Not long ago, miscreants who wanted to buy an exploit kit — automated software that helps booby-trap hacked sites to deploy malicious code — had to be fairly well-connected, or at least have access to semi-private underground forums. These days, some exploit kit makers are brazenly advertising and offering their services out in the open, marketing their wares as browser vulnerability “stress-test platforms.”
Aptly named after the river in Greek mythology that separates mere mortals from the underworld, the Styx exploit pack is a high-end software package that is made for the underground but marketed and serviced at the public styx-crypt[dot]com. The purveyors of this malware-as-a-service also have made a 24 hour virtual help desk available to paying customers.
Styx customers might expect such niceties for the $3,000 price tag that accompanies this kit. A source with access to one Styx kit exploit panel that was apparently licensed by a team of bad guys shared a glimpse into their operations and the workings of this relatively slick crimeware offering.
The Styx panel I examined is set up for use by a dozen separate user accounts, each of which appears to be leveraging the pack to load malware components that target different moneymaking schemes. The account named “admin,” for example, is spreading an executable file that tries to install the Reveton ransomware.
Other user accounts appear to be targeting victims in specific countries. For example, the user accounts “IT” and “IT2” are pushing variants of the ZeuS banking trojan, and according to this Styx panel’s statistics page, Italy was by far the largest source of traffic to the malicious domains used by these two accounts. Additional apparently country-focused accounts included “NL,” AUSS,” and “Adultamer” (“amer” is a derisive Russian slur used to describe Americans).
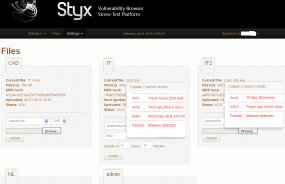
ZeuS Trojan variants targeted at Italian victims were detected by fewer than 5 out 17 antivirus tools.
An exploit kit — also called an “exploit pack” (Styx is marketed as “Styx Pack”) is a software toolkit that gets injected into hacked or malicious sites, allowing the attacker to foist a kitchen sink full of browser exploits on visitors. Those visiting such sites with outdated browser plugins may have malware silently installed.
Unlike other kits, Styx doesn’t give a detailed breakdown of the exploits used in the panel. Rather, the panel I looked at referred to its bundled exploits by simple two-digit numbers. This particular Styx installation used just four browser exploits, all but one of which targets recent vulnerabilities in Java. The kit referred to each exploit merely by the numbers 11, 12, 13 and 32.
According to the considerable legwork done by Kafeine, a security blogger who digs deeply into exploit kit activity, Styx Kit exploit #11 is likely to be CVE-2013-1493, a critical flaw in a Java browser plugin that Java maker Oracle fixed with an emergency patch in March 2013. Exploit 12 is almost certainly CVE-2013-2423, another critical Java bug that Oracle patched in April 2013. In an instant message chat, Kafeine says exploit #13 is probably CVE-2013-0422, a critical Java vulnerability that was patched in January 2013. The final exploit used by the kit I examined, number 32, maps to CVE-2011-3402, the same Microsoft Windows font flaw exploited by the Duqu Trojan.
The Styx stats page reports that the hacked and malicious sites used by this kit have been able to infect roughly one out of every 10 users who visited the sites. This particular Styx installation was set up on June 24, 2013, and since that time it has infected approximately 13,300 Windows PCs — all via just those four vulnerabilities (but mostly the Java bugs).
One very interesting pattern I observed in poking at this exploit pack — and 0thers recently — is the decreasing prevalence or complete absence of reported infections from Google Chrome users, and to a lesser extent users of recent versions of Mozilla Firefox. As we can see from the graphic at the top of this blog post, users browsing with Microsoft’s Internet Explorer made up the lion’s share of victims.
This Styx installation reports installing malware on systems of just a handful of Firefox users, and against not a single Chrome user. In fact, the author of this kit freely states in a Q&A from an underground forum sales thread that his kit doesn’t even work against Chrome. For a complete breakdown of victims by browser and operating system, see this graphic.
Kafeine said he, too, has noticed a pronounced shift in the browser breakdowns from different exploit kits.
“Not many exploit kits [perform] very well against Chrome,” Kafeine said, noting that both Chrome and Firefox both now include integrated PDF readers, and that exploits against Adobe’s PDF reader have traditionally been a key contributor to exploit kit infection statistics.
Kafeine said one malware gang whose work he has followed — an organized crime crew that uses the Gameover ZeuS variant — doesn’t even attempt to infect Chrome users who wander into its malware traps. Instead, those users are hit with a social engineering attack that tries to trick them into installing the malware by disguising it as a Chrome browser update.
“Those users are automatically redirected to a fake Chrome update page,” Kafeine said.
For more details on Styx and the different flavors of this exploit kit that have emerged in recent months, check out these blog posts:
Styx Exploit Kit Takes Advantage of Vulnerabilities
Styx Exploit Kit Analysis – Building a Bridge to the Underworld



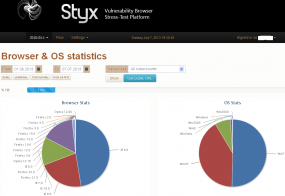

The statistics look pretty promising indeed – users of modern browsers are far less affected by exploits now. It seems that Chrome no longer allows Java to run automatically, that should be the reason why the exploits don’t work. As to the modern Firefox versions – vulnerable Java versions are blacklisted which should be sufficient to reduce the number of infections significantly. Firefox 3.x has this feature as well but my guess is that users still on these outdated versions likely have some kind of misconfiguration that also prevents the blacklist from working correctly.
Yeah that’s right about chrome and java but that needs to be configured and is not inbuilt by default.I have tried disabling java in chrome and most of the sites stopped responding only!!!!thats the kind of java dependency today!!!regards,,,,anupam
I think you’re muddling up Java and JavaScript.
The concept of selling illegal merchandise as completely legitimate products isn’t such a new concept though.
A good physical-world example would be ‘Bath Salts’, basically designer drugs that are chemically similar to drugs like cocaine, but sold ‘legitimately’ as actual bath salts. The users ‘consume’ this product in many ways except for putting it in their bath!
The key is where to draw the line between malicious and legitimate functionality which can be complicated especially with security compromising programs.
Actually “bath salts” and the myriads of other “designer drugs” (a term that is much more apt when applied here rather than illicit substances that took off in the ’80s and ’90s) that are put onto the market these days aren’t illicit, at least not at first.
That’s why the the compounds are created in the first place and why they’re sold openly.
Very informative and valuable insight. Thanks Brian. You do us a great service.
28 of 27 linux users refused the malware
just LOL, funny styx!
good job krebs
Although FF is not as secure as Chrome but I love the extensions I can get for it. To see that it is fairly secured is good. I quit using IE for anything else than Win update and sites that only work with IE. I no longer have Java installed at all. If a site absolutely need Java, I just won’t use it. I know this isn’t an option for a lot of folks. In the long run, Java will be fixed/strengthen like anything else and the hackers will move onto something else to hack.
Now and days the miscreants are using spam to hawk their wares. It’s that easy to get now and days.
The interesting point in this article is how both Firefox and Chrome have less of a prevalence in malware infection by way of a drive -by-download Just last Friday, Firefox along with AVG stopped a Java drive-by-download on my Windows 8 machine. It appears that a malicious advertisement on a website was serving up this junk.
Great article , proves yet again that using third party browsers helps prevent malware infection.
It seems weird to me that some exploits used to work in Chrome, but apparently they stopped “exploiting” them.
Does anybody know why? If Google monitors everything Chrome does, could it be that Chrome is avoided because nobody want to be on the blacklist of Google Safe Browsing? – because that will probably kill their business model..
The chart indicates that Firefox 23, 24, and 25 have been hacked. However, the most current version is 22.
The chart also makes it clear that we should all switch to Windows 95 or ME! 🙂
Way ahead of you. That’s my defense. Use an operating system that no one wants to exploit 🙂
Domo Arigato, PC Roboto ?
Beyond my control, We all need control,
I need control, We all need “browser control”
It would be interesting to relate the numbers shown for different browsers vs. the quantity of them in use.
I.e. what percentage of the different browsers in use were “attacked” both successfully and unsuccessfully. (Or is that in the graphics and I missed it ?).
Also, what would be statistics for Firefox used with NoScript vs. without it.
In any case, fascinating information. Thanks, Brian.
FYI, the PDF reader in Firefox uses JavaScript instead of C++.
Once people begin using application whitelisting these exploit kits will no longer be relevant. Enterprises are slowly moving toward it with products like bit9 and lumension etc and i have seen kaspersky has a cloud reputation feature now too that will stop most untrustworthy exe’s from launching in the first place, i think the other av vendors are slowly catching up, surprisingly even avira hasnt cottone’d on to this new paradigm yet and they used to have the best catch rate.
I have tinkered with it quite a bit over the last 2 years, it is far from a perfect solution. It does work quite well, but getting the right rules in place and making it so nobody screws them up is a challenge. There are a lot of applications that are simply poorly designed which further complicate matters – Symantec AV has been a mess to try to accomodate as it changes 50 files a day in multiple locations.
Hmm it looks like your website ate my first comment
(it was super long) so I guess I’ll just sum it up what I wrote and say, I’m thoroughly enjoying your blog.
I as well am an aspiring blog blogger but I’m still new to the whole thing. Do you have any suggestions for inexperienced blog writers? I’d definitely appreciate it.