“History is much decried; it is a tissue of errors, we are told, no doubt correctly; and rival historians expose each other’s blunders with gratification. Yet the worst historian has a clearer view of the period he studies than the best of us can hope to form of that in which we live. The obscurest epoch is to-day; and that for a thousand reasons of incohate tendency, conflicting report, and sheer mass and multiplicity of experience; but chiefly, perhaps, by reason of an insidious shifting of landmarks.” – Robert Louis Stevenson
To say that there is a law enforcement manhunt on for the individuals responsible for posting credit report information on public figures and celebrities at the rogue site exposed.su would be a major understatement. I like to think that when that investigation is completed, some of the information I’ve helped to uncover about those affiliated with the site will come to light. For now, however, I’m content to retrace some of my footwork this past weekend that went into tracking individuals who may have been responsible for attacking my site and SWATing my home last Thursday.
I state upfront that the information in this piece is certainly not the whole story (most news reporting is, at best, a snapshot in time, a first rough draft of history). While the clues I’ve uncovered thus far point to the role of a single individual, this person is likely part of a larger group involved in hacking and SWATing activity.
In my story last week, I posted a copy of the internal database for booter.tw, one of several fee-for-service “booter” sites. Booter sites are perhaps most popular among online gaming enthusiasts, who like to use them to knock opponents offline; but they are frequently also used to launch debilitating attacks on Web sites. That leaked booter.tw database shows that the denial-of-service attack that hit my site last week was paid for by a booter.tw user with the account name “countonme,” and using the address “countonme@gmail.com.”
Since the attack, I reached out to the proprietor of booter.tw, a hacker who uses the nickname “Askaa.” He informed me that the individual who launched the attack on my site was a hacker who used the screen name Phobia. “Phobia hacked into the countonme account to make it look like the according user attacked you,” Askaa said in a brief interview over Skype instant message. Askaa declined to say why he was so confident of this information.
Separately, over the weekend I received an email from a person who claimed to have direct knowledge of the attacks (perhaps because he, too, was involved). This individual said those who attacked my site were a group of young online video game enthusiasts who were upset that earlier in the week I’d written about ssndob.ru, a site that sells access to peoples’ credit files, Social Security numbers and other sensitive information.
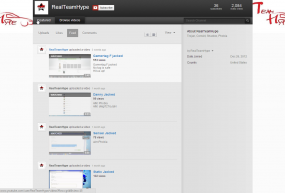
According to this source, the hackers in this case belong to a four-man Xbox live gamer team that calls itself “Team Hype,” which until this past weekend had posted a number of videos to their own youtube.com channel, RealTeamHype (more on what happened to these videos in a moment).
According to the anonymous source, Team Hype consists of hackers who use the nicknames “Trojan,” “Shadow,” Convict,” and “Phobia.” The source said the group used SSNs from ssndob.ru to hijack “gamertags,” online personas tied to Xbox Live game accounts. In this case, specifically from Microsoft employees who work on the Xbox Live gaming platform. Some of the group members then sell those accounts to other Xbox Live players.
“They hack/social engineer Gamertags off Microsoft employees by using SSNs,” the source wrote. “I didn’t DDoS your site and I didn’t SWAT you, Phobia has been telling everyone he did. The method he released he said he gets SSNs, then calls phone companies and redirects the number and than gets xbox phone support to call number and confirm. I heard he got pissed that you released the site he uses. Also Trojan told a buddie of mines ‘fear'(on AIM) something about a dead body in your closet about your swat.”
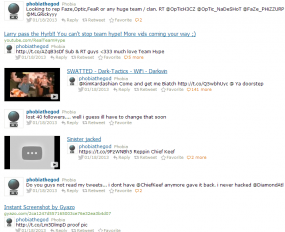
The source said Phobia used the Twitter account @PhobiaTheGod (now closed, but partially available here and at this cache), and that Phobia’s personal information — including real name, address and phone number — had been “doxed” or released onto Pastebin-like sites some time ago. It didn’t take long to locate this profile at skidpaste.org (“skid” is a diminutive reference to the term “script kiddies,” referring to relatively unskilled young hackers who conduct most of their exploits using automated tools without understanding how those tools actually do the dirty work).
Having watched most of the videos at RealTeamHype’s youtube channel, it appeared that my source was telling the truth about the hijacked accounts: In fact, the videos at that channel documented such hijackings in progress using desktop screen-grabbing software. The videos even showed conversations with other team members in instant message windows in the background.
But I was reluctant to put much stock in the information until the source sent me a piece of information that only the attackers and my ISP would have known. On Friday, I received a call from Cox Communications, my Internet service provider. They wanted to know why I had paid $3,000 toward my account using several different credit card numbers. I assured them that I hadn’t made that payment. Then I heard from a member of Cox’s security team, who asked if I’d reset my password and if I’d indeed asked to cancel my Internet service. He was unsurprised to learn that I hadn’t. Apparently, hackers reset the password to my Cox email account by working out the answer to my secret question (this account is separate from my Cox user account, was set up over 10 years ago, and has never been used for anything remotely interesting or sensitive).
The source told me via email: “Hey brian, i just spoke to fear he told me phobia and his buddies were telling him that they hacked your cox email and paid your cox bill with hacked credit card, im not sure if this is true but im letting you know.”
I decided to give a call to the phone number included in the doxed records for Phobia, which rang at a home in Milford, Ct. A 20-year-old named Ryan Stevenson picked up the phone. After introducing myself, I asked Ryan if he knew anything about booter.tw, and he said he didn’t bother with booter sites because they were lame.
I then asked if he was part of a Xbox gaming group called TeamHype. He said yes, but that he hadn’t been associated with that group for six months. When I asked why, he said that his teammates had repeatedly called his house posing as the police, and had even SWATed his home — something his father confirmed by interjecting over Ryan’s voice. I told Ryan I found this strange, since the youtube channel for TeamHype’s video channel was created on Dec. 26, 2012, and his youtube.com account “Phobia” had uploaded videos of Microsoft Xbox accounts being hijacked as recently as February 2013. What’s more, those videos (like the one reproduced here) show Phobia sending shouts out to his buddies.
Then I remembered where I’d heard the nickname “Phobia”: In a terrifying tale by Mat Honan, a wired.com reporter who woke up one day last year to find his Macbook and other Apple devices being remotely wiped of their data after hackers managed to commandeer his Apple iCloud account. According to Honan’s story, “How Apple and Amazon Security Flaws Led to My Epic Hacking,” a hacker named Phobia reached out to him shortly after the incident. “Phobia was able to reveal enough detail about the hack and my compromised accounts that it became clear he was, at the very least, a party to how it went down,” Honan wrote of his ordeal. “I agreed not to press charges, and in return he laid out exactly how the hack worked.”
I asked Ryan if he knew Mat Honan. Here’s a snippet of our conversation:
BK: I’m looking at a story in Wired magazine from Mat Honan about how his Apple iCloud account was hacked. Do you know this guy?
RS: Yeah, I used to.
BK: Uh huh. And is Honan referring to you in this article?
RS: Yeah.
BK Yes?
RS: Uh huh.
BK: Did anything bad ever happen to you because of this?
RS: No.
BK: So, this was your doing with the Mat Honan hack, but you say you would never use a site like a stresser or…
RS: Yeah, I would never do that. That’s stupid.
BK: …or hack a reporter’s account or launch a denial of service attack against a reporter, or SWAT his house….
RS: <extended silence>
BK: So what’s the point of hacking a reporter’s iCloud account? Why’d you do that?
RS: Just to prove a point that, like…the security is breachable.
BK: Are you still on twitter?
RS: Yeah. But I changed my username yesterday.
BK: Really? Why?
RS: Because I don’t want to deal with people anymore. People call my house and pretend to be the police and stuff.
BK: Yeah, I know what you mean. So, what was your old Twitter account name?
RS: I think you know.
BK: PhobiaTheGod?
RS: Uh-huh.
BK: So what’s your new Twitter handle?
RS: <extended silence>
BK: Look, did you launch the attack on my site or not? Some of your gaming buddies sure seem ready to throw you under the bus for it.
RS: I didn’t even know who you were until someone tweeted your site. I just went to it to see what it was about.
At this point, Ryan’s dad grabs the phone and tries to tell me that his son didn’t really say that he hacked Mat Honan’s iCloud account, but that what he really said was he only knew the guy who hacked Honan’s account. Ryan’s dad goes on to explain that his son is basically a good kid who fell in with the wrong crowd, and that his son wouldn’t stoop to hacking other people, and certainly not to sending SWAT teams or any of that nonsense.
I decide to share with Ryan’s dad the URL for the TeamHype channel at youtube.com, and I can hear the father taking notes on the other end of the line. From the racket in the background noise behind the voice of Ryan’s dad, it’s clear that someone is furiously banging away at a computer keyboard. My suspicions are confirmed when I refresh the TeamHype youtube channel and find all of the videos have been deleted (the one above was cached in my window so I was able to re-record it).
This entire episode is giving me flashbacks that date back almost a decade, when I began communicating with a hacker group that called itself Team Defonic. These young men positively lived to hack into and post online personal data and photos belonging to celebrities and public figures. They also were obsessed with plundering databases for Social Security numbers and other sensitive information. Most of them were later arrested and jailed for their roles in breaking into Paris Hilton’s cell phone and hacking into accounts at Accurint, a law enforcement database run by data aggregator LexisNexis.
Stay tuned for more on this developing story. Meantime, many thanks again to all of you who’ve expressed concern or reached out via Twitter, Facebook (and Paypal!) to voice support and solidarity.




20years old, no longer a juvenile. Adios, kid!
Ryan Stevenson, meet 18 U.S.C. § 1030. Mr 18 U.S.C. § 1030 is also known as the Computer Fraud and Abuse Act, and is not somebody you want to meet up with in a well lit courtroom.
18 U.S.C. § 1030, meet Ryan Stevenson. Please make sure that, if Mr Stevenson is the SWATter responsible, that Mr Stevenson gets to enjoy PMITA prison.
This latest post just serves to reinforce my position that *parents need to be acutely aware of the activities of their children* online.
Far too many kids out there are meddling in activities that they don’t realize will land them in prison… and their parents are completely out-of-the-loop as to what their kids are up to.
Look forward to reading about how this all turns out.
Yeah, that wouldn’t make a difference in the slightest. He’s “20” and how many other late teens, 20-30 year olds typically make up that scene? A ton. Rarely do you see a 40-50+ year old “hacker”. These are the people that grew up on computers. The mentality though, I get it and I don’t.
No one ever thinks they will get caught, because when dishing it out to other kids that can’t fight back, or lack the knowledge, nothing happens. You pull that same stunt with a celebrity, someone involved in government or someone that does understand it, then it doesn’t work out the same.
I feel that comment is mis-guided.
IMHO there are more likely to be plenty of 30+ “hackers” but more in the sense of white hat hackers who know the workings of what is behind what they’re doing.
Its true that the 20-something and under group did grow up with computers, the problem is that the majority of them know “how” to use a computer but not “why” they work in the way they do. Buying the services of malware authors etc. does not a hacker make.
I think this story highlights the lack of maturity of these 20-something and under script kiddies, the repercussions they /may/ face and that youthful optimism that you are untouchable and immortal.
See BrokenSyntax’s post below. And I agree with both his and yours.
I don’t mean to come across as saying “no one over 30 knows anything about hacking or security”. My point is, growing up with computers, the internet, someone might have a muddied idea that anything you do online actually matters offline, cause a lot of times it doesn’t. Look at piracy, everyone has downloaded songs or movies. Hey, hardly anyone gets caught.
Interesting point, but the “losses” incurred from downloading a song is purely theoretical (technically, just because someone downloads a song doesn’t mean they would’ve bought it otherwise). Nothing is taken away either, as copies are being made (nobody is losing the song from their collection, for example). Stealing credit card information and using it to buy things is indeed very real, as is stealing someones ID and using it to sign up to different services, etc (indeed, people can be RUINED from stuff like this).
The problem is that a lot of script kiddies simply don’t think or discern the difference between virtual and physical (or just don’t care).
Years ago, people hacked (or cracked, as hacking is also a term for using anything in a way that it wasn’t designed for), to do things such as seeing if they could penetrate an “un-penetrable system”, or to explore the latest technology, or encountering a challenge, etc. That’s not to say that this doesn’t happen anymore, or that even back then this was all that hacking was, but its a notable difference to the kids that download a pre-made script, enter one or two details, and then hack someone. There is no exploratory challenge there, just intent to do damage.
I was almost going to add “and I don’t want to turn this into a right vs. wrong with piracy”, I just used that out of the many examples of things people don’t think twice about, they don’t view it as wrong even though it can get you in trouble.
Maybe I’m thinking too much into it, you know, cause all it really boils down to is “this person doesn’t give one shit and what they’re doing makes them feel good.”. Million different ways to acquire that mindset, but it’s all the same idea. “This makes me feel good, and I don’t care, I’m going to do it till I can’t.”
Selling blue boxes to allow people to make long distance calls without paying was a crime, and “Cap’n Crunch” did hard time for it. Steve Jobs and Steve Wozniak avoided the same fate by just a fluke. (The cop that pulled them over one night didn’t know what the stuff in the car was.) We might all be entering data in straight lines on putty colored IBM terminals and using cell phones that just make phone calls if Apple/NeXT hadn’t become competitors in the consumer electronics market.
This kid, who knows what his potential is. He effed up, badly. But we don’t know much more about him. When you see what adolescent males are capable of when put in groups and isolated from the real world (e.g., the Stanford Prison Experiment, where even the researchers found themselves being sucked into the scenario), you need to realize they are going to go through a lot of changes as the mature in a few years. You need to assess each person as an individual to see if they’re really amoral or just “joyriding” with virtual friends.
And if you’re raising your kids to believe that obedience is a virtue, be warned that when they hit adolescence, they’ll start obeying someone other than you. Raise them to be stubborn and strong willed, and give them a strong sense of right and wrong, so they will be the nonconformists who say “stop” when things get out of hand in a group.
+1, like, thumbs up Alpha. You nailed it.
“everyone has downloaded songs or movies”
I have never illegally downloaded a single song or movie, and it is highly unlikely that I am the only person in the world to have avoided doing so, so therefore your assertion is incorrect.
Really, you’re putting too much thought into my choice of words over the point.
The group of people who steal movies and songs is rather small in terms of the entire population, but those in that group erroneously believe that the entire world does it because that is their peer group. They tend to be teenagers and slightly older. They have not created anything of value and therefore never thought of how they would feel if they spent years creating something — software, literary, music, etc — and then sold only a few copies because some child gave it to the world for free.
Searching twitter for @phobiathegod will show what others had been saying to him, even though his account is gone: https://twitter.com/search?q=%40phobiathegod
Looks like there’s a protected twitter account named @MVPhobia that appears to have been in a response from Stephen Toulouse to @PhobiaTheGod.
@Negro also posted this, which also shows @MVPhobia in the conversation: “@PhobiaTheGod u sure it wasn’t u? U bragged about getting SSN’s on twitter :/”
And another from @XboxSupport with @MVPhobia: “@PhobiaTheGod Did you have any Xbox questions that we can help with today?^JN”
Obviously @MVPhobia is somehow associated with @PhobiaTheGod, if it’s not the same person.
Yeah, thats him.
He changed it to “PhobiaWasGod” I guess since basic social engineering is godly today, LOL
reading blog posts has never been such awesome !!!
thanks brian
“working out the answer to my secret question”
You actually give a valid answer? I never do that. I make something up, e.g. “What was your mother’s maiden name? Barack.” My answers are actually much more obtuse. Birth date? I make one up. Yada, yada.
But back to the main event: never screw with an investigative reporter, especially one who specializes in cyber-stuff.
that’s what you put for your answers now, but what about 10 years ago? the advice to lie on security questions is relatively new as far as i can recall.
In terms of paranoia, I am a pioneer. I always thought it ridiculous that Juno, Yahoo, et al, needed to know my actual birth date.
And if you lie on the security question, you get caught in the liar’s paradox where you have to either 1) tell the same lie all the time or 2) remember the different lies you’ve told. 1) makes the lie almost as ineffective as a true security answer (though possibly harder to guess) and 2) makes the security answers just as hard to remember as passwords.
Of course. However, my lies have a method to them. My “birth date” is that of a historical event which means something to me. My “first girlfriend’s name” is that of an obscure person, one who I remember. And so on.
And given the movement towards outsourcing every single database to India and other countries, your honest replies to these questions will not be secure.
the liar’s paradox is easily solved by writing the lies down.
or storing them in your password manager, for that matter.
For the last 10+ yrs, I’ve been lying on those security questions. Never tell the truth unless absolutely necessary. Not just lie – but let your password manager have fun since these fields seldom have the stupid limits that the password field has.
However, like many people here, I might need to look at some of my older accounts to see if I was always a liar or not.
I wrote ” My answers are actually much more obtuse.”
Make that “obscure.”
I will not drink and comment.
I will not drink and comment.
I will not drink and comment.
I will not drink and comment.
I will not drink and comment.
…..
If they are obscure, they will be obtuse.
I do try to stick to that convention, but fall off the wagon occasionally! HA! 😀
“But I do know this: you strap on a gun and go struttin’ around some other mens country you better be ready for some action, Jack. People are touchy about that sort of thing.” – Carlin
George Carlin? Sounds like him! 🙂
Awesome follow up, BK!
Hehehe, and here was me dreaming about elite cybercriminals getting pissed off and attacking you and this blog and it turns out to be a bunch of (apparently not unintelligent but foolhardy) adult “children”. LMAO.
Nonetheless please keep up the good work, never a dull read at this blog.
Still lolling 😀
I’d think the “elite” would want better stuff than this, stuff they can sell. Unless they just want the bragging rights, they wouldn’t risk it or waste their time.
Anyone dumb enough to come out of the woodwork and show what they really know (including myself) is not elite, especially this guy.
The FBI needs to pay this young kid in Milford Connecticut a visit to find out exactly what he does and does not know. By the way the site exposed.su looks to be shut down as of this afternoon .
NICE!
and wow these kids threw around 3 grand like nothing?
You’d think after the MIT kid was getting sentenced with 35 years and then was found hanging in his cell, for doing nothing illegal but “seeming” like a hacker and defending file sharing……that these hackers would understand the hate forming for them in society.
When 1 out of 3 Americans get their credit, accounts or identities stolen, or when the avg computer user’s laptop gets so virused it becomes frustrating to use….. they are past the point of thinking hackers are “cool” and are now beginning to hate them.
All online communities are dying, not just the gaming ones. All of them! These hackers even cost people jobs. And its starting to get sad.
As it is most Americans are gaming on console systems and use their phones and ipads for everyday computing. Its not because we are more computer illiterate then the avg European, Its just because we’ve “been there, done that” and know better. They are safer and faster. We have higher standards, when it comes to sports, fairness and productivity, which is making us realize our lack of security.
These hackers should be especially worried now that John Brenan is CIA director…(the cia is a hit squad now) Especially America’s growing fear about all these corporations and gov’t sites that are being hacked. Hackers can be labeled terrorists and are gradually being seen as a bigger threat to our economy and national security then Al Qaeda.
Even American citizens can be hunted down and assassinated without warrant or trial now!
These guys should really find a new line of work or hobby before they ruin their families lives.(like they do to so many)
But when it seems like there are no good guys left on the web anymore, there are rare guys like Brian Krebs.
I salute you Brian.
Rich.
Um, Rich? That’s…..not what happened. Aaron Swartz had yet to be tried, let alone convicted, let alone sentenced. He was not in a cell.
“As it is most Americans are gaming on console systems and use their phones and ipads for everyday computing. Its not because we are more computer illiterate then the avg European, Its just because we’ve “been there, done that” and know better. They are safer and faster. We have higher standards, when it comes to sports, fairness and productivity, which is making us realize our lack of security.”
Uhhhh… I disagree on this bit at pretty much every level. Sounds like you haven’t been much to Europe, frankly.
Well you can disagree on my American exceptional-ism. But from what i hear from Europeans its because we are more computer illiterate. I disagree.
The facts are we designed and invented most of the computers, software and pc games in the world, so I doubt thats the case. (this kid BK exposed i believe is American?)
But its a fact, most online communities are losing most of their Americans. This can’t be disputed.
The majority of the game servers are now hosted in germany and brazil. Most American servers, alot of times, have more foreigners on them then Americans!
The pc industry is dying imo.
Now we can argue as to why this all is…..but those are the facts. IMO, just like public parks were ruined after the crack era and early 90s gangs, which is why you rarely see Americans in alot of nyc public parks anymore, its mostly foreign tourists and immigrants, the same thing is happening to the pc industry. Its becoming abandoned, to people who don’t know better or take it for granted yet.
And eventually we will get policed out of the internet in the same manner as public parks. These hackers who think they are unstoppable are delusional. And the silence, and the turning of a blind eye by these cyber activists group like anonymous, or Aaran swartz, by not going after the real malicious hackers…..and not talking about the real underlying issue that ruins the web, instead defending them!?!? are useless and are only doing more harm then good.
What happened to white hats vs black hats? It seems everyone is now just a malicious pos spy/thief on the internet. The younger generation has no morals, and these internet companies are unscrupulous….and they are the ones taking our potential and freedoms away. not the government! Grow up!
Pretty simple, the PC industry is dying because it is cheaper to work the web on a smart phone with unlimited services. PCs cost too much for the average Joe Citizen to upkeep.
Straight Talk at Walmart for 40 bucks a month unlimited 3G is the death nell for PCs in our area! Also the death nell for POTs services, DSL, and even cable tv, if you can stand to watch TV on a little teenie tiny screen! 😉
you think these ipads and iphones are cheap? IMO, they cost as much as a pc…lol 700 dollars for an ipad? hundreds for a phone?
and 3g for 40 dollars a month is extremely slow and unbearable for me. compared to what i get with verizon fios for the same price…lol forget about youtube videos.
And you can’t do real office work or anything practical and productive on an android device, imo. Its all for show and simple basic tasks. Like checking emails or browsing some webpages while on the go. You still need a real pc to do real work.
IMO, I think most people use these android devices…because their old virused laptop at home is too slow and frustrating to use unless they need it to do something that can’t be done on the ipad.
Most people don’t want to be bothered cleaning or reformatting their pc if they have a phone they can use instead for simple things.
and buying a “new” pc for these reasons, even for the people who are not too computer savvy, just doesn’t seem right. They just stop using them.
“The facts are we designed and invented most of the computers, software and pc games in the world”
World Wide Web.. british citizen.
Pirate Bay.. Swedish citizens
Mega… german citizen
Playstation/Sony… Japanese
Nintendo… Japanese
Samsung… South Korean
Nero… Germany
Skype.. Estonian
Kaspersky… Russian.
IRC… finnish
Linux…. finnish
Ubisoft… French
Konami… Japanese
Sega… Japanese
While it is true the US has given the world a lot of tech, tech companies etc, don’t underestimate the importance of other countries in the world and their contributions to tech industry, games etc. and while the US makes up a large portion of these countries the scale of foreign workers in these US companies can also be quite large.
I don’t know any “European” who claims that the average US citizen is computer illiterate. I, as a European would expect the majority of US citizens to be able to use a computer.
Actual internet users which although doesn’t give a full view of computer illiterate is a good indicator
http://en.wikipedia.org/wiki/List_of_countries_by_number_of_Internet_users
The US has the second biggest amount of users of the internet based on numbers, but by actual percentage of users based on population makes the US 27th in the world.
Learn world geography before engaging typing.
“World Wide Web.. british citizen”
The Internet had many fathers, including ARPANET.
“Pirate Bay.. Swedish citizens”
That’s like saying that Al Capone invented soup kitchens because he would sometimes give away food to convince Chicago voters to vote his way. Pirate Bay is a group of petty thieves, nothing more.
“Samsung… South Korean”
Huh? Samsung is a South Korean corporation. What’s your point?
“Linux…. finnish”
Unix, which all flavors of Linux borrowed from, was an invention of AT&T / Bell Labs, an American corporation. Not to mention C, C++, and a great deal of telecommunications technology.
And since you are too young to know, I’ll add the pioneers of computing: HP, IBM, Sperry Univac, RCA (not the current French company), Digital Equipment Corporation, Burroughs Corporation, NCR, General Electric, Honeywell, Cray Research, Data General, Storage Technology Corporation (later StorageTek), and Control Data Corporation, all American companies.
Oh, and “finnish,” “german,” and “british” are to be capitalized.
An American who doesn’t know anything about the world outside of the USA… *sigh*
“All online communities are dying, not just the gaming ones. All of them!”
Diversification, destructive competition and bad improvement cannibalize market shares, but overall online communities are still growing.
Do they have Xbox Live in prison? Stay tuned?! LOL
Daddy might really regret helping junior destroy evidence after he is informed by the FBI that he is now an accomplice after the fact. The family that SWATs together, stays together: in prison!
Brian,
Years ago a marine who had been in…uh…interesting circumstances told me that the biggest thing in the world is the bore of a gun that’s pointed at you. I regret that you learned this when the swat team pointed multiple weapons at you.
When my house was burglarized, it meant a lot when neighbors expressed support and empathy, so I’m writing to say “Thank you” for fighting the good fight on behalf of us all.
Have another dinner with your friends: living well is the best revenge!
Hampton DeJarnette
Did anyone else notice that Brian’s titles for his SWAT adventure epics are rather erudite, so unlike his usual workmanlike style? It reminds one of dusty tomes, not derelict tomboys.
One can get pretty philosophical when one stares down the barrel of a gun (or five). Both of the past two headlines are from RLS, a favorite author of mine.
heh, heh… I’ve had a cop’s gun pointed at me from two feet away. And I was looking at years in prison – which I ended up actually doing.
You managed to avoid both injury and the “fun part”… 🙂 Good work!
As Andrew Vachss hard case character Burke says:
The only way to do anything is to do it so you walk away from it.
The only game I play is where winning means you keep playing.
I managed to avoid THAT part, too. Course, it wasn’t nearly as fun being paranoid enough to be in the “better” category.
Pieces of eight! Pieces of eight!
Oh, yeah, the FBI will be on this kid and his father like jackals! 🙂
Just what you posted here is probably enough for a warrant. Assuming they weren’t already on to him about something else.
Seriously, if it wasn’t for the sheer AMOUNT of this stuff going on and the LEA backlog, most of these guys would be in prison. Their opsec just sucks! It’s amazing!
It’s like a bank robber stepping out of the bank and waiting to sing an aria until the cops come! 🙂
When you called, first thing that kid should have done was hang up! LOL! 🙂 He’d better be Guttman wiping every hard drive he has NOW! LOL! 🙂
“Seriously, if it wasn’t for the sheer AMOUNT of this stuff going on and the LEA backlog, most of these guys would be in prison. Their opsec just sucks! It’s amazing!”
Absolutely. It’s ridiculous. It’s like they aren’t even trying. Maybe they’re just that cocky or maybe they’re as dumb as they are smart. Proxies and not posting identifying vids of oneself, at a minimum. Not even that from these kiddies. So many do it for pride, fame and identity though. I think that’s the problem as staying behind text, an alias and asynchronous messages is just not as fun.
Far as this kid goes, if Krebs recorded the conversation then they essentially have a partial confession. They have a confession for one serious crime in the past. Then, they have partial confession for the current one. It’s better than a warrant: it’s enough for arrest on one (did it himself or accessory) and investigation on the other while he in bars.
SWATers have always annoyed me. Fake ass hackers and anarchists, too. I hope he does some time.
Guttman wipe can be recovered by the right techniques; only total physical destruction of the drive can they hope for success.
Well, practically speaking, no. Guttman is good enough by all reports. In fact, in most cases, one or two wipes is good enough.
Physical destruction IS best for the absolutely paranoid. But unless you’re bin Laden, Guttman is fine. No one’s going to use an electron microscope on this kid’s drive.
I read about a guy on the border who had to give up his drive to the TSA, and they defeated the Guttman technique in about 15 minutes. Of course he wasn’t a terrorist, but that information was harmless to him at least.
I read another article about a person discussing this same subject to a friend who worked somewhere with Homeland Security, and this friend of his recovered a drive for him in the same amount of time. Sorry I don’t have any links.
While we’re on the subject, what about microwaving them? I know it destroys cds.
And what about SSDs? I know a lot of people recommend not doing wipes/file overwriting cause it will shorten their lifespan, but do they benefit from wiping more than once?
Agreed either way though, before tossing a hard drive of any sort, drill it. You know, less of course you’re doing it to hide malicious stuff in which you’ll be found “destroying evidence”.
Microwaving metal, including CDs/CDROMs, is risky because you might end up melting the plastic on the floor of the appliance due to heat transfer. You might even end up with the CD melted into the floor.
Microwaving magnetic media, e.g. hard drives, will accomplish nothing, erasure-wise. X-rays will also do nothing to magnetic media. I learned this years ago while working for a DOD contractor.
“Microwaving magnetic media, e.g. hard drives, will accomplish nothing, erasure-wise” unless you heat the platters to the point of deforming, with a risk of fire. Don’t do it.
I didn’t plan on it anyway, nor would I cook my food in the same microwave. It was more of a tongue in cheek sort of idea. I still think it’d seriously mess them up from the sparking, some videos on youtube confirm this but there are better ways to go about trashing a hard drive anyway.
If the hard drive had glass disks with coating, it may cause sparking tracks along the surface, which would pretty much destroy a lot of the data; but you’d have to disassemble the drive to keep the housing from shielding the microwave radio waves.
However, I was also reading a Popular Science or Scientific American article about how they can analyse the magnetic surface of disassembled drives, and peel back the magnetic history quite handily. I assume this was for all metal constructed drives, or coated drives that didn’t have much damage.
Anyway, it was an real eye opener in computer forensics, so I always advise my clients with IP to protect to burn their drives into ashes, if possible. Thermite always does the trick! It is a lot easier than trying to torch them.
Sorry but no, TSA, DHS, no one is recovering drives that have had more than one or two wipes without using a scanning electron microscope and even then – forget it. FUD, I’m sure they would love for you to actually believe this lol. Talk to someone who knows their way around a PC3000 and get the real story…
NIST 800-88 (the federal standard for destroying data) is happy with a real overwrite-once secure-erase of hard drives as “purge” (which is considered sufficient to handle a laboratory attack, and is acceptable for drives containing Top Secret material if the drive is to be reused within the same security enclave), and are happy with that for disks LEAVING the security enclave if its of “moderate” or less security categorization.
Since these guys are paranoid, I’m comfortable with “erase once” as my data purge technique.
To give you an idea of NIST’s paranoia, for paper its “shred to either 1mm x 5mm OR pulverize until the pieces can fit though a 3/32” screen, and for microfilm its “Burn to white ash”
I am constantly running across articles explaining how investigative agencies – and in fact – industrial espionage criminals, analyse hard drives to harvest data. The last one I read had something about gauss fields of magnetism, that can see deep into the magnetic history of the drive. They don’t always use the drives hardware to read the disks, they can use other methods, and I’m sure they sometimes probably disassemble the drive.
I’m sure a lot of misinformation is disseminated to confuse people into revealing their data. The idea being, why make it harder for the government to do forensic recovery of criminal evidence?
Nicholas Weaver is correct. Most of that is mythical at best. Most quick recovery they do is usually because of one of two things: (1) the data wasn’t really deleted or protected at all, (2) there was an extra copy (e.g. cache, swap) that the owner didn’t know about. Then, there’s the companies that recover data. Even Guttman has said his advice for that mainly applied to older drives. I never overwrite more that once.
A few of us discussed this on Schneier’s blog on the flash drive article. My long-standing claim is that the best way to erase data is to encrypt it and forget the key. Destroying a key is so easy compared to destroying tons of data allocated in who knows what way. If extra concerned, I destroy the key and then do a quick overwrite with random data.
One of best strategies is an inline encryptor. This puts the key in dedicated, simple hardware. Erasure is pushbutton simple. The solution is OS and drive neutral, plus fast. See the NSA Inline Media Encryptor for an example of some of the properties. It’s what I compared my designs against.
Clive Robinson, who helped me work out the details, further suggested that ultra sensitive data be protected by triple encryption: software crypto, IME, and a SED. Three points of failure in crypto required in that case, for anyone really worried about crypto part. I honestly spend more time worrying about endpoints in my designs. So, one good crypto layer over storage is good enough for me. From there, it’s compartmentalization of software or maybe dedicated devices for processing certain information.
A 3/4 inch carbide drill bit at maximum speed while the hard drive is in a vise will do the trick.
Heh! Heh! … I like thermite myself. 🙂
Honestly these are both overkill. A microwave, hammer, or both would do the job quite nicely.
It is sad what elite Xbox gamers get up to in their spare time. And how they use the Internet to make other people’s life miserable just because they don’t like something they said.
I’ve had to put up with my share of abuse, no SWAT teams were ever sent after me… Apparently what is acceptable behaviour, especially online, has declined since the early 90s when I first started using BBSs and FidoNet.
I have had the cops point their guns at me a couple of times in the past. I will tell you this, it is absolutely not a fun experience to deal with. When a person is in their early twenties you are more willing to take stupid risks. As you get older and mature doing illegal crap on the internet real is not worth the risk of doing state or federal time. Why people take that risk in doing internet related crimes kind of makes you wonder if they real know right from wrong or if it’s something else. I read a article a while back that stated most hackers may have some type of autism which makes them better at focusing on things like coding or doing advanced network research . In my opinion, It’s better to do right on the internet , instead of thinking that you can get away with doing unethical things, then at a later date start bragging about it.
You mean something like Asperger? That’s half the internet right there, and I don’t mean that as an insult like “morons”. I mean, I honestly think certain types really do have something going on in their heads. Disorders of all sorts.
The other thing is, sitting infront of a screen, day after day after day, you get desensitized and dissociate people being actual people when dealing with people through text/online. Some may never have done anything noteworthy “bad” offline, others might still. Look at John D. Carmack, smart guy, but was arrested as a kid and someone noted him as having “no empathy for other human beings”.
Since Warren Buffet got a hold of Bill Gates, he has alot of empathy for people now.
If you think it’s scary to have a cop’s gun trained on you, imagine instead a twitchy, paranoid criminal. Much scarier.
sounds like this kids world is starting to fall apart. sounds like he’s got enemies on all sides of the game, and it’s only a matter of time before law enforcement steps in. kinda sounds like he knows his days are numbered.
hopefully if/when he gets in legal trouble he can bounce back and turn his life around. hate to see someone at such a young age struggle later in life due to mistakes they made in their youth.
I’m sorry, but at 20, i knew what was right and wrong and illegal, thanks the long forgotten art of PARENTING. At 20, I knew what I was doing when I did something wrong or illegal, and did it knowing there were consequences that I might have to pay, including prison time.
Time to pay the piper, none of this “oh he made some mistakes in his youth, I hope he bounces back”. Make an example of these adults (at least in the eyes of the law, not by their common sense).
I agree, it’s that kind of soft attitude that encourages things to get to the state they are now. Even now his dad is defending him instead of dealing with it properly. No wonder the guy doesn’t understand responsibility if his dad is acting like an idiotic mate instead of a parent.
If anything now happens with the law then he brought it on himself. Seemingly he learned nothing from the time before with Mat because he got let off with it back then too. I’m pretty sure he’ll get away with it anyway though and in another 6 months some other victim will have to suffer when his ego needs inflating again.
RIP Phobia, we hardly knew ye.
Congrats on making an example of this guy, Krebs. Hopefully the rest of the scene will learn something from him.
To any wannabe hackers reading this: You cannot hack, and you will never be able to hack. SE is not hacking. DDOS is not hacking. You have not read or written a single line of code in your life and you deserve what’s coming to you.
There are plenty of 40+ hackers out there, most of them have gotten over their mischief phase (*most*) and moved on to hacking as a career. (Engineers, pen-testers, security experts and more.)
Those who still seek the thrill of mischief are less likely to be the type who seek attention and titles like “TheGod” or outside validation. They may have a small tight-knit group of friends with whom they hack, or against whom they hack some times.
Wargames for the wise and aged legions.
The younger crowd, are just like any crowd of misspent youths. Rebelling against the system, seeking acceptance, etc.
But it’s this yearning for recognition as an “Elite” hacker that gets you caught. Become known, become a target.
It’s hard to tell much about this guy’s psyche from the phone call. It doesn’t strike me as the behavior as someone who would best be dealt with by a long prison sentence.
Adolescents typically underestimate risk and overestimate benefits, as in, “Let’s do this. It will be fun. It’s no big deal.” They may know intellectually that they are putting people at risk, but they don’t accurately assess how bad what they’re doing is. A lot of teenager problems work themselves out in a couple years just from normal progression of maturity.
I’m dating myself, but I remember the day when males were not considered adults until age 21, four years older than females (eg., for entering into things like marriage). There’s some developmental justification for that. It wasn’t lowered to 18 until people complained about guys being drafted when they weren’t allowed to vote — so the age of majority was lowered, rather than the draft age being raised.
Based on the information read on this blog, Dad is an enabler, suspending his disbelief of the blatant stories and excuses Sonny is telling, therefor complicit in the crimes.
IMHO, both have earned serious consequences. Time to pay the penalties.
Too bad BK did not archive more of the evidence before the phone call. I think I would have.
I will be pleased to learn when the skiddies and enablers get what ‘real time’ is coming to them.
KUDOS to BK !!
Don’t worry – one National Security Letter to Google and the FBI will have copies of all the deleted YouTube videos.
NSA archives every bit ever transmitted… 😉
…, and spending money on a ‘stolen’ credit card is a crime, is it not !!
Yeah they’re going to get what they deserve pretty soon.
The reason you don’t hear of old hackers getting busted is because they are not looking for rep.
They are not looking to brag about what they did, can do, or getting ready to do.
They don’t want to be part of any group.
They would rather people think they’re completely clueless when it comes to technology.
Posting videos of whoever being jacked and tweeting daily actions is not flying under the radar.
These kids with their over inflated egos don’t realize their hacker rep or whatever you want to call it is the reason they’re getting busted. It’s a good thing because they’re breaking the law.
The best hackers are well actually we don’t know who they are or even what their alias is and that’s why they’re the best.
Oh well I guess it does not matter in this case which is good for you. Now the morons can be sent up the river to reflect on their choices in life.
Excellent article that was enjoyable to read… Looking forward to the updates add they happen. Seems the problem with these script kiddies its they truly don’t understand their actions have non virtual consequences (real life). We’re in this weird period in time where our virtual and physical worlds are linked to so many services we use for the first time. Will be interesting in 20 years to read about these times and see what we think of them in past tense.
I’m a little disappointed that you did not download and save those videos off YouTube.
I’m pretty sure if push comes to shove LE will be able to get deleted content from various providers. Perhaps there is something akin to the wayback machine for this? If not, I guess that’d be a good thing to start, surely it’d come in handy to have a copy of video from there that some folks take down…muahaha! ;oP
Actually, I’m not pretty sure….I’m hopeful. Ha. Funny how easily I used that term without thinking of the weigh of the true meaning…
They can get deleted videos no problem. They’re not actually deleted. Just removed from the public facing servers. The vids should be retrievable for several months afterwards.
Topsy has a good history of his tweets http://topsy.com/twitter/phobiathegod?nohidden=1&page=1
I was a big Topsy fan, right up until they started wanting me to pay to use their API…
Using Twitter and trying to keep your identity a secret seems incompatible. The more you Tweet, the bigger trail you leave to be tracked down.
What about “favourited” Tweets? If Favourited Tweets get deleted are they really gone or do they show up forever in the person who favourited them’s list of Favourite Tweets?
? http://www.google.com/imgres?q=%40PhobiaTheGod&hl=en&biw=1366&bih=620&tbm=isch&tbnid=lT303A9kbnwB-M:&imgrefurl=https://twitter.com/PhobiaTheGod/status/291818151577006080&docid=BSjLVSMD6-8HkM&itg=1&imgurl=https://si0.twimg.com/profile_images/3034215276/8d04b11b2470d1bdb447a168a7609346_normal.jpeg&w=48&h=48&ei=vI5IUaSUJKen0AXD0oHADA&zoom=1&sa=X&ved=0CHAQhBwwCg&ved=1t:3588,r:10,s:0,i:112&iact=rc&dur=936&page=1&tbnh=48&tbnw=48&start=0&ndsp=33&tx=23&ty=23
Interesting take on the possible punishment for this guy from Robert Pegoraro:
http://sulia.com/channel/information-security/f/0ca4db13-0c81-4762-b8b2-5bf072cd72ea/?source=twitter
“With the precedents set above, we basically have to go for the death penalty, right?”
Krebs, you’re amazing. This kid is done.
As far as him deleting the YouTube videos: These can be easily recovered by Google. These videos are never, ever permanently deleted from their servers, only the public links are removed. If law enforcement or your lawyers get involved, make sure you subpoena Google for the videos. If by same crazy fate, they actually did lose those videos, they are certain to have logs of who posted what and when. These should also be under subpoena
by your lawyers/law enforcement.