Operating and planting an ATM skimmer — cleverly disguised technology that thieves attach to cash machines to intercept credit and debit card data — can be a risky venture, because the crooks have to return to the scene of the crime to retrieve their skimmers along with the purloined data. Increasingly, however, criminals are using ATM skimmers that eliminate much of that risk by relaying the information via text message.
[NOTE TO READERS: The Today Show this morning ran an interview with me for a segment they produced on ATM skimmers.]
Visit msnbc.com for breaking news, world news, and news about the economy
This latest entry in my series on skimmers includes a number of never before published pictures of a cell-phone based skimmer set that sends stolen bank card data to the attacker using encrypted text messages. The following images were obtained directly from a skimmer maker who sells them on a very well-protected online fraud forum. This particular craftsman designs the fraud devices made-to-order, even requesting photos of the customer’s targeted ATMs before embarking on a sale.
Just as virus writers target Windows in large part because it is the dominant operating system on the planet, skimmer makers tend to center their designs around one or two ATM models that are broadly deployed around the globe. Among the most popular is the NCR 5886, a legitimate, unadulterated version of which is pictured below. 
This skimmer I’m writing about today sells for between $7,000 and $8,000 USD, and includes two main components: The actual card skimmer device that fits over the card acceptance slot and records the data that is stored on the back of any ATM cards inserted into the device; and a metal plate with a fake PIN pad that is designed to sit directly on top of the real PIN pad and capture the victim’s personal identification number (PIN) while simultaneously passing it on to the real PIN pad underneath.
Not all skimmers are so pricey: Many are prefabricated, relatively simple devices that fraudsters attach to an ATM and then collect at some later point to retrieve the stolen data. The trouble with these devices is that the fraudster has to return to the compromised ATM to grab the device and the stolen data stored on it.
In contrast, wireless skimmers like the one pictured below allow the thief to receive the stolen card data from anywhere in the world, provided he or she has a working cell phone signal.
The actual card skimmer in this seller’s model is quite small, and yet includes both a magnetic strip reader and a tiny radio that sends the collected data (known as “dumps” in fraud circles) in an encrypted format to a device built into the PIN pad (more on that in a moment).
Here are a few photos of the razor thin skimmer that comes with this kit:
And here’s a view of the electronics that powers this little thief:
Now, let’s have a look at the brains behind this custom skimming combo. Below is the PIN pad overlay:
And if we turn the bogus PIN pad overlay around, we get a glimpse of what really makes this thing tick:
Although you cannot really tell from this picture, the PIN pad overlay contains its own GSM module, basically the guts of a cell phone that is capable of sending text messages to any phone of the customer’s choosing that operates under the GSM mobile communications standard. According to the maker of this kit, to whom I spoke briefly via online chat, the GSM module is responsible for collecting the skimmed card data from radio transmissions sent by the skimmer, and then bundling that data with the corresponding PIN into an encrypted text message.
The designer says it typically takes between 2 to 4 text messages to send the encrypted output from a single dump and PIN combination.
We didn’t get too chummy in our chat, but one of the pictures this guy shared with me provides a clue to his potential home country. Check out the photograph below, which includes a pencil ostensibly designed to give a point of reference for the size of the bogus PIN pad.
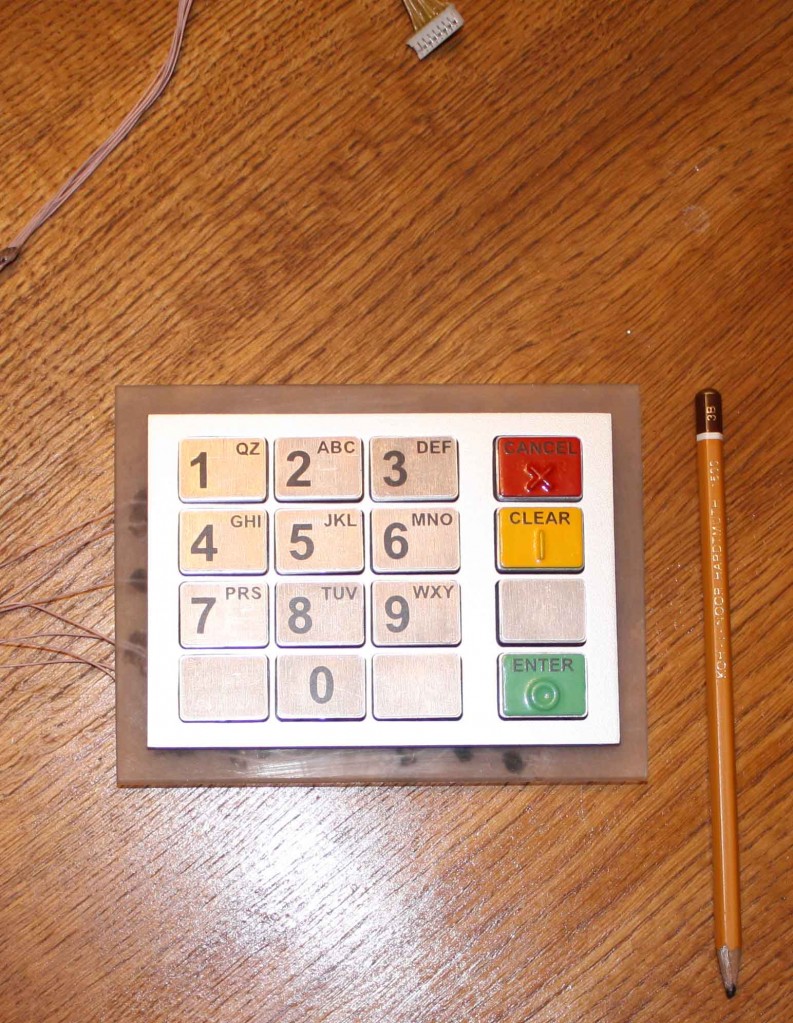 The markings on the pencil show it to be a “Koh-I-Noor” drafting pencil, a brand of writing utensil first introduced in 1890, according to leadholder.com, which bills itself as the online “pencil museum.” Leadholder.com says this writing stick established a number of trends in pencil design that we now take for granted, most notably the yellow finish, a trait that other pencil manufacturers would later imitate. More importantly, the maker of the Koh-I-Noor, a company called L&C Hardmuth, is based in the Czech Republic.
The markings on the pencil show it to be a “Koh-I-Noor” drafting pencil, a brand of writing utensil first introduced in 1890, according to leadholder.com, which bills itself as the online “pencil museum.” Leadholder.com says this writing stick established a number of trends in pencil design that we now take for granted, most notably the yellow finish, a trait that other pencil manufacturers would later imitate. More importantly, the maker of the Koh-I-Noor, a company called L&C Hardmuth, is based in the Czech Republic.
Leadholder curator Dennis Smith said the pencil in the photo is a Czech-made model 1500 that has not been distributed in the U.S. since before World War II.
“The type shown in the picture is of recent vintage, 1990s to present. There was an American made 1500 that died with the [now defunct] U.S. company in the 1990s,” Smith wrote in an e-mail to KrebsOnSecurity. “A company called Chartpak now owns the rights to the trademark in the U.S. They import and distribute products of the Czech company, but not the 1500 for some reason.”
At any rate, below is a photo of both devices attached to a working ATM (the photo has been retouched by the designer, probably to hide markings that might identify the location of the machine).
[EPSB]
Have you seen:
Skimmers Siphoning Card Data at the Pump…Thieves recently attached bank card skimmers to gas pumps at more than 30 service stations along several major highways in and around Denver, Colorado, the latest area to be hit by a scam that allows crooks to siphon credit and debit card account information from motorists filling up their tanks.
[/EPSB]









Why can’t security camera footage/photos at ATM’s be pulled up to find someone carrying ATM sized panels to the device and leaving without them?
Ben,
Sometimes they do!
http://krebsonsecurity.com/2010/05/fun-with-atm-skimmers-part-iii/
I wouldn’t know for sure, but I’d bet that in a lot of cases, security cameras — including those at ATMs — are set-it-and-forget-it type deals where they can be not functioning properly for some time and no one at the branch would notice. But in the banks’ defense, it wouldn’t be hard for the ATM thief to wear a disguise of some kind.
Also, even if they do have a picture, it does no good unless they recognize the person. It would be useful in court, but they have to catch them first.
Here in Nepal, most all ATMs come with a security guard standing outside the door, so unless the guard was paid off, this probably won’t happen. But in other countries where labor is not so cheap, I don’t get why security tapes are not monitored / scanned / whatever to prevent this. If the cam is spraypainted or down for any reason, that should kick off a physical scan of the equipment. How hard is that?