Federal authorities in New Jersey announced a series of arrests and indictments of 14 individuals thought to be connected to an online one-stop shop selling embossed, counterfeit credit cards and holographic overlays.
According to documents released by prosecutors in New Jersey and North Carolina, the men ran or otherwise profited from the Web site fakeplastic[dot]net, which specializes in selling high-quality, custom-made counterfeit credit and debit cards, as well as holographic overlays used to create fake driver’s licenses.
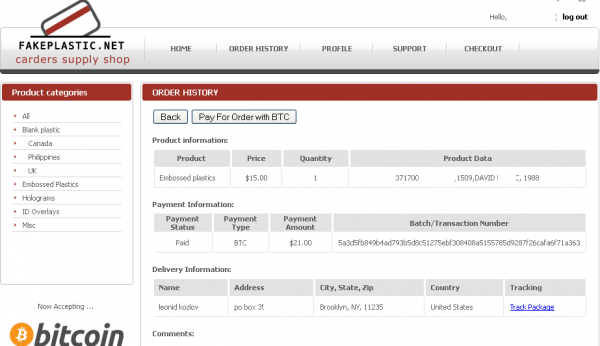
![A customer's purchases from fakeplastic[dot]net, which federal authorities secretly seized on Dec. 5, 2013.](https://krebsonsecurity.com/wp-content/uploads/2014/01/FakePlastic-600x319.png)
A customer’s purchases from fakeplastic[dot]net, which federal authorities secretly seized on Dec. 5, 2013.
The FBI and the U.S. Postal Investigative Service began investigating fakeplastic[dot]net in January 2013. Charged with running the site is 39-year-old Sean Roberson of Palm Bay, Fla. Investigators allege that Roberson began selling counterfeit cards in April 2011, and launched the site in June 2012. Since then, Roberson and two accomplices fulfilled orders for approximately 69,000 counterfeit cards — both embossed and unembossed; more than 35,000 holographic stickers used to make counterfeit cards appear more legitimate; and more than 30,000 state identification card holographic overlays. All of the orders — 36,000 parcels in total — were shipped by the site to customers via the U.S. mail.
Using a conservative estimate of loss of $500 associated with each counterfeit payment card (derived from the federal sentencing guidelines estimation of loss associated with stolen payment card information), prosecutors estimate the losses associated with just the counterfeit payment cards trafficked by Roberson and his conspirators at more than $34.5 million. The complaint against Roberson alleges that he personally made more than $1.7 million from the scheme.
According to the Justice Department, fakeplastic[dot]net was used by various groups of criminals across the country often referred to as “carding” or “cash out” crews. These crews buy stolen payment card numbers and related information – referred to as “track data” or “dumps” – which typically appear on the magnetic stripe on the back of legitimate payment cards. Illegal vendors of that information usually get it through hacking or skimming operations involving the installation of specialized equipment at ATM locations or point-of-sale terminals. The stolen data is ultimately put on a blank card and used to make unauthorized transactions.
“More sophisticated cash out operations use custom-made counterfeit payment cards embossed with the same account numbers that have been encoded on the back of the card, and often acquire fake identification cards in order to reduce the likelihood of detection from law enforcement,” reads a press release issued Thursday by New Jersey U.S. Attorney Paul J. Fishman and U.S. Attorney Anne M. Tompkins for the Western District of North Carolina. “The criminal underground has evolved from fractured, regional operations to an Internet-based market where buyers and sellers across the globe can advertise, purchase and transmit stolen track data. The fakeplastic website brought the physical tools needed by cash out operations to the world of e-commerce, as it eliminated the need for crews to purchase expensive hardware.”
The Justice Department says that by December 2013 — when federal agents quietly assumed control over fakeplastic[dot]net, the site had more than 400 members. Members with access to the fakeplastic website and seeking to purchase counterfeit payment cards could browse the website’s available counterfeit card templates. Members could then choose whether to input specific information to be embossed on the cards and whether they wanted additional authentication features – such as holographic stickers.
OPSEC IS HARD; LET’S GO TO DOLLYWOOD!
As is the case with many an online scam operation, the whole thing falls apart when key members fail to exercise proper operational and personal security habits. After assuming control over the card shop, federal agents made purchases through the site to learn more about the service’s shipping methods. According to charging documents, investigators confirmed that the Fakeplastic Click-N-Ship account used to generate the tracking number associated with the undercover purchases was registered to a “Sam Adams,” with a mailing address for a university in Florida, and that the email address associated with this account was budlighthouse@gmail.com (the “Budlighthouse Gmail Account”).
After obtaining a warrant to inspect that Gmail account, federal investigators discovered that all of the Web site’s order emails were sent to this address and to the address platplus@tormail.net. Tormail is a hidden service on the Tor darkweb network that allows users to send and receive email anonymously to addresses inside and outside of Tor, an anonymity network that is not reachable from the regular Internet and requires the use of special software to reach.
Interestingly, the feds used information gleaned from an incident last summer in which federal agents compromised TorMail as part of an investigation into a child pornography network. To wit:
Between July 22, 2013 and August 2, 2013, in connection with an unrelated criminal investigation, the FBI obtained a copy of a computer server located in France via a Mutual Legal Assistance Treaty request to France, which contained data and information from the Tormail email server, including the content of Tormail e-mail accounts. On or about September 24, 2013, law enforcement obtained a search warrant to search the contents of the Platplus Tormail Account, which resided on the seized Tormail server.
A key component of this investigation came from other federal actions and investigations, including the takedown of the ShadowCrew underground Web site, and the arrest of the alleged founder of Liberty Reserve, a virtual currency that went belly-up last year. When Liberty Reserve was seized by the feds, fakeplastic[dot]net switched to accepting payments via Bitcoin.
This is significant because investigators found that the Budlighthouse Gmail account contained a number of emails from Mt. Gox, a widely used Bitcoin exchanger.
“On or about August 27, 2012, the Budlighthouse Gmail Account received two withdrawal confirmation emails from Mt. Gox indicating that certain withdrawals were made from the IP address 97.104.141.223 (the “Budlighthouse IP Address;’).”
Investigators subpoenaed Time Warner Cable for the customer records related to that Internet address, but the ISP said it no longer had those records. So, authorities turned to Amazon because they noticed that Roberson had an Amazon account, and they tied both the purchases and references to items purchased in the Budlighthouse account to that same IP address. A subpoena to Amazon showed the account was registered to a Sean Roberson in Palm Bay, Fla., and that Roberson had purchased a number of items commonly used to make fake identification cards.
Failing to separate one’s online criminal activities from one’s personal affairs is Opsec Fail 101. And nowhere was this illustrated more clearly than in a ill-fated vacation that authorities say Roberson took at the end of 2012. According to investigators, Roberson closed his card shop from Dec. 22, 2012 through January 4, 2013, with a notice to customers stating, “Will respond to your message when I return from vacation. Sorry for the inconvenience, but I need an escape also :)”.
In August 2013, investigators subpoenaed the credit card records of Roberson’s wife, and found a trail of purchases showing that the couple had traveled to Dollywood during that Christmas break, beginning on Dec. 22. The same records showed that by Jan. 6, 2013, the Robersons were back in Palm Bay, Florida. “Law enforcement also identified a photograph of Sean Roberson with his wife and others in Dollywood, posted on the Facebook page of Roberson’s mother.”
Roberson’s mom wasn’t hard to find, once one has located Roberson’s Facebook and Google Plus pages. Here’s the picture in question:
More information on this case is available in the charging document against Roberson, posted here (PDF).



![The proprietor of fakeplastic[net] announces temporary closing of the shop.](https://krebsonsecurity.com/wp-content/uploads/2014/01/fakecardsmessage-285x94.png)


Another great report!
But was wondering why the snowman’s face is not blurred out.
The snowman was indicted too… on some COLD CASE!! (*rimshot*)
😀
I guess you could say…
(•_•)
( •_•)>⌐■-■
(⌐■_■)
Those plans got put on ice…
YYYYYEAAAAAAAAAHHHHHH!!
Originally the snowman was also going to be prosecuted, but now those plans have been put on ice.
The snowman’s lawyer is suing over the chilling effect his picture will have on other informants… 😀
There must have been some magic in that
old Black Hat they found
For when they placed it on his head
he began to dance around.
Thumpity thump thump
thumpity thump thump
Look at Frosty go!
I knew it! frosty@frosty, it all makes sense now!
Ulbricht is innocent. The real Dread Pirate Roberts is the snowman at DollyWood!
In court, the judge told the lawyer his case did not stand a snowball’s chance in hell of winning and threatened to throw his client into the cooler.
hehe.. I wondered the same.
I was thinking the same thing. Now everyone knows it’s Frosty.
LOL, to all of the funny posts!
On a serious note: Was any evidence publicized that this guy had taken any of the payment card numbers from Rescator? Yes, there are likely many more sites than that one to take from, so I acknowledge that the odds aren’t great. But it’d be an interesting coincidence if it turned out he did use numbers from Rescator, and possibly the Target breach.
There is no evidence in the documents suggesting this, and since the bust took place in early December (with the feds running the site for a while), I suspect that there may have been some buyers of Rescalor’s dumps who wanted to use this service, but, well…
Good info.
Yes, given the timing, that sounds like the right conclusion to draw.
Thanks.
Who does this and figures they won’t ever get caught? I could almost understand the logic of working locally – at one time, it was possible to buy any kind of photo ID, driver’s license or social-security card from MacArthur Park on the edge of Los Angeles. At least if you’re going to engage in criminal activity, do it cash-only, face-to-face. Mail order fraud, or anything involving the wiring of money, will send you to Club Fed for the rest of your life.
Heck, Fedex or UPS and he’s looking at way less trouble.
Yeah, that way you get to meet the Feds face to face.
http://imgur.com/ea6F1wd
What is more important to me was FBI confirmed Tormail seized.
This. Which is what I was trying hard to make people listen to when this story first came out last year. This won’t be the last time this cache will be used, and it’s probably already been used for other things.
Funny thing about the USA justice system — not allowed to supposedly “take” evidence — but if they “obtain” evidence, however obtained, they are allowed to use it in other cases. This should have never been allowed to happen at TorMail to begin with — I believe there is an ‘explicitness clause’ to search warrant and surveillance requests. I suspect this was able to be bypassed because the server was located in France. I am sure there are other ‘ownership’ issues from TorMail’s side of things. Were they noticed, and to what extent were they given notice of this ‘imaging’? And what means did the USA use to trace back the onion to make the request certainly should give pause to people who believe only NSA has such technology.
You can bet that the ‘carder forum’ sqldump leaks have been used a lot as well. Refer to contact-chaining also.
A lot of activists use(d) TorMail, from all countries around the world, as did people who just liked privacy, but as privacy is becoming practically outlawed in the US and thus in the rest of the world, I am sure there will be a lot of metadata analysis of people who used the service, because you know — National Security!
Hard labor, somewhere in Central Florida with no sea breezes and lots of ‘gators….
In the broader scheme of things, this guy seems like small potatoes. I wonder how many others like him are still out there.
It amazes me that he thought he wouldn’t get caught. One screwup and you are done for.
I love how the Feds quietly took over the site and then probably made a naughty list and gathered evidence of everyone who visited it while they were gathering evidence. I expect there will be some more fallout from this investigation.
Benjamin – In reading the Amended Complaint that Brian linked at the bottom it looks like the fallout has already fallen:
“Upon receiving these orders, the USPIS, in coordination with federal, state, and local prosecutors’ offices around the country, conducted over 30 controlled deliveries, leading to 11 additional arrests and the seizure of approximately 3 counterfeit payment card plants.”
Nice take down by law enforcement!
As a former small business owner who had to be on constant lookout for credit card fraud and as a cardholder who recently spotted a $490 fraudulent charge on my debit card account I hope the judge throws the book at these criminals!
Unfortunately, its a numbers games with these crooks and there will be more security issues revealed leading to more-and-more fraud. Until the U.S. implements a more secure system like chipped cards or whatever technology it takes to outwit these criminals they will pop up faster than they get closed down all around the globe.
I am very shocked at this news. I had no idea that Dollywood was still in business. Thanks Brian for digging this up.
goes to Alice Young!
FBI very busy yesterday… LA:
Two California Men Arrested in E-Mail Hacking Scheme…
– http://www.fbi.gov/losangeles/press-releases/2014/two-california-men-arrested-in-e-mail-hacking-scheme-that-yielded-nude-photos-that-were-posted-on-revenge-porn-website
Jan 23, 2014
.
Another fantastic report from Krebs. Not the same old homogenized news stories – real journalism. Keep up the great work! Please…
Now that LR is down and the Feds are presumably exploiting everything they’ve seized, what is the new coin of the shyster realm?
I’m sure that something has popped up in it’s place and I really don’t want to get anywhere near their nasty world.
Post LR, its been Bitcoin on the western side (thats what these guys shifted to). The Russians still use WebMoney, which hasn’t been touched.
Of course, moving real amounts of Bitcoin to cash is a real problem, there was a great article/interview in dailydot with Nod of silk road:
http://www.dailydot.com/crime/silk-road-confession-steven-sadler-nod/
The most interesting thing to me was the effort it took to turn $60K of BTC into dollars: either hundreds of polish debit cards at ATMs, or localbitcoin transactions involving suitcases of cash exchanged at a Vegas casino. The article makes selling drugs seem easier than turning the resulting BTC to actual money.
Brian has done a lot of research on LR and Silk too:
http://krebsonsecurity.com/tag/liberty-reserve/
http://krebsonsecurity.com/tag/silk-road/
FYI, The link I posted earlier is to an updated photo with the snowman’s face blurred out. I totally understand being f-ing paranoid about clicking on unfamiliar links on message boards, posted by insane lunatics like me.
I thought the snowman was the FBI agent tracking Roberson in disguise.
Email Notify
i found FBI estimates ridiculous .
I don`t think it cost 500 $ to make or replace a card , why are they saying – conservative estimate of loss of $500 associated with each counterfeit payment card ?
What losses are they talking about ? Imaginable losses ? Does FBI have a proof that every single one of them cards will be used fraudulently and not by some art project or for educational purposes or for something else like a door stop or something else for that matter , plastic cards have many useful futures if you ask me and not all of them are illegal . sometimes i use my as a window scraper , sometimes my kids playing with it so it becomes a TOY .
That estimate is based on the average amount that fraudsters generally get out of each card before it gets canceled by credit card issuers. And it’s more or less spot on if one reads the fraud forums regularly.
How can you get 500 $ on average out of a peace of plastic is just beyond my imagination .But i like the idea i give you that brian .If it true then David Copperfield knows noting compare to this guys .
If you have a gun it doesn’t mean that you going to kill someone !!?? or does it ?
Are you not understanding that this is talking about counterfeit credit cards with valid numbers on them that the purchaser can use to buy things with?
I see . So There where numbers printed on them cards !. In that case yes its a cc fraud .If no numbers where ever printed on them cards then its just a counterfeit of a logo .
You know what…If your gun has a serial # on it that is traced by law enforcement to have been stolen you have “a lot of splainen to do”! If you circumvented legitimate channels and thereby knowingly purchased said gun from someone that advertises online in the trafficking of stolen guns, or counterfeiting branded/trademarked guns, you just made yourself an accessory to a crime. Your don’t have to pull the trigger as you already committed a crime. Capiche?
By the way, fraudulent credit card use is not a David Copperfield illusion by any stretch of the imagination. The $500/card fraudulent transaction AVERAGE does not even consider non-monetary losses like time spent responding to the fraud, or any other ancillary out of pocket expenses when a person or business becomes victimized.
If you possess a gun with a stolen serial number on it, you have very little explaining to do. Private party sales are legal, all you have to say is that you bought it at a gun show or a site like arms list.
I was attempting to tie “What What’s” gun analogy to knowingly purchasing stolen Credit/Debit cards as it relates to the scope of this bust. The connection being that they both carry identifying #’s that are tied to specific legitimate owners of those goods. Not to turn this comment into a “gun rights” debate…but even after a short explanation to law enforcement of how you innocently came into possession of a stolen firearm it still would still be confiscated and hopefully returned to the rightful owner regardless of how it was purchased. The buyer then loses his investment. Its always a case of buyer beware. However, if people “knowingly” choose to support the sale of stolen merchandise then they are complicit and part of the problem.
Remember that after Federal Agents assumed control of the FakePlastic Web site and traced orders it led to 11 arrests.
The problem with these 500$ figures extends beyond ‘averages’ as the numbers of cards go up. Not all cards would get used. Not all cards could be used. Not all cards would even be seen probably. Or successfully even pass a fraud check. Does this mean no damages? Of course not. But to attribute a 500$ average to ALL carding instead of SUCCESSFUL carding only works on smaller prosecutions, and should only work when they catch people, as they say in your country, “red handed” — or for the actual amount of fraud, what ever that might be.
There is probably a reason that most of the indictments I have seen from ten years ago only would name 10 or so cards, selected by victims as to where to prosecute. It is easier to prove actual harm. Figures now are so grossly overinflated that numbers in the millions of dollars are tossed to the hungry public when the actual fraud loss amounts are probably closer to 1/10 or even 1/50 of the amount that will often get quoted.
And again, if they were indeed guilty of creating these cards, they have absolutely no value for anything but a piece of plastic until they are used. Clearly if they did make these cards and were shipping them out, they were not intending to use them. Charge the people that would use them. Or would it be illegal for me to get MSR out and put dump of my own card onto a piece of plastic and go to an ATM in the USA? Is encoding something illegal? Shouldn’t the USE of it be what is illegal?
So, if I ran a print shop and was caught by the authorities with stacks of counterfeit $100 bills your saying a plausible defense would be:
“I’m just the printer, these are just pieces of paper with serial #’s (that just happen to match in every detail a real $100 bill)…I haven’t actually used any myself, I haven’t sold them all and of the ones I did sell I sold at a discounted rate! No harm, no foul.”
Surely you jest! Counterfeiting and becoming a party to committing financial fraud, even at arms length, is not going fly in the U.S.
Wow! Usually these guys are from “way over there somewhere.” I guess I never thought I see something this big based right here in Brevard county (other than the usual credit card skimmers being found in Cocoa Beach). Very close to home on this one…
Brian,
Any evidence that these guys were directly involved with the Target or NM breach? Also, have either retailer revealed yet the point of entry for the malware?
Is the website at FakePlastic[dot]biz also involved? It appears to be using the identical logon script with a dedicated IP Address at Amazon and was registered on 2012-02-07 using the registrar PDR LTD. Strangely, FakePlastic[dot]net was also registered on 2012-02-07, also using the registrar PDR LTD. Conscience? I think not! I really hope the Feds are looking into this second website? No mention is made in the FBI press release of the second Domain.
I also instructed Domain Tools to take forensic screenshots of the homepages in the top six TLD’s which are active. The other four TLD’s , both registered and unregistered, don’t appear to be involved and are not that interesting. If you are a registered Domain Tools user, and see a Domain name mentioned in the news, drop by a take s screenshot, you may be helping another investigator in the future.
Why haven’t these Domains been seized and transferred to federal control? This is not normal behavior for federal law enforcement. If my interpretation of what I am seeing is correct, the FBI has been sloppy or there is more going on than has been reported.
due process requires evidence, the best honey pots are those operating in the underverse developing trusted reputations, which is possibly a reason for not shutting down the other sites. Regrettably, there a growing numbers of people like seann with no moral code and no concern for the consequences of his actons on the lives of others, kind of like mall shooters but not as noisy and with far highr victim counts. can we restore the value of maintaining a moral compass? if so, how? if not, then what is our next course of action?
An earlier security breach at Michaels Stores Inc. was solved:
http://www.justice.gov/usao/can/news/2012/2012_03_20_arakelyan.vardanyan.guiltyplea.press.html
According to Sean’s FB page, he likes Nickleback and Mitt Romney.
This chap just gets worse and worse.
Those two are not relevant to money-stealing, information-stealing and impersonation crimes.
But one of his “Other Favorites” is below. One very large reason to keep online gambling from having any access to credit or debit cards for payment anywhere :
Help Make Online Poker Legal in the U.S.,
hxxps://www.facebook.com/legalizepoker
Ha, that post made my day…
Proof he has no soul.
Brian’s reporting on ‘skimming’ has been some of the best I have seen in the last 15 years. In fact, there is far too little reported about this subject. When I use the term ‘skimming’, this includes the cloning and theft of the data to make cloned cards with.
I saw the cloning of credit cards start when I was in the card industry back in the mid 90’s. krebsonsecurity.com has become a leading source of information on this subject which I direct many of my contacts towards.
Card skimming and cloning has changed as much as the PC has changed since 1995 and impressively become one of the #1 financial crime being committed today at an unprecedented level.
This is a crime now committed by large and small groups of organized criminal elements. This has become the new crime of both North American criminal organizations and Eastern European criminal organizations.
Ask anyone working in a law enforcement gang, robbery, fraud or organized crime unit, and ask them who they see committing these crimes in the U.S. They will tell you that the street gangs are now hiring black hat hackers and becoming hackers so they can commit crimes that do not get them thrown in jail for 10 – 30 years right off the bat, just breaking in the front door of a bank or house.
I have been speaking on this subject (among other related subjects) more regularly for the last 4 years. I find it amazing that I can speak in front of some 100+ people and see that the majority have never heard of it, and more over, many walk up too me and have only just realized that they had been a victim of skimming.
Thanks Brian, thanks again for not just focusing on the breaches that get all the attention, but keeping the subjects you cover all over the criminal map.
Brian,
What happened to your site overnight? It was a new format yesterday and then as I logged on this morning it was in the new format, wrote my comment, hit PUBLISH and it refreshed back to the old format???
I like the new format, it was had a much easier flow and function to it.
Were you using a mobile device when you logged in yesterday? I was testing out a new mobile version of the site yesterday but had to turn it off because it was being served to regular desktop users also and I putting up a big story.
Brian,
No sir, I was on my lap top highbred lap top but operating in laptop mode.
Brian – Investigate using a responsive theme, i will solve both desktop and mobile sizing so you don’t experience those issues. you can then later tailor if you want an exclusive mobile user experience.
What’s with the tormail.net email address? I thought they shut down a few months ago with the freedom hosting arrests.
Just as we in the Colonies are planning the big move to chip and pin, some blokes on the other side of the pond are trying to find security methods that are better than chip and pin.
http://www.bbc.co.uk/news/technology-21085738
“Could the chip and pin system have had its day?
In itself, chip and pin technology is not that bad, according to computer security expert Brian Krebs in the US.
“The chip and pin solution is pretty good. It’s not perfect, but a big part of security is about making it more expensive for the bad guys.”
One issue is that it has not been adopted worldwide.
Mr Krebs thinks biometrics are still a long way off.
“I think it’s like leaping six generations ahead,” he said.
“We don’t need to go to biometrics for this.” ”
http://www.bbc.co.uk/search/news/?q=ATM
http://www.bbc.co.uk/search/news/?q=chip%20and%20pin
he was running a pretty profitable online business as it seems …
Crime is always profitable until one gets caught. Ripping off others IP, overhead is low and margins are high.
Good article, I just don’t get posting a “family” photo from a Facebook acct that isn’t his. He is the criminal. Let’s not exploit his family. Yeah, I know you blurred the faces, but come on…