China has been actively diverting unencrypted Web traffic destined for its top online search service — Baidu.com — so that some visitors from outside of the country were unwittingly enlisted in a novel and unsettling series of denial-of-service attacks aimed at sidelining sites that distribute anti-censorship tools, according to research released this week.
The findings, published in a joint paper today by researchers with University of Toronto’s Citizen Lab, the International Computer Science Institute (ICSI) and the University of California, Berkeley, track a remarkable development in China’s increasingly public display of its evolving cyber warfare prowess.
“Their willingness to be so public mystifies me,” said Nicholas Weaver, a researcher at the ICSI who helped dig through the clues about the mysterious attack. “But it does appear to be a very public statement about their capabilities.”
Earlier this month, Github — an open-source code repository — and greatfire.org, which distributes software to help Chinese citizens evade censorship restrictions enacted by the so-called “Great Firewall of China,” found themselves on the receiving end of a massive and constantly-changing attack apparently designed to prevent people from being able to access the sites.
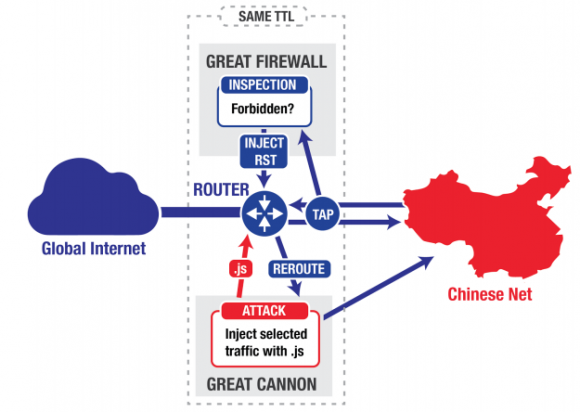
Experts have long known that China’s Great Firewall is capable of blocking Web surfers from within the country from accessing online sites that host content which is deemed prohibited by the Chinese government. But according to researchers, this latest censorship innovation targeted Web surfers from outside the country who were requesting various pages associated with Baidu, such that Internet traffic from a small percentage of surfers outside the country was quietly redirected toward Github and greatfire.org.
This attack method, which the researchers have dubbed the “Great Cannon,” works by intercepting non-Chinese traffic to Baidu Web properties, Weaver explained.
“It only intercepts traffic to a certain set of Internet addresses, and then only looks for specific script requests. About 98 percent of the time it sends the Web request straight on to Baidu, but about two percent of the time it says, ‘Okay, I’m going to drop the request going to Baidu,’ and instead it directly provides the malicious reply, replying with a bit of Javascript which causes the user’s browser to participate in a DOS attack, Weaver said.
The researchers said they tracked the attack for several days after Github apparently figured out how to filter the malicious traffic, which relied on malicious Javascript files that were served to visitors outside of China that were browsing various Baidu properties.
Chillingly, the report concludes that Chinese censors could just have easily served malicious code to exploit known Web browser vulnerabilities.
“With a minor tweak in the code, they could have provided exploits to targeted [Internet addresses], so that instead of intercepting all traffic to Baidu, they would serve malware attacks to those visitors,” Weaver said.
Interestingly, this type of attack is not unprecedented. According to documents leaked by National Security Agency whistleblower Edward Snowden, the NSA and British intelligence services used a system dubbed “QUANTUM” to inject content and modify Web results for individual targets that appeared to be coming from a pre-selected range of Internet addresses.
“The Chinese government can credibly say the United States has done similar things in the past,” Weaver said. “They can’t say we’ve done large scale DDoS attacks, but the Chinese government can honestly state that the U.S. has modified traffic in-flight to attack and exploit systems.”
Weaver said the attacks from the Great Cannon don’t succeed when people are browsing Chinese sites with a Web address that begins with “https://”, meaning that regular Internet users can limit their exposure to these attacks by insisting that all Internet communications are routed over “https” versus unencrypted “http://” connections in their browsers. A number of third-party browser plug-ins — such as https-everywhere — can help people accomplish this goal.
“The lesson here is encrypt all the things all the time always,” Weaver said. “If you have to worry about a nation state adversary and if they can see an unencrypted web request that they can tie to your identity, they can use that as a vehicle for attack. This has always been the case, but it’s now practice.”
But Bill Marczak, a research fellow with Citizen Lab, said relying on an always-on encryption strategy is not a foolproof counter to this attack, because plug-ins like https-everywhere will still serve regular unencrypted content when Web sites refuse to or don’t offer the same content over an encrypted connection. What’s more, many Web sites draw content from a variety of sources online, meaning that the Great Cannon attack could succeed merely by drawing on resources provided by online ad networks that serve ads on a variety of Web sites from a dizzying array of sources.
“Some of the scripts being injected in this attack are from online ad networks,” Marczak said. “But certainly this kind of attack suggests a far more aggressive use of https where available.”
For a deep dive into the research referenced in this story, check out this link.




Yes, we’d probably all be screwed if PRC had served some browser 0days…
Stupidly, I didn’t even think of the possibility of that. Makes you wonder why PRC just decided to ddos the “script kiddie” way instead of putting on their big boy shorts and serving exploits…
We should all be scared of China.
Totally agree with what you wrote with one exception, I don’t fear any country, never have & never will. I thrive on the challenge.
Fear is useful to concentrate one’s attention. Ignoring it can be fatal.
Why do you think they did *not* also serve exploits?
Because the world reaction would have crippled baidu. Cyber genocide on their own corporations. In its current state the traffic is relatively harmless to anyone except those being attacked. If, however, we knew active exploits were coming down the pipe to infect our users that we had no patch for, the immediate and only recourse for many corporations and even some ISP’s would be to block all traffic to Baidu and possibly to any Chinese web servers. Big difference between a little bit of redirected traffic and actively delivering 0 day malware.
1. I am sure that the PRC has ways to find or purchase 0 day vulnerabilities and develop exploits for them pretty much any time it wants to. The same is true of any country with substantial economic and military resources.
2. How do you know that they did not serve up Trojans or other malware to some at the same time they were sending out the DDoS client to other browsers? Or perhaps they tested the malware distribution capabilities of their “cannon” prior to testing the DDoS function?
remember, this is usually from within China out, and they may not want to poison their own kind-yet. Its a censorship – the Chinese government may not want people to see how much freedoms are actually out there in the world. That is one way to subdue people in believing that their way is the best way, and that everyone else in the world is jacked up.
If somehow this censorship process would break, and the Chinese people finally see what their government is trying to do, there might just be a revolt.
Too funny, do we really think that our own “information” is always on the up and up?
They all try and manipulate, it’s what “they” do.
No difference in a “spinned” report vs. censorship in my book.
For a nice example look no further than the Homeland Security page about bringing tobacco into the US from anywhere. My favorite part is ” you just can’t trust those foreign sources”. All I wanted was to get a damn Cuban cigar.
All nations control their citizens in various ways either through restrictions on what we can trade or buy to restrictions on where we can go.
It’s all the same.
Exactely, Eng is a little indoctrinated. Are the Chines so blind of the outside world? Look at China’s outbound international tourist number – went from 45 million to over 100 million in the last 6 years.
What? There is a big difference between spin and censorship. With spin others are allowed to say what they want, you just spin. With censorship other voices are disallowed. That’s monumental.
And yet Krebs On Security doesn’t offer https encryption. I wonder why not.
Sure it does Tom.
I agree
It does, just not by default. There are a few WordPress plugins that force https all the time. Usage of one of them would be good here.
HTTPS to this website works perfectly. And if you think that an insecure HTTP request should automatically redirect users to the HTTPS content then you need to read up on browser security to see what that’s not such a good idea. It would be better for Brian to disable HTTP access to this site completely.
> HTTPS to this website works perfectly
Yes it does, however it includes mixed content that is NOT secure. The end result is just as risky as though there were no HTTPS.
But offering HTTPS is the first step in being able to offer a fully secured connection later on.
Sorry, that’s incorrect. It’s not “just as risky”, the only elements of the page that can be modified are the non encrypted elements. All the content served over https is still secure
Your connection to krebsonsecurity.com is encrypted with obsolete cryptography – is what chrome tells me.
Yeah the certs are good, its just his config on the server side that is weak.
Hey Brian, update your cipher suites on Apache!
See: https://wiki.mozilla.org/Security/Server_Side_TLS#Apache
He’s using nginx, not apache.
For those of you that control corporate routers, there is a simple and effective fix. Prohibit YOUR internal users from accessing any Chinese address space. Hit back and hit in the pocketbook.
Ip route Null0
yeah, try that, tell us how it works for you when the traffic you block is some line of business app ordering parts from a supplier. Or restocking inventory in your retail outlets. Or any of a whole host of other legitimate traffic requirements.
Pocketbook that will be hit is likely to be yours, break a line of business app in the interest of security and you’ll find out exactly why cybersecurity is such a mess.
If I view this page with https, I see 6 comments; if I use http, I see 8, and the 6th is different.
Https can make DDOS worse. It’s easier to pass along (or even generate fake encrypted packets) than it is to decrypt and reject them.
Quttera.com scans and detects the scripts, see their report for more info or scan on your own: http://quttera.com/detailed_report/baidu.com
http://quttera.com/detailed_report/krebsonsecurity.com
“Detected reference to malicious blacklisted domain web.archive.org” lol
This kind of incident just goes to show four things:
1. We should all be using HTTPS wherever possible.
2. We should all be whitelisting JS instead of letting random websites run code on our machines.
3. Reputable website operators should (re)design their sites with JS whitelisting in mind, so everything that can work without JS (e.g. just view text, images, follow links) does work without JS and the rest (interactive/dynamic-loading features) degrades gracefully, with a message saying you can have more features with JS.
4. The US should never have let the NSA do many of the things that it did. It was bound to become public sooner or later, and then it was bound to be used as an excuse by other nation-states for similar or worse behavior: “But they did it without being punished, why shouldn’t we?”
Do you also mean to include things like using or even just developing nuclear weapons, too?
HTTPS is just as vulnerable. Where, exactly do you think that those Chinese websites get their TLS/SSL certificates from?
Notice any unrecognizable CAs in your OS or browser or App runtime (Java, Android, Python, PHP, etc)?
SSL Observatories in addition to encryption everywhere is critical, too.
If Bluecoat, WebSense, NetNanny, Avast, and all of the other TLS/SSL inspecting proxies can do it, why would anyone think the Chinese can’t do it with state-owned government CAs already trusted by default in your phone, PC, and app?
How do I contact you about a possible speaking engagement? Thank you.
I bet a good place to start would be on the “About the author” link at the top right of every page. There’s a contact form on it that you could use to directly communicate “securely” with Brian.
I am responsible for the IT security at my employer, and last year I actually did configure our corporate firewall to block all connections TO, as well as from, China (as well as a few other unsavory countries).
Yes, it’s a little inconvenient at times, when you can’t get to the support forums of some suppliers of IT equipment, etc.
But after discovering that our internet-facing FTP server was suffering from thousands of Chinese attempts per hour to brute-force login, 24/7, enough was enough, and I just cut them off.
Of course, they could use proxies to get around that, but they didn’t (and those proxies would be aggressively and permanently auto-banned since last year).
The attacks you have to worry about are the ones using zombie relays so they appear to come from outside China.
Hi all,
I found out just the other day using a fairly new app called: “Lostnet no root firewall” in playstore. ES File Explorer was connecting to Baidu three different paths. One was automatically looking for updates,since unchecked in settings. The others are Baidu analytics,and connect periodically while navigating in the app. I did a packet capture,but was not able to see more than the IP address. The file was not very big,(zip file) only a few thousand kilobytes. But that could just be my recent activity. The problem is,many productivity and security apps are offered for free in playstore by Chinese developer’s. Great apps,but they ALL connect back to China. This traffic can now be used to serve up all kinds of malicious software,and all the vulnerabilities for older device’s are well known. I obviously now block all traffic to and from China. But for the unknowing,many millions are vulnerable. Furthermore,finding the country of origin for Chinese apps is a difficult proposition,because they ALL are free. So no address on playstore page. This is now going to be a really big problem. Even just updating to the latest os does nothing to alleviate the app vulnerabilities.
Malware can just as easily com from sites in the USA, Western Europe or Bangladesh, for that matter. If you want to block access to every country with malware servers, the Internet will become a quiet, lonely place for you. 🙂
In short, we have to enable TLS on our websites. Gradually, all websites should serve the content encrypted. That’s what Google and many other big corporations are trying for. There are numerous benefits serving the content on an encrypted channel rather than in plaintext.
These days, getting a good TLS cert is not that much hard I think. 🙂
My websites are using free TLS certs. 🙂
https://www.robinmathewrajan.com/
https://www.robinmathewrajan.com/ramblings/
“What’s more, many Web sites draw content from a variety of sources online, meaning that the Great Cannon attack could succeed merely by drawing on resources provided by online ad networks that serve ads on a variety of Web sites from a dizzying array of sources.”
One can now claim “national defense” when using Ad-Block.
Pay cash when you can, get off the internet, go to church and visit your mom. Stop the insanity.
You trust cash?
What are the chances that this ‘great cannon’ is just a badly implemented copy of Websense’s engine? Several years ago, every Websense customer hitting one of the websites I supported generated an identical (save for the source ip and /some/ header information) query from a websense ip. My solution to their poor product was to null route Websense’s poller ip block. You’d be surprised how many fraud detection alerts got generated by that crap.
Between, the previous, and the second half of the school year. One of the better schools, in penetration, may be learning another project, from notes taken from a secure agency of the feds. After all, the Americans probably stored the method and results of the attack, in plain sight, along with a numbered copy, to see who? Where? So probably them?
The Chinese texts I’m seeing are saying Cannon (大炮) which is literally just “big gun” someone has translated it as great cannon when in fact the Chinese is simply Cannon.
see
http://chinadigitaltimes.net/chinese/2015/04/%E5%A5%87%E5%AE%A2%E8%B5%84%E8%AE%AF%EF%BD%9C%E4%B8%BA%E4%BB%80%E4%B9%88%E8%A6%81%E9%AB%98%E8%B0%83%E7%9A%84%E4%BD%BF%E7%94%A8%E5%A4%A7%E7%82%AE%EF%BC%9F/
and
http://www.solidot.org/story?sid=43668
The chinese have continued to use this even when one chart
Where can I found a addon/extension for Firefox/Chrome/safari which can block all the website from China? I don’t want to be hacked or be fodder of the “Great Cannon”.
NoScript will work.
Note that just because China is adding a script to your Baidu request doesn’t mean that the script itself has to be hosted in China. (they could probably host it on GitHub if they wanted to…)
The attack from China that I really worry about may have been going on for a long time now, and that specifically is backdoors planted in hardware built in China and sold to the rest of the world, especially to the US.
Someone asked above why the Chinese were being so open about these attacks. My guess is that they are doing what every stage magician does, keeping us distracted from the real action by dangling something else in front of us to distract us.
People can check software, after all, but who among us opens up chips and reverse engineers them to find out what the HARDWARE is REALLY doing?
With all the hardware we are buying from China, what assurances do we have that the Chinese dictatorship is not building a “DestructoNet” quietly in hardware which WE then place throughout our Internet?
Interesting point. I doubt it would be a “destructo net”, though. Much more effective to just build security bypasses into the hardware.
Also, I doubt this is occurring on a broad scale if it is occurring at all. But that doesn’t mean it’s impossible.
http://thehackernews.com/2015/02/hard-drive-firmware-hacking.html
It’s somewhat of a hassle but I use NoScript in Firefox and configured it to default to blocking all javascript. I put NoScript’s “Temporarily Allow All” button on the toolbar. I have no Flash in Firefox and use another browser with Flash in order to view sites requiring it.
Many sites work even with javascript blocked. I don’t bother partially choosing which scripts to run and which to allow and instead just “temporarily allow all.” I used to cherry pick which to allow but that’s not really practical. If a site looks fishy, I don’t allow any scripts. And if a site works fine without javascript, I don’t enable them.
I’ve only run into a few sites that don’t work well even after clicking NoScript’s “temporarily allow all” button. Lately, though, I’ve run into a few sites that have trouble with NoScript’s default “enabled ABE (Applications Boundaries Enforcer),” which I have to manually uncheck for sites I trust and need that don’t work otherwise (usually logging into some part of a site).
For my email, I run the another browser with Flash-enabled and without any blocking addons/extensions. I only browse with it to fully trusted sites, though that can still be risky, of course.
More and more not having Flash in Firefox is ok with html5 video more and more common. But I can’t imagine when javascript will go away, though.
Javascript certainly has a practical use and can be quite helpful. But, it’s used so often for advertising and code injection that the biggest portion of it can easily be filtered out without any issue. My question regarding your practices are mainly in the idea of using No Script that way. It would seem so much easier to not use NoScript at all and have one browser set to disable javascript while having the other browser set to have it enabled? As a matter of security and general performance though, I usually find it better to avoid “toolbars” across the board. I do agree however that flash is an issue and really needs to go away. I’ve found it rather easy to prevent most flash related items from coming in by making use of the host file.
I tend to add sites / services to NoScript’s whitelist if I find they’re essential and that I visit them regularly.
If you permanently whitelist things (which is a tradeoff, you’d saying that you trust them not to be hacked), then with time your beaten path won’t require additional tuning.
For off my beaten track, I use temporarily allow…
Not having Videos automatically start (html:video of Flash) is a good thing (and NoScript can do this).
Pretty much any content can be a security risk, although generally newer features have more risk than older.
Reducing your attack surface simplifies things, and generally results in faster page loads.
I agree
Given that what China did was not that stealthy it could be a learning exercise instead of a full on attack. What they are doing is burnishing their capabilities in this area for when a more extensive attack is attempted for their purposes. When North Korea took down Sony it was sloppy as they were learning and this could be the same.
One possible scenario, which would explain the very public nature of this event would be if it had been unintentional. Perhaps it wasn’t a deliberate attack at all, just a software bug or configuration error. Or perhaps someone else managed to get control of some routers in China and injected the js traffic without the knowledge of the Chinese government?
Obviously these ideas are pure speculation. My point is simply, that a deliberate attack by the Chinese government is perhaps the most plausible explanation for the DDoS attacks, but not the only one.
China is an oppressive communist country that we have no choice but to tolerate because of their economic and military might. Wage you add in their cyber espionage and warfare capabilities, we definitely have a lot to fear.
So here we can see why we need to use SSL Certificate on all websites.
I checked out some web locations which handle https-everywhere. Some of the comments from users indicate that it doesn’t quite work as well as you would like. I’m a little hesitant to install it for that reason.
I think a reasonable alternative would be use either Google Chrome or wrap your browser in “sandboxie”. With either of these you get the added benefit of resistance to malware from the web, not just from malware from man-in-the-middle attacks.
Sandbox as much as possible.