space come under Russian control or sold to Internet address brokers since February 2022, a new study finds. The analysis indicates large chunks of Ukrainian Internet address space are now in the hands of proxy and anonymity services nested at some of America’s largest Internet service providers (ISPs).