Criminals have launched an major e-mail campaign to deploy the infamous ZeuS Trojan, blasting out spam messages variously disguised as fraud alerts from the Internal Revenue Service, Twitter account hijack warnings, and salacious Youtube.com videos.
 According to Gary Warner, director of research in computer forensics at the University of Alabama, Birmingham, this latest attack appears to be an extension of a broad malware spam campaign that began at the end of May.
According to Gary Warner, director of research in computer forensics at the University of Alabama, Birmingham, this latest attack appears to be an extension of a broad malware spam campaign that began at the end of May.
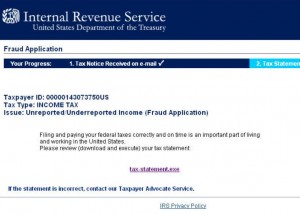
The fake IRS e-mails arrive with the tried-and-true subject line “Notice of Underreported Income,” and encourage the recipient to click a link to review their tax statement.
All of the latest e-mails use a variety of URL shortening services. For example, this shortened link (currently live and dangerous, and therefore neutered here)…
hxxp://qurl.com/zv9j7
….when clicked reverts to:
hxxp://www.irs.gov.vrddr.ru/fraud_application/directory/statement.php?tid=00000143073750US
….which takes the user to one of dozens of identical Web pages that spoof the IRS and encourage visitors to download and review their tax statement, which is of course a powerful and stealthy password-stealing program.
Warner said anti-virus detection for this malware is extremely low: Only three out of 40 different anti-virus products detected the file as malicious, yet none of those currently identify it for what it is: Another new version of the ZeuS Trojan.
These broad attacks usually are quite successful, and in the past they have been used to great effect by the same criminal gangs that have been stealing tens of millions of dollars from small to mid-sized businesses. In September 2009, I wrote about a landfill service company in New York that had $150,000 stolen from its online bank account after an employee opened one of these ZeuS-laden bogus IRS e-mails.
A word to the wise: Do not click on attachments included in unsolicited e-mails, especially those that encourage you to act quickly or else suffer some scary fate. These are almost universally scams or attempts to plant malicious software on your computer. Also, note that the IRS has stated emphatically that it does not communicate with citizens via e-mail.




I always forward these alerts to my coworkers, but every couple of my months someone will come to my office with a sheepish look and say, “I clicked on the button because…”
Brian, the last couple of days my work AV has been quarantining a trojan, and I suspect it’s using Adobe or Javascript to sneak in. I don’t visit a lot of sites other than “reputable” sites like airlines, cnn, government sites, etc., so what else could it be? In 3 years I haven’t gotten one, but for the last 6 days I’ve had the AV message come up letting me know it’s quarantined one. I updated Adobe.
How do I go about setting my PC at work to not let script run unless I specifically allow it?
Thanks many times for your blog!
Hope you don’t mind me chiming in here Brian! The firefox plugin ‘NoScript’ is very powerful and well worth installing- it blocks all javascript on any site you visit, except for what you explicitly allow (by domain, on either a temporary or permanent basis). I use it both at home and at work and once you get used to the extra whitelisting step of browsing to new sites, it’s hard to go back to anything else.
That said, there are other ways a trojan might infect your machine too. I would advise checking for other infected machines on the network, and also any removable storage devices that you use.
Dear Maureen;
How do you know it isn’t a fake message? Some of those popups can be fake messages as a precursor to an attack. Clicking on them, can start a process that gives it permission to do actions other than what it purports to be.
Please bear in mind that I’ve seen some of these popups look just like popular AV brands, or UAC prompts, but they are actually triggers to attempt a malware install. If you are logged in as a standard user, these usually fail – especially on a x64 Windows system.
Have you simply tried removing from quarantine?
Fire Fox with “No Script” will work if you don’t give the page blanket permission. If you do need extensive permission, there are active x blockers that can disable such page controls. I’ve had better luck with Avast Pro v. 5+; as it has an auto-script blocker that is even more effective, and usually doesn’t interfere with page graphics, or page controls, as long as that control icon isn’t infected. If it is infected, all you can see is a red x where the control icon was supposed to be located.
If a sight has been badly compromised, the whole page will not display properly. MBAM can block bad servers that provide the malicious page objects to sites that have been compromised. You have to have the real time protection enabled to do this.
I do not work for Javacools, Alwil, or MBAM, and I don’t make any money or sell any software in regard to this advice. I am just big on promoting web-safety. They all have free versions, though; only Javacools has free real-time active X protection, and Mozilla NoScript is free, and works well when blocking everything on the page. At least there is usually granular control on No Script, so you can decide for your self which objects you trust.
The problem with NoScript is that it requires a bit of sophistication that most people do not have. I have tried to convince non-techies to use NoScript and it has only served to confuse them.
In fact, that’s the problem with a lot of this software that is supposed to protect the user: it is not user friendly! Responses from these programs are not on English but in computerese. They are dry and maybe too descriptive at times. It is as if nobody has tried to use this with “real” users.
Maybe it’s time for the AVS and spyware companies to do some usability studies and figure out a way to communicate risks to real users and not just the geeks.
Also, why are we not pounding on Microsoft for writing software that allows for this type of attack? Why isn’t the browser sandboxed and something watching the sandbox? The whole model is bad and will keep getting worse until Microsoft and other browser vendors look at fixing the browser model.
@Scott
I agree – NoScript is great, but for some users it ‘stops the web working!’ although the same people don’t have a problem using Adblock… some small usability improvements would make NoScript far more popular.
Do your homework – on Vista and Win7 IE does run in a sand box by default. Because of the way Microsoft incorporated IE into Windows XP its not possible back port the sandbox into XP without breaking certian apps from 3rd party developers – the same developers that are screaming that Vista and Win7 are broken and will never change from XP. Its those developers that need to be scolded.
Thanks to everyone who replied. (They are definitely not fake messages.) I try to be as tech-savvy as possible, but a lot of it comes from listening to folks like you. So I hope you all don’t mind if and when I pose a dumb question.
One more thing: after I ran a fix and read the log, I noticed that the harmful files started arriving two days after I installed the American Airlines shopping toolbar. I did it for 500 bonus miles (my bad).
I will read some more about NoScript with your cautions in mind and consider installing it.
Thanks again!
Yes,
Toolbars are notorious for attracting malware, if not installing them directly! Even legitimate sources like the airline you mentioned, may not even be aware they’ve been hijacked!
AdBlock Plus for Firefox is set up for bad ad servers, some of which supply malware. SpywareBlaster has a host file that is malware centric, and concentrates on blocking malware servers. It works for FF and IE both, but you can only have one host file per browser – I believe, so one must choose. With the life-time MBAM license, it will block all bad communications to malicious servers, I’ve begun relying on it pretty heavy now that I had to temporarily stop using Comodo firewall.
Maureen, I never install any toolbar. For any reason. That includes Google, Yahoo and any others. Having said that I use Linux as my operating system rather than Windows. My choice.
Yes, NoScript is very useful but some users will not be able to use it properly because they need educating. Like my wife. Perhaps we need a video that shows thew difference between blocking javascript and not blocking it and the consequences. Brian, do you know of any? Training video maybe? If there are any around I cold post a link on my website http://www.dragonnefyre.org.uk and on my blog http://www.dragonnefyre.wordpress.com. Spreading the word and user education is what’s needed. Yes, there were days when even I didn’t know enough. Now I do it is time to pass on my knowledge to those who need it. Sorry about that Maureen. Bottom line is educating those who need it.
Do you use web sites with ads? There’s an entry point.
I use this site with AdBlock Plus disabled. I want to help Brian’s site anyway I can, although I wouldn’t know if they really look at this.
I doubt very seriously any crackers would be attacking this page; but I got to admit, it is probably a prime target for those that don’t like educated information about web criminals getting out on the internet.
I trust Brian completely.
Just a note: the domain name v-ddr was also used in addition to vrddr with the ccTLD of ru. Both were registered with NAUNET-REG-RIPN (NauNet SP) and both appear to have gone down this afternoon.
It was using the same fast-flux server it has been using for several months and many of the hosting sites on the server are used over and over again.
The main difference I noticed this time was they went to the trouble of registering multiple domains used in the email campaign which then linked to the fast-flux server. Usually they put the domain that references the fast-flux server in the email.
We had to create a thread on inboxrevenge.com with reporting links for the ones that involved spammed links to downloads on Google Groups, since Google did not provide any means for reporting the dangerous downloads on the spammed pages themselves. You had to be familiar with the Google Groups file structure to know what the main page for the group would be. And even when Google finally did respond to our reports, they just put a warning that the files might be spam or malware without actually removing them. openexe.googlegroups.com/web/Twitter_security_model_setup.zip is still alive, for instance.
The links now all appear to be hacked sites. providenceoptical.com looks like it was once legitimate:
http://web.archive.org/web/20011127193653/http://www.providenceoptical.com/
but the home page is now missing and the exposed index links to pages that redirect to software-discovery.net, toldspeak.com, sonnose.ru, and tabletshealthpharmacydirect.net. There’s also an interesting page here:
providenceoptical.com/red.html.hrbackup
with a long list of links to pharma files that the intruder apparently expected to be on a server at MIT (but which are not there now.)
The zeus folks are an interesting lot to keep tabs on. I’ve been monitoring an interesting trend in these same email payloads where instead of the links taking you to a phishing site (for example) as could be expected from the social engineering hook of the spam message, they drop you off at a Canadian Pharmacy site.
The schizophrenia between the lure and the landing is interesting. Why would a Twitter phish, or an Amazon gift card trojan email have a call to action link that drops you on a CPharm site?
Many of these campaigns are characterized by the fact that the spam messages use urls of pages hosted on compromised web servers in the call to action link. The page on the compromised host is just a simple redirect, but increasingly these redirecting pages are including an iframe that fetches 3 level deep obfuscated javascript from a fast-flux’d host (recently, using .ru ccTLDs on port 8080) that if executed, downloads a malicious .pdf and may attempt other exploits as well.
The recent YouTube spam from yesterday was another in this set of campaigns that landed people on a CPharm site (actually toldspeak.com was used here too as mentioned by AlphaCentauri above).
Moreover, the malware distributing hosts would only dish up the code if the browser requesting was vulnerable, and even then, would only do so once for a given IP.
Anyone have theories on the odd divergence between the spam lure and the CPharm landing page?
It is possible that it redirects you specifically to different links.
I have also done a bit of my own research on malware (not zeus specifically) and I have discovered a long known fact that the exploited servers register your IP/mac in case you are say an AV company employee and wish to get multiple samples.
The samples provided are randomized(recrypted etc) and if you go to the same malicious link few times in a row with the same IP/mac first time you get a fake AV second time you get nothing or c-pharmacy or others….can also be more older exploits on the final links to confuse potential security researchers.
“Canadian Pharmacy” spam comes from any of hundreds of independent affiliates. Each of them may also be mailing for several other affiliate programs.
In addition, Zeus is distributed by multiple spammers who may have purchased the kit. So inconsistencies are to be expected.
I imagine some mailer realized people clueless enough to fall for the phish emails would purchase drugs once they arrived at the CPh site, so he’s continued that strategy.
I have no doubt that the Partnerka and Zeus (although perhaps not exclusively) toolkits are involved with this recent spate of schizophrenic campaigns.
I think it might serve as a kind of red herring, to draw attention away from the one-click exploit that seems to be the true nature of these campaigns.
Or it may simply be that the PPI crew is rushing to take advantage of the recent Adobe vulns, and the drop at a CPharm site is just another monetization aspect of the campaign. (Statistically, I can imagine, this would be a good move for the spammers.)
Whatever the case, the spammers appear to be doing whatever it takes to get the user to click, using every SE trick in the book.
I guess why this has struck me as so novel is because I can’t recall any other case where, in particular, phishing lures have been used principally to generate clicks, not to actually take the user to a phishing site.
That, and the fact that these are not small isolated cases — it’s the majority of the newly active, significant campaigns this week (across a wide variety of categories).
People who respond to spam emails must just have brains that process things differently than mine. I get many spams for CPh that imitate the format of the fake e-card spams that were used to spread Storm Worm — except instead of getting a malware download, you just go to a pharma site. Who would be /more/ likely to follow a link if it looked like a malware download?
Ditto for the attachments that just contain image files of the spammed link. Everyone claims to know not to open attachments from people they don’t know. But I get lots of spams that do this.
These short URLs are being abused far too much.
I always wonder why nobody realized in advance how easy it is to hide malicious stuff behind those nice URLs. For instance, Apache.org got hacked by hiding an XSS: http://www.avertlabs.com/research/blog/index.php/2010/04/14/from-xss-to-root-lessons-learned-from-a-security-breach/
When TinyURL, and all the other >500 followers, started to offer shortening services, all the people began to use short URLs like crazy. I believe that Twitter played a significant role, though. Wouldn’t it be better to prevent all this to happen by analyzing short links before the bad guys started to exploit them?
I would like to notify our effort along this direction: besides it’s own shortening service, http://long-shore.com offers a simple analyzer that goes a little deeper than simply “previewing”. Add-ons for Firefox and other browsers are available now. In the future, we will integrate with major analyzers such as Google Safe Browse, PhishTank and friends to alert the users before they click.
Yes, definitely abused too much. Almost as though they were designed specifically to help criminal groups like zeus conceal their activity.
Your approach sounds good. Personally, I never go to one of these shortened URLs without first checking it out with a program, not a browser, designed specifically to examine what it does.
Twitter will release their own URL shortener later in the year. The site is already active but the service is not. They plan on checking each and every URL posted and already use this internally on DMs.
“/fraud_application/directory/statement.php”
“detection for this malware is extremely low: Only three out of 40 different anti-virus products detected the file as malicious, yet none of those currently identify it for what it is: Another new version of the ZeuS Trojan.”
Note: that exact same path, “/fraud_application/directory/statement.php”, has been used by zeus to reference the bogus tax statement and download the zeus trojan as ‘statement.exe’ or ‘tax-statement.exe’ since at least september of last year.
And also: You don’t have to do an MD5 on a file to know that anything the IRS sends you from a site hosted in the russian federation, or simply outside the US, should probably be avoided.
I find that trying to foil Zues in other ways may be more productive; like Comodo’s HIPs that will stop file manipulation, or any one of the programs that block browser communications and/or keyboard/video logging.
Rapport is free, and seemingly makes the similar claims as Prevx. So far it has blocked all unauthorized keyboard or video attempts in my honeypot lab. Can’t vouch for the browser “bubble” claim though.
I’ve only had one false positive with Prevx so far.
MBAM seems to do a very good job blocking all communications to the maleware server minions though.
Sure wish you guys would name the AV programs that do detect Zeus as well as the Firefox add-ons mentioned above.
It might seem like a worthy thing to know, but its worth nothing.
Come 2morrow or next zues 0-3 other random out of 40 AV will detect it(it is usually 0 you can check it)
The best ways I can think of against these type of attacks are:
1 – experience/awareness, spam usually fits a pattern and you will learn to recognize it eventually. If you have any doubt search the links you receive before entering them.
90% of the scam is the social engineering email, tax notes or paypal or other account related warnings
2 – sandboxing your browser, use Sandboxy instead of Noscript. Noscript while it can fit some people IMO is a really annoying and rather useless add-on, and it is not unheard of exploits going specifically to disable noscript or bypass it :
http://forums.mozillazine.org/viewtopic.php?p=6025135#p6025135
These are comments also from the author of noscirpt, besides java scripts mostly do not include exploits and you might want to let them run without clicking OK on noscirpt all the time.
Sandboxing is not 100% immune either but it is like 99% prevent any harm from browser downloaded executable, if you had sandboxed browser and went to a zeus page and downloaded malware and you even ran it, no harm would be caused.
I really prefer solutions that do not irritate users like noscirpt and crazy heuristics programs, they do help but also require too much attention. It is less annoying to pop a sandboxed browser once in a while than click ok every 2 mins.
What is your opinion of Chrome? I’d try it for the sandbox, but it doesn’t work on x64 Windows. I haven’t checked to see if Sandboxie has a 64 bit version.
The great majority of my clients are migrating to x64 Windows.
“A word to the wise: Do not click on attachments included in unsolicited e-mails, especially those that encourage you to act quickly or else suffer some scary fate.”
How long have we been espousing this???
You can lead a horse to water…
IMHO, the real issue here is a lack of critical thinking skills causing what is called “low hanging fruit”. There are just too many ignorant people who will always be ripe for the picking. 🙁
The IRS is VERY interested in hearing about scams that are perpetrated in its name.
Forward the suspect e-mail to:
phishing@irs.gov
Brian, the shortened URL in your article was effectively neutered, but the actual URL with hxxp is only neutered in IE. In Firefox, the rest of the URL remains a valid link (which may or may not connect to a live site — I won’t risk clicking it to find out!)
They came back this afternoon with domains “pdll” and “msdll”, same ccTLD of “ru”, registered with NAUNET-REG-RIPN (NauNet SP).
Registrar URL: http://www.naunet.ru.
You can now add “psdrv” to that list of domains, same ccTLD of “ru” and same registrar: NAUNET-REG-RIPN (NauNet SP).
They are using a fast-flux server with 8 sites per domain. They have added Bank of Spain to their American Express and IRS exploits on these sites.
Registrar URL: http://www.naunet.ru.
Registrar Email: domreg@naunet.ru
All domains referencing the fast-flux server used by the botnet to deliver the zeus trojan via the IRS scam appear to have been unregistered late last night.
I am not seeing the ff hosts being used to distribute the malware anymore either. They appear to have switched to using compromised hosts.
These campaigns using the malicious iframe have largely switched to attaching the javascript downloader directly to the spam in various forms (.html, or zipped .html) instead of having the browser fetch the downloader via an iframe in the page linked by the call-to-action url.
Also the drop site has changed from the Canadian Pharmacy to a fake Rolex site.
Or at least this was the case as of Tuesday night; I’ve been on vacation 🙂
One item of note that I discovered the other night was that if you deobfuscate the javascript downloader through the first level of obfuscation, VT goes from 0 detections to 3. After reversing the second layer of obfuscation to obtain the raw js, detection goes up to 13 vendors on VT. Interesting that so few AV companies can detect the fairly obvious signatures inherent in obfuscated code.
Here’s my scan of the raw js:
http://www.virustotal.com/file-scan/report.html?id=667eb8fb323b390165539fd577d462576e8059272f0d7c282a87e7fe4457faa0-1276690545
Thanks for the info. I got an ‘object not found’ on your link, however.
I am going to have to start digging into the javascript myself. Zeus seems to be giving up on the ff botnets. Maybe just doesn’t provide the level of protection they once enjoyed. They sure stopped using the 15 site ff servers referred to as ‘avalanche’. Last time I saw them use that was late february of this year. But they are still trying ff servers with 8 sites like this last exploit.
Oops, sorry about that; I must’ve grabbed the wrong link. VT seems to be having some issues recently too. I was stoked when they added the comment and login features, but that seems to have only lasted about a day. Hopefully they will bring it back at some point.
Anyway, I put up a fairly detailed post about this topic here: http://www.redcondor.com/blog/?p=246
That has the correct VT links… 😉
They came back again this afternoon. This time the domain “filedrv”, same ccTLD of “ru”, same registrar “NAUNET-REG-RIPN (NauNet SP)”.
They are using a fast-flux server with 8 sites per domain. They have added BBVA bank to their American Express, Banco de Espana and IRS exploits on these sites.
Registrar URL: http://www.naunet.ru.
Registrar Email: domreg@naunet.ru
The domain names “pdll” and “msdll” have been re-registered this morning. So the zeus trojan is still being delivered using the IRS ‘fraud statement’ exploit and banks are being faked.
The same ccTLD of “ru” and same registrar are being used.
Registrar URL: http://www.naunet.ru.
Registrar Email: domreg@naunet.ru
It appears as long as a registrar pays their dues they are allowed to participate in internet criminal activity with no interference by any governing body.
The domain “srvdll” has been re-activated this afternoon. That makes at least 4 active domains referencing the fast-flux server on this botnet. So the zeus trojan is still being delivered using the IRS ‘fraud statement’ exploit and several banks are being faked.
The same ccTLD of “ru” is being used. This is still compliments of registrar “NAUNET-REG-RIPN (NauNet SP)”.
Registrar URL: http://www.naunet.ru.
Registrar Email: domreg@naunet.ru
This makes the fifth straight day that this registrar has had active domains to deliver the zeus trojan.
Early this morning, domains “msdll”, “pdll” and “filedrv” became inactive, leaving “srvdll” as the only NauNet active domain.
Domain “srvdll” was up and down all morning today. It appears to have finally gone offline at about 10:00 (UTC -400). I know of no other active NauNet domains referencing the botnet hosting the Zeus trojan.