Staminus Communications Inc., a California-based Internet hosting provider that specializes in protecting customers from massive “distributed denial of service” (DDoS) attacks aimed at knocking sites offline, has itself apparently been massively hacked. Staminus’s entire network was down for more than 20 hours until Thursday evening, leaving customers to vent their rage on the company’s Facebook and Twitter pages. In the midst of the outage, someone posted online download links for what appear to be Staminus’s customer credentials, support tickets, credit card numbers and other sensitive data.
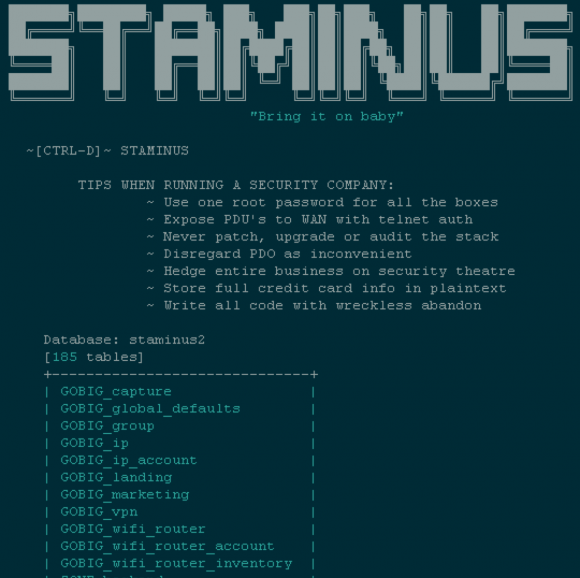
The e-zine posted online Thursday following an outage at Staminus Communications.
Newport Beach, Calif.-based Staminus first acknowledged an issue on its social media pages because the company’s Web site was unavailable much of Thursday.
“Around 5am PST today, a rare event cascaded across multiple routers in a system wide event, making our backbone unavailable,” Staminus wrote to its customers. “Our technicians quickly began working to identify the problem. We understand and share your frustration. We currently have all hands on deck working to restore service but have no ETA for full recovery.”
Staminus now says its global services are back online, and that ancillary services are being brought back online. However, the company’s Web site still displays a black page with a short message directing customers to Staminus’s social media pages.
Meanwhile, a huge trove of data appeared online Thursday, in a classic “hacker e-zine” format entitled, “Fuck ’em all.” The page includes links to download databases reportedly stolen from Staminus and from Intreppid, another Staminus project that targets customers looking for protection against large DDoS attacks.
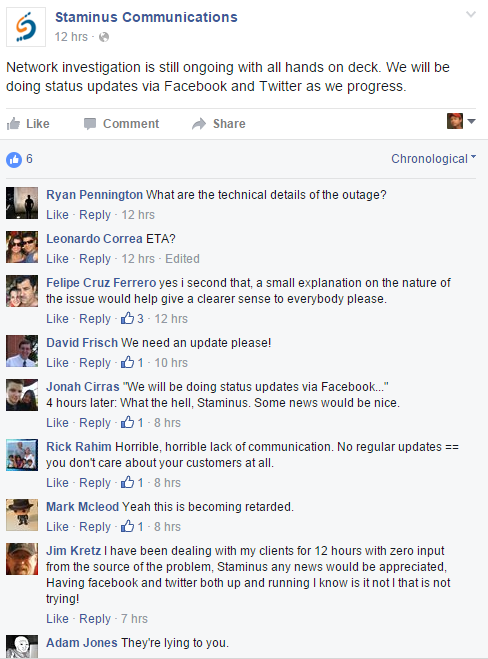
Frustrated Staminus customers vent on the company’s Facebook page.
The authors of this particular e-zine indicated that they seized control over most or all of Staminus’s Internet routers and reset the devices to their factory settings. They also accuse Staminus of “using one root password for all the boxes,” and of storing customer credit card data in plain text, which is violation of payment card industry standards.
Staminus so far has not offered any additional details about what may have caused the outage, nor has it acknowledged any kind of intrusion. Several Twitter accounts associated with people who claim to be Staminus customers frustrated by the outage say they have confirmed seeing their own account credentials in the trove of data dumped online.
I’ve sent multiple requests for comment to Staminus, which is no doubt busy with more pressing matters at the moment. I’ll update this post in the event I hear back from them.
It is not unusual for attackers to target Anti-DDoS providers. After all, they typically host many customers whose content or message might be offensive — even hateful — speech to many. For example, among the company’s many other clients is kkk-dot-com, the official home page of the Ku Klux Klan (KKK) white supremacist group. In addition, Staminus appears to be hosting a large number of internet relay chat (IRC) networks, text-based communities that are often the staging grounds for large-scale DDoS attack services.




I found this interesting because Staminus is one of the networks that was hosting PPC click fraud traffic. I don’t blame them because I don’t think any hosting provider is detecting and stopping this type of activity on their networks. Even if they do a good job at protecting abuse directed from the outside, providers don’t seem to know or care that they are an indirect source of abuse. Well, unless you report it to them.
But how many people out their besides me have the technical ability to detect and monitor abuse and how many of them bother to report it?
I just found someone trying to hack our server and noticed they were using Microsoft business hosting. I was pleased that MS took the report and investigated and some action resulted.
Why can’t all providers that care be more proactive and monitor for customer traffic that results and “access denied”, 403 errors, or other signs that indicate unwanted activity?
If they don’t want to “spy” on their users, why not set up a special URL that we can use for automatic reporting? I can redirect many forms of abuse and hacking attempts to that URL and then they can investigate it.
Right now, blocking is the key for us. We block most of the non-English speaking world when abuse is detected. And we block most of the hosting provider IP space because even if there is limited abuse, we don’t care about any user traffic that originates there. Most of it is nothing more than bots or abuse.
I try my best to watch and to protect the private network I have set up. Throughout the many years, Its basically futile to try to set up a IP blocking scheme that works. A foreign entity has access to many different USA based computers, and with that simply can command one of the bot to do their dirty work, circumventing any blocking scheme in place.
Reporting helps, but the ISP’s seem to be tight lipped on exactly what they can tell the person once they have reported it. They supposedly investigate the issue. They can then legally inform the attacker(s) to cease the activity, or have to pass that request off to the offending ISP, and if they are even in the same country, ask them to fulfill the request. At the ISP level, they can block an IP, but they wont block a complete domain unless it is doing some really bad stuff. With the IP’s being dynamic, or DHCP, the block typically works until the offending PC gets a dhcp release.
Many ISP’s simply are staffed for a normal day. If they do have a NOC, NOSC or other center to try to thwart any sort of attacks, they are typically concentrating on things that have a higher priority and scale.
The ISP, point blank – are not going to pay much attention to reports unless there are many being reported and they are pressured to do something. Then they fall into your shoes, trying to convince something upstream to do what you have asked. Its much better to concentrate the efforts at protecting your private IP space, hardening servers, pen testing your own stuff from the inside and keep the “unauthorized personnel” out and they will go look somewhere else.
I am not willing to discuss my methods for thwarting most attacks. But you can start by ensuring your behind a NAT and that all services, ports and applications that you are not using are turned off. That will keep your footprint down and the script kiddies that are scanning networks are less likely to pick on you as bait.
Depending on your budget, there are plenty of low hanging IPS solutions out there that work absolutely fine. The IPS that offers some sort of snort based engine, even if it is a custom import works pretty decent.
I work for a ISP and we do take these reports seriously. In 99% of the cases it is some kind of bot net that has infected the local network in the customers home.
What you did not say, Mr ISP Tech Support Guy is if you block all outbound traffic on the reported computer on your network, if you merely report it to the client and/or allow the hacked transmissions to continue.
Furthermore, you didnt say if you are proactively monitoring your customer’s outbound traffic, looking for connections to C&C networks, or other such naughty IPs, or doing deep packet inspection looking for evidence of compromise. Shutting down these connections until systems are cleaned is great incentive to get your users to figure out how to stop crapping all over the internet.
Most routers nowadays will not have a port open not in use, they automatically close them. And not sure what someone can do, such as a business server, to stop a major ddos attack unless paying alot of money to a service such as this one that got hacked.
But I think filtering outgoing ports and ip’s is just as important on a private network. First thing I do is disable ipv6. And although protocols like http/s can be overwhelming I use blacklist programs like peerblock or peerguardian and lists from various sources like iblocklist.com for years to block 3/4’s of the ipv4 webspace on one of my pcs. I two click temp allow ip’s as I browse. Which I guess would be sadistic for most people lol. But contrary to popular belief I do think daily blacklists can still be effective.
It would be nice if isp’s filtered outgoing though, because from what I hear they don’t even block ips outgoing that aren’t even part of their network range which would probably stop alot of ddos attacks…lol
> from what I hear they don’t even block ips outgoing that aren’t even part of their network range
There’s some data to cite…
http://spoofer.cmand.org/summary.php
Obvious flaw of the study is only testing 20K IPs, but I think it’s at least a good ballpark.
There is no excuse for not reporting abuse to any ISP, even if they are unresponsive. The ones that take down an offensive server are helping to clean up the mess, albeit one server at a time. My peers sometimes consider this activity a waste of time. But really if no one reports anything, nothing will ever be done to fix the issue.
My favorite quote for this situation:
Bad men need nothing more to compass their ends, than that good men should look on and do nothing – Mill
Monitoring and reporting is akin to closing the barn doors after the horses have escaped. And yet everyone seems to be re-inventing a way to do the same thing with different cosmetics. For a whole new approach, keep reading.
The hacking, DDOS and other varieties of malware are escalating, not only because of general ignorance, but also because of the continued passive/evasive approach to the problem. And it is now being made more complicated by our own government.
The FTC has gotten involved by holding businesses responsible for hacks and malware that negatively affects their customers – triple jeopardy!
Wyndham Hotel Law Suit
UNITED STATES COURT OF APPEALS FOR THE THIRD CIRCUIT issued in August 2015
FEDERAL TRADE COMMISSION v. WYNDHAM WORLDWIDE CORPORATION
http://www2.ca3.uscourts.gov/opinarch/143514p.pdf
Read Page 8, but not before going to bed unless you want to be up all night!
Check out our just-launched cyber security software at https://theironjacket.com. Our system is now the only solution that detects, identifies, tags and then eliminates malware and other intrusions that make it past your firewall. All activity is robustly logged in immediate, real time which is only a matter of micro-seconds. The IRON JACKET is also the wrap-around that protects our HIPAA Secure and NSA proof file sharing program, https://myorangeconnection.com.
Because they are so impenetrable, both products are only available by application. This limits use to legitimate businesses. Please use the “Contact” page on either web site to request an application or a direct contact.
J. R. Hildebrand, COO / https://theironjacket.com
“~ Hedge entire business on security theatre”
The hackers are either not Americans, or want us to think they’re not.
Por que? Albeit a sentence fragment, the thought makes general sense and the point comes across: sell security, while actually only talking about it; which, unfortunately, is par for the course these days.
Because that’s not how Americans spell “theater”?
My favorites are the guys on irc who claim they are european or austrailian, and spell things like favorite as favourite, but yet keep the same hours as americans lol.
Hey, they could be working for the Australian arm of a US company, and be required to work US hours so they can do real time collaboration with US employees. I did that for a US branch of a German company once, and dear lord did I hate coming in at 3am. Almost as much as I hated the owner, who ran the US branch, but that’s another story.
My understanding (based on dating a long-time theater person way back when) is that the building with a stage is a theater, and what you do on that stage is theatre.
The linguistofascists don’t entirely agree with me, but hey, what do they know, right?
Thanks Brian for the writeup. Hopefully Staminus recovers OK. If anyone needs help with network DDOS mitigation, we are happy to help.
I’ve moved all my services from http://staminus.net to http://hyperfilter.com
The reasons were:
1) Too long downtime.
2) No explanations at all.
3) Lies, lies and lies, and still no official announcement about leaked data (our data).
This was enough, good luck for them.
Ah James, james, james.
you never wish your enemies good luck, and you never interrupt your enemies when they’re making mistakes.
have you learned nothing in all your years here?
reminds me of the e – corp, steel mountain and allsafe cyber security company incident due to fsociety. sorta.
They aren’t my enemies, I’m just unsatisfied with what have happened to me and I decided to move, nothing else.
Someone didn’t get the reference
Hyperfilter.com is a brazilian garage team who ripped the old serverorigin.com website. Proof http://www.webhostingtalk.com/showthread.php?t=1145846
Large companies started in a garage, see as example : Google, Apple, Microsoft, Yahoo… So garages, universities, shops, it doesn’t matter, really.
And when checking stuff on the web, try at least to do not resurrect subjects from 2012, as that’s pretty silly (too many things can change with such time interval), and as long the op is satisfied, that’s all that matters. ( https://www.sengokudaimyo.com/webpix/threadrevive.jpg )
Isn’t this going too out of the topic ? Who cares for any of this, that’s about Staminus and their crappy handling of their own security ffs, we had a lot of losses due to this, some of our boxes got even compromised, sadly it wen’t this way, we are preparing to sue them, since we were certified in terms of security, and with the last issue in Staminus we’ve lost this certification, someone will have to cover us on this one…. Still we are using their service, but considering to change to something else, maybe Level 3.
I hope statminus uses an outside vendor to assist them in investigating, planning, and implementing a resolution to their breach. It was on their watch that the system was compromised, they should not trust them selves to resolve it.
I hope they go out of business. Any business selling security services without having basic security themselves needs to go into bankruptcy.
“… a California-based Internet hosting provider …”
They ARE an outside vendor.
This all makes a big point.
Even when you can’t help people, communicate with them.
Let them know you are putting in effort.
It may “seem” that you are only providing a tech service, but it’s the communication, especially in moments of bad problems that this matters, which is service. (even if its only lip lol)
Even if you post every hour “we are still bla bla bla” it’s miles better than silence, to the customer.
Can someone please post a link to the ezine? Thanks!
No. If you want to see stolen data, you’re on your own. Your neighbor’s teenager will know how to find it.
Many people will see your post. That’s my opinion; let’s see what others say.
http://hastebin.com/raw/oweyukamuj
If they actually didn’t put their power distribution units on their own subnet and prevented traffic to and from that subnet from going over the gateway router, AND left Telnet open on those devices…
Wow. Just.. wow.
Telnet open is not the issue, but using a weak password is, and exposing it on WAN even more, a single VPN would be much more safe in this case. 🙂
Considering that you could use Secure Shell instead of Telnet? Yes, telnet is the problem.
Not all PDUs comes with SSH, really. 🙂
These days when people want to improve security such as OTP, One time Passwords, Limited IP access, even getting a RSA SecurID 700 10-pack is only 500 bucks. Clients will complain its too much to do each time they need to access equipment.
Soon there will be a forced standard that may seem like a pain in the bum, but it needs to be done.
Ezine link? google is your friend. Note that it appears to have been first publicized on reddit.com
Looks like FTA deliberately dox’d a KKK sysadmin with a list of all the domains he wanted protected as well as the source IP he made the request from.
That DOXing might be part of the motive since they went out of their way to highlight it. Or for he/she/their amusement or just white noise (quickly ducks)
I’m all for free speech, but these guys are a liability, I found this the funniest of their screw ups
Company name Staminus
Root password on most of their boxes St4m|nu5
The KKK should know better of course, and not be relying on all this potentially non-Aryan technology.
I sincerely hope this is sarcasm.
They’ve left a Windows Server 2003 box basically open to the web: https://www.shodan.io/host/72.8.157.110 I guess that was a good starting point for any hacker (it’s offline now)
Yeah replying to my own comment – =P
Uhh Ohh – looks like Staminus’ statement was correct – the passwords are indeed “Hashed” and not “Encrypted” – looks like they are using Portable PHP password hashing framework (old article here on how easy it is to decipher) https://www.hackthissite.org/forums/viewtopic.php?f=28&t=11875
How do you know the Server 2003 box belonged to their internal network, rather than customer facing equipment?
Evidently, not the best security methods implemented here but I’ll bet every computer was updated and patch.
It is interesting though that people are actually talking about the KKK alot more these days.
Anyone notice the obvious failure in the ezine:
mysql> select email,companyname,password from tblclients wgere status=’Active’;
http://siph0n.net/exploits.php?id=4561
An earlier post on the onion site claims that Staminus is low key owned by Stackpath. Is this true?
yes. stackpath bought staminus and after the ink dried this happened. stackpath also purchased a well known CDN. none of this has been announced, of course.
Looks like cybercrooks will have bitcoins soon near future so I guess they need money to exchange for bitcoins guess what can get cheap bitcoins from Russia now and sell them to west if I’m right ??
Why the date of the post is showing as 16th march instead of today’s date which is 14th march :-p
March 16, not March 16th.
Take a look on serversdrift.com. They are well know russians administrators for complicated security arrangements and ddos mitigation as well.
owhhh hackers aren’t my enemies, I’m just unsatisfied with what have happened to me and I decided to move, nothing else.
Get in touch with geniushack08@gmail.com for any hacking services of your thought,emails,phones,credit card,school grades change,social media,instant messages,servers and database,etc
LMFAO
Hackers are not the enemies but stupid stuff like that is. The enemy is ignorance. What kind of idiot what actually click that link and send an email? Nonsense like this is what makes bad things happen.