Adobe Systems pushed out a critical security update for its Shockwave Player that fixes nearly a dozen security vulnerabilities. The software maker also is warning that attackers are targeting a previously unidentified security hole in its Acrobat and PDF Reader products.
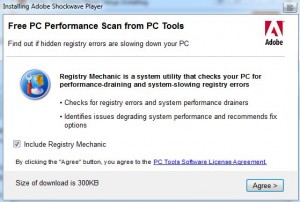 The Shockwave patch plugs 11 security holes in program, most of which attackers could use remotely to take control over an affected system. Updates are available for Mac and Windows computers, from this link. The latest version is 11.5.9.615. Before you blithely click through the process, keep a lookout for pre-checked “free” software that will install alongside this Shockwave update if you simply accept all the default options. When I tested the Shockwave installer, it included a “free PC performance scan from PC Tools’s Registry Mechanic. I opted to untick the check mark next to that option before proceeding with the rest of the install, which was otherwise uneventful.
The Shockwave patch plugs 11 security holes in program, most of which attackers could use remotely to take control over an affected system. Updates are available for Mac and Windows computers, from this link. The latest version is 11.5.9.615. Before you blithely click through the process, keep a lookout for pre-checked “free” software that will install alongside this Shockwave update if you simply accept all the default options. When I tested the Shockwave installer, it included a “free PC performance scan from PC Tools’s Registry Mechanic. I opted to untick the check mark next to that option before proceeding with the rest of the install, which was otherwise uneventful.
Due to Adobe’s huge market share and apparent abundance of as-yet-undiscovered security holes, life with Adobe’s products can feel a bit like playing Whac-a-Mole: Just when you’ve patched one Adobe product it seems like there’s another one under assault by attackers. True to form, Adobe released a separate advisory today warning that hackers were targeting a critical flaw in the latest version of its Acrobat and PDF Reader products.
Adobe says the Acrobat/Reader vulnerability could cause a crash and potentially allow an attacker to take control of the affected computer, and that there are reports that this vulnerability is being actively exploited in the wild against Adobe Reader and Acrobat 9.x. The flaw also exists in ubiquitous Adobe’s Flash Player, although the company said it is not currently aware of attacks targeting the latest version of Flash (v. 10.1.85.3).
![]() Even so, Adobe plans to fix the issue in Flash before tackling it in Reader and Acrobat. The company says it plans to issue a fix for the bug in Flash by Nov. 9, 2010, but that it doesn’t expect to release an update to clobber the problem on Acrobat/Reader until the following week.
Even so, Adobe plans to fix the issue in Flash before tackling it in Reader and Acrobat. The company says it plans to issue a fix for the bug in Flash by Nov. 9, 2010, but that it doesn’t expect to release an update to clobber the problem on Acrobat/Reader until the following week.
In other patch news, Mozilla has released an update that fixes a critical flaw that security experts warned this week was being used to attack Firefox users. Chances are good that your copy of Firefox (assuming it is semi-recent) has already downloaded this update, which brings Firefox to version 3.6.12 If you haven’t already been prompted to restart Firefox, click “Help” in the menu bar on top and look for an item that says “Apply Downloaded Update Now.” Otherwise, it’s available from Mozilla’s home page.




Brian, did you mean version 10.1.85.3 of Adobe Flash Player?I have not seen a version 10.1.86.3
Yes, thanks Steve. Fat fingered that one I guess. Fixed!
Once more unto the breach dear friends, once more. Well i think i have a hardware upgrade that should be malware proof.
http://cgi.ebay.com./25-/120631060192
I note the absence of the obligatory blurb about Shockwave Player not really being needed. I never installed it on my newest machine and I haven’t missed it at all.
Thank you, Brian. Your updates are always timely and much appreciated.
I do have one question:
Does the Shockwave fix have to be downloaded separately for each browser, or will one download take care of all browsers?
I believe I whined about this earlier but still I’m so irritated I’m going to do it again. Where the hell do those [expletive deleted] at Adobe get off trying to get paid while patching their garbage software? How could they think it’s appropriate to hoist pay-per-install toolbars and trash onto the backs of these critical updates. If Microsoft tried folding MS Office trial versions into every Black Tuesday patch they’d get dragged over the coals. The cynic in me suspects Adobe of monetizing their security flaws; depending on how many Reg Mechanic/TimesReader/Mcafee installs they get paid for, you can insinuate that the real reason they ramped up their patching program is to reel in the easy money.
Phew, okay, I’m done with my rant. Back to the topic at hand: who the hell is using Shockwave, and why the hell does it need to be a completely separate player from Flash? Especially if it’s duplicating the security problems in both applications!
At least I could uninstall Adobe’s PDF products and use comparable ones like Foxit or Sumatra. For Flash (or Shockwave too, I guess) people are just stuck.
Maybe the reason Adobe tries to make some $$ from the toolbars and other add-ins to updates, is that the products themselves are free? And there is an opt-out check box – no one is forcing you to take anything that you don’t want.
With Microsoft products, on the other hand, you have paid for their products (and updates) as part of the cost of the computer they are installed on. (And even Microsoft tries to sell upgrades to programs that come pre-installed, via annoying pop-ups reminding you that there is a “free trial” upgrade already installed on your new computer.)
And why aren’t you ranting about the annoying flashing ads that appear on this and other free websites? They bother me a lot more than an uncheck box that I see infrequently.
When I do work, I expect to get paid for it one way or another. Do you honestly believe that you are entitled to everything on the internet for “free” and without any way for the producers to profit from their efforts?
I believe everyone should be paid for their work JBV. Please take a moment to understand Adobe’s business model and I think you’ll also understand my ire.
Right now as I check Amazon, Adobe Flash Pro CS5 is on sale for only $606. That is where Adobe makes its money. They also do enterprise licensing for larger businesses no doubt, and offer the Adobe ACA certification exam (for a price). There is a whole ecosystem surrounding Flash (and all Adobe products) that provides sustained revenue.
In the case of Flash Player specifically, it isn’t an asset being given away charitably. It is Adobe’s sales tool, and everyone who installs it is participating in Adobe’s sales process. It says to the world “look at these thousands/millions/billions of people who can view Flash content, you should use it as your rich content platform”. Nothing in life is free; Flash Player is paid for by me when I install it, proclaiming to content developers (in net effect) that I approve of and desire to see Flash content, and they should pay Adobe for the development tools.
SO WHEN ADOBE F*CKS UP THEIR SOFTWARE, A SALES TOOL I GRACIOUSLY UTILIZE ON THEIR BEHALF, WITH GAPING SECURITY HOLES THAT CYBER CRIMINALS CAN USE TO TAKE OVER MY COMPUTER COMPLETELY, I EXPECT THEM TO FIX IT QUICKLY, PROPERLY, AND APOLOGETICALLY WITHOUT DROWNING ME IN CRAP I DON’T WANT WRAPPED IN GOTCHA-BOXES I HAVE TO CHECK & UNCHECK.
Of course I’m not going to complain about Flash advertising; I wouldn’t be caught dead on the web without NoScript and Flashblock. That is not because I’m trying to screw Brian out of ad revenue (furthest thing from my mind) but because of the risks associated with Flash ads. It is not uncommon for well-known ad networks to be hosting malicious Flash disguised as legit advertising.
Example:
http://www.eweek.com/c/a/Security/Attackers-Infect-Ads-With-Old-Adobe-Vulnerability-Exploit/
[EDIT]
In my haste I linked to an eweek.com article where the malicious ads used PDF exploits. Sorry, I intended to show one specifically for Flash exploits but posted hastily.
See here:
http://securitylabs.websense.com/content/Alerts/3061.aspx
@ potty-mouth Russ:
After you’re done washing your mouth out with soap, consider this:
In effect, you are blaming Adobe for not being able to predict the activities of cyber criminals, and to “FIX [flaws] QUICKLY, PROPERLY, AND APOLOGETICALLY” without your having to uncheck one box during the free update process.
Seems to me that your rage would more properly be directed at cyber criminals. They, not Adobe, are the ones who cause the problems. (Of course, the upside to their activities is that they provide a vocation for Brian and his peers. Without these malefactors, Brian, et al., would be working 9 to 5 like the rest of us.)
@JBV There is no excuse for insecure coding with the exception of negligence.
As I’ve said before, I’m surprised the browsers don’t sandbox the crap out of Adobe’s exploitware because of damage it does to their reputation.
@Russ, “…why the hell does it need to be a completely separate player from Flash”
Don’t forget there is also the “Authorware Player”, which is still included in the version checks on http://www.adobe.com/shockwave/welcome/. Can’t say I’ve heard anyone say “Authorware” in a long, long time. And of course AIR is another separate product/component/platform.
Personally I wouldn’t install any of them if I could help it, but several of my financial sites use Flash for significant interface components. And the kid’s machines have to have both Flash and Shockwave for all the cool “free” games they like to play…
This is my obligatory comment on running Firefox as a limited user. No, you don’t even need to run as a limited user yourself, just setup an account and use runas or the GUI to start FF as that limited user. Seems like most users could handle that especially ones that need local admin for games, legacy apps, etc.
Brian, I feel so much safer since I have been reading and following your professional safety and security tips and have learned so much in the process! Staying ahead of the bad guys seems to become more and more difficult as technology advances. A big thank you to you for being so knowledgeable in your field and for sharing part of that knowledge with us!
Thanks, Dirgster. I’m glad you find the content here useful. Welcome.
Brian, you don’t need to go to Mozilla site for a Firefox update – even if the update wasn’t downloaded yet, there is “Check for Updates” in the Help menu. If there is an update it will download the incremental update – which is usually significantly smaller than the full download package.
Whilst I admire Adobe’s chutzpah to ship embarrassingly weak software and then use security updates as a selling opportunity… I don’t think it does them any good in the long term.
Brian, in addition to timely and important security posting, you do most of the digital work when you provide screen-shots and links to sites that are involved in security updates or additional information. My brain and fingers are most appreciative.
Maybe I missed something, but when I try to run Firefox as a limited user, No-Script and Ad-block will not run. What am I missing?
“Will not run” or “are not there”? Unfortunately, Firefox add-ons generally have to be installed on a user-by-user basis. If you set up FF in your regular account and then run it from a different, limited account, your regular add-ons won’t be installed. You’ll have to add them again under the limited account.
The mitigation for Adobe Reader is clear, it’s in the Adobe advisory (rename or delete “authplay.dll”; typically it can be found in C:\Program Files\Adobe\Reader 9.0\Reader\). PDFs with Flash should crash, but not cause any problems.
But the mitigation for the web-based Flash Player is not mentioned. A few solutions, none ideal, assuming Firefox on Windows:
1. Wait for the update, about two weeks.
2. Uninstall Flash.
3. Run as a limited user with a new profile.
4. Use the NoScript extension, with scripts globally not allowed. Then in Options/Embeddings/untrusted check “Forbid Adobe Flash”. But without scripts, most web sites will not fail in one way or another. You can enable trusted sites one-by-one.
5. Use NoScript, with script globally allowed. Install a 4th party filter supported by NoScript called Blitzableiter. In NoScript’s Advanced Options, check “Blitzableiter” and specify its location. Blitzableiter will parse every Flash file except on Hulu and Youtube for coding errors. Why exclude Hulu and Youtube? Because their files have errors as do many on the web. The Blitzableiter parsing is *slow* and itself causes strange errors such as once sending a file to the printer! When it works correctly, it shows you the error message, and you can override and allow the file. Certainly not ideal.
Note: *Flashblock* reportedly will not prevent all attacks, because the files may not initially be marked as Flash. Reportedly, Flashblock misses these and Blitzableiter catches them.
Really an intolerable situation presented by Adobe.
I have not looked, but I am assuming there is no alternative to Adobe Flash?
I actually used Foxit for PDF once until I noticed it dropped an unusual icon on my desktop. It was a shortcut URL to ebay? I ran the it through Anubis and Anubis found many problems with the page, including modifications to the registry. So that was the end of my Foxit experiment. So now, I will just use a PDF reader when I need it and then uninstall it.
Shockwave and Flash are actually different technologies, kind of like Java and Javascript. (It’s a common mistake due to their previous naming schemes.)
Since you don’t know the difference (I didn’t either until today!), there’s a pretty good chance you don’t even use Shockwave. And if that’s the case it should be deleted.
http://en.wikipedia.org/wiki/Adobe_Shockwave
The vulnerabilities are in both products, as well as Acrobat Reader, via Flash. Confusingly, “Flash” was once called “Shockwave Flash”.
Another workaround is to run two browsers, one Firefox or Seamonkey locked down with maximum NoScript and Flashblock, and the other Opera, or Chrome, etc., plus of course IE. Firefox has plugins for putting little icons in the menu bar to open the current page in a different browser. (“Opera View”, “IE View”.)