What makes one novel strain of malicious software more dangerous or noteworthy than another? Is it the sheer capability and feature set of the new malware, or are these qualities meaningless without also considering the skills, intentions and ingenuity of the person wielding it? Most experts probably would say it’s important to consider attribution insofar as it is knowable, but it’s remarkable how seldom companies that regularly publish reports on the latest criminal innovations go the extra mile to add context about the crooks apparently involved in deploying those tools.
Perhaps with some new malware samples, the associated actor attribution data is too inconclusive to publish —particularly when corporate lawyers are involved and such findings are juxtaposed to facts about a new code sample that can be demonstrated empirically. Maybe in other cases, the company publishing the research privately has concerns that airing their findings on attribution will somehow cause people to take them or the newfound threat less seriously?
I doubt many who are familiar with my reporting will have trouble telling where I come down on this subject, which explains why I’m fascinated by a bit of digging done into the actor behind a new malware sample that recently received quite a bit of media attention. That threat, known variously as “Rombertik” and “Carbon Grabber,” is financial crimeware that gained media attention because of a curious feature: it was apparently designed to overwrite key sections of the hard drive, rendering the host system unbootable.
News about Rombertik’s destructive ways was first published by Cisco, which posited that the feature was a defense mechanism built into the malware to frustrate security researchers who might be trying to unlock its secrets. Other security firms published competing theories about the purpose of the destructive component of the malware. Some argued it was the malware author’s way of enforcing licensing agreements with his customers: Those who tried to use the malware on Web addresses or domains that were not authorized as part of the original sale would be considered in violation of the software agreement — their malware infrastructure thus exposed to (criminal) a copyright enforcement regime of the most unforgiving kind.
Incredibly, none of these companies bothered to look more closely at the clues rather clumsily left behind by the person apparently responsible for spreading the malware sample that prompted Cisco to blog about Rombertik in the first place. Had they done so, they might have discovered that this ultra-sophisticated new malware strain was unearthed precisely because it was being wielded by a relatively unsophisticated actor who seems to pose more of a threat to himself than to others.
AFRICAN PERSISTENT THREAT
As much as I would love to take credit for this research, that glory belongs to the community which has sprung up around ThreatConnect, a company that specializes in threat attribution with a special focus on crowdsourcing raw actor data across a large community of users.
In this case, ThreatConnect dug deeper into centozos[dot]org[dot]in, the control server used in the Rombertik sample featured in the original Cisco report. The Web site registration records for that domain lists an individual in Lagos, Nigeria who used the email address genhostkay@dispostable.com. For those unfamiliar with Dispostable, it is a free, throwaway email service that allows anyone to send and receive email without supplying a password for the account. While this kind of service relieves the user of having to remember their password, it also allows anyone who knows the username to read all of the mail associated with that account.
Reviewing the messages in that genhostkay@dispostable.com account reveals that the account holder registered the domain centozos[dot]org[dot]in with registrar Internet.bs, and that he asked to be CC’d on another email address, “kallysky@yahoo.com”. ThreatConnect found that same genhostkay@dispostable.com email address used to register a number of other domains associated with distributing malware, including kallyguru[dot]in, nimoru[dot]com, directxex[dot]net, and norqren[dot]com.
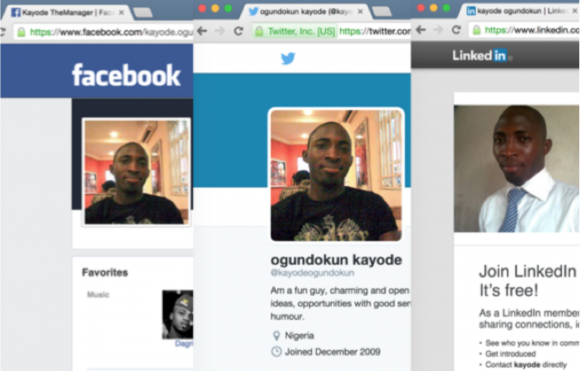
The email address kallysky@yahoo.com is tied to a Facebook account for a 30-year-old Kayode Ogundokun from Lagos, Nigeria, who maintains a robust online presence from his personal and “business” Facebook accounts, Blogger, LinkedIn, Twitter and Youtube,” ThreatConnect wrote.
“In fact Ogundokun has done very little in the way of operational security (OPSEC). His efforts in covering tracks his tracks have been minimal to non-existent,” ThreatConnect continued. “Ogundokun’s skillset appears to be limited to using commodity RATs and botnets within email borne attacks and is motivated primarily on financial gain rather than espionage or ideological purposes. [We assess] that Ogundokun likely purchased a new version of Carbon Grabber from a much more capable and sophisticated tool author, where the author subsequently licensed it to a less capable operator. His particular sample of Carbon Grabber was simply caught up in a headline grabbing story.”
REVEALING INTERNET SECRETS TO YOU
For several years until very recently, Kally/Koyode maintained kallysky.com, which thanks to archive.org we can still review in all its glory. In it, Kally’s site — which boldly and confidently displays the banner message “Revealing Internet Secrets to You” — links to dozens of video tutorials he produced and stars in on how to use various malware tools.
“He claims to offer services for Citadel Bot, Cybergate RAT, Darkcomet RAT with cpanel web services, ‘Fully Undetectable’ by anti-virus as well as other capabilities such as binders and file extension spoofers, all for educational purposes, of course,” ThreatConnect notes. “He also provides his phone number, BlackBerry Pin and the same kallysky@yahoo[dot]com email address that we observed earlier with the genhostkay@dispostable[dot]com norqren[dot]com domain expiration email.”In an April 2014 video, Ogundokun provides a Carbon Form Grabber / Carbon Grabber tutorial. At the beginning of the video, he includes his kallysky@yahoo[dot]com contact details.
Sadly, Kally did not respond to requests for an interview about his work sent to his yahoo.com address. But his case and the initial industry writeups on Rombertik are illustrative of a trend within the security industry that’s become all-too-common: Threat reports that lack context — particularly on attribution that is so trivially discoverable, ThreatConnect observed.
“As news of Rombertik spread, we saw sensationalized reporting which used attention grabbing terms such as ‘terrifying,’ ‘deadly’ and ‘suicide bomber malware’ dominate the security news headlines,” the company wrote. “Now if we consider for a moment the man hours and ad hoc reprioritization for many security teams globally who were queried or tasked to determine if their organization was at risk to Rombertik – had the organizations also had adversary intelligence of Ogundokun’s rudimentary technical and operational sophistication, they would have seen a clearer comparison of the functional capabilities of the Rombertik/Carbon Grabber contrasted against the operator’s (Ogundokun) intent, and could have more effectively determined the level of risk.”




![One of countless pages archived from Kallysky[dot]com](https://krebsonsecurity.com/wp-content/uploads/2015/05/kallysecrets-580x480.png)

“had the organizations also had adversary intelligence of Ogundokun’s rudimentary technical and operational sophistication, they would have seen a clearer comparison of the functional capabilities of the Rombertik/Carbon Grabber contrasted against the operator’s (Ogundokun) intent, and could have more effectively determined the level of risk.”
Yeah, but there’s no headlines in that approach! And these companies are all about headlines.
It’s now common for infosec people I follow on Twitter to complain about companies that are more focused on assigning a catchy name and a logo to malware than in researching its capabilities or determining who created it.
In most cases, attribution isn’t particularly helpful – unless of course you can blame either China, Russia, Iran or North Korea in line with the White House’s current “enemies list” – in actually doing anything about the malware. But you can still get a lot of PR from inflating the importance or (speculated) source of the malware.
Since infosec is more and more clearly losing the security war, it’s become more about hype and PR than anything concrete.
It’s so strange that security companies and teams, with people working in the field for decades or more, paid very high salaries, seem to fail at even the most basic investigative work.
Welcome to planet Earth, we hope you enjoy your stay.
I’m obviously in the wrong job.
I don’t think most are trying, honestly. For your average run of the mill security guy there is no real point to figuring out who created it, just that it exists and the general way it works or what it does. Most companies have whole hosts of people threats from ex lovers of the CEO to hostile company offers and lawsuits. Knowing that someone is behind the tools is interesting, but changes little of the day to day efforts.
What I mean to say is that while it is good to know and interesting, few companies are bothering with reverse engineering malware and trying to find out who to pin it on, they just want it gone or never to show up in the first place. These reports are usually targeted at a wide audience many of whom are CEOs, CFOs, software/hardware salesmen, etc. who also probably don’t want to read dozens and dozens of profiles of these crooks. There is a smaller subset of the security community for whom this is tremendously beneficial, but not everyone across the board.
I think the last paragraph sums it all up quite well.
Very interesting! Thanks, Brian, for your work and for pointing out this important oversight of many malware “analysts”. Perhaps if more of them followed the attribution trail, there wouldn’t be as many people in the malware “industry” if they knew they would be tracked.
Regards,
Attribution should be left to the authorities, not private companies with profit motives like ThreatConnect (formerly CyberSquared). The margin for error is huge and all of us deserve due process before having our names dragged through the dirt. Even the ones who are guilty.
Sorry Jeff opinions on attribution should be left to real analysts who can actually analyze themselves out of a wet paper bag.
I love anonymous critics who are too afraid to use their real names. Stay classy.
HA ! The researchers were scattering like rats, probably thinking of the network holocaust that happened at Sony. IF the software had “non-compliance” wiper software, it could have been dangerous…. But precautions can be put in place to protect the important assets.
As the good side of security uncovers more about the dark side ways, the tactics the dark side will either head away from port 80 into a more secure method of transmission. making it more difficult to detect. Add in robust security features embedded in the software and the dark side will go from dark to utterly evil.
You bring up some good points but there aren’t really any “secret” methods that are unknown to defenders and researchers, if anything it’s the other way around. You don’t need to have every particular 0day to understand your weak spots. “Cyber security” is the war, your network environment is literally a battlefield. The munitions and hardware change but the risks and vulnerabilities are always the same.
This is not for everyone, hardly most. Understanding networks and technology alone will not lead to victory, you must also understand your enemies. Lacking a clear understanding of either will result in failure or loss every time.
hehehehe. There are plenty of “secrets” out there, but they belong to the bad guys. There has been many cases of espionage or malware sets that have been crawling around networks for years. That in itself is either a pretty well kept secret – or just lax security on the good side.
So far in my 15+ years in network security, I’ve seen a lot of wars, battlefields, losses and victories.
Knowing your “enemies” is a broad statement – there are many unless your are being targeted. As Brian has posted before, there ar a ton of people who scan attack surfaces, looking for that fame and fortune, whether good or bad.
The crooks have a more united front and rely on each other moreso than the good guys. Until the security industry learns to work together the effort to squash most of the vile events will take longer and result in nothing significant. All the effort is doing is creating a learning experience for both sides, with the evil side always one step ahead.
At least L3 grew a set and is trying something out of the box. People are complaining about L3 squashing communications to crimeware sites – as if its legitimate traffic. Most of these complainers are good security analysts with no clue what the bottom line is in respect to the effort. This is one example why the crooks will continue to win. Nature of the beast.
Again, good points. However, I was speaking more towards the nature of the attacks that are feasible, this is a much broader discussion than with the specifics you are bringing up. The “good guys” are certainly behind on where they need to be overall. However, you might be forgetting that the “good guys” are also made up of quite a few former and current “bad guys”, so again, there isn’t much that’s completely secret, per se. That’s the real danger with “cybersecurity”, that nobody can ever be truly secure regardless of where your ideologies may fall.
Brian
Big fan – just completed audiobook version of “Spam Nation” really enjoyed it and learned a lot.
Question re: Sept 2014 blog “Data Broker Giants Hacked by ID Theft Service”
where does this leave HireRight? My corporation is asking us to trust HireRight with very personal identity data and I’m not happy with that. Are they any better or worse at data security than other major data aggregators?
For fun I decided to get into his account, dumped all IP logins, all passwords, furthermore dumped all files and databases. Looking threw them currently.
While agree Ogundokun isn’t much of a threat, Rombertik and variants are available and can cause real damage when wielded by more capable actors. I don’t see any need to lessen the security posture because Ogundokun had the first sample to be caught.
Day by day malware’s are increasing in email section and we need some ways to stop them. this was quite help full information, but we can also save our self from malware’s through understand what is malware and how we can save our self from them.
What oxo did earlier, going in, having a look through the drawers and copying out detail is all very good. It gives oxo an idea of what the guy is at and a bit of background detail. Maybe even gives access to material which would leave the owner vulnerable. But what next? Do you give it to law enforcement in which case you may be asked how did you get it? Depending on jurisdiction you may have broken the law. What if law enforcement are already looking at the suspect? Now they have oxo’s IP address in the mix as well. At court the suspect may potentially allege that oxo planted the material there or that oxo was responsible for some of the alleged activity and communications. Messy! Of course it depends whether your goal is disruption or investigation. And what footprint you leave on the doormat!
Just checking.
Live short and fail.
It’s worth pointing out that traditional military threat analysis focuses first on capabilities, then on intentions. Capabilities are objective facts (not that analysts and others can’t skew them!); if an actor lacks the requisite capabilities, his intentions don’t matter. Intentions, however, are based on human attitudes. They are difficult to determine in the best of circumstances, and subject to rapid change. Hence, you initially plan around your opponents capabilities, regardless of their apparent intentions. At least that’s the theory.
Along the same lines, you can justify looking at the malware out there as the primary factor, the individuals who wield it second. (The individuals with the skills to *create* new malware fall more on the “capabilities” side.)
These are theoretical, broad based arguments about what one might consider *first*. I have no disagreement with the premise here that it’s *also* important to do attribution analysis. In theory, you build a military strong enough to take on the capabilities of any potential opponent; in reality, if you could do that you’t trigger an arms race as your potential opponents did the same; and besides, you can never really afford that anyway. Knowing the intentions and the actual identities and characteristics of your opponents are essential.
— Jerry