Federal prosecutors today announced criminal charges against three men alleged to be responsible for creating and distributing the Gozi Trojan, an extremely sophisticated strain of malicious software that was sold to cyber crooks and was tailor-made to attack specific financial institutions targeted by each buyer.
According to charging documents filed in the U.S. District Court for the Southern District of New York, authorities believe Gozi was the creation of Nikita Kuzmin, a 25-year-old Russian national. Authorities say Kuzmin was aided by 27-year-old Latvian resident Deniss “Miami” Calovskis, and Mihai Ionut Paunescu, a 28-year-0ld Romanian national who allegedly used the screen name “Virus”.
A press conference announcement sent to reporters today by the office of New York U.S. Attorney Preet Bharara states that Gozi infected more than one million computers — at least 40,000 of which were in the United States — and caused millions of dollars in losses. Bharara’s office called Gozi “one of the most financially destructive computer viruses in history.”
The charges include bank-fraud conspiracy, conspiracy to commit computer intrusion, wire-fraud conspiracy. Kuzmin was arrested in California in Nov. 2010; Calovskis was arrested in Latvia in Nov. 2012; Paunescu was arrested in last month in Romania.
First discovered in early 2007, the Gozi Trojan is a stealthy cybertheft tool that typically evades anti-virus detection for weeks — sometimes months — at a time. Cyber forensics experts say Gozi has remained a potent threat, mainly because its author has been very selective in choosing new customers and fastidious in creating custom, undetectable versions of the malware.
For all the Trojan’s sophistication, however, investigators say it was merely the delivery vehicle for the author’s real moneymaking machine: A software-as-a-service fraud scheme called “76 Service.” According to authorities, Kuzmin marketed the service on highly-vetted cyber criminal forums online, offering customers a soup-to-nuts crime machine that automated the processes of robbing online banking customers. Incredibly, this turnkey system even automated the ready supply of so-called “money mules,” willing or unwitting individuals recruited through work-at-home job scams to help thieves launder stolen funds.
“This was kind of like Salesforce.com for the bad guys, where he’d hook them up to his cyber crime facility and then charge them out the ear for additional services,” said one fraud investigator who worked closely with law enforcement officials on the investigation but who asked to remain anonymous.
“As a customer, you’d tell him which banks you wanted to target, and he has close-knit relationships with people who can code together pre-coded scripts to interact specifically with those bank Web sites, or has developers on standby to meet your needs,” the source said. “Then he generates the custom Gozi Trojan just for you, providing the cryptor that helps it evade anti-virus detection, and he provides the hosting infrastructure on the back end that lets you manage all of the machines infected with the Trojan.”
76 Service customers were supplied a slick, point-and-click Web-based interface that could be used to control machines infected with their customer Gozi variant, and to manipulate the way victim customers interacted with their financial institutions’ Web site.
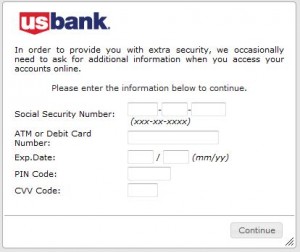
To that end, the “injects” supplied by the Gozi team were the key moneymaker for the 76Service. A typical Gozi attack worked like this: A 76Service customer would decide which banks most of those victimized by his Trojan were using, and then pay the author to create automated system so that when victims logged in to their bank’s site, the Trojan would inject HTML content into the bank’s Web site as displayed in the victim’s browser — usually form fields that requested additional personal or financial data on the victim, and then relayed that data back to the attackers.
One common type of inject used by Gozi was a pop-up box — such as the actual Gozi inject in the image above left, an inject that targeted US Bank and requested additional data from victim account holders.
Investigators say Gozi also was used to inject content directly into the bank’s Web page as displayed by the victim’s browser, allowing attackers to spoof the victim’s bank balance: In such attacks, the crooks could empty an account of all available funds, and yet force the victim’s browser to display the original balance before the robbery.
Another inject that sources say was used primarily against banks in the United Kingdom actually automated the process of sending stolen funds from compromised accounts to money mules. The mules were thought to be supplied by a third-party group that specialized in recruiting, vetting and training mules — priming them to be ready to receive transfers, pull the money out in cash, and then wire the funds to the attackers.
Prosecutors allege that Kuzmin directed the creation of Gozi, and that Calovskis was responsible for writing Web injects for Gozi and for customers of the ZeuS Trojan, another malware strain commonly used in cyberheists. According to investigators, Paunescu ran a “bulletproof hosting” service that was used as a proxy server for computers infected with Gozi and ZeuS.
If convicted, Kuzmin faces up to 95 years in prison. Calovskis and Paunescu face a maximum of 67 and 60 years in prison, respectively. Here are PDF copies of the charges against Calovskis, Kuzmin, and Paunescu.





Nikita Kuzmin is foster-son of famous russian singer Vladimir Kuzmin: http://en.wikipedia.org/wiki/Vladimir_Kuzmin
Is there any proof ?
Nikita, the foster son of Vladimir was born in 1988, so the age checks if his birthday is in January. The russian news sites would be covering this juicy detail, but there is nothing there right now.
His first nickname was RdM-[YanDeX].
http://web.archive.org/web/20020208124603/http://rdm-yandex.comtv.ru/
“Этот сайт сделал Никита Кузьмин и никто другой!”
Никита Кузьмин is Nikita Kuzmin in russian.
Than try to google “rdm-yandex.comtv.ru”.
You will find http://mylove.ru/rav69/
That is not 100% proof but a reason to think.
There’s certain visual similarity between RdM-[YanDeX] and the foster son of Vladimir Kuz’min. But what links the person with this online nickname to Gozi trojan and the related FBI cybercrime investigation ?
Aleksey, read please this document:
http://www.justice.gov/usao/nys/pressreleases/January13/GoziVirusDocuments/Kuzmin,%20Nikita%20Complaint.pdf, page 22, paragraph 30.
Bingo! I’m surprised this is not covered in Russian news yet. I’m sure it will be soon.
Here’s the photo of Nikita Kuzmin with his father, the famous singer Vladimir Kuzmin – https://img-fotki.yandex.ru/get/4006/yes06.61/0_17706_47fce0f7_XL.jpg
Nikita is first from the left. Does anyone have the photo of the federal cybercrime inmate Nikita Kuzmin to compare?
следствие видут Колобки .
How did they get caught?
Does the authenticated banking website page have to be vulnerable to stored or reflected XSS to allow the page injects? If not, how is this done specifically? thx!
No. The banking Trojan re-writes the HTML on the fly as it is displayed in the victim’s browser. The manipulation of the bank’s site is done on the client’s machine.
For more on how web injects work, see:
http://secniche.blogspot.com/2011/07/spyeye-zeus-web-injects-parameters-and.html
The thing to keep in mind is that once malware hijacks your browser, the attackers can make your browser display whatever they want. They can also hijack your browser session once you’ve authenticated to the bank’s site.
I wonder what makes these guys think they are so invincible and dare to visit USA. If I was mastermind behind a thing like Gozi, I would definitely stay away from USA or any western country for that matter. There are plenty of other places on the planet to enjoy ill gotten funds. Staying in Russia would be the best bet for a criminal like this.
Why did they ask for PIN in inject ?
PIN is useless without magstripe data.
Some card manufacturers still create the card using non-random ids. Depending on the card, if I know your bank and account number I can generate a valid card id.
If I’ve got the pin as well, generating a (non-chip&pin) card is trivial.
Bob,
sorry but I don’t understand your reply.
It’s not about generating a card number (what you refer to as “id”?), since that number is asked ( and alas gotten ) already in the inject field “card number”.
And anyway if you get that number you won’t (from what i read) be able to make a usable card without adding CVV to the stripe. The CVV is calculated factoring various front info like card number and expiary date AND a secret key know only to the card maker.
The crooks have gotten smarter, that inject on the fly right on to the bank site is way better than the old phishing page. However I think this guys undoing was that it was his site would have left some trails as to what went on. I wonder what the banks are doing to counter injects like this from taking place during a session.
Brian have your heard if the banks have a good counter measure against these type of injects from occuring during a users session?
I would think they must have a strategy in place or are trying to develop something to counter this.
As this is the customers browser, we (Banks) can’t do much. Some Banks offer the customer to download security software to prevent the inject (e.g.: software on the browser checks if any unusual activity is going on, and warns the user – and the Bank in the background could e.g. put the transaction on hold)
Main issue: deal with customers and support their browser problems (that have nothing to do with your software)
Best option is to use two factor authentication (e.g.: send authorization code to SMS), that code will not match the altered transaction. (BUT there is malware out there to circumvent this too – see Zitmo- Zeus in the mobile)
In regards to fully automated mule selection (which mule is “live”, their account number, limits, etc) I have to disappoint you too, this has been seen in malware for a while – again ZEUS being the most prominent one.
Regrettably, the mechanisms in place to differentiate between secure and unsecure content on a web page are often ignored (although I am unsure of how useful these tools would be in this case). All too frequently consumers are “trained” by web developers to ignore certificate warnings, and browser developers make it easy by including the “do not warne me againe” option on the pop-up boxes, giving the uneducated users a dangerous option. Educating users is the best course of action, and Brian’s blog is doing this quite well – well done Brian. Please continue your efforts.
smart crooks? Kuzmin smart to travel to the US where he was caught 2010 and cooperated fully, hoping for a deal? 2 years to catch the romanian? I call that slow and cumbersome, useless and of no impact.
What is ” slow and cumbersome, useless and of no impact.” ? FBI efforts in addressing the issue of financial trojans? I would disagree, they definitely deserve credit for uncovering the real identity of a person behind online nickname and they definitely used well the amazing opportunity they got when Kuzmin was stupid enough to travel to the states.
Looking at the trend, it seems like FBI knows the real identity of many people who are prominent in “the biz”. Once the criminals take the mind-boggling-stupid step of entering US or US-friendly jurisdiction they are caught and detained. I say this is really good work by the agency.
According to the Paunescu complaint (http://krebsonsecurity.com/wp-content/uploads/2013/01/Paunescu-Mihai-Ionut-Complaint.pdf) it seems the Paunescu hosting service was a callback for the ‘Virut’ Botnet (http://krebsonsecurity.com/2013/01/polish-takedown-targets-virut-botnet/) . See the complaint page 15, paragraph 25.a. and page 13, paragraph 23.b.