Crooks who create botnets with the help of crimeware kits SpyEye and ZeuS are actively venting their frustration with two Web services that help ISPs and companies block infected machines from communicating with control networks run by these botmasters. The lengths to which established cyber criminals are willing to go to disable and discredit these anti-fraud services provide convincing proof that the services are working as designed, and that the bad guys are suffering financially as a result.
The creations of Swiss security expert Roman Hüssy,  ZeusTracker and its sister service SpyEye Tracker have endured countless distributed denial-of-service (DDoS) attacks from botmasters apparently retaliating for having their network infrastructure listed by these services. At one point, someone wrote a fake suicide in Hüssy’s name and distributed it to his family and friends, prompting local police to rouse him from slumber to investigate his well-being. But, those attacks haven’t deterred Hüssy or sidelined his services.
ZeusTracker and its sister service SpyEye Tracker have endured countless distributed denial-of-service (DDoS) attacks from botmasters apparently retaliating for having their network infrastructure listed by these services. At one point, someone wrote a fake suicide in Hüssy’s name and distributed it to his family and friends, prompting local police to rouse him from slumber to investigate his well-being. But, those attacks haven’t deterred Hüssy or sidelined his services.
Now, the attackers are beginning to consider stealthier and more diabolical ways to strike back. A series of discussions on an uber-exclusive Russian language forum that caters to identity and credit card thieves reveal that botmasters are becoming impatient in their search for a solution that puts Hüssy and/or his tracking services out of commission once and for all (click the images in this post twice to read along).
“DDoSing doesn’t bring satisfactory results. We’re now working on mapping his entire infrastructure, flag his scripts,” writes a user named Sal, who claims to specialize in providing bulletproof servers. “Now we will engage in a pinpointed assault. This should be cheaper + should bring results at least temporarily….Let’s brainstorm here.”
 Other members join the discussion. One suggests pooling funds to hire a hitman. “It’s easier and more productive to just use a joint fund to hire a killer, and story’s over,” writes user “Femar.” Another forum member named “Deviant” recommends dosing Hüssy with organic mercury. “Dimethylmercury – the fluid has no color. One drop on your hand will penetrate thick latex gloves. Lethal result is guaranteed within one month.”
Other members join the discussion. One suggests pooling funds to hire a hitman. “It’s easier and more productive to just use a joint fund to hire a killer, and story’s over,” writes user “Femar.” Another forum member named “Deviant” recommends dosing Hüssy with organic mercury. “Dimethylmercury – the fluid has no color. One drop on your hand will penetrate thick latex gloves. Lethal result is guaranteed within one month.”
But forum members seemed to coalesce around an idea for seeding the ZeuS and SpyEye configuration files (those that list the location of key parts of the botnet, such as the place to deposit stolen data) with legitimate Web sites. Their stated goal? To cause SpyEye Tracker and ZeuS Tracker to flag legitimate sites as hostile, and thereby to lose credibility with ISPs that rely on the trackers.
I caught up with Hüssy via instant message yesterday, and asked whether he’d seen any SpyEye or ZeuS configuration files seeded with legitimate sites. He just laughed.
“ZeusTracker checks if a command and control server is really up before adding it to the blocklist,” Hüssy said. “These guys have no clue how ZeusTracker works.”
Toward the end of February, a user named “Hobo” from the criminal forum refreshed the discussion about taking on Hüssy’s creations, observing that “A month has passed and the tracker is alive and kicking, more than ever.”
 Sal responds by acknowledging that the blacklist plan didn’t seem to pan out. “Hobo, it’s too expensive to shut down. I was the only one with the initiative. It would be cheaper to resolve the problems in the way our system works. Nevertheless, this was not a useless effort. I understood what I needed from [ZeusTracker] work methods, filtered away a lot of bots, and made Roman Hussy pay exactly what he cost me. Made myself and my clients safe. Still, we’re interested in actively working against the tracker, but I need people that share my ideas, as I don’t have a lot of time to spend on this. Me and my employees don’t have the time to make ALL the ideas we accumulated here work. And I’ll say this now — I don’t need the money. I need participation.”
Sal responds by acknowledging that the blacklist plan didn’t seem to pan out. “Hobo, it’s too expensive to shut down. I was the only one with the initiative. It would be cheaper to resolve the problems in the way our system works. Nevertheless, this was not a useless effort. I understood what I needed from [ZeusTracker] work methods, filtered away a lot of bots, and made Roman Hussy pay exactly what he cost me. Made myself and my clients safe. Still, we’re interested in actively working against the tracker, but I need people that share my ideas, as I don’t have a lot of time to spend on this. Me and my employees don’t have the time to make ALL the ideas we accumulated here work. And I’ll say this now — I don’t need the money. I need participation.”
Sal closes by wryly noting that having ZeusTracker and SpyEyeTracker around isn’t all bad, because it tends to do a good job of killing off botnets run by novice hackers who don’t know to watch out for the services.
“P.S. – this is directed to people that do hosting around here, if you learned to fight the tracker, having it around is pretty valuable since all the newbies and users of publicly available trojan versions go down quickly with it, but my altruism will die last!”
It appears that the latest salvo against Hüssy’s projects comes straight from the author of SpyEye himself: According to a blog post from RSA FraudAction Research Lab, the latest version of SpyEye ships with a plugin that is configured to attack the SpyEye Tracker domain that is dedicated to tracking SpyEye command and control servers. From that post:
“It is worth noting that more recent versions of SpyEye support the inclusion of separate modules, in the form of distinct DLLs. The Trojan’s builder is even sold with a Software Development Kit (SDK), to facilitate the development of new modules by individual botmasters. This enables cybercriminals to independently author various plug-ins, like the DDoS plug-in we traced, and include them in their own SpyEye variants.”
RSA said it also found a variant of SpyEye that employs the bogus configuration file listings discussed in the fraudster forum.
“The FraudAction Research Lab recently uncovered this exact kind of contaminated configuration in a variant of SpyEye 1.3.10 (the latest SpyEye version seen to date). In addition to genuine SpyEye drop points — collectors.txt — the file used to configure the Trojan’s drop points, was found to contain legitimate domains, such as google.com, myspace.com, and vkontakte.ru (a popular Russian social network).”
It’s not often we get such a ground-level detail on how the criminals view the effectiveness of the countermeasures deployed against them. But it is clear from these and other threads on this forum that the botmasters will continue devising new methods of disabling the trackers. As Sal puts it, herding bots is a living, not a hobby.
“I’m not doing this as my hobby,” he wrote. “You think I’m afraid of anything? I have no time to be afraid. I’m working.”
Update, 9:54 a.m. ET: An entity that provides DNS services to ZeuSTracker and SpyEye Tracker sent me the following data showing recent traffic spikes from DDoS attacks.



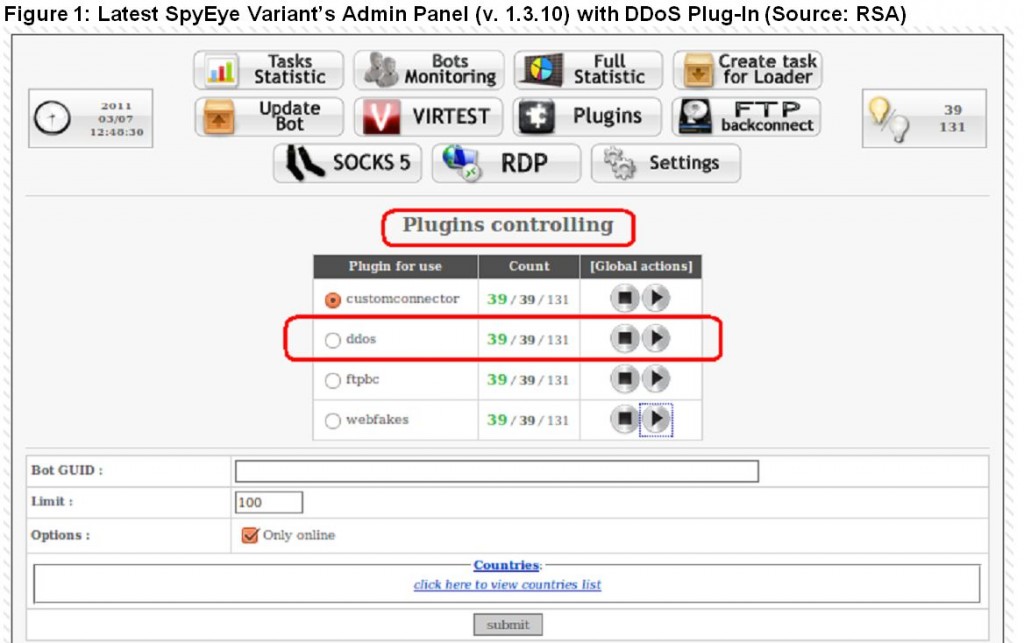
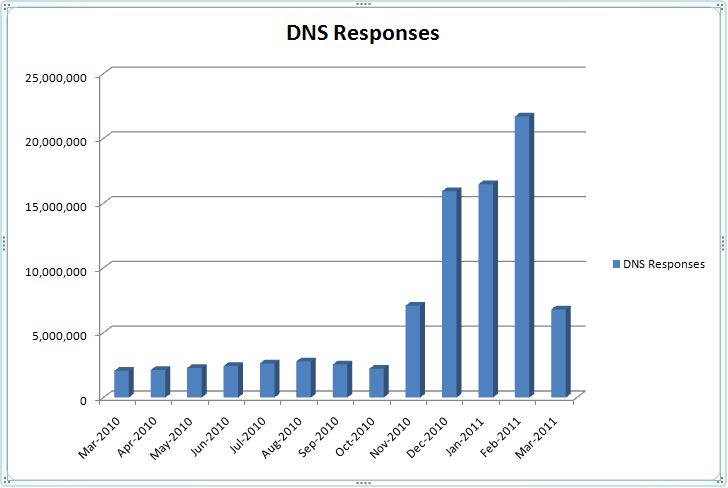

Ouch:
“Dancho Danchev sucked it and he will eventually suck it too.”
I’ve received a few questions from people who are having trouble viewing the thread images. To view them full size, you’ll need to click them twice: Once to bring them up on their own page, and again to enlarge them.
I just right click and open in new tab, then zoom in.
I am not moved by their problems.Like George Carlin said, “Crap in Crap out”.You get out of life what you put in.Karma has a nasty way of being a boomerang.
So the bad fellows are upset.
I’m really hurting for them. They deploy tons of grief and destroy lives of innocent folk and they brag about their trail of tears.
Maybe they play for the Miami Heat ?
[img]http://img683.imageshack.us/img683/9549/krabs.jpg[img]
krabs on security, use this logo, better than old
What is most interesting to me is how the situation is asymetrtical in scope. A handful of jerks like this mess with millions of normal people.
It occurs to me that all the spam and bot problems would go away if Russia was “accidentally” disconnected from the internet.
Question:
What you could say to “security expert” if you will meet him after disconnecting China and Russia from internet?
Answer:
One cheeseburger, please.
Speaking of Dancho, Brian, have you heard anything recently? Last I heard were some conflicting reports of him being hospitalized in Europe.
Well, I never wrote about that whole episode, even though I knew about it early, so I didn’t feel the need to update readers on his status. Dancho is back at work, blogging and tweeting. You can find his stuff in the usual places.
Thank you for that– I hadn’t thought to look him up recently until your article.
Nice job, Brian. I’m trying to catalog a Zeus/SpyEye attribute report card and your posts are most helpful. Again, thanks.
Everytime I read articles about fraud-forums like these I’m wondering, why they can still host in countries like NL for such a long time.
Well, there’re certs and unusual http-ports, but black sheeps and “traitors” should be everywhere…
Excellent post! Slight corrections in translation:
1. When Sal writes “У меня на данный момент у админов “проблема с человеко-часами” he’s not talking about admin panels but rather about sysadmins -his employees or cohorts. The meaning here is “My admins are currently too busy to work on this” (“проблема с человеко-часами” means “a problem with man-hours”)
2. When he writes “P.S. К слову, лично для нас (хостеров), кто научился бороться с трэкером, весьма выгодно его существование. Т.к. почти все пионеры с подполья и паблика всасывают =)” he says smth like “P.S. Personally, for those of us (hosters) who found a way to fight the tracker , its (tracker’s) existence is pretty valuable since all newbies from underground and public (forums) understand and act accordingly”.
I’m not 100% sure about what exactly he meant by “всасывают”. In this context it must be a slang word for “understand and act accordingly”, i.e. buy his services. I think his business is bulletproof hosting and he means that since he is successful in not being listed by ZT he has more customers as opposed to other bulletproof hosters.
“всасывают” means “sucks” in meaning they will be banned or noticed by trackers
According to a dictionary of post-Soviet Russian I have всасывают means”to savvy” or “to be versed in the army way of doing things or to understand army lingo”
I’m rather surprised they would even talk about hiring a hit man. Currently, internet bank robbery is a rather low risk crime. Arranging a hit is an entirely different type of crime and much higher risk.
Oops. There’s a reply further down the page.
“Other members join the discussion. One suggests pooling funds to hire a hitman.” – I was at the gateway lounge at the airport a few years back checking emails when one of my associates exclaimed that there was another Nigerian spam letter in his inbox. A tall, dark African looking stranger sitting on the other side of the lounge leaned over and asked if it was a real problem. After a short discussion, he offered the services of a hitman to eliminate the problem, for just two hundred dollars. I must confess I did check in my pocket and had the correct change, but it never went any further.
Rather than spending countless of man-hours, setting up a sophisticated anti-malware trapping environment, nad waging an online war with ever changing filters, if a few people chipped in a hundred bucks each to ‘eliminate’ the problem at the source, wouldn’t it be a more efficient solution?
It *is* getting rather personal when you have to watch over your should in the street, and not just online.
Then I woke up… 🙂
I was at the gateway lounge at the airport a few years back checking emails when one of my associates exclaimed that there was another Nigerian spam letter in his inbox. A tall, dark African looking stranger sitting on the other side of the lounge leaned over and asked if it was a real problem. After a short discussion, he offered the services of a hitman to eliminate the problem, for just two hundred dollars.
Maybe this tall ,dark African looking “DUDE” was the person that sent the e-mail . Most likely he was hacked by him and then would of been out $200.00 if hired, for services not rendered . By the way for $200.00 bucks I wonder if he had a real gun , just my thoughts .
50 мемберов по 500 баксов и проблема с трекером решена. не на долго но на год два можно забыть.
еще раз по 500 и про кребса тоже можно будет забыть. в общем надо сделать приватный раздел на мф и там скординировать наем киллера, потому что уже заебывать начинает.
50 мемберов по 500 баксов и проблема с трекером решена. не на долго но на год два можно забыть.
еще раз по 500 и про кребса тоже можно будет забыть. в общем надо сделать приватный раздел на мф и там скординировать наем киллера, потому что уже заебывать начинает.
it means in english: 50 members with 500 usd each (50*500=25000 usd) and problem with tracker will be resolved. not at long time but on 1 or 2 years we can forget about tracker, and again 500 usd from 50 members ( 25000 usd total) and we can forget about Krebs too. so we ( russian botmasters) must do private subforum on mf ( some botmasters’ forum) and coordinate the hiring of killer, because they ( Krebs and tracker) fuck our ass with their tryings to fight with botnets
i think this criminal russians can only talk and hide their asses
“mf” = mazafaka
Well well Well Brian vs Rest of the World …
Brian D Krebs
Age 39
Minneapolis, MN
Barnesville, MN
Lake Elmo, MN
Moorhead, MN
Relatives
Svenja K Krebs
Steve T Krebs
Carrie A Krebs
DOB ——-check
Phone ——- check
Address —– check
Avg. Income —–check
Avg. Home Value —– check
da 500 $ mnogo budet mi evo i za 200 $ zdelaem ..
zavtro posimaem emu POLONIUM 210. v pisme na xatu i vse gotov zai4ik …u menja eshe gde to ostalos
He now lives in Alabama. i got the address too .
Long live the BRIAN . NOT
The hitman claim is entirely posturing. They will just keep innovating ways around the trackers and defenses, while griping about defenders’ successes. I disagree with another poster about it being a much more serious crime: a Russian guy who kills someone, goes back to Russia, and pays off the right people is safer than the average American thief.
I mean, does anyone really think Russian police couldn’t track more of these guys when they do so much right out in the open?
I mean, does anyone really think Russian police couldn’t track more of these guys when they do so much right out in the open?
why? Why blame russian crooks if some american crackhead will break brian’s or tracker’s autors head?
What I don’t get is why they have not out evolved the tracker.
It is usual for the smarter criminal to out manoeuvre LEO’s and others and stay ahead of the game. It is those that don’t evolve (most of the ones Brian has shown here) that get squished. Often LEO’s wait untill their nuisance value rises to the point where the LEO’s see value in devoting resources to the problem. Then focus the spot light and round up the bugs running for cover while sqquishing those actually caught in the light.
I suspect that what we see are efectivly the bot hearders that are not evolving and the question is “why” are they two busy or to ignorant, my money is on the latter for most of them.
Look at it another way if they had smarts they would have made their own Zeus etc.
Also evading such trackers is an already solved problem if the bot hearders just bother to sit down and apply a few grey cells.
The www connects w/ the tangible world. In Mother Russia’s version of the tangible, gangsters w/ guns are very important. If you google Peter Gutmann’s paper, “The Commercial Malware Industry,” pg 5 gives a very brief, very credible outline of the “technique” used by Russian organized crime to control malware.
Brian, do you know that your surname sounds pretty similar to the Russian slang word “krab”?
Folks, I am really surprised that all of you trust that double agent!
The ZeuS users speak about murder openly because they know they’ll never do it, the same way people are doing in the comments here. And they threaten people’s relatives because they know Brian and Roman both understand they’re taking more personal risk driving their cars on expressways than by exposing the cowards who populate that forum.
AlphaC,
As you say talking about murder is easy, however it shows up another aspect of the Bot-hearders basic make up.
Ask yourself a simple question what sort of person talks of doing something like this?
Two main types, those who are effectivly impotent and are living “Walter Mitty” life styles, and those who wish to push their buttons.
However there can be a problem with pushing an idiots buttons. You see it in Bars all the time, it is sometimes they do strike out al be it clumsily and in rage.
Unfortunatly as we know the Russians both Political and criminal are not averse to sending out “hit men” occasionally. Putin pushed through laws to make state sanctiond murder of individuals in other states legal.
However I suspect that for all their nuisance value the Bot-herders are not sufficiently connected with the Russian criminal or political organisations to have the sort of connections required.
However looking at what they (allegedly) said does throw external light on their existance which may help in the removal of the nuisance.
What sort of person talks about murdering people in creatively evil ways? Most of us do at times, if we’re sure no one will take us seriously. There are even a couple posts here calling for the “good guys” to preemptively hire hit men to go get these guys. But I don’t think any of the people posting those comments are taking up a collection to actually do it.
The ZeuS guys might be posting their murderous suggestions kind of hoping someone else will take up the idea and run with it. But if Roman or Brian actually showed up dead with mercury poisoning, how certain could they be that their post would not incriminate them? How certain could they be that no one in the forum is a mole, that the domain host won’t turn over the database to law enforcement, that the person suggesting the murder isn’t a law enforcement officer from a country where entrapment is permitted, that the proxy they are using isn’t a honeypot recording their IP addresses, etc? I think if they were actually serious, at the very least they would have taken the discussion off forum before they started getting into any specifics.
I mean, we might be seeing a murder being planned by The Gang That Couldn’t Shoot Straight and seeing them make all kinds of mistakes, but such carelessness would not be expected of someone who is accustomed to hiring hit men.
That being said, has anyone checked Dancho Danchev’s hair for heavy metals?
Well seems like after the good old Chronopay article Brian has ruffled a few feathers…lol… Well vermin usually don’t like being exposed! I said this before and I will say it again there’s always been one constant problem and that’s the refusal of some hosts/ASNs/registrars, to do their job and that’s enforce their AUP/ToS and take action against those who constanatly abuse the system. There is far too many devious entity’s out there that blatantly ignore abuse in their midst for the almighty dollar, but until ICANN/hosts/registars/ASNs work together to combat this we are in for a long long fight..
That points out another reason that at least at present, they eat their losses rather than taking dramatic action. They make money from their trojan infections only because there are more clueless potential victims than there are readers of this blog.
Once educated, the clueless move permanently out of the pool of easy targets. Something like a murder, that could make headlines outside of the tech media, would have a bigger impact on their income in the long run.
A11a-T020 TITLE: Automated malware understanding and classification
TECHNOLOGY AREAS: Information Systems
The technology within this topic is restricted under the International Traffic in Arms Regulation (ITAR), which controls the export and import of defense-related material and services. Offerors must disclose any proposed use of foreign nationals, their country of origin, and what tasks each would accomplish in the statement of work in accordance with section 3.5.b.(7) of the solicitation.
OBJECTIVE: Automated techniques for understanding and classifying behavior of novel malware.
DESCRIPTION: The number of new malware being encountered in the wild is steadily and rapidly increasing. Recent reports show that more than 5,000 new, unique malware samples are encountered daily. In order to keep pace and not fall behind in the arms race with malware creators, there is a dire need for a systematic, automated way to process this deluge of malware. When a malware is encountered, there are two questions that need to be answered: (i) what does the malware do? (ii) is the malware a variant of an already known malware? Automated and effective techniques combining static and dynamic analysis of executables, mining techniques for behaviors, and malware classification are needed to address this challenging problem. The same technique may also help understand behavior of COTS from untrusted and unknown sources.
Researchers are exploring new techniques that can address these questions, such as the recent work on automated construction of dependence graphs from executions of malware for understanding and summarizing the behavior of the malware. Researchers have also studied mining tools and techniques based on dependence graphs to extract the behavior of malware. Semi-automated specification generation techniques have been explored to help analysts construct detection mechanisms for newly discovered malware behaviors for incorporating them into behavior-based or cloud-based malware detectors. Some researchers (such as Bailey et al. 2007) have addressed the malware classification problem: classifying malware by type (e.g., Virus, Worm, Spyware), family (e.g., Bagle, Netsky, MyDoom), and whether it has been encountered before.
The current practice of analysts manually inspecting each individual incoming malware is not a sustainable solution. There is a need for proven and deployable automated techniques that can process and analyze large volumes of malware binaries.
PHASE I: 1) Research and develop automated malware understanding and classification technologies based on recent new techniques such as dependence graphs or symbolic execution that can effectively and efficiently analyze and characterize malware behavior and to defeat the use of obfuscation and polymorphism. 2) Demonstrate that the proposed techniques can be implemented successfully in classifying behaviors for a large corpus of malware in near real-time.
PHASE II: 1) Extend the techniques proposed in phase I to mine or extract relevant behaviors of malware. 2) Develop and implement techniques for automatically transforming the extracted malware pattern and behaviors into policies or patterns that can be ported into existing malware detectors. 3) Validate the techniques under operational conditions. The goal of this phase will be to demonstrate that a new malware can be analyzed near real-time. The goal will be to analyze, classify, and mine behaviors in less than five minutes with minimum human intervention.
PHASE III DUAL USE APPLICATIONS: Effective techniques for understanding and classifying malware are critical for both military and commercial sectors. The developed system will be marketed as a malware-analysis platform which will be attractive to malware-detection companies and defense agencies. The malware-analysis platform can be used by agencies and companies for developing a faster defense against zero-day attacks.
REFERENCES:
[1] B. Acohido and J. Swartz. Zero Day Threat: The Shocking Truth of How Banks and Credit Bureaus Help Cyber Crooks Steal Your Money and Identity. Union Square Press, April 2008.
[2] Michael Bailey, Jon Oberheide, Jon Andersen, Z. Morley Mao, Farnam Jahanian, and Jose Nazario, Automated Classification and Analysis of Internet Malware, Proceedings of Recent Advances in Intrusion Detection (RAID’07), September 2007.
[3] Mihai Christodorescu, Somesh Jha, and Christopher Kruegel, Mining specifications of malicious behavior, ESEC/SIGSOFT FSE, 2007.
[4] Matt Fredrikson, Mihai Christodorescu, Somesh Jha, Reiner Sailer, and Xifeng Yan, Synthesizing Near-Optimal Malware Specifications from Suspicious Behaviors IEEE Symposium on Security and Privacy, 2010.
[5] Lorenzo Martignoni, Elizabeth Stinson, Matt Fredrikson, Somesh Jha, John C. Mitchell, A Layered Architecture for Detecting Malicious Behaviors, RAID 2008.
[6] Mila Dalla Preda, Mihai Christodorescu, Somesh Jha, Saumya K. Debray, A semantics-based approach to malware detection, ACM Trans. Program. Lang. Syst., 30(5), 2008
[7] David Brumley, Hao Wang, Somesh Jha, Dawn Xiaodong Song, Creating Vulnerability Signatures Using Weakest Preconditions, CSF, 2007:
[8] Hao Wang, Somesh Jha, Vinod Ganapathy, NetSpy: Automatic Generation of Spyware Signatures for NIDS, ACSAC, 2006.
That sounds neat, but it’s reactive. The real problem is that malware works so easily in the first place. That’s the problem they need to fix. For example, why are stack overflows still possible when there are OS’s that use reverse stacks to prevent this? Ancient Multics and modern day OS’s like SourceT and that which powers Hydra firewall can’t be overrun by malware. Additionally, what’s up with all of this spaghetti code that Microsoft calls API’s?
Want a solution to much of the malware problem? Here you go. US Government declares minimum architectural and quality requirements for code and hardware they will be using. Pervasive, irreplaceable code like Microsoft’s receives a subsidy whereby the government pays them to re-engineer their software to meet new standards. Intel is paid to produce a new x86 architecture without serious errata, minus the legacy BS, and with necessary security features. Software vendors that produce the government’s software are required to modularize and clean up their software for easy porting should the government change platforms again. Everyone pushing Windows software makes any required improvements, recompiles and suddenly many system-level attacks don’t work anymore. *That* problem would be solved.
Alternative: Try to build software and algorithms that can distinguish good and evil program behavior, predict the program’s master plan, and restrict only evil programs in just the right way to prevent them from breaking arbitrary security policies. This is the current strategy. It hasn’t worked. It never will. Must fix the root of the problem, like vendors above did, for mainstream desktop and server platforms.
@ Nick P,
Whilst I agree you have identified one valid way to go, it is not without it’s problems.
My personal belief is the first positive step Microsoft could make is to drop legacy support for various early platform issues (do you realy need to be able to run MS Office 4.3c on the latest OS version for instance).
Another are MS could improve things is dump the registry in it’s current form. It should be “human readable” at the disk level and without any (all be it weak) cryptography.
These two things alone make a massive rod for MS’s back for little reason and could be cleaned up and removed.
However one aspect of “legacy support” is MS’s and it is as you note the spaghetti API’s.
There have been various arguments over the years as to why ranging from “getting a quart in a pint pot”, “sloppy coding practice” through to establishing an illegal monopoly. All of which have a degree of evidence to support the accusations.
However MS are probably coming around to the idea that their monolithic OS in it’s current form is fairly near it’s “end of shelf life”. Which might account for the recent spat between it and the likes of Motorola over licencing pushing in the direction of an attack against android.
MS realy saw the bottom drop out of their Win CE market when HTC and other phone manufactures went Android.
The simple fact is hand held portable devices now have more CPU power than desktops in use at the end of the last Millennium, and this trend will continue, possibly at the expense of desktop machines and the Mainline MS OS’s.
You also need to concider that some other OS manufactures have not done so well out of “open sourcing” such as Sun Microsystems. Unlike Oracal that went a different route Sun Microsystems got it wrong and got “eaten” as a self defence measure.
Man i wanna talk with u. Msg me. It’s will be interesting for u. Can we make more private conversation.
dude, try sending me an email with your real contact details already. krebsonsecurity at gmail dot com
First, the hurried post with broken English. Then, he says “I need this.” Do you have many crazed fans or stalkers, Krebs? The man obviously has problems is all I can say for sure.
You never know, Nick, but I wouldn’t use “broken English” as a criterion for labeling someone “crazed”.
A desperate non native English speaker once begged an astronomer in broken English to perform an experiment for him during a solar eclipse to prove that gravity bends space. He was anything but crazed!
Good point. To be fair though, I didn’t say he was crazed/creepy because of broken English. It was the wording, especially the extra “I need this” that inspired my post.
I need this.
Wait, I cannot fathom it being so straigfthorward.