Late last month I wrote about Citadel, an “open source” version of the ZeuS Trojan whose defining feature is a social networking platform where users can report and fix programming bugs, suggest and vote on new features, and generally guide future development of the botnet malware. Since then, I’ve been given a peek inside that community, and the view so far suggests that Citadel’s collaborative approach is fueling rapid growth of this new malware strain.
A customer who bought a license to the Citadel Trojan extended an invitation to drop in on that community of hackers. Those who have purchased the software can interact with the developers and other buyers via comments submitted to the Citadel Store, a front-end interface that is made available after users successfully navigate through a two-step authentication process.
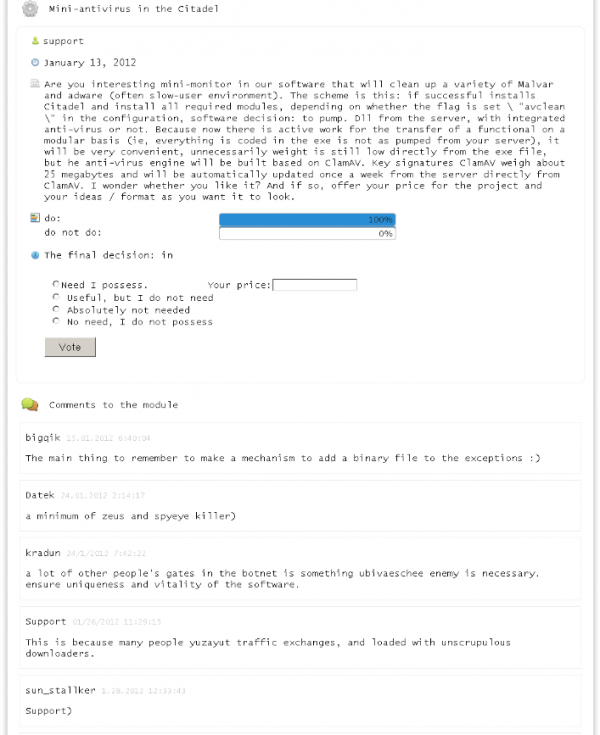
Upon logging into the Citadel Store, users see the main “customer resource management” page, which shows the latest breakdown of votes cast by all users regarding the desirability of proposed new features in the botnet code.
In the screen shot to the right, we can see democracy in action among miscreants: The image shows the outcome of voting on several newly proposed modules for Citadel, including a plugin that searches for specific files on the victim’s PC, and a “mini-antivirus” program that can clean up a variety of malware, adware and other parasites already on the victim’s computer that may prevent Citadel from operating cleanly or stealthily. Currently, there are nine separate modules that can be voted and commented on by the Citadel community.
Drilling down into the details page for each suggested botnet plugin reveals comments from various users about the suggested feature (screenshot below). Overall, users seem enthusiastic about most suggested new features, although several customers used the comments section to warn about potential pitfalls in implementing the proposed changes.
The customer resource management page also reveals that although the principal authors of the Citadel Trojan treat this as their day job, they try their best to have a life on the weekends. A notice prominetly posted to the Citadel CRM homepage reads:
Please note regarding the Help Desk in the Jabber chat & CRM page:
Daily from 10.00 to 00.30
Sat, Sun – closed, you can write us offline.
All requests and questions will be processed on Monday.
The collegial atmosphere being cultivated by the Citadel authors appears to have hastened the malware’s maturity, according to researchers at Seculert. In a blog post published Wednesday, researchers there said that they’d observed at least five new versions of Citadel since first spotting the malware on Dec. 17, 2011.
Seculert’s Aviv Raff said that means the miscreants behind Citadel are pushing out a new version of the Trojan about once a week.
“The only similar Trojan who got close to this pace was the so called ‘SpyZeus’ Trojan,” Raff said. “Others, including ZeuS itself, took between a month to several months to release a new version.”





It’s obvious from the second screenshot that two comments were made by Russians. Since one of the posts in question is writen under nickname “Support” it seems to me that people behind Citadel are Russians. Both messages were probably translated into English with something like Google translate.
“ubivaeschee” from Russian “ubivat'” (to kill).
“yuzayut” is a barbarized version of English verb “to use”.
is google translate really that bad with russian? 🙂
german -> english got quite good with google translate.
Russian is more irregular and complicated than German, that is putting aside that German and English are more closely related than Russian and English.
From my experience, Google is very poor at translating from Russian, slightly better at translating to it.
What for do they need a video grabber?
Might be useful in watching to see whether the Web injections are working correctly on victim PCs when victims log into specific bank web sites.
Aha, so that’s for debugging… Makes sense 🙂
not necesseraly “Russians”, but definitely Russian speaking- that could be anybody from former Soviet Union’s republic – Ukraine, Baltics, etc. and anywhere in the world. Could be your neighbour…
Just wondering how much is this crimeware kit going for on the blackmarket?
Ed – See the original story on this a few weeks back for the pricing info
http://krebsonsecurity.com/2012/01/citadel-trojan-touts-trouble-ticket-system/
The malicious intent notwithstanding, this is an excellent business model. I really wish some above-the-ground software developers adopted this approach.
I know of one example: PowerArchiver, a full-featured compression/decompression program (similar to WinZip, but better in my opinion). The PowerArchiver developers have a page where users can propose and vote on improvements or new features.
If you’re a beta tester for any type of software, you get that kind of interface. And the smaller/hungrier the company, the more responsive. If you’re beta testing for a one-person operation, you may see your comments implemented within a couple hours — very satisfying!