Ransomware — malicious software that encrypts the victim’s files and holds them hostage unless and until the victim pays a ransom in Bitcoin — has emerged as a potent and increasingly common threat online. But many Internet users are unaware that ransomware also can just as easily seize control over files stored on cloud services.
 Toni Casala found this out the hard way. Casala’s firm — Children in Film — works as an advocate for young actors and their families. The company’s entire operations run off of application hosting services at a managed cloud solutions firm in California, from QuickBooks to Microsoft Office and Outlook. Employees use Citrix to connect to the cloud, and the hosting firm’s application maps the cloud drive as a local disk on the user’s hard drive.
Toni Casala found this out the hard way. Casala’s firm — Children in Film — works as an advocate for young actors and their families. The company’s entire operations run off of application hosting services at a managed cloud solutions firm in California, from QuickBooks to Microsoft Office and Outlook. Employees use Citrix to connect to the cloud, and the hosting firm’s application maps the cloud drive as a local disk on the user’s hard drive.
“We were loving that situation,” Casala said. “We can keep the computers here at work empty, and the service is very inexpensive when you compare it the cost of having more IT people on staff. Also, when we need support, they are very responsive. We don’t get farmed out to some call center in India.”
They were loving it, that is, until just before New Year’s Eve, when an employee opened an email attachment that appeared to be an invoice. Thirty minutes later, nobody in Casala’s firm could access any of the company’s 4,000+ files stored on the cloud drive.
“Someone in my office was logged into Outlook and opened up invoice attachment and BAM!, within 30 minutes, every single file on our Q drive had ‘vvv’ added as file extensions,” she said. Every single folder -had a file that said “help.decrypt,” essentially the attacker’s’ instructions for how to pay the ransom.
The cloud provider that Casala’s company is using was keeping daily backups, but she said it still took them almost a week to fully restore all of the files that were held hostage. She said the hosting service told her that the malware also disrupted operations for other customers on the same server.
Casala said her company got lucky on several fronts. For starters, the infection happened right before her firm closed down operations for the New Year’s break, so the outage was less of a disruption than it might normally have been.
More importantly, the malware that scrambled their files — a strain of ransomware called TeslaCrypt, contained a coding weakness that has allowed security and antivirus firms to help victims decrypt the files without paying the ransom. Users over at the computer help forum BleepingComputer have created TeslaDecoder, which allows victims to decrypt files locked by TeslaCrypt.
Casala said the hosting firm had antivirus installed on the server, but that the ransomware slipped past those defenses. That’s because the crooks who are distributing ransomware engineer the malware to evade detection by antivirus software. For more on how cybercriminals achieve that, see Antivirus is Dead: Long Live Antivirus.
The best defense against ransomware is a good set of data backups that are made each day — preferably to a device that is not always connected to the network. Unfortunately, this is often easier said than done, especially for small businesses. For many ransomware victims who do not have backups to rely upon, the choice of whether to pay comes down to the question of how badly the victim needs access to the ransomed files, and whether the files lost are worth more than the ransom demand (which is usually only a few hundred dollars in Bitcoin).
Many readers may have a hard time believing that ransomware peddlers will actually return the encrypted files to their original state if the ransom is paid. But cyber criminals who run these schemes have a vested interest in making sure the transaction is a relatively seamless one: They understand that if word gets out that victims aren’t getting their files back after paying, fewer victims will pay. What’s more, the amount demanded in ransom is about hitting that sweet spot: Thieves know that if they demand too much from each victim, they’ll have fewer victims who end up paying.
That said, ransomware is computer code, and even malware coders make mistakes. Every so often, crooks will release a new version of ransomware that contains critical programming errors, effectively rendering the victim’s files unrecoverable even if they do pay the ransom.
One big reason that ransomware scams are becoming more prevalent has to do with the proliferation of plug-and-play tools and services that make it simple to start your own cybercrime syndicate. Earlier this month, security firm Emsisoft published a fascinating look at a crimeware-as-a-service product being marketed in the underground called Ransom32, which allows anyone to start their own ransomware campaign just by providing a Bitcoin address to which victims will be asked to send the funds.
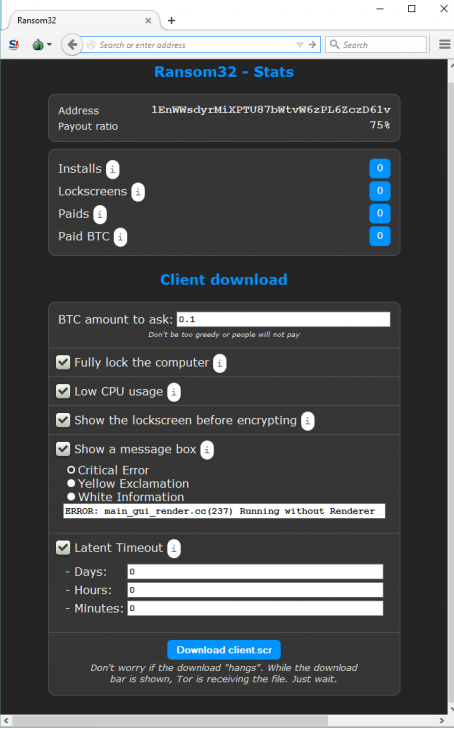
The crimeware as a service ransomware package, Ransome32. Image: Emsisoft.
“After you type in your Bitcoin address, you will get access to the rudimentary administration panel,” the company explained. “In the admin panel, you can get various statistics, like for example how many people already paid or how many systems were infected. You can also configure your “client”, which is their term for the actual malware. It is possible to change the amount of Bitcoins the malware will ask for, as well as configure parameters like fake message boxes the malware is supposed to show during install.”
According to Emsisoft, the Ransom32 crimeware service also includes a feature that offers to decrypt a single file to demonstrate that the malware author has the capability to reverse the encryption.
It seems to me that ransomware attacks have a great deal of room for growth. I would expect criminals who have the skills to construct and manage their own ransomware campaigns eventually to begin doing a better job targeting victims — that is, taking the extra time to get a better idea of how much the ransomed files are worth, and then adjusting the ransom demand accordingly.
If you or your company is hit with ransomware, resist the temptation to pay up, which just perpetuates these scams. Take a deep breath, head on over to BleepingComputer’s ransomware removal section, which includes resources that may allow you to recover files without rewarding the crooks.




Cloud services like OneNote usually have the ability to recover old versions of files. That’s how I would proceed in such a case
After this incident, other cloud storage services should also reconsider their security policies.
A/V on the hosting wouldn’t detect the infection because the malware was on the local computer and it was just reading and re-writing the files on the Q drive which would just look like normal activity to the server A/V.
Maybe best practice here is not to have the cloud service drive mounted all the time?
Thank the gods for good backups…
They can configure to scan files on write.
The files that were written are just the encrypted versions of the user’s original file. On its end the server is not seeing anything suspicious. Scanning the files would not help.
In fact, there are actual encryption services that do the same thing – the only difference is that the user has the decryption key 🙂
Please elaborate on how scanning an encrypted file helps here.
AV detection is signature based and the compromise happened at the host system, not in the cloud. AV in the cloud would produce zero results since they were all compromised (& encrypted) at the host before being written back to the cloud. The cloud itself is pristine except for the encrypted files.
Now, if you want to talk about scanning for those help files, maybe but that is generally done after the files are encrypted.
which is useless when it is encrypted.
I’m sure I’d pay a lot more than the average ransom to get back pictures of my deceased child. Fortunately, I have multiple offline copies of them, including offsite, so I don’t have to worry about that.
However, I can understand how there are people who would pay to get various files back, no matter how much that encouraged the criminals.
Holy crap that got dark in a hurry
I’m sorry, I was just trying to give an example of why some people would pay a ransom, other than the usual example of a small business that has had all their business records encrypted.
I feel for you Bob, I can’t imagine what that would be like, my condolences.
I’d be exactly the same, willing to pay quite a hefty sum, especially if I lost one of my two kids.
Some people don’t understand why I take so many photos or keep them all, they’re just as much an insurance policy and memories for 50+ years in the future as anything else.
I have almost a terabyte of photos now that I keep multiple copies of, I’d be devastated if I lost them.
A company I used to work for got hit by ransomware in November. They were saved by having a recent backup that they could restore to.
Per Brian’s comment about the perpetrators getting more sophisticated: in this instance the ransomware had shut down the business of a manufacturing and retail company with over 500 employees, but the ransom was just the amount that you would expect a “home user” to pay. Fortunately the company was able to restore data, but if they did not have the backups, and the crook knew that they had actually shut down a somewhat large business, they would have asked for a whole lot more.
“the hosting service told her that the malware also disrupted operations for other customers on the same server.” < so much for tenant isolation
John C, you misunderstood. All they are saying is other customers had been hit by the ransomware.
Remember, it is NOT running “in the cloud”. It’s just local software, reading and writing cloud-based files. The cloud is ONLY file storage in this case.
All five companies I have worked four in the past four years were hit by one type of ransomware or another. 4 out of 5 times, there were no backups available (wtf) and only once was I able to recover local user data (CryptoWall-infected user data was recoverable with a utility called ShadowExplore.) One of the companies was in the medical insurance field and their corporate proprietary-app servers got an earlier version of Cryptolocker on them. If only the ransomware-planters knew the name of the company they attacked I’m sure the ransom would have been much much greater, as Robert states above. It was a treasure trove of PHI. The idiot execs actually thought about paying the ransom after stressing out for two days while we worked on getting things back to normal… fun times.
The most common cry heard was “but I thought we had antivirus”… every single infection was caused by a rouge email attachment. Ransomware is a main reason why I believe anti-virus software is a joke and one of the most profitable scams ever created.
Unfortunately we can’t install AV on people, but we can use layers of security to lessen the likelihood and impact of these events.
So whatever happened to CryptoPrevent? Had your staff been aware of it? It is available at majorgeeks(dot)com. Don’t let the authors company name dissuade you. Foolish IT is a legitimate company. I think you can get it at the author’s site, and places like Wilders Security Forums and bleepingcomputer(dot)com
One of the clever solutions provided to help prevent the infections in the first place was Cryptomonitor. Suspiciously, the site went down, and we haven’t seen anything from it’s developer, “Nathan” on the BleepingComputer boards since… The thread is on their forum, just look for the app name.
From what I was told, Nathan had some issues with his hosting provider and is trying to get it straightened. That partnered with a currently busy work schedule for him has made the process a bit longer than expected.
Brian, thanks for mentioning us. We are working hard on helping people as best as we can.
The TeslaCrypt devs unfortunately just released version 3.0, which closes down that vuln in their code we were exploiting to decrypt people’s files. We can still, though, help those who were encrypted by the earlier variants.
What about CryptoPrevent – have the criminal coders found a way around that too?
The reason why people open email attachments is Microsoft’s stupid decision that the default on Windows installation is ‘do not show file extensions’ (View options) so that for example ‘invoice.exe’ just shows as ‘invoice’.
If the extensions were shown and the file was named “invoice.virus” or “get.infected” users would still try to open it, especially if it has a spoofed from address of someone they know.
This is one of the reasons I have put three defenses in place to stop this. First, .js files now open in notepad per group policy. Secondly, I use Software Restriction Policies to prevent email attachments from executing.
Finally, I have most users trained to forward any suspicious emails to us. If in doubt, send it. Most of the time multiple people get the same malware ladden email. With Fireamp, we can write a custom signature and have it pushed out to all our systems in 15 minutes. A race, but at least we have a shot of winning.
@Robert ” I have most users trained to forward any suspicious emails to us. If in doubt, send it.”
That reminds me of a story. Many years back, I received what appeared to be some malware in a mail message. Since I read my mail using a text mail program on a Unix system, it had no effect on me. But I forwarded it to the mailing list our Windows admins so that they could warn our Windows users.
Our CIO was rather pissed at me – it promptly infected her computer. My response was that if she were going to read mail on a list that was highly likely to contain copies of dangerous emails with a mail program as vulnerable as Outlook was in those days, she had only herself to blame. (I also pointed out that the message *had already made it through all their filters* – it reached me from an outside address.)
— Jerry
I wonder how much protection is offered by Linux/windows? (I realize I’m being selfish here – corporations are not going to switch away from windows.)
If it is possible for you to encrypt data on you Linux OS than it is possible for the malware to encrypt data on your Linux OS – it just depends on whether the malware is coded to run on your platform. I know of no popular platform that isn’t just as vulnerable, especially if you use cloud service to backup. It may reduce your chances of getting hit. but just look at the problems the popular Android has on mobile devices, and you can see an example of what I mean.
It actually would be harder to infect people by email attachment under Linux. The reason is, Linux completely ignores file extensions when deciding whether a file is executable or not. To execute a file on Linux you have to set the execute bit and that’s not something that can be done through an email client.
It’s difficult to imagine that ransomware or any other kind of infectious software wouldn’t be able to infect remote computers any differently than a home or office machine. Cloud services are not anything more than remote servers somewhere out on the web. Wether these computers use solid state drives or conventional platter based drives is irrelevant. They all would seem just as vulnerable. Is the thinking that a cloud service provider would be using better a/v software? If so, well, isn’t it obvious that a/v just doesn’t catch many of the things that we think it should?
I guess I just don’t see how anyone could think that cloud servers are safer from these kinds of things. It just makes sense to me that they would be just as susceptible.
I’ve had users claim Carbonite cloud service is invulnerable to this attack, but I really don’t know for sure. Maybe they just have a good backup plan in their organization.
When has there EVER been ANYTHING in this life (particularly in the arena of IT/web/computers/electronics/gadgets) that is actually “invulnerable”? If such a state of being were possible, this website would not even exist and Krebs would have little to write about. We do what we can (or so we say) to insure the safety and security of our data, but nothing is invulnerable.
They said that the Titanic was unsinkable…..
One of the big problems is the failure of mail platforms like Google Apps to prevent phishing attacks. I’ve had users get hacked since the emails clearly had phishing links. Since the sale of Postini to Google, all the good functionality of Postini is gone. Vendors are doing a poor job of screening emails.
I backup my files to the cloud, then backup the backup files in the cloud to another cloud. I haven’t done a backup of the backup of the files in the cloud that are a backup of the local files, because this sentence is getting too convoluted.
IT should strongly consider storage that offers continuous snapshots that are read only. I’m no salesman, but Exablox makes an intriguing system.
When the recommended primary defense for malware is to do daily backups of data, then there is a systemic problem. Time to start thinking of systemic solutions! I don’t hear entomologists saying, “We must identify all the bugs before we can do anything to really protect the environment.” Why don’t they say this? Evolution of course. There will always be new bugs! It is time to quit solving the symptom (receiving not previously cataloged malware) and start solving the problem (undetectable malware that is able to execute).
I get your analogy, but one nitpick..im pretty certain its not bugs destroying the environment.. Its humans
There were so many ways this could have/should have been stopped. Security is about defense in depth, not just depending on anti virus (which should have stopped a .exe attachment). At least a few of our layers would have stopped an .exe attachment from ever having the chance to be double clicked on and a couple layers would have stopped it from delivering the ransomware.
First, great article Brian. Ransomware attacks are appearing at an unprecedented rate, whether they are small as in this case or larger like the recent BlackEnergy KillDisk malware that is being accredited for wiping the files of a Ukraine energy company.
Rick, I agree with your defense in depth statement, though malware is finding its way into networks despite even the most sophisticated security infrastructure. It is why a different approach is being taken and a shift is occurring where detection technology is being added to prevention solutions. For example, deception lures and engagement servers will deceive an attacker into engaging, providing immediate detection and an alert with forensics on the infected system, enabling immediate remediation action to taken. In the case of CryptoLocker and KillDisk, deception would have been able to in real-time detect the attacker in the network as they looked to infect additional systems.
“malware is finding its way into networks despite even the most sophisticated security infrastructure”
You miss my point. I’m not saying my security would stop a nation state or all attempts. I’m saying any real decent security would stop something as simple as an .exe file from ever having the chance to be clicked on. There’s nothing sophisticated about the failure here.
And who says it was an Exe file?
Please check your list of blocked file types. Do you block all email with *.com, *.pif, *.wsh attachments and more? How about *.zip?
If you do block *.zip, how do your users share files?
The problem is that with sophisticated social engineering, attackers can get a surprising number of users to open a file.
“Please check your list of blocked file types. Do you block all email with *.com, *.pif, *.wsh attachments and more? How about *.zip?”
We block all kinds of attachments that can be executed, yes. Not just .exe.
More importantly, we’ve trained on security too. Our admittedly small user base is pretty unlikely to run something they shouldn’t and our layers would either not have let it through and/or not let it execute. For example, group policies forbid executables running in appdata, a common attack approach.
We also certainly have backups but having to rely on them is obviously not a first choice.
We’re not a typical small business, I know.
We should have multiple options to mitigate such problems.
Instead of backup, there should be Versioning of all files on the cloud.
Email providers should block downloading of auto-executing files to the client computers.
Critical files should be backed up daily.
At one time, prior to retirement, I delt with many encrypted e-mails. If things have not changed since the early 90’s, they all come with an “exe” attached.and the other derivatives attached ched. If they blocked one, they would effectively have to block all. That’s the only good thing of embedded systems for opening a suspect fish.
Some interesting approaches to find a solution, but no amount of backs are going to stop users opening email attachments, clicking link and running download applications. Isolation and containment of such files on the host is a very effective way of mitigation the risk before it becomes a problem – a proactive approach rather that reacting to something once it is detected or already become an issue.
When its addressed as a “Q” drive, its the same as a mapped drive. If you have access and privs to access the drive it too will become a victim of the encryption as well.
I don’t know enough about the ransomware internally, so know if the least privilege and strict permission sets (everyone having their own file tree) and a common dumping ground will ease the pain.
a 2-4TB external drive can save a copy of most files that are commonly accessed. Its a simple unplugging of a external drive power cable, and on a routine basis, that 10 second a day process can save the day. Backup software can make the process easier, on a timely daily routine. plug it in for 30 minutes a day, backup, and unplug.
When I started reading the article, my immediate thought was trimming the budget. The next question in the think tank was, how does this affect the security posture there?
The problem with this malware, if you will, is that its almost polymorphic in it self. Parts of the file change, which change the generic signature of the file, and the Antivirus signature might miss this all together.
So are you saying using CryptoPrevent a waste of time? Maybe the malware coders found a work around to that solution too!
I’d like to know who this “cloud” provider is. According to what was mentioned in the article they don’t do basic file server security correctly.
If you have something valuable why keep it on a server or servers in the cloud? I will never understand the cloud storage of personal files for anything, especially anything important.
For business, yes it is convenient. It is also dangerous.
Backup storage is cheap and prevalent and various these days.
This is not a personal attack on anyone. I don’t believe all technology is de facto good and cloud storage is an example of what is not good.
After all, we live in the age of hack and attack.
Cloud storage/backup seems like a easy answer until it’s not. As you said …why do it? Memory is cheap, unplug from net, back up to isolated drive never on net,.future problem not there if some net system hacked as back up never exposed.
So what if the attach package is sleeping on your system, and waiting for the day you back it up too?
It sounds like they had the drive mounted as a Windows network drive. It’s possible (I’d say likely) the ransomwere had no idea the files were in the cloud.
Since Windows Vista, Microsoft has enabled by default Volume Shadow Copies. Shouldn’t a user be able to revert to an earlier shadow copy and be able to access all their files? I realize that this won’t work with a Cloud service, but on a local computer, why shouldn’t it? I’ve never seen any discussion of VSCs in connection with Ransomware. Does anyone know for sure whether it works or not, in terms of unlocking the files by reverting to an earlier shadow copy?
Somebody mentions an app called Shadow Explorer or something like that earlier in this discussion; maybe you could check that out. I’ve never had a chance to test it.
Lots of ransomware disables VSS and nukes all existing shadow copies before encrypting the files.
One thing that is worth doing, is always ALWAYS make a forensic image of all the infected drives. even if the data isn’t recoverable at the moment there is a small chance that at some point in the future the server hosting the keys may end up being seized.
Also sometimes there are fragments of the original files in slack space etc, again with improvements in technology it might be possible to use these + encrypted files to get them back eventually as long as you have a forensic image of the entire drive.
Also don’t forget allot of early variants and even some current ones just delete the files after encrypting them, leaving the books in the library just destroying the card catalog. If you IMMEDIATELY take the drive offline minimizing the possibility that the deleted files get over written, you may just be able to recover those deleted files sitting in what is now unallocated space.
As soon as you find out you are infected take Conundrums advice make a forensic image and do an analysis, you may just find that a majority of data is still there. Even if it’s just some of it, that’s better than nothing
Would putting your email account on a VPN network work? You would only loose your email then.
I have a home network with multiple PCs …etc.
I purchased cryptoprevent as soon as it was available and installed it on every PC on the network.
As far as I know it stops more than just cryptolocker because most of those types of malware must infect the registry to do their dirty work which cryptoprevent prevents.
I purchased cryptoprevent as soon as it was available and installed it on all the PCs in my home network.
It’s supposed to be able to stop more than cryptolocker because they all must infect the registry which cryptoprevent prevents.
I think here it’s the same thing covered: http://www.anti-spyware-101.com/remove-ransom32 though I am not sure about getting the encrypted files back.
It would be nice of these kinds of articles would name how the attacks work. In this case, what was the email attachment? Was there social engineering tricks aside from the obvious work ‘invoice’? It is not enough just to describe the results, we need to know how the problem presented itself.
This report may be worth reading…
http://cyberthreatalliance.org/cryptowall-report.pdf