The Internet of Things is fast turning into the Internet-of-Things-We-Can’t-Afford. Almost daily now we are hearing about virtual shakedowns wherein attackers demand payment in Bitcoin virtual currency from a bank, e-retailer or online service. Those who don’t pay the ransom see their sites knocked offline in coordinated cyberattacks. This story examines one contributor to the problem, and asks whether we should demand better security from ISPs, software and hardware makers.
 These attacks are fueled in part by an explosion in the number of Internet-connected things that are either misconfigured or shipped in a default insecure state. In June I wrote about robot networks or “botnets” of hacked Internet routers that were all made and shipped by networking firm Ubiquiti. Attackers were able to compromise the routers because Ubiquiti shipped them with remote administration switched on by default and protected by a factory default password pair (ubnt/ubnt or no password at all).
These attacks are fueled in part by an explosion in the number of Internet-connected things that are either misconfigured or shipped in a default insecure state. In June I wrote about robot networks or “botnets” of hacked Internet routers that were all made and shipped by networking firm Ubiquiti. Attackers were able to compromise the routers because Ubiquiti shipped them with remote administration switched on by default and protected by a factory default password pair (ubnt/ubnt or no password at all).
That story followed on reports from security firm Imperva (see Lax Security Opens the Door for Mass-Scale Hijacking of SOHO Routers) which found a botnet of tens of thousands of hijacked Ubiquiti routers being used to launch massive ransom-based denial-of-service attacks. Imperva discovered that those tens of thousands of hacked devices were so easy to remotely control that each router was being exploited by several different extortion groups or individual criminal actors. The company also found those actors used the hacked routers to continuously scan the Internet for more vulnerable routers.
Last week, researchers in Vienna, Austria-based security firm SEC Consult released data suggesting that there are more than 600,000 vulnerable Ubiquiti routers in use by Internet service providers (ISPs) and their customers. All are sitting on the Internet wide open and permitting anyone to abuse them for these digital shakedowns.
These vulnerable devices tend to coalesce in distinct geographical pools with deeper pools in countries with more ISPs that shipped them direct to customers without modification. SEC Consult said it found heavy concentrations of the exposed Ubiquiti devices in Brazil (480,000), Thailand (170,000) and the United States (77,000).
SEC Consult cautions that the actual number of vulnerable Ubiquiti systems may be closer to 1.1 million. Turns out, the devices ship with a cryptographic certificate embedded in the router’s built-in software (or “firmware”) that further weakens security on the devices and makes them trivial to discover on the open Internet. Indeed, the Censys Project, a scan-driven Internet search engine that allows anyone to quickly find hosts that use that certificate, shows exactly where each exposed router resides online.
The Imperva research from May 2015 touched a nerve among some Ubiquiti customers who thought the company should be doing more to help customers secure these routers. In a May 2015 discussion thread on the company’s support site, Ubiquiti’s vice president of technology applications Matt Harding said the router maker briefly disabled remote access on new devices, only to reverse that move after pushback from ISPs and other customers who wanted the feature turned back on.
In a statement sent to KrebsOnSecurity via email, Harding said the company doesn’t market its products to home users, and that it sells its products to industry professionals and ISPs.
“Because of this we originally shipped with the products’ configurations as flexible as possible and relied on the ISPs to secure their equipment appropriately,” he said. “Some ISPs use self-built provisioning scripts and intentionally locking down devices out of the box would interfere with the provisioning workflows of many customers.”
Harding said it’s common in the networking equipment industry to ship with a default password for initial use. While this may be true, it seems far less common that networking companies ship hardware that allows remote administration over the Internet by default. He added that beginning with firmware version 5.5.2 — originally released in August 2012 — Ubiquiti devices have included very persistent messaging in the user interface to remind customers to follow best practices and change their passwords.
“Any devices shipping since then would have this reminder and users would have to intentionally ignore it to install equipment with default credentials,” he wrote. Harding noted that the company also provides a management platform that ISPs can use to change all default device passwords in bulk.
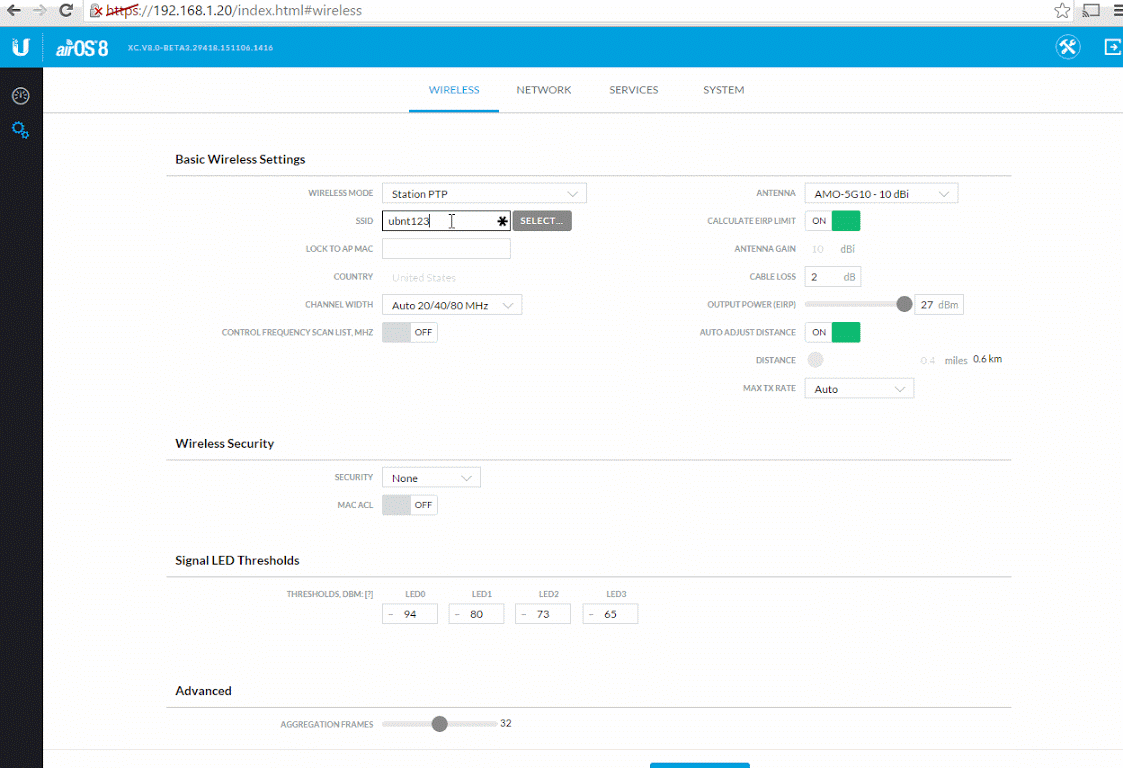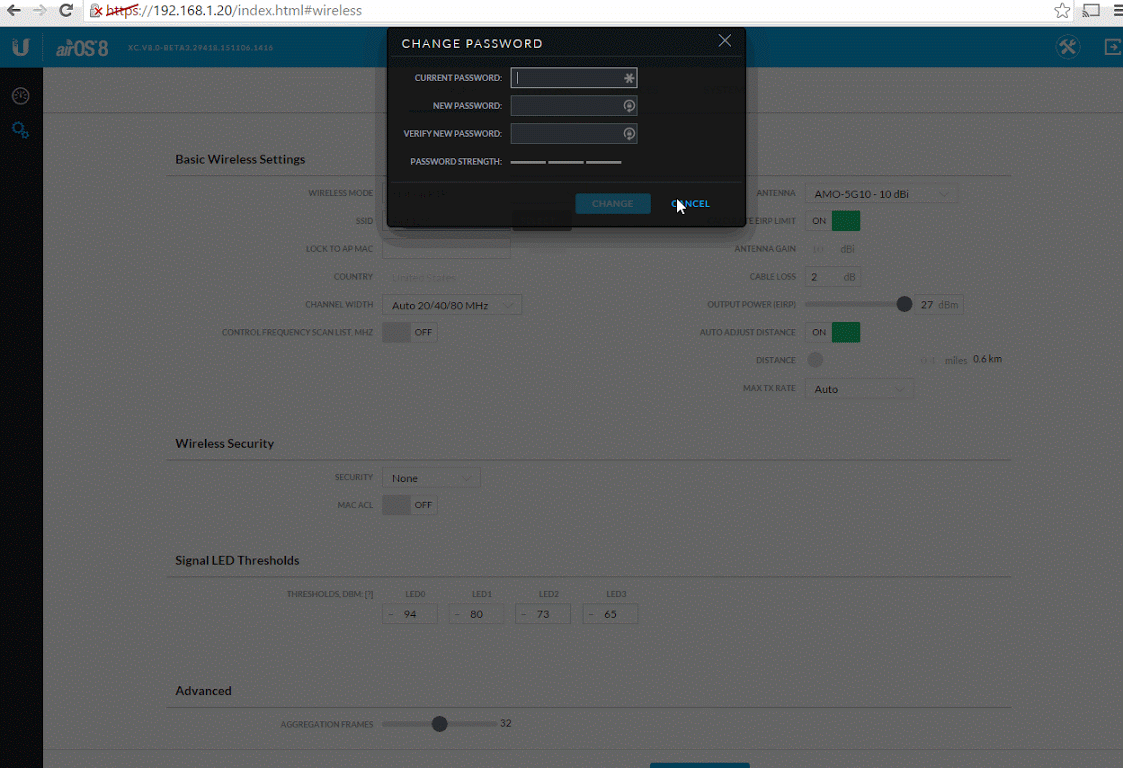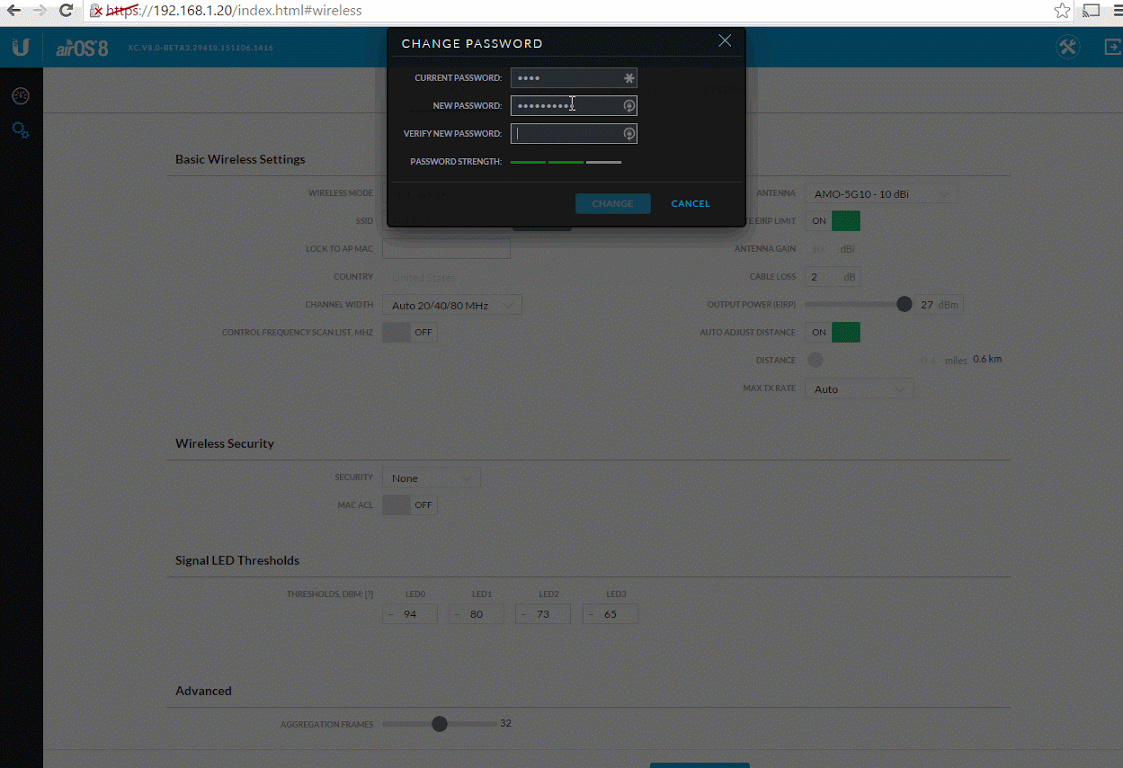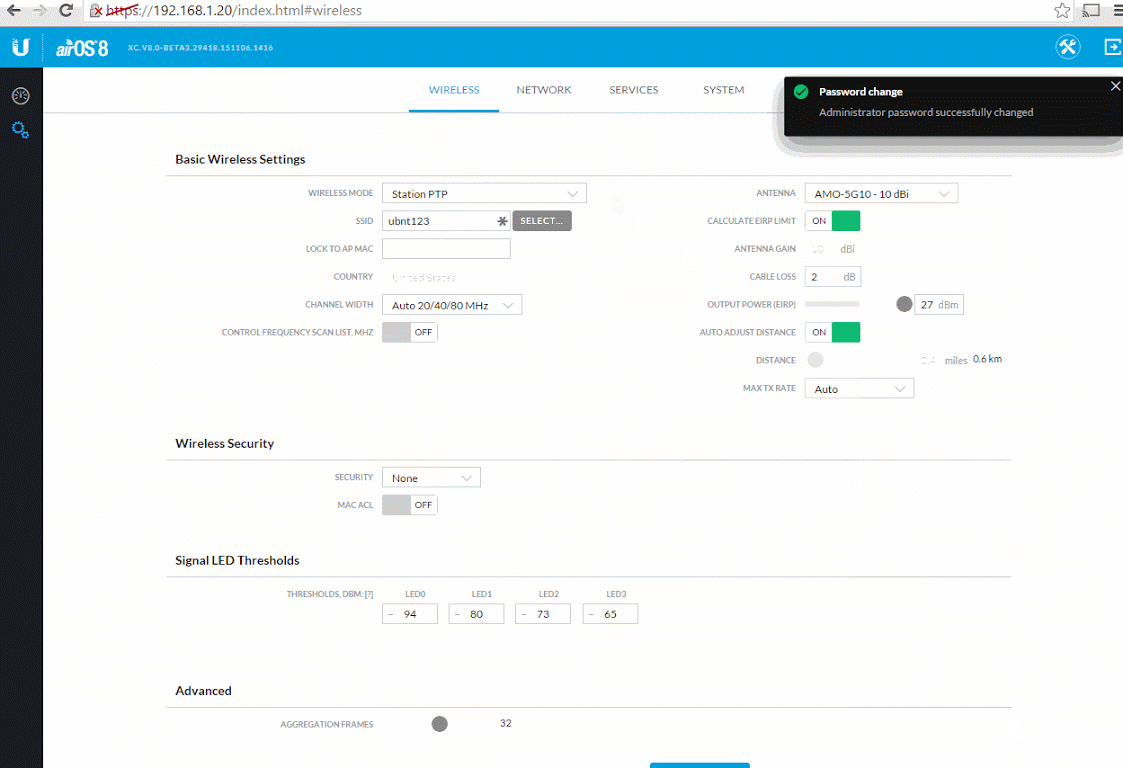
Ubiquiti’s nag screen asking users to change the default credentials. The company’s devices still ship with remote administration turned on.
ANALYSIS
When companies ship products, software or services with built-in, by-design vulnerabilities, good citizens of the Internet suffer for it. Protonmail — an email service dedicated to privacy enthusiasts — has been offline for much of the past week thanks to one of these shakedowns.
[NB: While no one is claiming that compromised routers were involved in the Protonmail attacks, the situation with Ubiquiti is an example of the type of vulnerability that allows attackers to get in and abuse these devices for nefarious purposes without the legitimate users ever even knowing they are unwittingly facilitating criminal activity (and also making themselves a target of data theft)].
Protonmail received a ransom demand: Pay Bitcoins or be knocked offline. The sad part? The company paid the ransom and soon got hit by what appears to be a second extortion group that likely smelled blood in the water.
The criminal or group that extorted Protonmail, which self-identifies as the “Armada Collective,” also tried to extort VFEmail, another email service provider. VFE’s Rick Romero blogged about the extortion demand, which turned into a full-blown outage for his ISP when he ignored it. The attack caused major disruption for other customers on his ISP’s network, and now Romero says he’s having to look for another provider. But he said he never paid the ransom.
“It took out my [hosting] provider and THEIR upstream providers,” he said in an email. “After the 3rd attack took down their datacenter, I got kicked out.”
For his part, Romero places a large portion of the blame for the attacks on the ISP community.
“Who can see this bandwidth? Who can stop this,” Romero asked in his online column. “I once had an argument with a nice German fellow – they have very strict privacy laws – about what the ISP can block. You can’t block anything in the EU. In the US we’re fighting for open access, and for good reason – but we still have to be responsible netizens. I think the ISP should have the flexibility to block potentially harmful traffic – whether it be email spam, fraud, or denial of service attacks.”
So, hardware makers definitely could be doing more, but ISPs probably have a much bigger role to play in fighting large scale attacks. Indeed, many security experts and recent victims of these Bitcoin shakedowns say the ISP community could be doing a lot more to make it difficult for attackers to exploit these exposed devices.
This is how the former cyber advisor to Presidents Clinton and Bush sees it. Richard Clarke, now chairman and CEO of Good Harbor Consulting, said at a conference last year that the ISPs could stop an awful lot of what’s going with malware and denial-of-service attacks, but they don’t.
“They don’t, they ship it on, and in some cases they actually make money by shipping it on,” Clarke said at a May 2014 conference by the Information Systems Security Association (ISSA). “Denial-of-service attacks actually make money for the ISPs, huge volumes of data coming down the line. Why don’t we require ISPs to do everything that the technology allows to stop [denial-of-service] attacks and to identify and kill malware before it gets to its destination. They could do it.”
One basic step that many ISPs can but are not taking to blunt these attacks involves a network security standard that was developed and released more than a dozen years ago. Known as BCP38, its use prevents abusable resources on an ISPs network (hacked Ubiquiti routers, e.g.) from being leveraged in especially destructive and powerful denial-of-service attacks.
Back in the day, attackers focused on having huge armies of bot-infected computers they controlled from afar. These days an attacker needs far fewer resources to launch even more destructive attacks that let the assailant both mask his true origin online and amplify the bandwidth of his attacks.
Using a technique called traffic amplification, the attacker reflects his traffic from one or more third-party machines toward the intended target. In this type of assault, the attacker sends a message to a third party, while spoofing the Internet address of the victim. When the third party replies to the message, the reply is sent to the victim — and the reply is much larger than the original message, thereby amplifying the size of the attack.
BCP-38 is designed to filter such spoofed traffic, so that it never even traverses the network of an ISP that’s adopted the anti-spoofing measures. This blog post from the Internet Society does a good job of explaining why many ISPs ultimately decide not to implement BCP38.
As the Internet of Things grows, we can scarcely afford a massive glut of things that are insecure-by-design. One reason is that this stuff has far too long a half-life, and it will remain in our Internet’s land and streams for many years to come.
Okay, so maybe that’s putting it a bit too dramatically, but I don’t think by much. Mass-deployed, insecure-by-default devices are difficult and expensive to clean up and/or harden for security, and the costs of that vulnerability are felt across the Internet and around the globe.
Dan Geer, chief information security officer for In-Q-Tel — the Central Intelligence Agency’s (CIA) venture capital arm — perhaps said it most eloquently in a May 2014 address at Cambridge. Geer talks about the Internet of Things in terms of a broader class of software+hardware devices dubbed “embedded systems” and their tendency to remain use long after they become potential security liabilities:
Perhaps what is needed is for embedded systems to be more like
humans, and I most assuredly do not mean artificially intelligent.
By “more like humans” I mean this: Embedded systems, if having no
remote management interface and thus out of reach, are a life form
and as the purpose of life is to end, an embedded system without a
remote management interface must be so designed as to be certain
to die no later than some fixed time. Conversely, an embedded
system with a remote management interface must be sufficiently
self-protecting that it is capable of refusing a command. Inevitable
death and purposive resistance are two aspects of the human condition
we need to replicate, not somehow imagine that to overcome them is
to improve the future.
Jeremiah Grossman, chief technology officer at WhiteHat Security, said the world will eventually grasp how important it is to build security into all of the new types of devices being plugged into the Internet each day.
“Only after Internet of Things devices get hacked en masse, and only after billions of internet-connected devices are deployed in the wild,” Grossman said. “We know this future is coming, and there isn’t a lot we can do to stop it. The question I’m asking myself today, is when that day comes, and it will, how can we address the IoT problem 5-10 years from now with billion of those insecure devices in circulation? I don’t have a good answer yet, but we’ve got time.”




I’m a customer of Vfemail net and I wasn’t happy on what happened last week
I used to work for a small WISP and we loved Ubiquiti. The reason we liked the remote administration is that we could plug in the AP to our network and it would be automatically configured. When you are configuring dozens and dozens of these APs, their system made it very easy. They are right in saying they are mostly sold to professionals and if the “professionals” do not change the password, then the blame lies with them and not Ubiquiti…..just saying.
The reason we rarely blocked infected computers was because the end users are clueless and we could’ve spent all day turning people off. There were many occasions where we did have to cut people off due to the infection affecting the network but otherwise it is incumbent on the end user to take their privacy (which they freely give away) and security seriously.
Remote access is great, but it (e.g. the specific IP/port combo) should be blocked from access from the internet. That way, you and customer support can access it, but not the ‘attacker’.
In fact this is just one of tons of attacks on various ISP routers/modems through the admin interface. Many larger ISP’s do therefore exactly that and turn access from the internet off through filtering.
I agree with your caveats, however we configured them on a private network (set to the private network where they would end up at) and then moved them to the location. You’d have to be inside the private network to access the Remote Configuration.
The closer the future comes the more scary it looks. As lazy corporation feel they do not need to increase security because it is either inconvenient or to costly, and as hacker become smarter and more adept, It becomes clearer and clearer that the consumer will be victimized more and more. The consumer becomes the hostage of corporate avarice. That is scary!
Just wondering why your website keeps having advertisements for an illegal pocket cell-phone signal blocker from pockethound . com.
It’s not a signal blocker. It’s a detector.
Jason,
I haven’t seen the ad, but these devices are not illegal everywhere. It is a big world.
Interesting. But, as one on the consumer side of this equation. Why? In other words, I bought a consumer usable device, I should expect it to work for me. Not someone else. Someone else did not give me the device. And therefore own it, I bought it with the understanding it is mine. Why are best practices not being followed, in the first place?
Was it really consumers that flooded the response channel, or the controller of the device? You know, the botnet denizen. And especially love the the CIA guy saying implode the internet, gunna be done by bad devices, no, more like someone will get to the backdoor and pull a plug.
Depends what you’re talking about. The devices @Brian started talking about were bought by the ISPs, not by consumers. The ISPs deployed them, possibly in a “you’ve signed up, here’s your AP” model.
If you bought the device directly from the vendor, then it’s your responsibility to turn off the remote access stuff or at least change the password. But when the ISP buys it, that’s the ISP’s responsibility, and apparently they’re frequently not doing a good job (I’m not remotely surprised).
Billions of IOT devices. A number that is hard to grasp, especially if you grew up in the 60’s. The advance of technology is daunting.
Perhaps we need to learn how to cope without all these nifty little devices that make our day “easier”. Good disaster planning should include ways to continue with our lives without using all this crap.
I foresee a day when we all go outside and rub our eyes in the bright light of the day and discover that the world is not as virtual as we have been conditioned to expect.
The more reliant we become on IOT the more powerless we are to control our own lives.
IOT. New controllable devices based off of TCP/IP data packets are endless. TCP/IP was not initially developed with security in mind. Vulnerabilities that exist today on the internet will exist in these new devices. The internet is running out of IP addresses with IPv4 and IPv6 is meeting resistance. Home monitoring and security systems controlled by new IOT technology over the internet. I don’t know, VOIP is bad enough.
Eh, what was that?
Apparently, my text-to-speech isn’t working (again)…
Billions of connected devices.
I call it “the Insanely Dangerous Internet Of Things,” and the acronym “IDIOT” is intentional as well.
Scenario: malware infects internet-connected refrigerators, causing them to cycle to “warm” when people are asleep or at work. Thereby causing pandemic food poisoning with no obvious common food source, and mass panic about bioterrorists embedded in the food supply chain.
And that’s hardly as bad as what will happen to robotic automobiles: “Pay us now or we’ll slam you into a hard surface at high speed.”
And all for what, exactly? Trivial convenience and the ability to live one’s entire life as a couch potato, never even having to lift a finger to click the Buy button because the machine will talk to you and you’ll reply by saying Yes.
This, we’re told, is supposed to be “inevitable,” but solving hunger and homelessness, disease and crime, not to mention climate change, are not supposed to be “inevitable.” We’re supposed to beg for those things, while we get endless new baubles shoved in our faces.
“My neighbor just got fired by a robot and is about to become homeless!” “Have another bauble!” “We haven’t had decent rain in five years and the last heat wave killed 30,000 people!” “Stop complaining and have another bauble!”
The “bauble bubble” is warping our culture, our sense of priorities, it’s threatening our basic security and safety, stealing our privacy and the freedom that privacy protects, and yet it’s supposed to be “inevitable” while urgent needs go unmet.
This is a definition of insanity: doing the same thing over and over again despite it being harmful.
Anyone with an IQ above room temperature (Fahrenheit) ought to dig in their heels and “just say NO.” No Insanely Dangerous Internet Of Things, no AI golems, no greed-driven agendas to foist stupid and dangerous things on us that we really don’t need and really don’t want.
That’s not “anti-technology,” it’s called being a “selective adopter” who thinks for himself or herself and makes deliberate choices, rather than mindlessly going along with whatever garbage is being dished out at the moment.
I expect car companies to become like airlines. Creating difficulties such as long lines so you can be offered the opportunity (for a fee of course) to avoid long lines with special security bypass options and early boarding. The counter-sardine option (called first class) has been around for years, but even it isn’t what it used to be. Baggage used to be … never mind.
Car companies can charge to REMOVE “standard” options like internet connectivity, but think of the police power in being able to stop escaping cars. Nice idea until you realize that the people stopping your car might not be the police. Congratulations: modern technology has delivered you into the hands of those who would do you harm.
Just because we can does not mean we should.
My opinion is the solution is we the human beings. Instead of playing cat and mouse let’s turn the table around. Let’s go the ecosystem and everybody in the ecosystem been to a ecosystem that’s lucrative and praiseworthy. There’s no way we would ever create a security system or feature that human being who has a billion brain neurons his head to not compromise. There is no effort or opportunity being created for people who do such things. As long as we continue to ignore people who need to be guided to the right ecosystem. Can be lucrative we shall never be safe as far as Security is concerned. I end with the beginning saying that the solution is with the people or the humans whatever you want to call them 🙂
Is, it really guidance or education. There are levels of both. Do we expect an 70 year old grandma to have the same expertise as a college age graduate? But they, the grandparents need the same levels of security as a government. Their information is even more valuable, its part of their lifeline. The government gets bailed out by its taxes, grandma has to move in with family. All colleges may teach the same courses, but the emphasis on importance of brands is bypassed. Or else you would probably just getting up to the “B”s.
The problem with the IoT concept is that they started with out of date assumptions, and went backwards from there. The Internet of Things is not a new idea. We have been doing this since before the Internet existed. It is called SCADA.
Things have changed. Despite more modern notions with event driven reports, encryption, authentication, and networking, the IoT folk were hell bent on solving a 30 year old problem with modern tools. Unfortunately for all of us, the target moved over a decade ago and they missed it.
IoT is a sick joke among most industrial security people. We call it Industrial Device Internet Of Things (IDIOT). I believe it will be stillborn unless they get serious about security. Right now, I don’t see that happening.
Exactly. My new HVAC system came with thermostat that can be connected to the internet via wi-fi. It will never be connected. I have my own wi-fi router that I control, not the ISP.
In the meantime, a friend has a Nest thermostat, his garage door opener and security system, including the cameras, are internet accessible. Fortunately, he has no need of a baby monitor, or he’d also have that on the internet.
Offered for your consideration an acronym
Inherent Dangers in the Internet Of Things
IDIOT
a sad joke and a warning in one. Soon manufacturers will charge to disconnect cars from the internet. Or add expensive “internet security” devices. Like airlines, they make regular use miserable or dangerous so they can “save” you from them by charging you for it.
Jonathan @nc3mobi
Heh, we both hit the same acronym, but my version (30 years in tech speaking here) is the Insanely Dangerous Internet Of Things.
See my other comment where I mention internet-connected fridges and pandemic food poisoning, and robotic automobiles as kidnapping machines.
Digital monkey-traps with shiny objects as bait.
“I foresee a day when we all go outside and rub our eyes in the bright light of the day and discover that the world is not as virtual as we have been conditioned to expect.” – NotMe
Love this comment! Thanks!
Besides routers, what about an ISP’s cable modems? How often are they compromised?
It used to be that consumer devices had easy default passwords (Linksys comes to mind.)
But that has changed in recent years.
AT&T’s U-Verse DSL modems, for example, have a preset password, but it a different one for each device, it is printed on a sticker on the device. And it is not easily guessable. So you really have to have physical access to the device.
End-users will never properly secure either their network or their devices.
Vendors know this and don’t want the support calls from grandma, so they set the defaults to work for most uses. Grandma doesn’t know any better. Either it works or it doesn’t. Security isn’t a consideration. She has better things to do.
And while this is very much true, there are ways in which vendors can deliver products without using default credentials that are the same for everyone.
Our FIOS routers come with what appear to be randomly generated passwords, where the password is given to the user by placing a sticker on the box (the router, not the box it came in). The user can change it of course, but the default configuration doesn’t leave them open to this sort of attack.
If you wanted to get a tiny bit fancier, you could put a barcode or a QR code on the sticker. Scan it with your phone, and it logs you in with the factory credentials.
Grandma doesn’t know any better, which is why she calls on her grandson, Jimmy. And Jimmy should know better, at least he if was trained properly.
But in many cases, the grandson is just a kid, and not trained at all – they just know enough to get the thing set up and working.
“This blog post from the Internet Society does a good job of explaining why many ISPs ultimately decide not to implement BCP38”.
What?? I interpret the post differently. The post says:
* “However, this argument starts to break down when we investigate the real costs of DDOS attacks, the real costs associated of installing filters to stop spoofing, and basic network management principles.”
* “I’ve talked with hundreds of network operators from around the world in virtually every industry. Never have I met a network operator who wants more malicious traffic on their network, even if they are simply transporting that malicious traffic.”
I interpret the society’s post as going against the stated purpose of the Internet Society, “open … use of the Internet for the benefit of all—which I’ve disagreed with that broad statement of their mission for awhile. Until I read this society post, to me the Internet Society mission includes promoting the use of the Internet for the benefit of miscreants to transit malicious traffic to the detriment of all. However, the society’s post moreso aligns with not-complete-internet-openess (openess, except for curtailing transiting malicious traffic).
Brian, could you give us an example of a commonly used embedded
system without a remote management interface.
I haven’t played w/ IoT items, I’m confident they’re a disaster in the making.
http://wirelesstag.net/
Describes a system where individual items just report to their master. (I say “describes” because I just searched for a likely device, I don’t own any and have absolutely no experience/relationship/knowledge of the details of this brand — i.e. this isn’t an endorsement.)
If you treat the individual tags as things (which I think they are), I don’t think they have a local management interface. Instead they broadcast their data to a manager.
This isn’t an unreasonable design. And for power reasons, it makes a lot of sense. You don’t want each tag to run a web server with a complicated management system.
Now, it’s true that the manager will have some form of administrative interface, but it’s quite possible that it won’t be able to send commands to some of those tags, merely choose to ignore them.
Brian, you touched a bit on things hardware manufacturers can do. Device makers have quite a bit of influence over the end state of their products. Not control (as a consumer I can do things the manufacturer didn’t intend), but influence (the vast majority of consumers take a thing out of the box, go through the default setup process, then forget about it).
Defaulting to a reasonably secure state would curb much of this abuse – and isn’t that hard.
> Build into the setup sequence a step to require a new password (preferably a strong password, but even a weak chosen password is better than a known default).
> Provide automated software and firmware updates, enabled by default, and guaranteed for the reasonable lifetime of the product.
> Features that impact privacy and physical safety should be clearly presented so the owner can make an informed decision whether to use the feature.
As Jeremiah Grossman said in the quote you printed, IoT is going to continue to grow, but it’s not too late to shape how it grows. I have hope that the “Cyber UL” led by Peiter Zatko may eventually influence manufacturers to start going in this direction.
> Provide automated software and firmware updates, enabled by default, and guaranteed for the reasonable lifetime of the product.
And notification of the approaching EOL to all registered owners of the product so they can replace the product with something newer if they so desire.
Secure passwords aren’t what people think they are.
The reason that Gmail is secure isn’t because you have a long password, it’s because if you try to enter the wrong password X times, Google will stop letting you try and make you do something special.
Devices rarely have this. If you enter the wrong password a million times, they’re typically quite happy. Which means something can just try *all* passwords until it gets in.
Unfortunately, I do agree w/ Dan Geer, devices should have a shelf life (2-3 years) — probably in the form of a non replaceable battery that will expire in 2 years of use. And devices should be more of a lease system, where returning them gets you a deposit refund (ala glass bottles).
A device will have security vulnerabilities, and eventually one of them won’t be fixable through a software update for one reason or another.
Until Brian does, I can:
Almost every HD TV which can stream Netflix has the equivalent of a router built in. Many are Linux boxes with ARM processors, most are not remotely administrateable.
“Smart TV” for internet connectivity.
Now if they could only invent a way to create programs that are worth watching.
Thanks, you two!
Though, not having a remote management interface, doesn’t prevent a device from being hacked. Also, Internet devices may be hacked in other ways besides only through remote management, there are many catagories of networking and device vulnerabilities. Hacked Smart TV:
https://blog.avast.com/2015/11/11/the-anatomy-of-an-iot-hack
They may not be capable of being remotely administered, but if it gets exposed to the internet, it is capable of being remotely exploited. A fixed version of Linux with a fixed version of software on the network with no hope of ever being updated beyond a once in a lifetime chance of the OEM giving a crap about after-sales support. The most they do is update support for services, which usually doesn’t require updating the OS, just configuring the existing services.
Business shakedowns isn’t new, the Internet is a new opportunity. The problem is business rushed in without first putting in and testing the locks on the doors. They figured too much money to make and now they are turning some of it over to the crooks. Face it, it was too good a chance for thief’s not to use it. To late now, but the big corporations should have proceeded more slowly. Business for the most part didn’t do its homework.
What a fantastic post. Thank you.
How can an end user know if his or her modem has been hacked? I can use Wireshark to see if it is creating traffic within my internal network but what it does on the WAN side is invisible to me. Are there any tools that can help?
It’s not necessarily about knowing if it is hacked, but knowing if it is vulnerable and and updated against known vulnerabilites.
I vulnerability doesn’t have to be immediately used as a hacking entry point; it may be used in the future.
If you had a switch with a monitor port, which basically means all traffic going into port A gets mirrored to port B, you could monitor the traffic hitting your router and going away from your router.
With third party firmware you can monitor the volume of data leaving your router, not to mention all interfaces, and if the data on the WAN port exceeds the total of data on all other interfaces (LAN, WLAN) then you know your router is being exploited.
Thanks, that sounds good, except that my WAN facing device is an ADSL modem/router. I don’t see how I can get visibility to the WAN side – essentially the phone line.
Most (all?) ADSL modem/routers can be dumbed down to modem-only mode (or bridge mode). Then you can attach a proper router behind it (the router function in ADSL modem/routers is crap anyway) or a firewall and then a router.
It can be done, but 80% of the people won’t commit to this “trouble”.
Thanks, although I don’t know how to do that yet.
If I achieve bridge mode, does it help? The modem can still be taken over from the WAN side and used to do whatever on the WAN – and I still cannot see that traffic. The advantage is that the modem cannot see local traffic, but in my case there isn’t any. Is there any other advantage?
I agree that ISP’s need to do a much better job protecting their networks and their customers. My ISP inbox frequently contained email allegedly from the ISP. Of course it was spam or phish. On the support forum I pointed out that since the source was allegedly from the ISP, the ISP owned the network, and the recipient was an ISP customer, the ISP would be able to detect and eliminate this fraudulent impersonation. After all, doesn’t the ISP use such controls for their own internal employee network? But that argument fell on deaf ears for many years. Recently it has been reduced, probably due to Kreb’s book and reporting.
Simultaneous DDOS attacks on six sites with one thing in common – encrypted email services. Each has a link so you can see the comments. Six at once? That is no coincidence.
Protonmail Nov 5-9 https://twitter.com/Protonmail
VFEmail Nov 5-8 http://www.vfemail.net/ tweets
Neomailbox Nov 4-7 https://blog.runbox.com/
FastMailFM Nov 8-9 http://www.fastmailstatus.com/
Hushmail Nov 7 https://help.hushmail.com/entries/107539976
Runbox Nov 5-7 https://twitter.com/Runbox
Vfemail.net might be shutting down because of ongoing attacks.
ProtonMail has already released a statement saying they believe state-actors are behind the second, more damaging attack. They also said that there was no ransom demand or credit taken for the second attack; plus the people who acknowledged the first attack, disavowed any responsibility for the second, adding that the people behind it control some massive power.
Intelligence agencies trying to do away with encrypted mail providers? Who is worst these days? the criminals or the rogue elements of our governments.
I would hate to think that people were getting confused between ‘Wifi login’ vs. ‘admin login’.
Where as Wifi does need to be secured, logging into Wifi only allows internet access and network access. It’s the same as wired with ethernet, only without the wire.
It is admin login the represents the biggest problem for the router itself as this is where all the settings for the router are made which includes remote administration. It is THIS password that usually gets completely ignored and IS the password that is default among manufacturers.
Many ISP modems with built in routers will have a sticker with a default Wifi login. This is NOT really the problem. THE problem is that most (if not all) of a particular brand modem have the same default admin login credentials (username=admin password=password).
is there a simple way to detect if your ubiquiti product is infected?
I’m asking for a friend.
Some this is much the same argument as made by Josh Corman and the I am the cavalry folks:
https://www.iamthecavalry.org/about/overview/
By the time I considered myself proficient enough to consider and deploy Ubiquiti hardware, I already knew well enough to change the default login as the first thing to do. Remember that Ubiquiti doesn’t sell your average “1-click-setup” [random consumer brand] router. They do sell fantastic networking products that until a few years ago were not affordable for many because of Cisco pricing.
I agree with others that Ubiquiti is not to blame, their product’s default config matches with what they can realistically expect from their intended audience. It’s the fault of the human who deployed it without changing the login.
Can someone write a script to change the passwords of these Ubiquiti routers still set to default to a random 16 characters?
Almost certainly, but at least whomever *ran* that script, and probably whomever wrote that script could be charged with a crime.
You almost need some sort of amnesty provision to enable white hat hackers to be silver hat (deputized) in order to do anything helpful proactively.
There are examples of things like this, but basically it involves a big company filing a lawsuit and asking a court for permission to do stuff. For this specific case, I don’t think anyone would have particular grounds, unless they perhaps could show that they were being attacked by the devices, in which case, perhaps they would…
Would this tend to lock the people out of their own routers? Sounds like a problem where they would reset the routers and get back the default password.
How about detecting the default and sending them a message about it with a note “In 2 days we’ll test again and if the default password is still effective we’ll publish your weakness. We’re happy to provide you this service and request 0.00 BitCoins.”
Jonathan @NC3.mobi
What a stupid idea to give a short lifecycle for the devices. Like we are already not over-consuming and throwing away hundreds of equipment just because the version has a nicer color/login page. We already have this nonsense with mobile phones, when after 2 years it is expected for the perfectly functional phone to be replaced, and no software updates come from either carrier or manufacturer.
Speaking about the ddos, there are still over 20 % of networks who allow IP spoofing. Just by presuring those networks to clean up their act would help tremendiously in case of the latest amplification attacks.