A major new malware spam campaign mimicking invites sent via business networking site LinkedIn.com leverages user trust and a kitchen sink of browser exploits in a bid to install the password-stealing ZeuS Trojan.
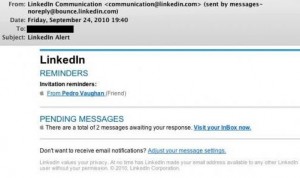 The spam campaign began Monday morning, according to security experts at networking giant Cisco Systems, and for a while the fake LinkedIn invitations accounted for as much as 24 percent of all spam. Recipients who click links in the message are taken to a Web page that reads, “Please Waiting, 4 seconds,” and then sent on to Google.com.
The spam campaign began Monday morning, according to security experts at networking giant Cisco Systems, and for a while the fake LinkedIn invitations accounted for as much as 24 percent of all spam. Recipients who click links in the message are taken to a Web page that reads, “Please Waiting, 4 seconds,” and then sent on to Google.com.
On the way to Google, however, the victim’s browser is silently passed through a site equipped with what appears to be the SEO Exploit Pack, a commercial crimeware kit that tries to exploit more than a dozen browser vulnerabilities in an attempt to install ZeuS.
This attack will no doubt fool a large number of people. Dan Tynan, a reporter for IT World, said he was tricked into clicking the link and possibly infecting his system.
It’s a good idea to avoid clicking social networking site invites that arrive by e-mail, especially if you don’t recognize the name of the person who’s inviting you. Instead, consider just browsing to the social networking site and handling any invites there. Also, this attack is a good reminder that it pays to stay up-to-date on the latest security patches.
What interests me most about this scam is that it shows that criminals wielding ZeuS are now using employment-oriented online services both to infect new PCs and to “cash out” these same victims, thanks to money mules recruited at job search sites like Monster.com and Careerbuilder.com.
I asked Cisco to supply more information about the domains used in this attack. Some of that information is included at the summary listed here (please take care with the domains on this list — they all should be considered hostile).





BitDefender released its Zbot/Zeus removal tool.
The Zbot Removal Tool can be downloaded from the ‘Removal Tools’ section of malwarecity.com, a BitDefender initiative for the software security community and a free resource for those interested in their online security.
We use OpenDNS (free) for our DNS. I’ve blocked all .ru and .cn domains. We don’t need them.
We actually started seeing a huge spike in HTML attachment spam the week before. On that Monday the general campaign moved the malicious JavaScript inside of an HTML “disguise”, with LinkedIn being just one of many possible attachments, restaurant specials being another, complete with attractive graphics. The JavaScript was essentially the same but the redirection targets changed from pharmacy to fake-AV and finally Zeus. The unifying thread was the inclusion of HTML as a seperate attachment rather than as inline content.
http://www.barracudalabs.com/wordpress/index.php/2010/09/23/html-is-not-harmless-email-security-update/
I got the first LinkedIn email Friday afternoon about 10 till 5pm. We also saw a large increase of fake emails with html attachments last week and started blocking all .html attachments.
Wow, I went over and read Dan Tynan’s article and am just amazed in the sheer stupidity of his actions. Now he may not have actually done it as described and could be using it as a “teachable moment”, but it’s one of those, “Can someone be that stupid?” type of thoughts, especially an IT reporter for a major computer magazine. What is really scary is I know from experience his actions are all too common among general computer users! 🙁
IMHO, this attack is a good example of why NOT to use social networking! It’s just ripe for exploitation!
Regardless, best practice: NEVER, NEVER, NEVER click on links or attachments in e-mail you were not expecting. Even then, use extreme caution!
This has nothing to do with social networking and everything to do with Adobe Reader, which the SEOSploit pack exploits. Linkedin was not compromised in any way. You could craft that link any way you like “pr0n ph0t0s click h3r3!!” would get you millions of clicks. The “You have here” email did just that!
The problem is that browser plugins are not being updated. Browsers need to warn people about out of date plug-ins. Adobe needs to start writing more secure code or people should just start moving away from them.
Ugh – just a matter of time before the bad guys targeted LinkedIn like this.
To compound the problem, I just had to remove the blocking rule at the smtp gateway which detected javascript in html attachments as it was blocking too many legit emails.
And what were those legit emails? So-called ‘secure’ email notifications from companies advising our users to start the process of retrieving their secure email by double-clicking on the handy little html attachment.
I despair!!!
So the SEOSploit kit is a bunch of PDFs that exploit one of many Adobe’s vulernatibilies. This is really unacceptable, Adobe has almost single-handedly destroyed the internet. Its shoddy apps are the main vector for all these exploits. Why isn’t this software autoupadting by default?
Microsoft needs to release its own PDF viewer with Windows 8. Its really time to get away from Adobe. They don’t care for security and they’re dragging the whole industry down.
Not to mention, how hostile their site is to those who want to update. I can’t download the .msi’s or exe’s directly without joining some kind of affiliate program. Their updater can’t update very well. Typically it can only do one increment at a time and requires a reboot. Its just easier to download the newest version of reader and just install it.
Lastly, why does Firefox warn me about Flash being out of date but not Reader? The browser vendors need to start warning end users to upgrade Reader AND Java (webstart vulnerability). Its really time to start making some changes as the status quo is clearly not working.
“Microsoft needs to release its own PDF viewer with Windows 8. ”
LOL. Yeah, that’s exactly what we need….
I find MS does a much better job with security than Adobe. If it updates itself using Windows Update then that’s one less thing the end user needs to worry about updating.
MS has an incentive to produce secure software because insecure software makes their platform look bad. Adobe gets a free pass because when people get infected they don’t know the vector and they just blame Windows.
Are you serious about asking Microsoft for a “secure” PDF reader? Have you tried Google Docs and have it render the PDF for you?
I’m 100% serious. MS could do a much better job than Adobe. Adobe’s security record is abysmal. MS could update its reader via Windows Update so that’s one less updater the end user needs to worry about.
Hey El Krebs, you’re in the SANS diary now… http://isc.sans.edu/diary.html?storyid=9622
The latest Zeus sure sounds nasty, am glad I’ve got puppylinux running again.