Late last month, hackers allied with the Syrian Electronic Army (SEA) compromised the Web site for the RSA Conference, the world’s largest computer security gathering. The attack, while unremarkable in many ways, illustrates the continued success of phishing attacks that spoof top executives within targeted organizations. It’s also a textbook example of how third-party content providers can be leveraged to break into high-profile Web sites.
The hack of rsaconference.com happened just hours after conference organizers posted several presentation videos from the February RSA Conference sessions, including one by noted security expert Ira Winkler that belittled the SEA’s hacking skills and labeled them “the cockroaches of the Internet.”
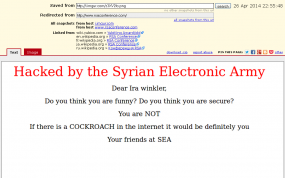
Shortly after that video went live, people browsing rsaconference.com with JavaScript enabled in their browser would have seen the homepage for the conference site replaced with a message from the SEA to Winkler stating, “If there is a cockroach in the internet it would definitely be you”.
The attackers were able to serve the message by exploiting a trust relationship that the RSA conference site had with a third-party hosting provider. The conference site uses a Web analytics package called “Lucky Orange,” which keeps track of how visitors use and browse the site. That package contained a Javascript function that called home to a stats page on a server hosted by codero.com, a hosting firm based in Austin, Texas.
According to Codero CEO Emil Sayegh, the attackers spoofed several messages from Codero executives and sent them to company employees. The messages led to a link that prompted the recipients to enter their account credentials, and someone within the organization who had the ability to change the domain name system (DNS) records for Codero fell for the ruse.
Sayegh said the attackers followed the script laid out in Winkler’s talk, almost to the letter.
“Go look at minute 16 from his talk,” Sayegh said. “It’s phenomenal. That’s exactly what they did.”
Amit Yoran, senior vice president of products and sales at RSA, said the SEA often finds success by exploiting trust relationships between content providers on large Web sites. In short: targets are only as strong as their weakest link.
“Unfortunately, complexity is very often the enemy of security,” said Yoran, emphasizing that he was speaking for RSA and not for the RSA conference Web site, which is a separate entity. “If it’s a content-rich and interactive Web site, it only takes one simple slip for the site to be hacked.”
The SEA has had great success by spoofing the boss and by targeting weaknesses in third-party content providers. Last year, the group claimed credit for defacing the Web sites of Time, CNN and The Washington Post after gaining administrative access to Outbrain, a third-party system that provides “Other stories from around the Web” recommendations at numerous sites. Outbrain later acknowledged that the incident was the result of a phishing attack sent to Outbrain employees that spoofed the company’s CEO.
From my perspective, what’s truly remarkable about these attacks from the SEA is that they could be so much more damaging, and yet this group appears to do little more than use each attack to spread a propagandist message. Unfortunately, malware purveyors don’t care about propaganda, and frequently abuse trust relationships between and among Web sites to spread malicious software.
That so many high-profile Web sites are potentially vulnerable to being hacked thanks to all of the third-party content they serve is the primary reason I advise users not to browse the Web with JavaScript enabled by default. For tips on how to manage JavaScript in the browser, check out my Tools for a Safer PC primer.




Hi! I simply wish to give you a big thumbs up for your great info you’ve got here on this post.
I’ll be coming back to your website for more soon.