The Lizard Squad, a band of young hooligans that recently became Internet famous for launching crippling distributed denial-of-service (DDoS) attacks against the largest online gaming networks, is now advertising its own Lizard-branded DDoS-for-hire service. Read on for a decidedly different take on this offering than what’s being portrayed in the mainstream media.
The new service, lizardstresser[dot]su, seems a natural evolution for a group of misguided youngsters that has sought to profit from its attention-seeking activities. The Lizard kids only ceased their attack against Sony’s Playstation and Microsoft’s Xbox Live networks last week after MegaUpload founder Kim Dotcom offered the group $300,000 worth of vouchers for his service in exchange for ending the assault. And in a development probably that shocks no one, the gang’s members cynically told Dailydot that both attacks were just elaborate commercials for and a run-up to this DDoS-for-hire offering.
The group is advertising the new “booter service” via its Twitter account, which has some 132,000+ followers. Subscriptions range from $5.99 per month for the ability to knock a target offline for 100 seconds at a time, to $129.99 monthly for DDoS attacks lasting more than eight hours.
In any case, I’m not terribly interested in turning this post into a commercial for the Lizard kids; rather, it’s a brain dump of related information I’ve gathered from various sources in the past 24 hours about the individuals and infrastructure that support the site.
In a show of just how little this group knows about actual hacking and coding, the source code for the service appears to have been lifted in its entirety from titaniumstresser, another, more established DDoS-for-hire booter service. In fact, these Lizard geniuses are so inexperienced at coding that they inadvertently exposed information about all of their 1,700+ registered users (more on this in a moment).
These two services, like most booters, are hidden behind CloudFlare, a content distribution service that lets sites obscure their true Internet address. In case anyone cares, Lizardstresser’s real Internet address currently is 217.71.50.57, at a hosting facility in Bosnia.
In any database of leaked forum or service usernames, it is usually safe to say that the usernames which show up first in the list are the administrators and/or creators of the site. The usernames exposed by the coding and authentication weaknesses in LizardStresser show that the first few registered users are “anti” and “antichrist.” As far as I can tell, these two users are the same guy: A ne’er-do-well who has previously sold access to his personal DDoS-for-hire service on Darkode — a notorious English-language cybercrime forum that I have profiled extensively on this blog.
As detailed in a recent, highly entertaining post on the blog Malwaretech, LizardSquad and Darkode are practically synonymous and indistinguishable now. Anyone curious about why the Lizard kids have picked on Yours Truly can probably find the answer in that Malwaretech story. As that post notes, the main online chat room for the Lizard kids (at lizardpatrol[dot]com) also is hidden behind CloudFlare, but careful research shows that it is actually hosted at the same Internet address as Darkode (5,38,89,132).

A suggested new banner for this blog from the jokers at black hat forum Darkode, which shares a server with the main chat forum for the Lizard kids.
In a show of just how desperate these kids are for attention, consider that the login page for LizardStresser currently says “Hosted somewhere on Brian Krebs’ forehead: Donate to the forehead reduction foundation, simply send money to krebsonsecurity@gmail.com on PayPal.” Many of you have done that in the past couple of days, although I doubt as a result of visiting the Lizard kids’ silly site. Anyway, for those generous donors, a hearty “thank you.”
It’s worth noting that the individual who registered LizardStresser is an interesting and angry teenager who appears to hail from Australia and uses the nickname “abdilo.” You can find his possibly not-safe-for-work rants on Twitter at this page. A reverse WHOIS lookup (ordered from Domaintools.com) on the email address used to register LizardStresser (9ajjs[at]zmail[dot]ru) shows this email has been used to register a number of domains tied to cybercrime operations, including sites selling stolen credit card data and access to hacked PCs.
A more nuanced lookup at Domaintools.com using some of this information turns up additional domains tied to Abdilo, including bkcn[dot]ru and abdilo[dot]ru (please do not attempt to visit these sites unless you know what you’re doing). Another domain that abdilo registered (in my name, no less) — http://x6b-x72-x65-x62-x73-x6f-x6e-x73-x65-x63-x75-x72-x69-x74-x79-x0[dot]com — is hexadecimal encoding for “krebsonsecurity.”
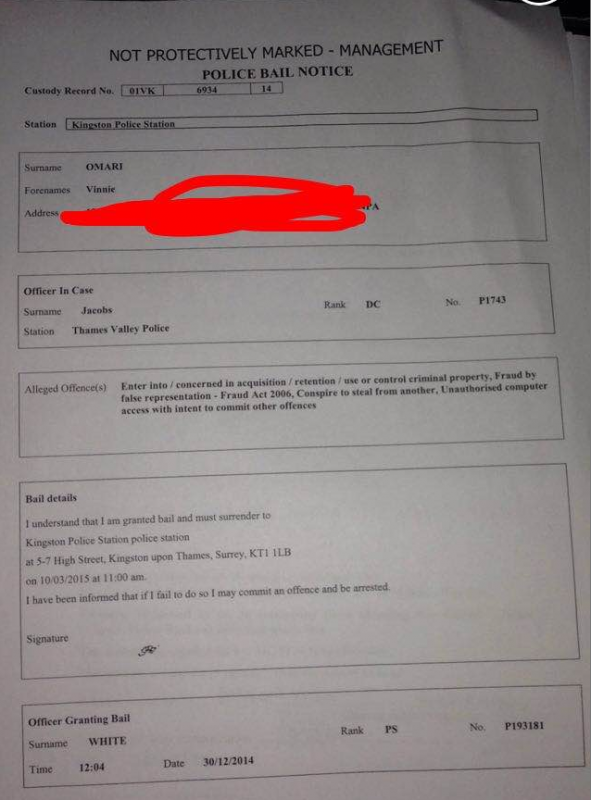
Last, but certainly not least, it appears that Vinnie Omari — the young man I identified earlier this week as being a self-proclaimed member of of the Lizard kids — has apparently just been arrested by the police in the United Kingdom (see screen shot below). Sources tell KrebsOnSecurity that Vinnie is one of many individuals associated with this sad little club who are being rounded up and questioned. My guess is most, if not all, of these kids will turn on one another. Time to go get some popcorn.
Happy New Year, everyone!



Yuk, 217.71.50.0/24 is definitely a sewer. Worth blocking.
Another great article Mr. Krebs!
Can’t wait to hear what’s going to happen with the Finnish kid, after he deleted his Facebook and all (as of a few days ago)!
What happens first, the ball drops or one of these guys rats on the other? Funny stuff!
Well they’re still around so ya. Anyway the only piece of information I found interesting was about the titanium source. This information fits perfectly with what I already knew with 99% percent on another member of lizard squad not listed anywhere publicly. He took down the website l, made by themuddfamily (Adam Mudd) which was first advertised on the website nodusgriefing.com (a forum about a minecraft griefing team, if you look back at most of these people they will have histories involving minecraft.) Now if you take a look at who breached the website and going on some other information, such as the names chfthecat and KMS, we arrive at the group known as DerpTrolling. In surprising you Krebs or any other news outlets have not realized that core members of but groups are the same, with the exception lizard squad has more people.
I can go into more detail and provide more proof if needed and Krebs I can give you some interesting stories (that is of course if this comment doesn’t say “awaiting moderation”)
If they really are being rounded up, it’s a wonderful late Christmas present. Here’s to a great new year with hopefully one less group of attention seeking kids causing trouble around the net!
You sure are passionate about what you do.
Happy New Year Krabs, hopefully we will see this “kindergarten club” put in jail in the new year
You are the new Santa Claus. Not only do you know if they’ve been bad or good, you know their IP addresses and arrest history.
Super stuff Brian… hope to read more from you on these saddos and other topical stories in 2015. May your blog go from strength to strength.
Brian.
You rule.
Brian, you totally missed out on an opportunity to title this article better: Lizard Kids: A Long Tale of Fail!
Yeah, I played with a lot of headlines. There was so much to choose from 🙂
Jail is no place for a kid,,maybe they can learn to code better and go to work for the gov.
Yeah, the gov’t really wants to hire a bunch of highly unreliable low-skill idiots.
These idiots think that they can get jobs if they get caught, but no one in their right mind is going to hire people like this. They’re untrustworthy and hiring them would be liability. Any and every business would know that. And why even put yourself at risk for a group of idiots that barely know the basics?
Earlier, I considered saying they’d have a lot to prove. You said it better. Potentially worse is highly unreliable high-skill idiots. Hopefully the guidance and insight available to them breaks through before they themselves are through.
@Brian: Do you know of programs that have had success redirecting talent before it washes out?
It amazes me how these idiots think they will get away with it. I’m sure they feel really clever when they figure out how to use a VPN or proxy chain, but they never seem to realise that ISPs communicate and there are no digital borders. It takes years of practice to evade even the most simple forensic examination. Ddosing a multi-billion dollar company, disrupting it’s primary source of income during it’s busiest period will result in a serious criminal investigation. Vinnie actually commented on calling the FBI to ask if they “had an investigation on LizardSquad”…. Fail.
The Anonymous persona was a fitting ascription as it encapsulated the enitiy as a whole. “LizardSquad” is quiet the opposite.
Something to hope for is that they figure out they screwed up, and spend the rest of their lives applying their skills preventing the havoc they caused. Perhaps better, where possible: redirecting up-and-coming’s who may go down the same path.
Too bad we don’t have a ‘Stand your Cyber-Ground’ law…..Keep up the good work Brain.
lizzardstresser.su no longer exists. Sic transit gloria mundi
However, checking the spelling: LIZARDSTRESSER.SU
lila.ns.cloudflare.com.
wesley.ns.cloudflare.com.
REGISTERED, DELEGATED
Private Person
9ajjs@zmail.ru
RUCENTER-REG-FID
2014.12.26
Happy new year!
I’m trying to understand why the OIC ( officer in the case) is from Thames Valley Police. Vinnie obviously lives on Surrey Polices patch so thats why he was taken to the nick in Kingston upon Thames.
His dox show TW post code, Twickenham area. Little posh kid…
This subject is all over the cable news, but they haven’t got the skinny on it like KOS! Great reporting Brian!
HAPPY NEW YEAR! 😀
I’m currently looking through the list of their customers to see how many were stupid enough to use their actual name when they bought the service. I am not at all surprised at the number.
Not to mention the apparent maturity level shown by how many people chose vulgar or racist names.
Keep up the good work.
If you want to fight with Brian be prepare to loose
Great Blog Thanks
Brian,
This is my first comment but I’ve been reading your blog since it has been around. I love the way you have approached journalism and you set the standard on security related reporting.
Sometimes the only way to deal with thugs is by speaking their language. Epic win with this post.
🙂
Their DDoS tool is hosted at txtv.ba, a hosting provider in bosnia. Thanks to cloudflare for telling me that in an email.
Ha sorry i missed the line where you already had that.
Am I the only one who thinks the uploads of his supposed arrest looks like it was made by a 5 year old kid using Photoshop for the first time?
I’ve already seen a few versions of this and they all have the telltale signs of terrible pixelation around the words that tell me they are fakes…and really amateur ones at that.
@Krebs
Something worth looking into is Vinnie’s relationship with viphackforums… I assume my comments never get approved because of the links, so just search anonbin for those terms. Doesn’t seem that this has been reported on elsewhere.
I find it funny how cybercriminals the world over always seem to become obsessed with you, Krebs. It looks like it’ll never end.
If they really didn’t see you as a threat, they wouldn’t mention you at all.
According to Yle (kinda BBC of Finland), “Ryan” has been interrogiated also.
Sadly, no english news on that yet. You have to google translate this:
http://yle.fi/uutiset/poliisi_epailee_ryan_syyllistynyt_torkeaan_tietojarjestelmien_hairintaan__teemme_tiivista_yhteistyota_fbin_kanssa/7714825
I had trouble getting to your site earlier today both on our corp net and my iPhone. i asked a few other to try and they had issues too. The site eventually came up but i had a few strange errors like the server was busy and a database error. May be just us or it coud be the “Fail” guys.
Nice piece of work Brian, thanks for the always entertaining journalistic work!
Happy new year to white hats everywhere!
Good way to end the year, exposing Lizard Squad.
When you said not to visit those links unless you know what you’re doing, I’m curious what that means and what being good enough entails.
Obviously if I have to ask, I’m not good enough, but I’m still intrigued/
I would use a VM that I could roll back and/or a live CD. And just for extra protection, I would make sure I had a firewall between the test machine and anything else I cared about.
Basically you assume that the machine you use to browse to such site would get infected.
Imagine an old fashioned Gang. It has a hideout. When someone knocks on the door and doesn’t provide the secret password / knock sequence, what do you think happens?
1. The person knocking is assumed to be antagonistic to the gang.
2. The gang is likely to retaliate for the incursion.
Since we’re talking about electronic communications instead of physical presence, it’s closer to a series of letters with valid return addresses (generally necessary for a reply).
If you sent an actual letter to a gang’s physical hideout and included a valid return address but not the secret password, you could expect to be fire bombed…
Note: even though I have a vague understanding of what we’re talking about, I’m happy to read about it in the press (I need to make some popcorn). I have no interest in knocking on anyone’s door.