A new resource for spotlighting organizations that are unwittingly contributing to the global spam problem aims to shame junk email havens into taking more aggressive security measures.
SpamRankings.net is a project launched by the Center for Research in Electronic Commerce at the University of Texas at Austin. Its goal is to identify and call attention to organizations with networks that have been infiltrated by spammers.
Andrew Whinston, the center’s director, said the group initially is focusing on health care providers that appear to be infected with spam bots. “Nobody wants to do business with a bank or hospital or Internet hosting company that has been hijacked by spammers,” Whinston said. “It’s an environment in which user data can be stolen or compromised.”
It’s not clear whether people pay attention to spam rankings when choosing providers, but it’s nice that another method of measuring badness and reputation on the Web has come online. Unfortunately, one doesn’t have to look very hard to find spambot infections at many health care providers. In April, I wrote about a service that lets crooks proxy their communications through hacked PCs (see: Is Your Computer Listed for Rent?): Within a few hours of poking around that service, I found three health care providers that were hosting spambots.
John Quarterman, senior researcher for Spamrankings.net and chief executive of network monitoring service Internetperils.com, said future versions of the project will focus on organizations in other industry verticals, such as banking and Web hosting.
The data come from the Composite Block List (CBL), which tracks Internet addresses that have been seen sending spam. The CBL contains a massive amount of information, but it doesn’t publish the data directly. What’s more, it isn’t terribly easy from looking at the CBL data to tell which organizations have spambot problems. Getting to that level of detail involves correlating obscure autonomous system numbers (ASNs) to network owners, and then drilling down to see which organizations are responsible for smaller subsets of Internet address space. Spamrankings said it got help with that translation process from Team Cyrmu, an organization that tracks cyber crime activity.
“Everybody knows there’s a lot of spam out there, but hardly anybody knows where it’s coming from,” Quarterman said. “Which is a little weird because the data is in the CBL but nobody has been pulling it out and tying it to individual organizations on a regular basis.”
Quarterman said he hopes that the data from spamrankings.net will be syndicated, perhaps via widgets built to republish the data on blogs or Facebook pages. In addition to highlighting sources of spam, the project plans to call attention to organizations that quickly respond to spambot problems.
“We’re not going to just wait for these organizations to contact us,” Quarterman said. “We’re going to try talking to them to find out what they’re doing about it, and hopefully we can share some of that, too.”
The data now on spamrankings.net is from April, but the project is preparing to publish its May numbers. Those stats show that some organizations listed in the April rankings have made dramatic improvements, and a few appear to have cleaned up their spambot problem entirely. Others seem to have had mixed results.
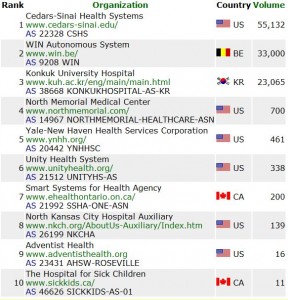
“Some organizations succeeded in bringing their spam to zero,” Quarterman said. “But the leader on the April list — Cedar Sinai Health Systems — managed to keep their spam volumes low for a few weeks in May, but by the end of the month they’d surged back into the number one spot.”
I applaud this effort, and hope that it gains traction. I remain convinced that the Internet community would benefit from a more comprehensive and centralized approach to measuring badness on the Web. There are many existing efforts to measure reputation and to quantify badness online, but most of those projects seek to enumerate very specific threats (such spam or hacked Web sites) and measure the problem from a limited vantage point. What is lacking is an organization that attempts to collate data collected by these disparate efforts and to publish that information in near real-time.




Despite HIPAA and SOX audits we used to do nothing does more damage to IT security than a profit driven hospital manager or director.
Its hard enough to get medical bureaucrats to fire outright dangerous doctors and nurses and other staff let alone care about solid internal IT security.
If most corp medicine types let poorly performing medical staff’s contract expire and then blackball the guy; then what kind of decisions would they do for IT?
What the real tragedy is, is that consumers don’t realize if someone got enough privilege to spam; they ought to ask if their medical care has been compromised: records, history, prescriptions, could be tainted, tampered, lost or stolen.
Secondly no mention of how such fraud impacts the cost of medical care — which always goes up now. How many vials of X have been ordered then “lost” in receiving and just covered over by deleting the transaction?
Really its only the exchange of money holding the US medical care system together not ideals and morals for “quality of life,” because those are just marketing to get your dollars.
Looks like Cedar Sinai sent a C&D letter pretty quickly.
Fifty-five thousand looks like an infection. But only eleven seems like a mistake.
How confident are they about the quality of the data?
Looks like the multiplier for the volume column got cut out of the screen shot – could be thousands or even millions.
I have two greenhorn questions and apologize if they were addressed:
In light of HIPAA regulations, wouldn’t health care providers be a little more responsive in getting their names off and keeping them off a list like this?
What is it about health care providers that makes them such a hot item? What I mean is, what could be their flaw or vulnerability that other organizations don’t have?
From my experience working as a Helpdesk Manager in healthcare previously, I can tell you that the healthcare industry seems to have a dangerous combination: employees that must use computers to do their jobs but do not have the skills to understand what they are doing, and some users who are too smart for their own good.
Meaning, nurses and front line staff that have access to computers and (some times) complex systems; that will click on shiny buttons.
Meaning, doctors who will not listen to anything you or any policies says; that will click on shiny buttons.
And, dare I say it, underpaid IT staff (usually equals poorly skilled and unmotivated), and management that is unwilling to spend money on their IS. 😀
Some other professions, like law enforcement for example, also have the type of arrogance of the profession, where they do not recognize as equals the people in other professions, and thus will never accept their guidance.
The medical equipment, that keeps people alive, has lovely buttons. Do they get messed with by people who have no training in that equipment?
Maureen, I don’t know that medical institutions are especially more vulnerable than other organizations: ISPs send far more spam (see the world or U.S. rankings for all organizations). However, some medical organizations do send noticeable amounts, and any is more than the desired amount.
Rankings for the month of May are now visible on the site: http://www.spamrankings.net.
We’re all ears for input.
-jsq
Mr. Quarterman, thanks for taking the time to answer. I did go out to the website and clicked on All in the categories, and finally saw what should have been obvious to me. Great website, and I appreciate the light you are shining on organizations not responsible enough to monitor and repair their contribution to the problem. It would be great if everyone with a site of their own would help spread the word.
A good concept and a worthy initiative.
I find the quote “Nobody wants to do business with a bank or hospital or Internet hosting company that has been hijacked by spammers,” hard to swallow.
In fact I’ll turn it around and say that just about nobody in the United States makes business decisions, or purchasing decisions, based on the suppliers unwilling role in spam, botnets or anything else like that. A hi-jacked spam sending HR computer in a hospital doesn’t affect patient care, AFAIK.
The only thing that gets people’s attention is the risk of “catching” malware and spyware. That’s a risk almost every user understands these days. Thankfully.
It’s been mentioned elsewhere in the comments, but: the issue isn’t “Spam? Who cares?” it’s “the hospital’s computers have been compromised.” Their “unwilling role” in spam doesn’t just mean they are innocent victims of a trivial inconvenience. I feel it’s wishful thinking to decide the spam-bot must just be on some insignificant computer that wasn’t worth protecting but the computers that matter to ME are locked down like Fort Knox.
Spam does not affect patient care. Compromised computers can affect patient privacy, cost, and care.
No, consumers don’t tend to make decisions based on these sort of indicators, especially when they’re hurt or sick. Children aren’t born knowing to look both ways before chasing a ball into the street, either. They have to learn.
So —- I’m hanging out in the waiting room of my local urgent care, hoping that one of the next calls is for me so I can get my leg sewn up & get back to mowing my lawn, when I notice that the highly regarded medical complex that I frequent offers free WiFi.
Cool. I can jump on to the free WiFi, offer up trivial information (my name) and continue my random postings to social media.
Can I also send SPAM? Probably.
Will my spam be sourced from a medical center IP address? Probably.
The obvious question – how much of this badness is coming from the guest wireless and how much is coming from staff/medical networks?
I’d love to know.
I was thinking the same thing. While I know there are plenty of medical systems with compromised PCs, patients and visitors (and people parked nearby) having access to insecure wifi may explain the extreme numbers at Cedars Sinai. Do they have separate IP ranges for their patient wifi vs. their staff internet access? Other hospitals with the same problem may simply outsource their patient internet access to a private firm, so the traffic isn’t attributed to the hospital.
I’ve used medical facilities that either had a decent wifi hotspot or a lame ask the receptionist the the phrase and your on the same network as their office printers and reception machines. There is not much middle ground.
Outbound throttling raw smtp traffic with firewall rules in a walled garden should be standard out of the box. Chillispot, Hotspot, etc and other still have a bit to go as the normal person may find it hard to setup a viable working configuration.
Egress logging & filtering & alerts from guest sources ought to be part of these “canned” packages.
I am most concerned for USB takeover/keyloggers that have been blackbagged in and go unnoticed.
My colleges have been tracking them to be in the wild for some time.
Have we disabled external accesses / especially USB booting from all resources in our labs & offices? Its a constant battle.
Also seen recently, thankfully rarely, have been small embedded devices hooked up to network printers that look like a piece of industrial equipment as camouflage.
The office workers never look behind a printer to see that its phy network connection is being “shared.”
Few SMB businesses run port security on their switches; many still have hubs. Zero I have consulted for even know about weekly internal network port sweeps yet religiously rattle physical door nobs to the supply closets.
Looking at the “All” vs. “Medical” stats for May, the number 10 in “All” has a monthly volume of over 20,000,000. The number 1 in “Medical” has a volume of under 11,000.
Either these stats are compiled differently, or the healthcare system is a non-issue in terms of quantity (though, of course, a compromised healthcare system is a serious issue).
Exactly, outbound spam mostly comes from botnets, which got in by compromising computers, which means those same computers have ‘the risk of “catching” malware and spyware.’
And probably other computers in the same organization, which are subject to the same organizational IT security policies.
Most spam comes from botnets, and mobile laptops aren’t very good candidates for that, since they’re hard to control remotely, so we’ll investigate the WIFI idea, but I doubt that’s the source of most of the medical spam.
Indeed, ‘of course, a compromised healthcare system is a serious issue.’
-jsq
I don’t know enough about spam quantities to give any real meaning to 11,000 messages a month, but isn’t that the kind of quantity that could come from a single machine?
OTOH, I have experience with medical software and know that, especially in small surgeries, security is not a consideration at all. I’ve had to install medical software on laptops that were used for generic browsing tasks and hadn’t been updated in ages. These surgeries are way too small to ever show up in any ranking though.
Fahmida Y. Rashid has a pithy summary of the problem in eweek:
http://www.eweek.com/c/a/Security/UT-Researchers-Launch-SpamRankings-to-Flag-Hospitals-Hijacked-by-Spammers-454480/
“Poor security measures are generally responsible for employee workstations getting compromised, either by spam or malicious Web content. Once the machine is compromised, the botnet herders can add it to its spam-spewing botnet to send out malware to even more people. The original employee or the organization rarely has any idea the machine has been hijacked for this purpose.”
Maybe now the organizations have more incentive to pay attention.
-jsq
Hi Brian, I have followed you from wp days and have not seen you address this yahoo hack:
http://dagblog.com/humor-satire/who-hijacked-yahoo-mail-3151
I’m found this information when I was searching on why my yahoo account (which I rarely use) started sending out spam. My computer is locked down per your helpful instructions so I was stymied–then I found out I was not alone and it could be a yahoo issue/coverup.
There’s a heck of a lot of assumptions in this thread regarding what can and cannot happen.
May I assume that some of these people who think a Mac cannot get a virus, they do not have malware protection for that reason?
The person who found his webmail had been hacked, could have asked the ISP nicely to trace the logs of how connected, then gone to FBI or Secret Service and used “Terroristic” phraseology about how his privacy was injured so the Dept of Homeland Security not ignore the request to trace the logs and take care of the Intruder.
The people who did not have that much evidence … their e-mail address could have been copied into faked headers. Nothing needed to be hacked to accomplish that.
When Yahoo says to get a subpoena, then get a subpoena. I don’t see the problem why not. A letter from an attorney to Yahoo can do wonders at cutting to the chase. Do that ASAP because the logs are not saved forever.