Adobe Systems Inc. says its plans to issue a patch on Wednesday to fix a zero-day vulnerability in its Flash Player software that is reportedly being exploited in active attacks. The flaw was disclosed publicly over the weekend after hackers broke into and posted online hundreds of gigabytes of data from Hacking Team, a controversial Italian company that’s long been accused of helping repressive regimes spy on dissident groups.
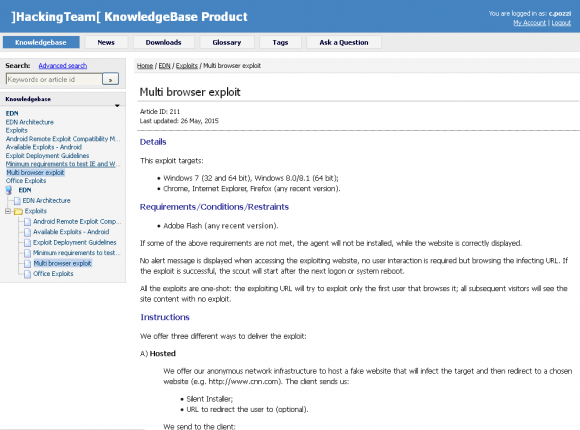
A knowledge base file stolen from Hacking Team explaining how to use a Flash exploit developed by the company.
In an advisory published today, Adobe said “a critical vulnerability (CVE-2015-5119) has been identified in Adobe Flash Player 18.0.0.194 and earlier versions for Windows, Macintosh and Linux. Successful exploitation could cause a crash and potentially allow an attacker to take control of the affected system.”
Update, July 8, 12:13 p.m. ET: The patch is now available in Flash Player 18.0.0.203 for Windows and Mac systems. See this advisory for more information and for links to downloads.
Original story:
Several reports on Twitter suggested the exploit could be used to bypass Google Chrome‘s protective “sandbox” technology, a security feature that forces the program to run in a heightened security mode designed to block attacks that target vulnerabilities in Flash. A spokesperson for Google confirmed that attackers could evade the Chrome sandbox by using the Flash exploit in tandem with another Windows vulnerability that appears to be unpatched at the moment. Google also says its already in the process of pushing the Flash fix out to Chrome users.
The Flash flaw was uncovered after Hacking Team’s proprietary information was posted online by hacktivists seeking to disprove the company’s claims that it does not work with repressive regimes (the leaked data suggests that Hacking Team has contracted to develop exploits for a variety of countries, including Egypt, Lebanon, Ethiopia, Sudan and Thailand). Included in the cache are several exploits for unpatched flaws, including apparently a Windows vulnerability.
According to new research from security firm Trend Micro, there is evidence that the Flash bug is being exploited in active attacks.
“A separate attack against one of these vulnerabilities shows that not sharing the discovery of vulnerabilities with the vendor or broader security community leaves everyone at risk,” wrote Christopher Budd, global threat communications manager at Trend. “This latest attack is yet another demonstration that Adobe is a prime target for exploit across commercial and consumer IT systems.”
There is no question that Adobe Flash Player is a major target of attackers. This Wednesday will mark the seventh time in as many months that Adobe has issued an emergency update to fix a zero-day flaw in Flash Player (the last one was on June 23).
Perhaps a more sane approach to incessantly patching Flash Player is to remove it altogether. Late last month, I blogged about my experience doing just that, and found I didn’t miss the program much at all. In any case, I’ll update this post once Adobe has issued an official fix.




I disabled Flash rather than not installing it, then it’s available if I need it for something…
I also run Flash disabled under Windows 7 sp1 x64. I only invoke it when I need it, using right click under Chrome, which I manually updated to Version 43.0.2357.132 m earlier today. Adobe Flash site does not list this level yet when I last checked.
Doesn’t matter. The .dll’s are still there that get exploited. You are still vulnerable even if you have it “disabled”.
is this true? can the dll get called even if flash is disabled?
No, if the plugin is disabled the browser won’t load the DLL’s. At least that is how it works under IE.
You know, if you have decent host mitigations in place – (even dare I say M$’s EMET), 99.8675309% of Flash vulnerabilities can be mitigated seeing as they are usually memory exploits. Just my $0.02.
“99.8675309%”?
You know, 76.285496301% of statistics are made up on the spot.
John, I don’t think you see what he did there…
You rang?
I got your number. I need to make you mine. Jenny, don’t change your number. You don’t know me but you make me so happy.
Jenny??
For those that don’t know the reference, google “Tommy Tutone jenny”. Talk about a blast from the past.
Yeah, that was 33 years ago, c.1982.
867-5309/Jenny – Wikipedia, the free encyclopedia https://en.wikipedia.org/wiki/867-5309/Jenny
Tommy Tutone – 867-5309/Jenny – YouTube https://www.youtube.com/watch?v=6WTdTwcmxyo
The cyber whipper-snappers of today just don’t have that depth of pop culture institutional knowledge… 😉
I have had Flash disabled (as an IE add-on) for a couple of months now on both our computers and don’t really miss it. Once in a while a site requests to run Flash, but I don’t need it to get the information I wanted from the site.
Regards,
If you still use Flash you’re going to have a bad time. Any network security stack that allows the deployment and execution of Flash, even within a virtualized container such as Chrome while running EMET, is inherently insecure and can be made to fail. While understanding that you can never achieve absolute security know that you can still protect yourself from the most common risks.
https://drive.google.com/file/d/0B5pT4hU_yYUWcUtsUWxxcFJjOVU/view?pli=1
Has anyone tested the exploit against Malwarebytes Anti-Exploit. It should block it.
That is a joke right? The flash exploit comes coupled with a 2nd 0day privilege exploit that gives the malicious code “NT Authority/System”. Malwarebytes can’t touch that.
The Flash exploit is blocked by EMET & Malwarebytes Anti-Exploit.
The Windows Kernel vuln is a priv escalation, which is outside the scope of EMET and Malwarebytes Anti-Exploit who deal with remote code exec vulnerabilities.
According to MS “We believe the overall risk for customers is limited, as this vulnerability could not, on its own, allow an adversary to take control of a machine”.
I run EMET using the default installation configuration. Is this sufficient to block the Flash exploit? Thanks!
“Perhaps a more sane approach to incessantly patching Flash Player is to remove it altogether.”
I completely agree.
loop and loop security patch again
Well if the “hacktivists” are Anonymous, I wouldn’t take this too seriously. It wouldn’t surprise me if someone in Anonymous, a real criminal, is pissed and wants revenge.
I uninstalled Flash in 2012 and don’t miss it at all.
This is what you know… Imagine what you don’t know…
Can someone comment on using a Flash-block/Flash-control browser plug-in to run Flash content on an “as-needed” basis? That would presumably block the Flash-based ads, but still allow to use of Flash-based video players, for example…
Leo
Here in the UK the BBC iPlayer requires Flash. I use Flash Block in Firefox but I need to “whitelist” the BBC urls to allow access to the Player. Flash Block stops all those annoying adds eg running athletes, moving cars etc that are just a distraction.
A more general question. Can anyone recommend an alternative to Flash that will still allow the iPlayer to work?
Brian
+1
Still trawling through the BBC site looking for more on this. Nothing found yet.
It’s time for internet users to move away from Adobe Flash for good.
Please get a clue. There will NEVER be a piece of software with >98% installed base that is not a target for hackers. Or did you think HTML5/web browsers/OS/apps/etc. are secure and hack-proof?
Do you even know what the steps are to exploit the security flaw in Flash Player?
I uninstalled it a month ago and haven’t missed it since. I use shumway now and “HTML5video everywhere”. Flash is a dying technology anyway.
Perhaps, but a lot of business application rely on Flash to operate, unfortunately the world doesn’t simply stop at people watching cats on youtube.
Have you noticed the growing number of businesses that are getting hacked? that are getting their security systems breached? that are bleeding sensitive data?
I understand what your saying but there is a reason why all these bad things are happening.
It’s all really keen how the tech-heads (of which I’m one) get on without the apparent need of Flash. High five.
Now help me explain that to my ~80 yo parents, my 12 yo daughter, and my cousins out in E. Beefeck.
Corporate interests aside, that’s where the real damage is happening.
I have a network with ~200 users. I blocked *.swf and *.flv at the gateway about 6 months ago and asked my users to let me know what business applications stopped working so that I could whitelist the domains.. I got about 10 requests in the first month. Surprisingly easy.
John,
I think this is a great mitigation, while Flash may be a special case because it frequently has critical vulnerabilities, all applications will have vulnerabilities at some point and it is important to put in effective mitigations such as yours to limit the attack vectors. Applying core tenants of security such as “Deny by Default, Allow by Exception” are some of your best weapons in combating bad actors. It may take a little bit of extra work, but its better than sitting around waiting for patches.
Are you just blacklisting those file extensions? That may block most Flash files, but it won’t get all of them. For instance, a Flash file can have another extension like *.jpg or no extension at all. Ideally you’d check the headers in the response for “application/x-shockwave-flash” and so on before letting the rest of it through.
Also you should block Silverlight too if you aren’t already. That’s probably the next plugin that hackers will go to if it becomes too hard to exploit Flash.
I wish they would rename new versions by date instead of jumping around with version 17 something one day then 18 something another day.
Imagine:
Adobe FlashPlayer Plugin version MM/DD/YYYY has been released?
That’s a good suggestion, except that they should use the ISO 8601 date standard: YYYY-MM-DD.
Note that the rational ISO 8601 standard proceeds from the most general (the year) first to the most specific (day). That is exactly the order of importance you place on the information if you’re searching for dated information.
Note that the European custom (DD-MM-YYYY) is exactly backwards.
So, there are people who actually still have Flash installed? Wonders over wonders!
ag.
Everyone so far has carefully avoided mentioning that this Flash zero-day was being held for private commercial use by a company which sold malware incorporating this 0-day to spooks and spies in various countries. Lots of questions suggest themselves, but here’s one to start : this is one of the smaller players in the field – so how many more zero-days are being guarded for use by the US Navy, the NSA, GCHQ, and all the rest?
Hayton, good question. I wrote about some research into this subject not long ago. You may find it eye-opening and food for thought. From the story:
“These are some of the questions posed by Stefan Frei, research director for Austin, Texas-based NSS Labs. Frei pored over reports from and about some of those private vendors — including boutique exploit providers like Endgame Systems, Exodus Intelligence, Netragard, ReVuln and VUPEN — and concluded that jointly these firms alone have the capacity to sell more than 100 zero-day exploits per year.
According to Frei, if we accept that the average zero-day exploit persists for about 312 days before it is detected (an estimate made by researchers at Symantec Research Labs), this means that these firms probably provide access to at least 85 zero-day exploits on any given day of the year. These companies all say they reserve the right to restrict which organizations, individuals and nation states may purchase their products, but they all expressly do not share information about exploits and flaws with the affected software vendors.”
Read more here:
http://krebsonsecurity.com/2013/12/how-many-zero-days-hit-you-today/
Supposedly the NSA etc. are the biggest buyers / owners of zero day exploits by far. And of course having those back doors means everyone else can and does discover and use those backdoors as well.
http://www.networkworld.com/article/2224620/microsoft-subnet/u-s–government-is–biggest-buyer–of-zero-day-vulnerabilities–report-claims.html
Got a Windows 10 preview system here. I’ve disabled Flash in Edge and in Chrome ( the two browsers in use).
Question: How do I know when Microsoft and Google have updated Flash in those browsers? Windows Updates will presumably tell me when it’s updating Flash, unless it hides it withing a generic security update. I see no way to get Edge to tell me what version of Flash it’s using.
You can always tell what Flash version you are actually running, with comparison to the most recent update, by going to:
http://www.adobe.com/software/flash/about/
Better than trying to get the browser to tell you, I think.
In chrome type: about:version and look for the flash version
If your chrome is up to date it should say:
Flash 18.0.0.204
that is, as of 07-11-2015 for
Google Chrome 43.0.2357.132 (Official Build) (64-bit)
Windows and Macintosh versions of Flash 18.0.0.203 now up at https://www.adobe.com/ca/products/flashplayer/distribution3.html
I’ve seen the update from MS for Win 8.1, but not for Win10, either either Edge or IE. Four separate Windows Defenders updates have come down today, though, for Win10.
Given its prerelease status, they lack of an immediate update for Win10 doesn’t surprise me. I still haven’t found a way to determine what version Edge is using.
Nice to see Adobe moving quickly on this, frankly I was hoping there would be a cache of exploits unearthed from Hacking Team and (as a result) patched.
Sounds like the Windows exploit is in the process of being closed. Wonder what the OS exploits are for OS X and Linux and are they being closed now?
There will likely be more. My understanding was that 400 GB of data were exfiltrated in the hack.
NYSE halted, United Airlines issues, Wall Street Journal website down. Coincidence?
Am I at risk even after installing a patch? What if I’ve already been compromised by malware due to a zero-day, and then I install Adobe’s patch — am I still compromised? (I’m a Mac user.).
If your computer is compromised, it’s compromised until it’s cleaned and personally, the only way I’d consider cleaning it is wiping the drive and reinstalling everything. If there’s a risk that the attacker also compromised firmware, then I’d wipe out all the data and trash the c computer and its peripherals.
Thankfully, it’s unlikely that you’re the target of someone with the resources and incentive to do this.
The specific attack described here was two part:
1. Adobe Flash exploit (runs on Linux, Mac OS X, and Windows)
2. Windows privilege escalation (Windows only)
Unless someone paired the Flash exploit with a similar OS X exploit, or wrote data elsewhere to run as you, the consequences of attacking your Macintosh are milder than the Windows attack. At best, it could leave a program that could run as you and steal/destroy all your data, but if you created a new user on your computer, that user would be mostly immune.
As a Macintosh user, once you’ve updated Flash, you’re only vulnerable to whatever other (unpublished) exploits are out there (and there are probably others as Brian notes). Whereas Windows users are still at heightened t risk I until Microsoft patches the Windows bug.
Windows users should be using EMET, which apparently would have protected against the Flash exploit, and will hopefully protect them against similar attacks which would otherwise be able to escalate via the Windows bug.
If you have NOT removed whatever malware has been installed on your system due to the Adobe exploit, your system is still compromised.
I find it interesting that you seem to think that being a MAC user has anything to do with anything.
As to your main question though….
Since Adobe has already been patched countless times and then given countless more patches to fix those patches….not to mention various patches for the OS and the browser
I would say that your still at risk….especially if your router is still compromised.
Google released the flash update for Chrome. See chrome://plugins and you should the new version 18.0.0.203.
The Maltese government was attempting to purchase this software.
http://daphnecaruanagalizia.com/2015/07/this-government-is-going-mad-now-it-wants-to-hack-us/
203 updates later… and it’s STILL buggy and a major
security risk.
What is Adobe’s problem????
Maybe you’ll fix it by the 450th update????
Why does this very “security” site have a total unsecure
https connection????
I take it you meant HTTP (plaintext), not HTTPS (encrypted). If so, the answer is that It’s Complicated. First off, there is no such thing as ‘secure’, as you always have to consider context. What am I securing, against what threat?
If you care about what is *in* the packets, such as a credit card number, you very much want HTTPS. But you want the contents of the packets (your comment) you sent to this site to appear in public anyway, so why would you demand HTTPS, in that context?
If, on the other hand, you don’t want anyone to know the contents of what you have been reading, you should probably be aware that metadata is more useful, in an NSA-style mass surveillance context. Despite government denials, metadata enables traffic analysis — a powerful tool. Encrypted packets do not protect you from that. Routing data, etc., is still available to snoopers. To protect yourself in that context, you need something like Tor.
Tor, BTW, is a point of disagreement between Brian and myself. He considers it evil, I do not.
But really, the worst thing you can do is automatically associate HTTPS with ‘secure’. That makes TLS/SSL certificate vendors happy, but it likely does not deliver on all of your expectations. Sorry, but it really is complicated, and it doesn’t seem to be well understood, in the face of massive marketing campaigns, that complicated power tools may leave the fingers of all but the most wary users lying on the ground.