Parking services have taken a beating this year at the hands of hackers bent on stealing credit and debit card data. This week’s victim — onestopparking.com — comes compliments of the same organized crime gang thought to be responsible for stealing tens of millions of card numbers from shoppers at Target and Home Depot.
 Late last week, the cybercrime shop best known for being the first to sell cards stolen in the Target and Home Depot breach moved a new batch of cards taken from an unknown online merchant. Several banks contacted by KrebsOnSecurity acquired cards from this batch, and determined that all had one thing in common: They’d all been used at onestopparking.com, a Florence, Ky. based company that provides low-cost parking services at airport hotels and seaports throughout the United States.
Late last week, the cybercrime shop best known for being the first to sell cards stolen in the Target and Home Depot breach moved a new batch of cards taken from an unknown online merchant. Several banks contacted by KrebsOnSecurity acquired cards from this batch, and determined that all had one thing in common: They’d all been used at onestopparking.com, a Florence, Ky. based company that provides low-cost parking services at airport hotels and seaports throughout the United States.
Contacted about the suspicious activity that banks have traced back to onestopparking.com, Amer Ghanem, the site’s manager, said the company began receiving complaints from customers about a week before Christmas.
“It’s been something we have been dealing with for the past week, where some of our customers have called in and complained about fraudulent charges,” Ghanem said. He noted that the complaints stopped after the company performed several security scans and upgraded software for the Web site, but the investigation continues.
“We have been unable to identify any specific issues that has caused any credit card breach on our website,” Ghanem said in a written statement. “However, being a part of the e-commerce industry and staying up to date with the security news, we are aware of security threats that are always around, especially during the holiday season, when people tend to shop and travel more. We currently have 2 different services that are always monitoring traffic on our website, 24/7 to ensure the safety of our customers.”
This was the second time in as many weeks that this cybercrime shop —Rescator[dot]cm — has put up for sale a batch of credit cards stolen from an online parking service: On Dec. 16, KrebsOnSecurity reported that the same shop was selling cards stolen from Park-n-Fly, a competing airport parking reservation service. Sometime over the past few days, Park-n-Fly announced it was suspending its online service.
“In the wake of suspicious activity relating to certain Park ‘N Fly’s system containing credit card data, Park ‘N Fly has suspended our online reservations system, pending remediation,” reads a security update posted on the company’s site. Park ‘N Fly noted that it is still taking reservations over the phone.
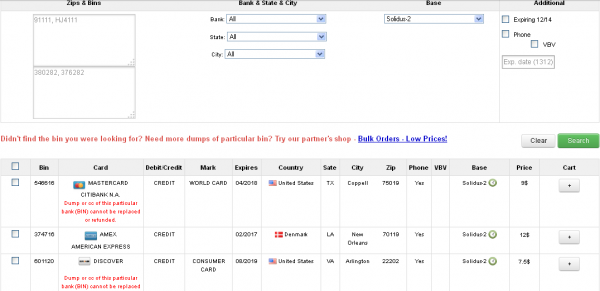
The stolen card data that bank sources traced back to Onestopparking.com are among hundreds or thousands that went on sale Dec. 21 at Rescator, in a batch dubbed “Solidus.” The card data ranges in price from $6 to $12 per card, and include the card number, expiration date, 3-digit card verification code, as well as the cardholder’s name, address and phone number.
Last month, SP Plus — a Chicago-based parking facility provider — said payment systems at 17 parking garages in Chicago, Philadelphia and Seattle that were hacked to capture credit card data after thieves installed malware to access credit card data from a remote location. Card data stolen from those SP+ locations ended up for sale on a competing cybercrime store called Goodshop.
In Missouri, the St. Louis Parking Company recently disclosed that it learned of breach involving card data stolen from its Union Station Parking facility between Oct. 6, 2014 and Oct. 31, 2014.



It looks like the safest thing is to go back to a cash-based economy.
Just dom’t use ATM then though …
Muggers would LOVE a cash-based economy. Prepaid Debit cards might be a part of the solution. Card issuers already offer single-use card numbers, but perhaps these should be supplemented with vacation/holiday cards with a separate number. Similar to single use, but only good for a month or two, with perhaps a SMS text 2-factor authentication required. This would limit the usefulness of cards for sale, and save consumers the hassle of changing all the card numbers on their auto-pay accounts.
Considering how gun crazy Americans are and the huge number of concealed carry permits being issued, I’m not so sure that muggers would “love” dying over a few hundred dollars.
In the vast majority of states, someone dumb enough to shoot a mugger would be spending years in prison themselves.
If the mugger is armed with a knife or gun, that’s not even remotely true…
The mugger doesn’t have to be armed, they can simply strong-arm you and you can use deadly force in many instances . . . stand your ground laws exist in 24 of the United States. You just have to have a reasonable fear / expectation that your life is in danger and you can use deadly force against your attacker. Even in States where no such law exists, other statute trumps, and if you believe you are being kidnapped in the process of a mugging you can use deadly force and most likely use lethal force legally. You don’t even need a gun. Any legally carried knife will do the job when applied correctly, and do so swiftly.
As a one-time muggee, I can assure you that more often than not the mugger gets the drop on their victim through the element of surprise. It’s nice to be able to believe one would be a ninja hero, but when you get clocked aside the head as you round a corner, it’s more likely the mugger will be long gone before you begin to become aware that something strange has just happened.
If you have a gun in your holder, under your coat, and the mugger surprises you with a knife at the throat, and takes your money, you might be able to shoot him after the fact as he runs away. By that time, your life is not in danger anymore, and you will go to prison if you kill that mugger. Having a gun might be a good idea in certain, very specific situations, which are very unlikely to happen to you, chances slim to none, and even then, the way it goes down might not be favoring you having a gun on you.
Far more USAians shoot themselves and/or family and friends then ever shoot muggers. If your muggers expect you to be armed they just attack more aggressively.
Cash is King, the odds of a thug coming to hit you up is slim to none. has it happened to you ? The thugs don’t know you are carrying cash unless you flash it or your pants jingle.
What about the use of Prepaid and re-fillable gift cards ? If that card is compromised or stolen, it covered.
There are a TON of ways other than a quick swipe of a card that goes back to your personal accounts.
We would like to think that a pre-paid card would offer some level of protection, but that has not been the case so far. When a prepaid phone card was stolen the vendor said there was nothing they could do about the person who continued to use the card after it was reported stolen. They wouldn’t suspend the card and/or refund the money and they wouldn’t forward the phone records pertaining to the thief to the relevant authorities.
As the vendor already has their share of the money there is nothing for them to gain, and nothing of value to them that they might need to protect, by offering the customer any kind of service in a situation like this. There’s no motivation for the vendor to feel compelled to do anything for the customer at this point. It’s only the potential for continued losses of capital in the future, near or distant, that leads a vendor to care what has happened to the data assigned to the customer. If the compromise of that data can lead to additional losses to the vendor, THEN the vendor will feel compelled to act “on behalf of the consumer.”
> safest thing
Perhaps for some definition of “safe” 🙂
Merchant breaches don’t scare me as a consumer – that’s a corporate problem which, with proper preparation, should affect me very little. My “prepper” advice to individuals worried about being the victim of card fraud :
1) Use only one or a very small number of cards in a given billing period
(less to keep track of = more sanity)
2) Monitor activity on those cards carefully, at least with every statement
(real-time alerts for every charge is ideal)
3) Store contact information for your card issuers in your mobile phone
(it needs to be where you can use it)
4) Have at least one card that is rarely used and is kept in a secure location
(if a wallet is stolen with all your primary cards, you still have a way to pay)
5) Have a reasonable amount of cash easily accessible
(if your bank account ends up being wiped / locked, you still have a way to pay)
6) Make full use of annualcreditreport.com
(investigate any odd accounts, faulty info, etc.)
Specific personal situations may alter some of these guidelines, but overall I have found they work pretty well in a variety of situations – and combined with *responsible* use, credit cards are not anything at all to worry about.
Whenever it’s offered, use “card not present” notification services. We use a bank that offers this and my spouse and I have received alerts on fraudulent activity within minutes of it occurring. Not all banks offer it, but when it is offered I recommend that you implement it.
I do something similar — I have the “large purchase limit” set to 1.00 on each of my credit cards and have SMS notifications enabled. Every time I make a purchase, I get an SMS within seconds. It’s not quite two-factor authentication, but it does mean that if a fraudulent transaction does get placed against one of my cards, I should know very quickly (provided I’m not asleep lol)
Yes, its does sound like this whole eCommerce thing wasn’t well thought out. Its understandable because bank losses are just passed back to customers through card fees which end up eventually raising the price for goods. In the long-run the banks are fully compensated so all this running around is really for the media.
Fixing the security issue after the fact, the new trend in stopping credit card fraud
I think it’s crazy how long a hack goes undetected. Getting hacked is not If but WHEN you get hacked. I think company’s need to spend more money on detection rather than prevention. Another big help is if company’s Would NOTG use outdated software. Last night night at Walmart the self checkouts was having lots of problems with accepting credit cards and getting cash back. One of the machines was rebooted and I saw Windows XP Professional logo and did not see anything indicating that it was POSReady 2009. It appears the Walmart self checkout by my house is using an outdated Windows XP Professional just begging to be hacked by criminals.
According to Microsoft, their ancient WEPOS 1.1 is still good until 2017.. Of course that means that every company has to somehow pass updates via WSUS which I doubt very many actually do. And most are probably not WEPOS 1.1 either. There are a lot of vendor products that still haven’t upgraded to the newer OS yet.
The suggested way to move forward is to have a single point of DATA bashing{i.e. using a state issued ID card} for a shorten cycle time. The best way is to remove the power that the fear these cyber thefts instil on the public and business.
The problem will only continue an educated consumer is the best defense going forward.
My check card was impacted by the Kmart POS data beach in September (http://krebsonsecurity.com/2014/10/malware-based-credit-card-breach-at-kmart/). My bank notified me in November and sent me a replacement card. I never detected any fraudulent activity on my checking account so I guess I dodged the bullet.
“the complaints stopped after the company performed several security scans and upgraded software for the Web site”
And there you have it. A good chunk of these problems will only be eliminated when companies start to realize that software and systems need maintenance. A for pete’s sake, hire some competent developers while you’re at it, not some Elance randos.
the key to stop these Malsubjects attacks is NOT to use major credit cards, but as said before, some sort of prepaid credit card that can be destroyed at a moment notice with the click of a button.
How is using a prepaid debit card better? “Destroyed…at the touch of a button” sounds great, but you don’t know it’s been compromised until fraudulent charges start showing up. By then it may be too late to do anything worth a debit card. With a credit card, issuers will protect you because the law requires them to do so.
“the complaints stopped after the company performed several security scans and upgraded software for the Web site”
This statement doesn’t seem to pass the smell test.
If there are already 100s – 1,000s of the stolen cards on the market (and being used) how could “scans and upgrading” possibly have any effect on that activity?
Sounds more like onestopparking.com is doing a PR campaign trying to comfort (?) customers
Online ecommerce is really getting nasty
would digital currency of some kind be a solution to all these hacks? would a bitcoin wallet be harder to steal than credit card info?
Please tell me you’re planning to do an end of year roundup of these hacks. A list of hacked companies in 2014 with accompanying “x million cards stolen” stats for each one would really illustrate the scope of this problem in a way that individual blog posts for each one just can’t quite capture.
This may be an elementary question to those of you in the IT security business but here goes. If Krebs on security know how to access these illegal carder shops, and banks can get to them, and I’m sure some of the rest of you know how to reach them, why can’t law enforcement identify them and shut them down? If it is to much trouble legally, maybe it’s time for an internet assassin squad. (Machines, not people, think Stuxnet) In other words why doesn’t an industry exist on the dark side of the internet that employs hackers to just kill off these websites that allow these anti-social criminals to profit? I would imagine banks and credit card companies monetarily banded together to take care of these criminals would not be that big of a contest if they wanted to resort to this. After all, banks and credit card companies are criminals too, so I can’t see them having a problem with this approach. It would be kind of like a Mafia style hit. This could be very entertaining. Think of the headlines. I know Brian would have plenty to write about then!